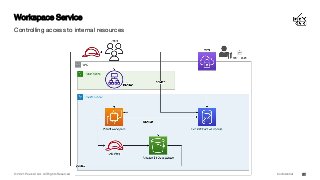
Securing Cloud Infrastructure and applications - concepts and popular services for managing traffic, detecting and preventing threats.
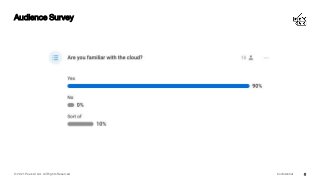
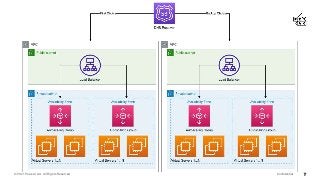
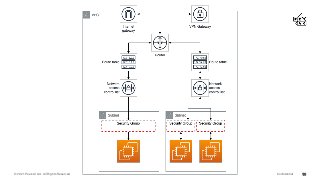
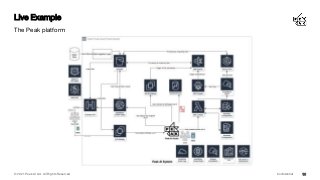
The cloud enables us to create enterprise grade infrastructure that is scalable, highly available and fault tolerant, often deployed across multiple regions - this needs to be secured with tools and services such as web application firewalls (WAF), intrusion detection systems (IDS), intrusion prevention systems (IPS), DDoS protection, and economic denial of service/sustainability (EDoS) to ensure our data stays private and secure.