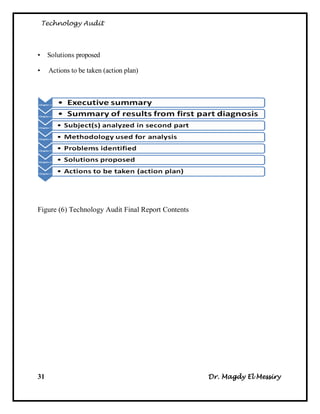
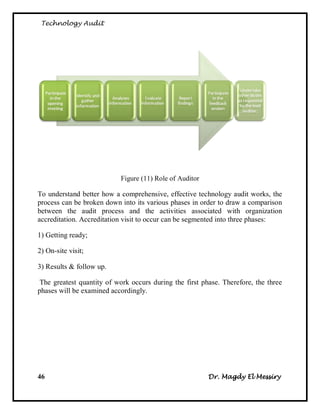
The document provides an overview of technology auditing and internal auditing processes. It discusses:
1. The objectives and composition of technology audits, which identify potential issues, assess capabilities, and optimize technology use.
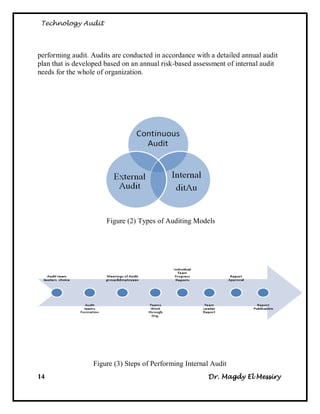
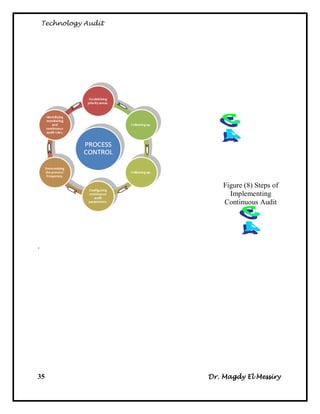
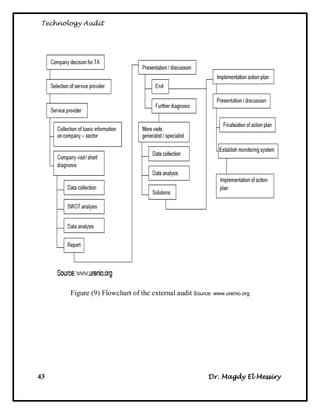
2. The types of audits - internal audits assess processes, external audits are implemented by external parties, and continuous auditing is ongoing.
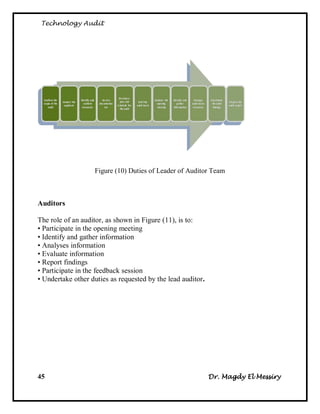
3. The steps for internal audits, which include developing audit strategies, planning specific audits, conducting audits, communicating results, and advising on improvements.




















































































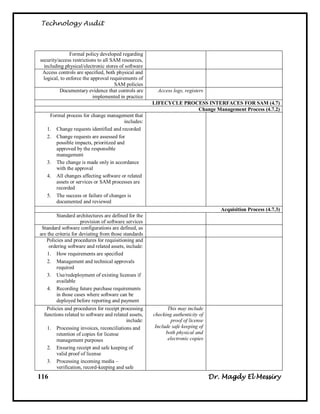
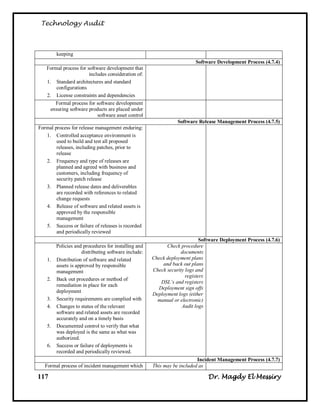
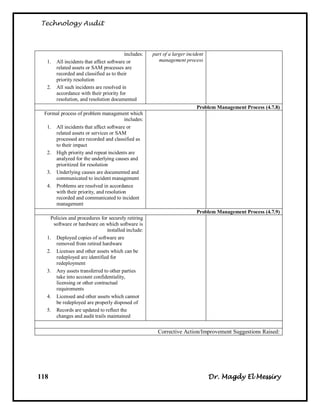




![Technology Audit
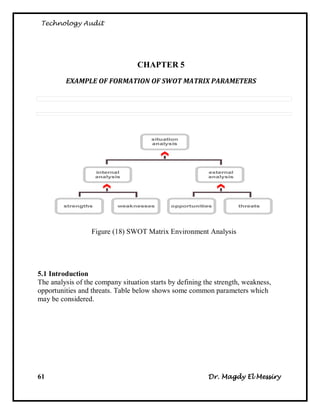
Appendix V
Information Technology Audit Report
Alpha Beta Gama (ABC) Co Ltd
Internal Audit Group Division 2009
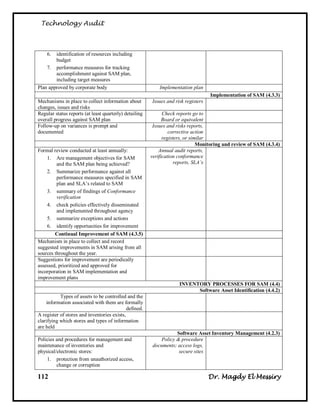
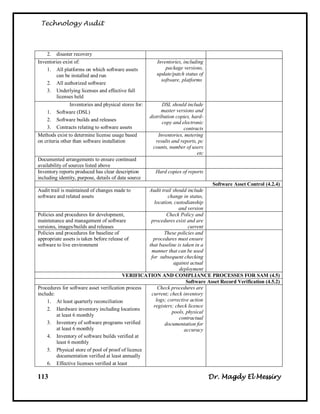
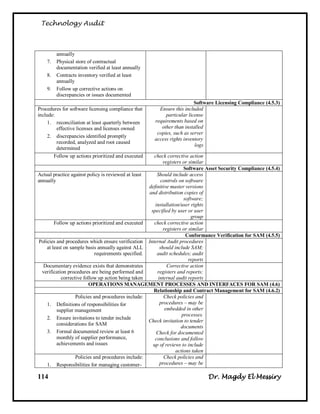
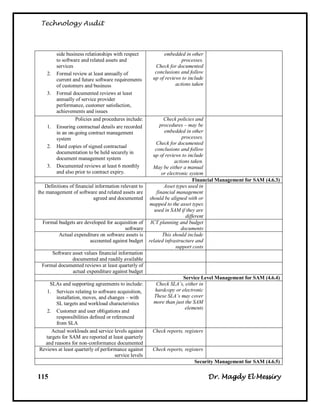
Audit Objectives:
To assess [Name of Company] compliance with the [Name of Standard] Standard
Overall conclusion:
Based on our observation we noted that the degree of compliance with [Name of
Standard] varied among [Name of Company] and the three Institutes that we
looked at. With the exception of business continuity planning, [Name of Company]
is compliant with [Name of Standard]. However, the three Institutes were less
compliant in key areas such as risk management and the certification and
accreditation of their systems.
Summary of Findings:
The audit team noted a number of strengths with respect to compliance with [Name
of Standard]. For example, [Name of Company] has specified the roles and
responsibilities for managing IT security. It has also issued a comprehensive set of
policies, procedures and standards for managing this function and instituted a
security-awareness program for its employees. [Name of Company] screens staff to
determine who will have access to which sensitive information, and has employed
security zones. These zones partition the network and provide higher levels of
security, depending on the sensitivity of information.
Detailed Findings and Remediation:
Recommendation:
To institute better monitoring and oversight of IT security, [Name of Company]'s
senior management should designate an IT Security Coordinator for [Name of
Company] who has responsibility and authority for IT security throughout the
organization.
Management Response:
Agreed; an IT Security Coordinator for [Name of Company] with organization-
wide responsibility and authority for IT security will be appointed following
consultation with the Senior Executive Committee (SEC). However, such a role
will need to be supported by a strong IM/IT governance structure in general and a
robust information security governance framework in articular. IM/IT governance
123 Dr. Magdy El Messiry](https://image.slidesharecdn.com/technologyauditbymagdyelmessiry-130410144619-phpapp01/85/Technology-audit-by-Magdy-El-messiry-123-320.jpg)
![Technology Audit
will be addressed as part of a study that [Name of Company] has already initiated –
a comprehensive IM/IT review to examine the current IT service delivery model
and determine how [Name of Company] can enhance effectiveness and cost-
efficiencies in this area. More specifically, the study will be broad in scope,
encompassing all IM/IT services provided to [Name of Company] staff either
centrally by IMSB or locally by individual institutes, branches and programs.
Terms of Reference have been developed and approved by SEC; the Director
General for IMSB will co-lead this effort along with a Director General from a
research institute still to be determined. The issues around IT service delivery will
be examined and reported back to SEC by January 2008. Specific areas of
opportunity or concern will also be identified for further study in a subsequent
phase. It is anticipated that most of the audit recommendations will be addressed
within the context of this review.
Timelines and Deliverables:
124 Dr. Magdy El Messiry](https://image.slidesharecdn.com/technologyauditbymagdyelmessiry-130410144619-phpapp01/85/Technology-audit-by-Magdy-El-messiry-124-320.jpg)