This document discusses how to hack proof a Drupal site. It covers common security strategies like permissions and software updates. It then details specific vulnerabilities like SQL injection, cross-site scripting, cross-site request forgery, node access bypass, and improper use of drupal_goto. For each vulnerability, it provides an example of an exploit and the proper way to prevent that exploit. It concludes with recommendations on security modules, references, and recovery strategies.






![SQL Injection
Attacker can supply messy parameters passed.
SQL injection:
<?php
db_query("SELECT uid FROM {users} u WHERE u.name =
'" . $_GET['user'] . "'");
?>
QED42](https://image.slidesharecdn.com/dcm-2015-150206232941-conversion-gate02/85/Hack-Proof-Your-Drupal-Site-7-320.jpg)

![<?php
db_query("SELECT uid FROM {users} u WHERE u.name = :
name",
array(':name' => $_GET['user']));
OR
db_select('users', 'u')
->fields('u', array('uid'))
->condition('u.name', $_GET['user'])
->execute();
?>
QED42
SQL Injection -Correct Usage](https://image.slidesharecdn.com/dcm-2015-150206232941-conversion-gate02/85/Hack-Proof-Your-Drupal-Site-9-320.jpg)



![Cross-site Request Forgery(CSRF)
function pizza_menu() {
$items['admin/pizza/%/delete'] = array(
'title' => 'Pizza',
'description' => 'Delete the pizza.',
'page callback' => 'pizza_delete',
'access arguments' => array('administer pizza'),
'file' => 'pizza.admin.inc',
);
function pizza_delete() {
$nid = arg(2);
node_delete($nid);
cache_clear_all();
drupal_goto('admin/pizza');
} QED42](https://image.slidesharecdn.com/dcm-2015-150206232941-conversion-gate02/85/Hack-Proof-Your-Drupal-Site-14-320.jpg)





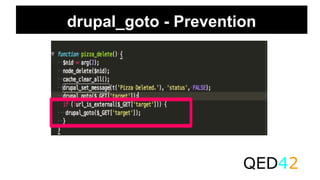
![Correct Usage of drupal_goto
● We usually use the drupal_goto to redirect the
user to some other page.This does a 30X
redirect .We usually suggest to use $form
[‘redirect’] in the forms instead of drupal_goto.
● Incorrect usage of drupal_goto leads to Open
Redirect
QED42](https://image.slidesharecdn.com/dcm-2015-150206232941-conversion-gate02/85/Hack-Proof-Your-Drupal-Site-21-320.jpg)