Zdlra copy to cloud
- 1. ZDLRA Copy to Cloud: Backup Workflow This procedure for archive-to-cloud builds on the techniques used for copy-to-tape. The difference is that it sends backups to cloud repositories for longer term storage. This procedure includes configuring a credential wallet to store TDE master keys, because backups are encrypted before they are archived to a cloud repository. The initial configuration tasks are performed in the Oracle Key Vault to prepare the wallet. At the end, a job template is created and run for archive-to-cloud. Pre-requisites for Archive-to-Cloud The following prerequisites must be met before starting to use cloud storage with the Recovery Appliance. Protected database(s) should already be enrolled and backups taken to the Recovery Appliance. The Recovery Appliance has been registered and enrolled at an Oracle Key Vault. All backup objects archived to cloud storage are encrypted using a random Data Encryption Key (DEK). A Transparent Data Encryption (TDE) master key for each protected database is used to encrypt the DEK; the encrypted DEK is stored in the backup piece. The Oracle Key Vault (OKV) contains the TDE master keys; it does not contain the individual DEKs used to encrypt backups written to tape or cloud. A protected database may acquire many TDE master keys with time, so restoration of an individual archived object requires the protected database's master key in use at time of backup.
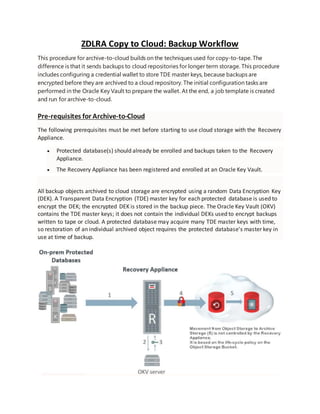
- 2. 1. Incremental backupsentunencryptedtoZDLRA – Virtual Full iscreated 2. ZDLRA requestsencryptionkeyfromOKV server 3. OKV serversendsencryptionkeytoZDLRA 4. ZDLRA encryptsvirtual full backuppiecesandsendsthemtocloudstorage 5. ObjectLifecycle Rulesmove the backuppiecestoArchive Storage. How Oracle Key vault works with Recovery appliance? The Oracle Key Vault (OKV) stores the TDE master keys and also keeps track of all enrolled endpoints. Endpoints are the database servers, application servers, and computer systems where actual cryptographic operations such as encryption or decryption are performed. Endpoints request OKV to store and retrieve security objects. Restore from Cloud Storage
- 3. 1. Restore requestfromProtectedDatabase isinitiatedonZDLRA 2. ZDLRA requestsencryptionkeyfromOKV server 3. OKV serversendsencryptionkeytoZDLRA 4. ZDLRA requestsbackuppiecesfromcloudstorage 5. If backuppiecesare inArchive Storage,theyare firstrecalledtoObjectStorage 6. ZDLRA retrievesbackuppiecesfromObjectStorage,decryptsthemandsends themtoProtectedDB Restore Directly to On-PremDatabase from CloudStorage 1. Restore requestfromCloudStorage isinitiatedbyProtectedDB 2. ProtectedDB (mustbe enrolledasOKV endpoint) requestsdecryptionkeytoOKV server 3. OKV serversendsdecryptionkeytoProtectedDB 4. ProtectedDB catalogsreadsbackup piecesfromCloudObjectStorage
- 4. EM Archive to CloudReporting Cloud backup Cost and estimates: Object storage and archive storage on the cloud will be based on Pay as you Go model. Infrequently accessed data is a prime candidate to be archived to the cloud. You can store data in the cloud for less than half a penny per GB of data. And, cloud storage infrastructure scales infinitely, so you will never run out of storage. Moving infrequently accessed data to the cloud will let you stretch your dollar to fit your storage budget! Oracle Cloud InfrastructureArchive Storageis purpose-built to storeall your long living, infrequentlyaccessed data. Whether you havea need to offload data from your primary storagearray, or you wish to archive data for a long duration to stay compliant with governmentregulations, wehaveyou covered. With prices as low as $0.003/GB per month, OracleArchiveStorageoffers a compelling reason for you to archiveinfrequently accessed data to thecloud. Why are we using OCI Object Storageand Archival storage? UseObject Storageto store'hot' data that you need unrestricted and immediateaccess to at all times. ArchiveStorageis ideal for storing 'cold' data that you do not need to access instantaneously. To read data from ArchiveStorage, you need to first 'Restore' thedata (using therestorework flow) to a staging area in Object Storage, where it can be read. Data stays in Object Storagefor a fixed period of timeafter which thedata is returned back to theArchiveStoragepool and becomes inaccessibleonceagain. Please notethat even
- 5. though you cannot instantaneouslyaccess data in theArchiveStorage, you can retrievethe archived object's metadata at all times.You can use Object Storageto preservebackup and archivedata that must bestored for an extended duration to adhereto various compliance mandates. How Oracle Key Vault Is Licensed? Oracle Key Vault is comprised of the following components: ■ Oracle Key Vault server ■ Oracle Key vault okvutil command-line utility ■ Oracle Key Vault PKCS#11 library ■ Oracle Key Vault management console The licensing is based on a per Oracle Key Vault server installation without per processor cost. There are no license restrictions on the number of endpoints connecting to the Oracle Key Vault server. This license includes restricted use licensing for the entire Oracle Key Vault stack. You should deploy a pair of Oracle Key Vault servers as primary and standby servers for high availability or network topology purposes. Why Kaiser should incorporate copy-to-cloud feature? Oracle’s Recovery Appliance copy-to-cloud feature represents the next leap forward in Oracle database backup and recovery technology. It reduces system, storage and networking overhead, while providing the full range of Oracle database backup & recovery functionality. Copy-to-cloud feature addresses all major sources of data loss by providing superior protection of database transaction logs, comprehensive database-aware block validation, policy based, recovery-aware data retention. Data encryption protect the data at-rest and in-transit in a way that allows to meet the security and compliance requirements with respect to cryptographic algorithms and key management. With various Advantages of object storage, it also includes Excellent for dealing with ransomware. With the ever-growing numbers of malware infections, and specifically ransomware, there is a tremendous need for giving serious thought to data security. Public cloud storage offers a few inherent ways to protect against and recover from ransomware, including cloud IAM and version control. Ransomware continued to dominate the world of cybersecurity. 6 out of 10 malware payloads in Q1 were ransomware. Furthermore, we can safely assume that ransomware has become the biggest security threat any organization or individual may face in the cyber realm.
- 6. Since an object is immutable (unchangeable), if ransomware encrypts an object, it becomes a new version. A new object is stored while the previous object remains intact, if you have a backup of it. When it comes to object storage and ransomware, object storage will not stop ransomware from attacking, even if it is seldom the target of a ransomware attack. However, what object storage can do is to help speed recovery from a ransomware attack. Additional Data Protection Advantages with Object Storage: Traditional architectures are coming under continual pressure as HDD sizes continue to increase. RAID recovery times are growing, creating vulnerability windows for subsequent failures that can lead to permanent data loss. Object storage uses erasure coding to protect data. This is a data protection scheme that breaks data into shards (fragments or symbols) that are encoded with parity (redundant data), and then stored across multiple storage media. Only a subset of the shards is needed to rehydrate the data and make it available so that in case of a failure, there is no rebuild involved, and no down time.