Computer networking.word
•Download as DOCX, PDF•
0 likes•24 views
hi i am a studend of bscs
Report
Share
Report
Share
Recommended
Recommended
More Related Content
Similar to Computer networking.word
Similar to Computer networking.word (20)
Analysis of Random Based Mobility Model using TCP Traffic for AODV and DSDV M...

Analysis of Random Based Mobility Model using TCP Traffic for AODV and DSDV M...
Lecture W2 CN Network Types, Layered approach.pptx

Lecture W2 CN Network Types, Layered approach.pptx
An Enhanced DSR Protocol for Improving QoS in MANET

An Enhanced DSR Protocol for Improving QoS in MANET
Recently uploaded
Recently uploaded (20)
Abortion Clinic in Kwa thema +27791653574 Kwa thema WhatsApp Abortion Clinic ...

Abortion Clinic in Kwa thema +27791653574 Kwa thema WhatsApp Abortion Clinic ...
Registry Data Accuracy Improvements, presented by Chimi Dorji at SANOG 41 / I...

Registry Data Accuracy Improvements, presented by Chimi Dorji at SANOG 41 / I...
[Hackersuli] Élő szövet a fémvázon: Python és gépi tanulás a Zeek platformon![[Hackersuli] Élő szövet a fémvázon: Python és gépi tanulás a Zeek platformon](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Hackersuli] Élő szövet a fémvázon: Python és gépi tanulás a Zeek platformon](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Hackersuli] Élő szövet a fémvázon: Python és gépi tanulás a Zeek platformon
Discovering OfficialUSA.com Your Go-To Resource.pdf

Discovering OfficialUSA.com Your Go-To Resource.pdf
TOP 100 Vulnerabilities Step-by-Step Guide Handbook

TOP 100 Vulnerabilities Step-by-Step Guide Handbook
SOC Analyst Guide For Beginners SOC analysts work as members of a managed sec...

SOC Analyst Guide For Beginners SOC analysts work as members of a managed sec...
Washington Football Commanders Redskins Feathers Shirt

Washington Football Commanders Redskins Feathers Shirt
HUMANIZE YOUR BRAND - FREE E-WORKBOOK Download Now

HUMANIZE YOUR BRAND - FREE E-WORKBOOK Download Now
Computer networking.word
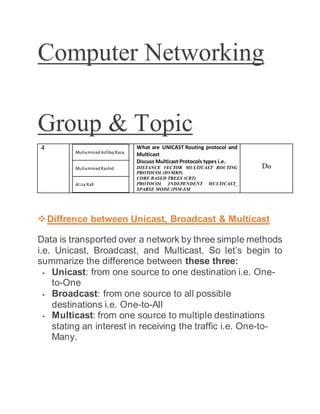
- 1. Computer Networking Group & Topic 4 MuhammadAshfaqRaza MuhammadRashid Aliza Rafi What are UNICAST Routing protocol and Multicast Discuss Multicast Protocols types i.e. DISTANCE VECTOR MULTICAST ROUTING PROTOCOL (DVMRP) CORE BASED TREES (CBT) PROTOCOL INDEPENDENT MULTICAST_ SPARSE MODE (PIM-SM Do Diffrence between Unicast, Broadcast & Multicast Data is transported over a network by three simple methods i.e. Unicast, Broadcast, and Multicast. So let’s begin to summarize the difference between these three: Unicast: from one source to one destination i.e. One- to-One Broadcast: from one source to all possible destinations i.e. One-to-All Multicast: from one source to multiple destinations stating an interest in receiving the traffic i.e. One-to- Many.
- 2. So let’s Dig Deeper into this subject Unicast: traffic, many streams of IP packets that move across networks flow from a single point, such as a website server, to a single endpoint such as a client PC. This is the most common form of information transference on networks. Broadcast: Here, traffic streams from a single point to all possible endpoints within reach on the network, which is generally a LAN. This is the easiest technique to ensure traffic reaches to its destinations. This mode is mainly utilized by television networks for video and audio distribution. Even if the television network is a cable television (CATV) system, the source signal reaches to all possible destinations, which is the key reason that some channels’ content is scrambled Multicast: In this method traffic recline between the boundaries of unicast (one point to one destination) and broadcast (one point to all destinations). And multicast is a “one source to many destinations” way of traffic distribution, means that only the destinations that openly point to their requisite to accept the data from a specific source to receive the traffic stream.
- 3. Unicastrouting Protocol unicast routing protocols. introduction. an internet is a combination of networks connected by routers. when a datagram goes from a source to a destination, it will probably pass through many routers until it reaches the router attached to the destination network. intra- and inter-domain routing today, an internet can be so large that one routing protocolcannot handle the task of updating the routing tables of all routers. for this reason, an internet is divided into autonomous systems. an autonomous system (as) is a group of networks and routers under the authority of a single administration. routing inside an autonomous system is referred to as intra-domain routing. routing between autonomous systems is referred to as inter-domain routing. each autonomous system can chooseone or more intradomain routing protocols to handle routing inside the autonomous system. however, only one interdomain routing protocol handles routing between autonomous systems. Multicast Routing Protocol The routing Algorithm used multicast routing. A single router in a network can be a part of two or more different Groups. Spanning Tree Minimize the Number of edges and un necessary edges are removed in network.
- 4. Example of Spanning Tree Prunning the Spanning Tree Seprate the group of multicasting the are router contain…and make the individual network is called pruning the spanning tree…
- 5. Techniques of Pruning the Spanning Tree Algorithms used for pruning Link State Routing Protocol used for this technique is MOSPF (Multicast Open shortest path first) Distance Vector Routing protocol used for this technique is DVMRP (Distance vector Multicast routing protocol)
- 6. Distance Vector Multicast Routing It’s a Adapted or Dynamic Algorithms. Each router maintaintables called“vector”. Each router is known best Distanceto reach another router. Table are Updatedor exchanging information with neighbor's(router). Also known as Bellman-fordalgorithms. Distanceis basicallyconsiderby No’s of hops. Or Delay etc….. Example… Step1
- 7. Step2 Step3