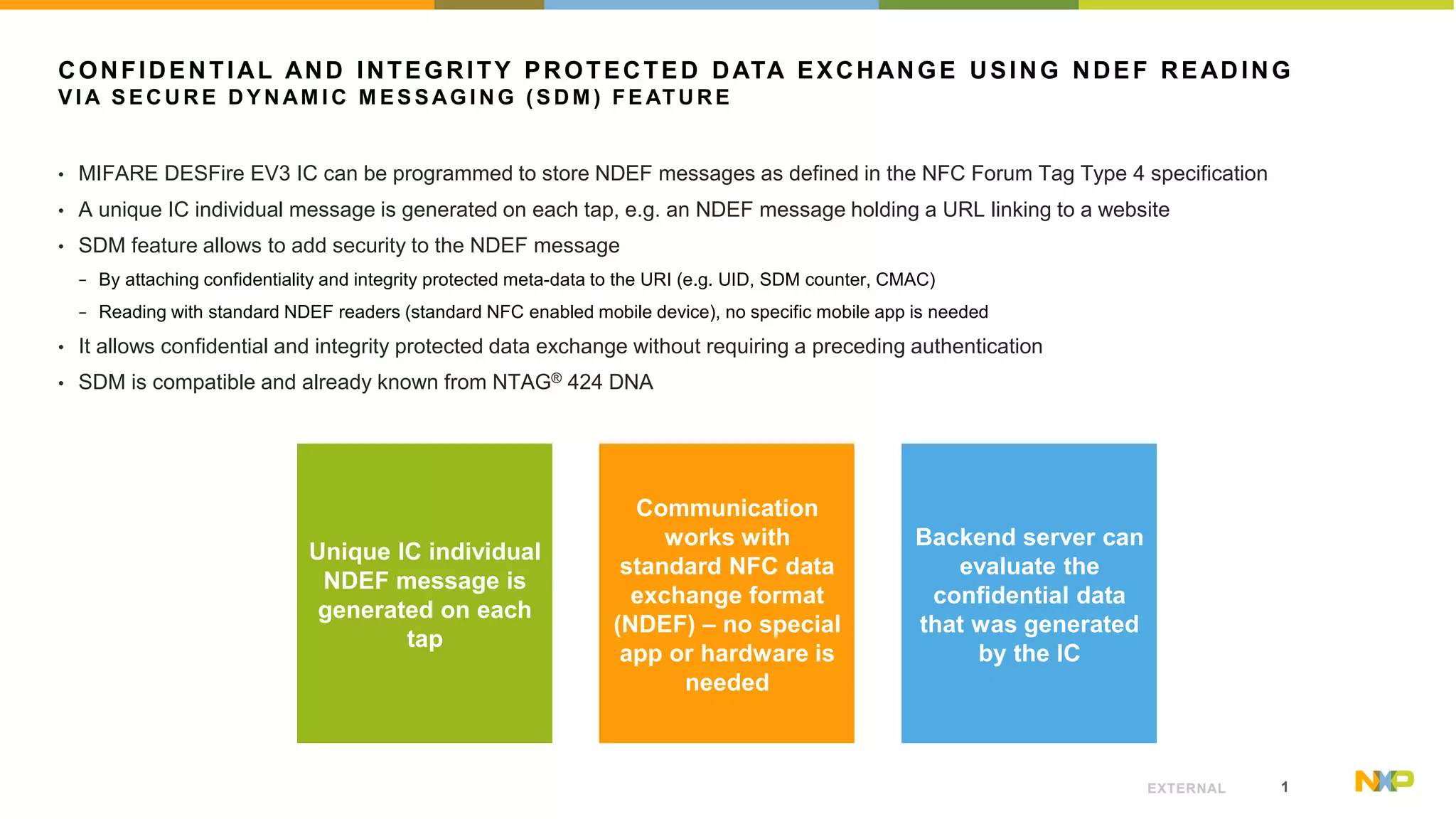
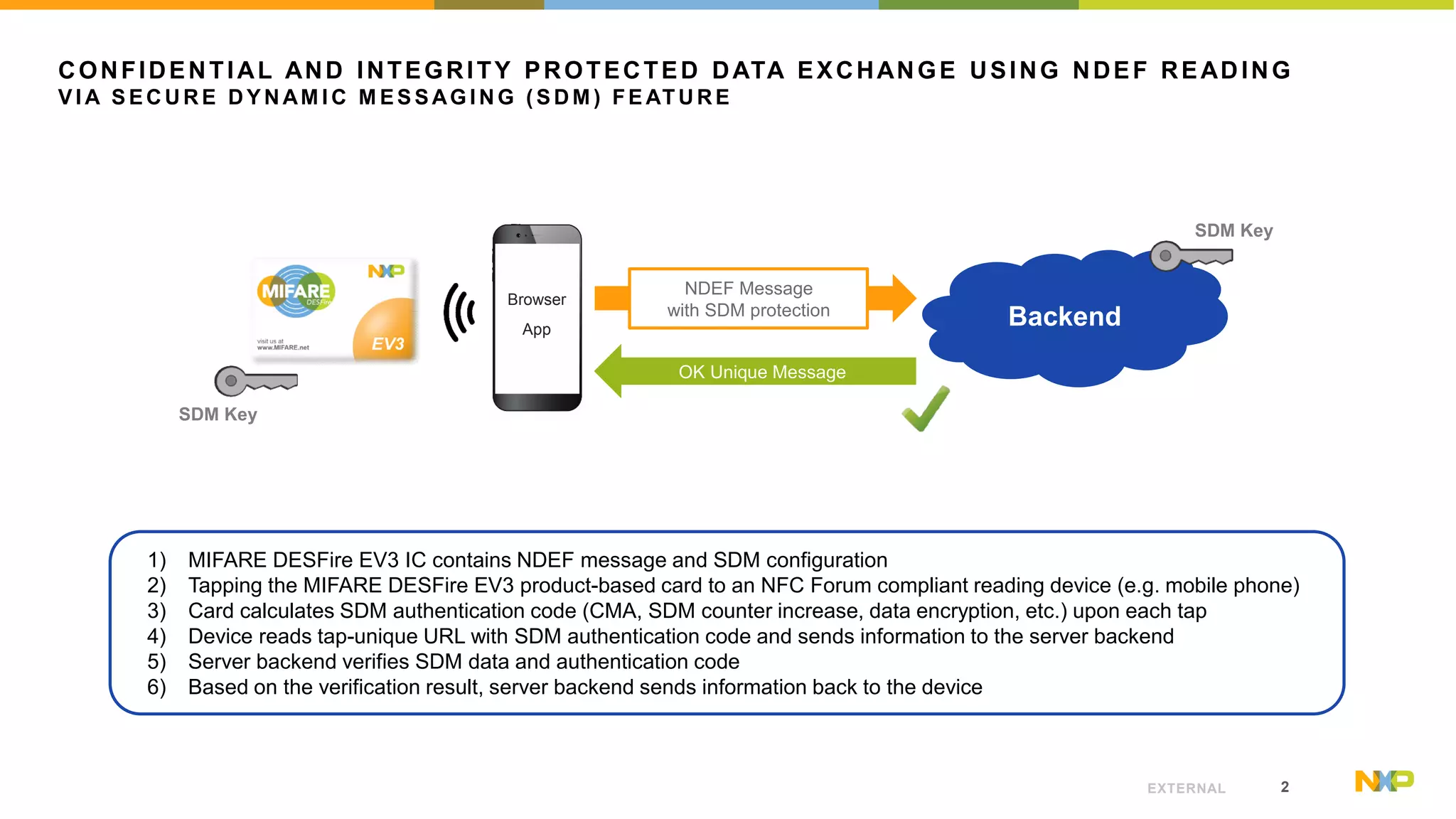
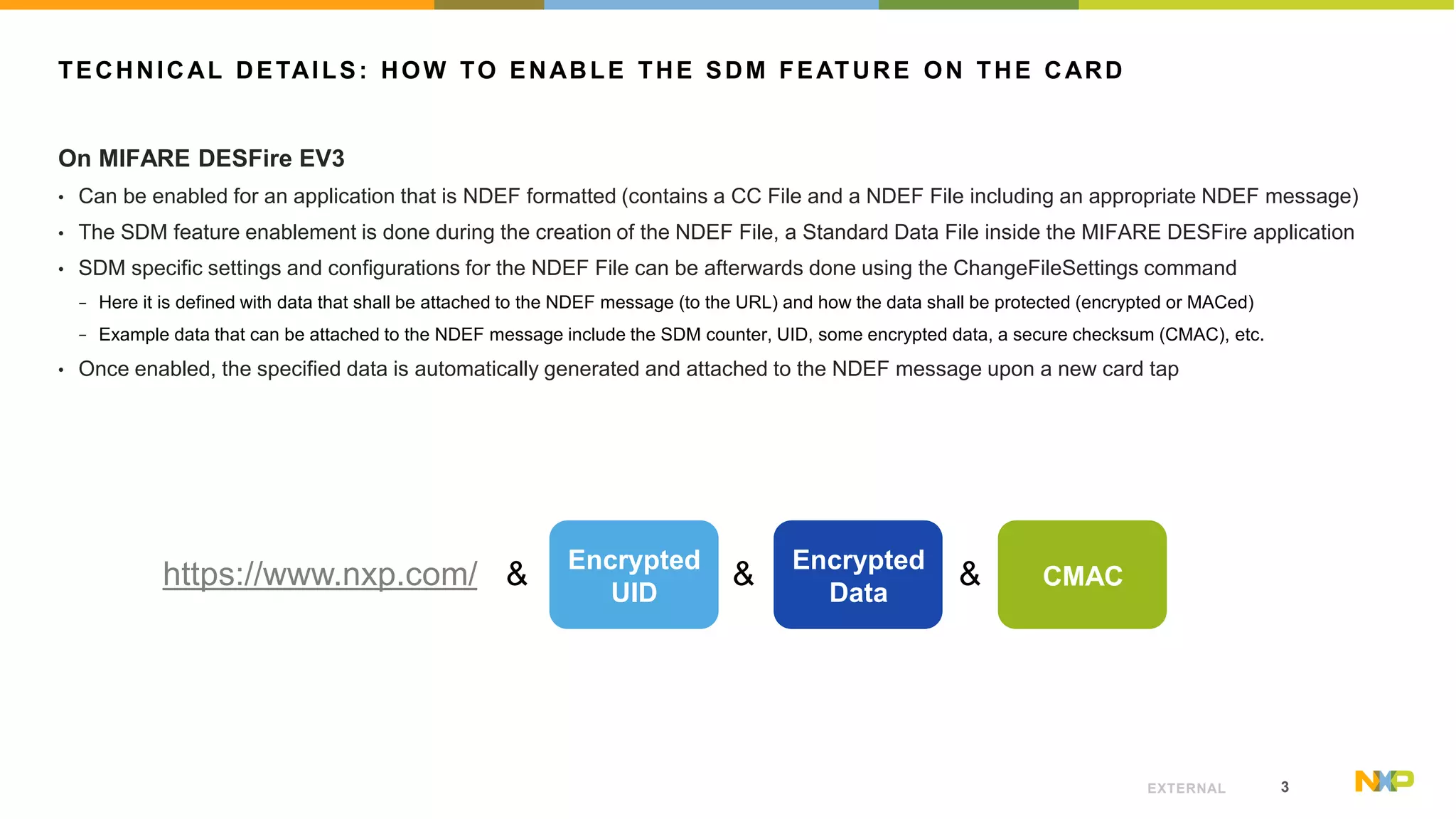
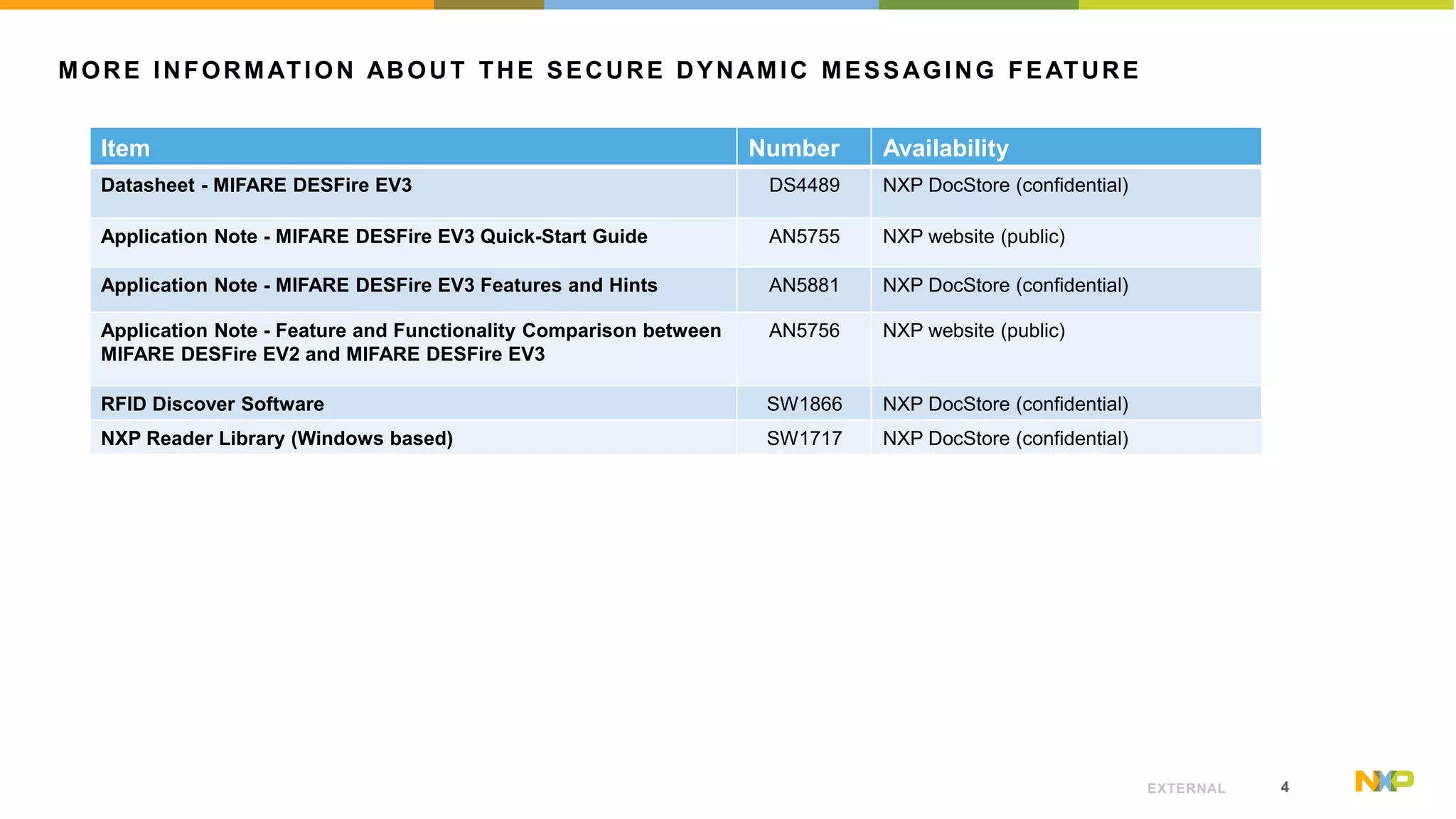
The document outlines the features of the MIFARE DESFire EV3, specifically focusing on its Secure Dynamic Messaging (SDM) capabilities, which enable secure and confidential data exchange using NDEF messages. Each interaction with the card generates a unique message, allowing data to be protected without requiring prior authentication. Technical details for implementing the SDM feature are provided, along with links to further resources and application notes.