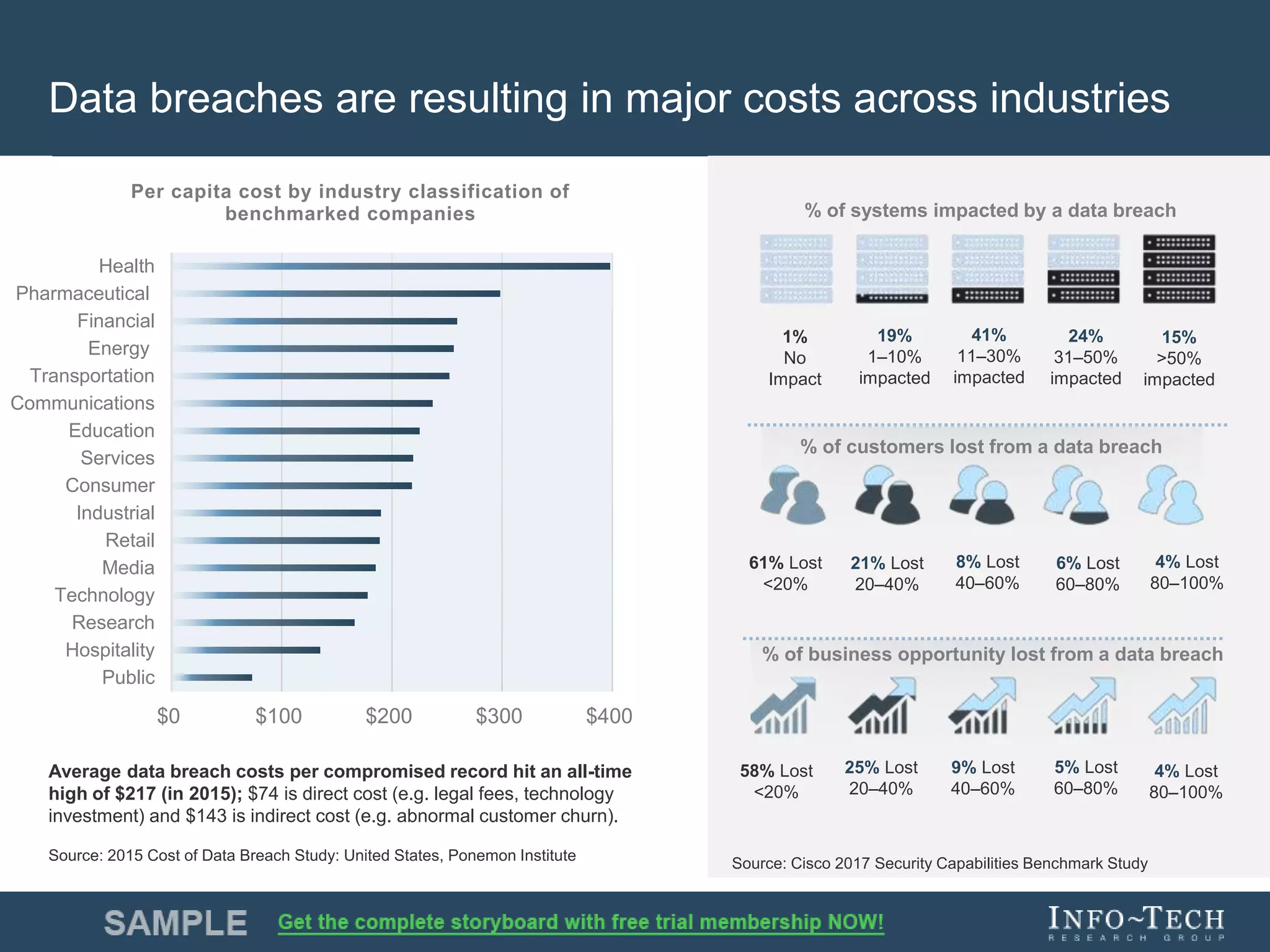
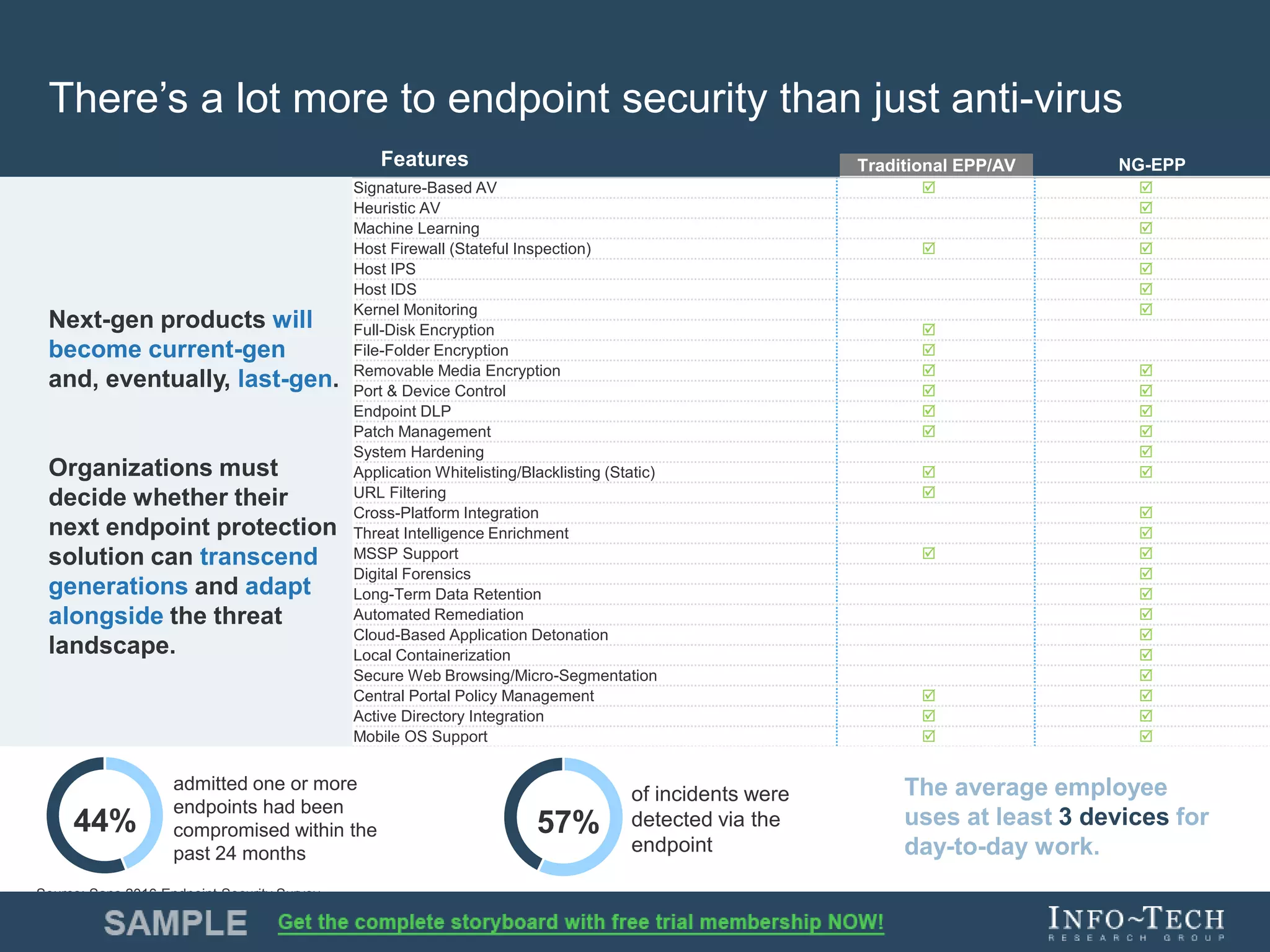
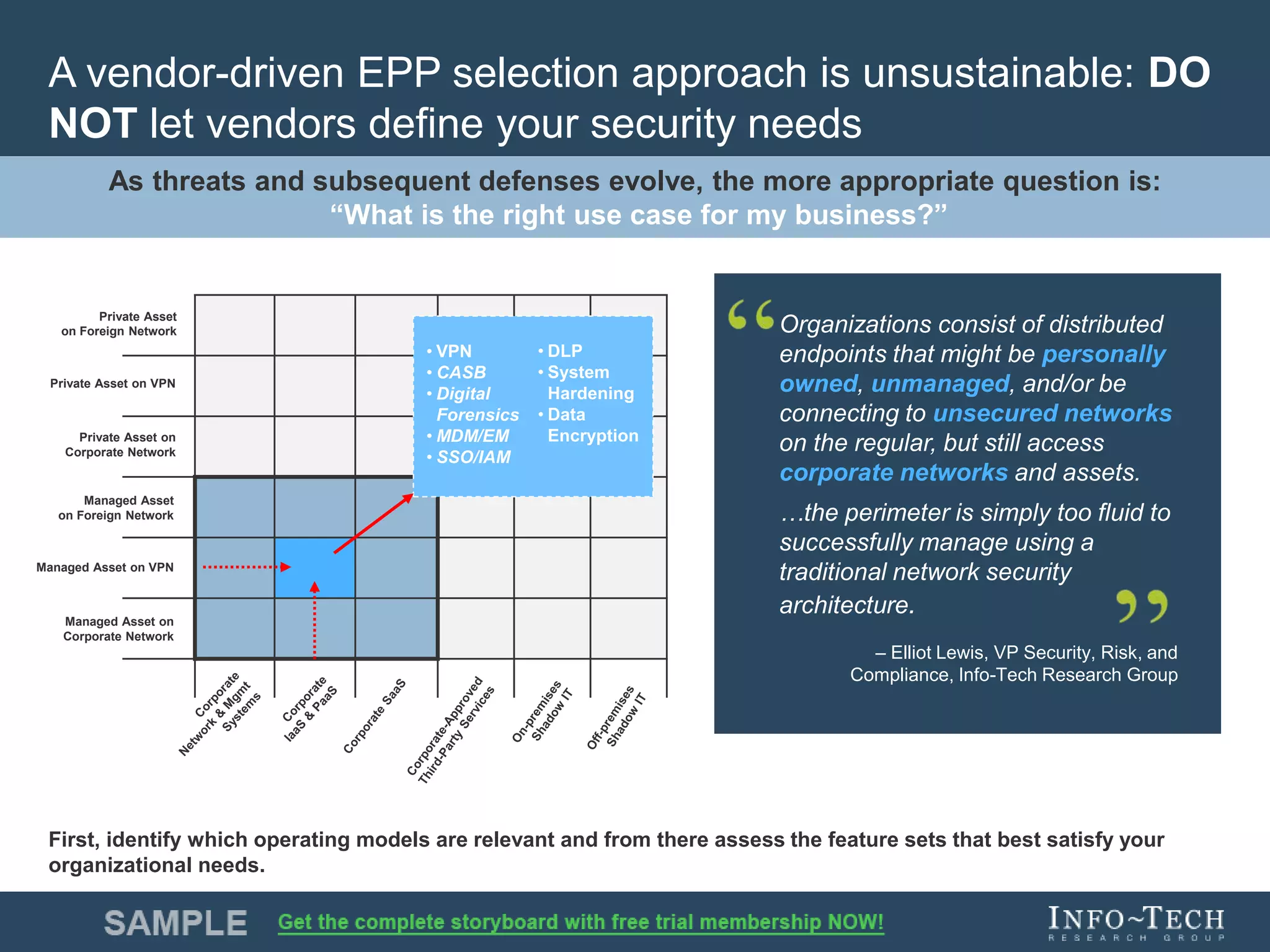
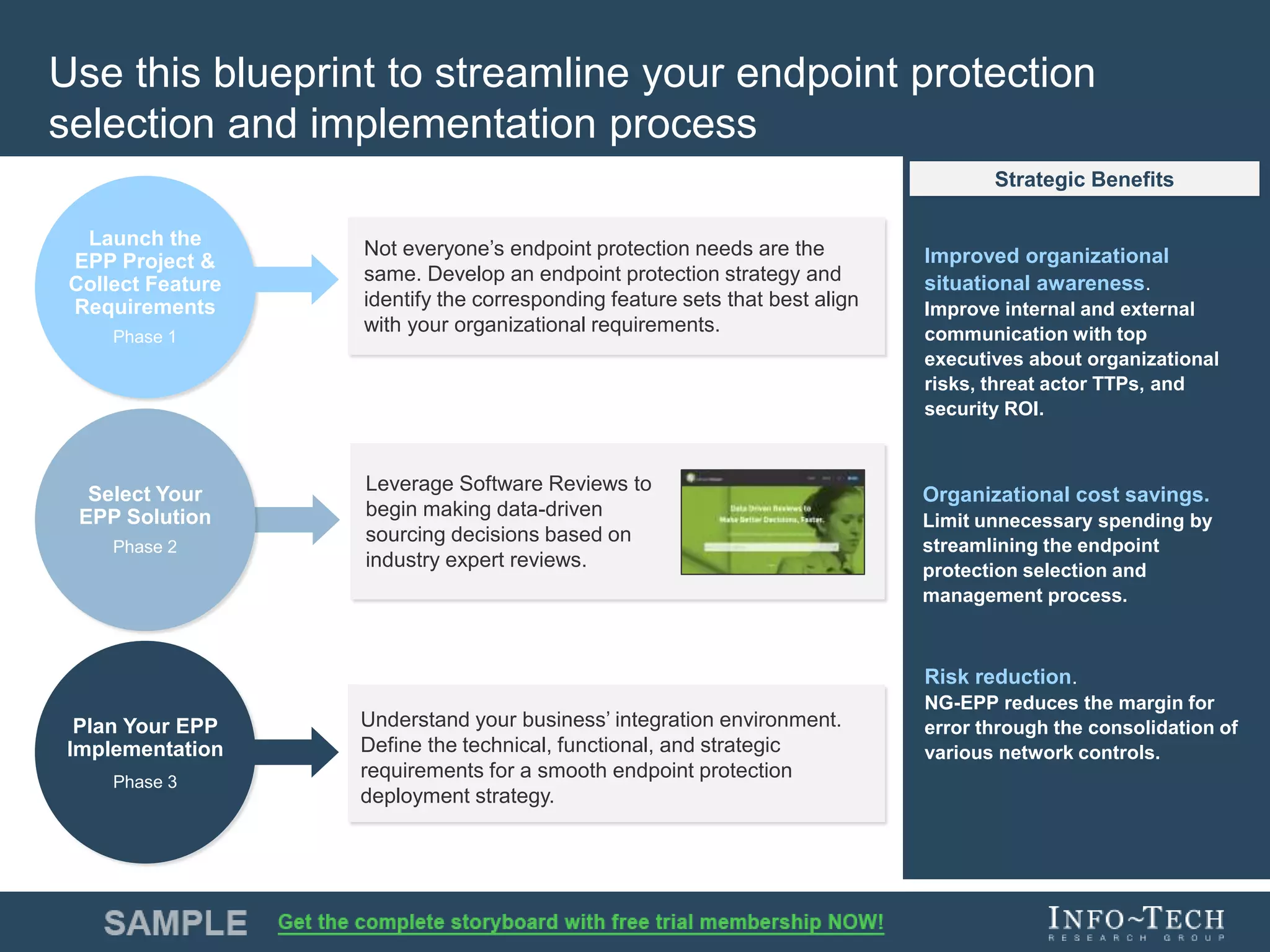
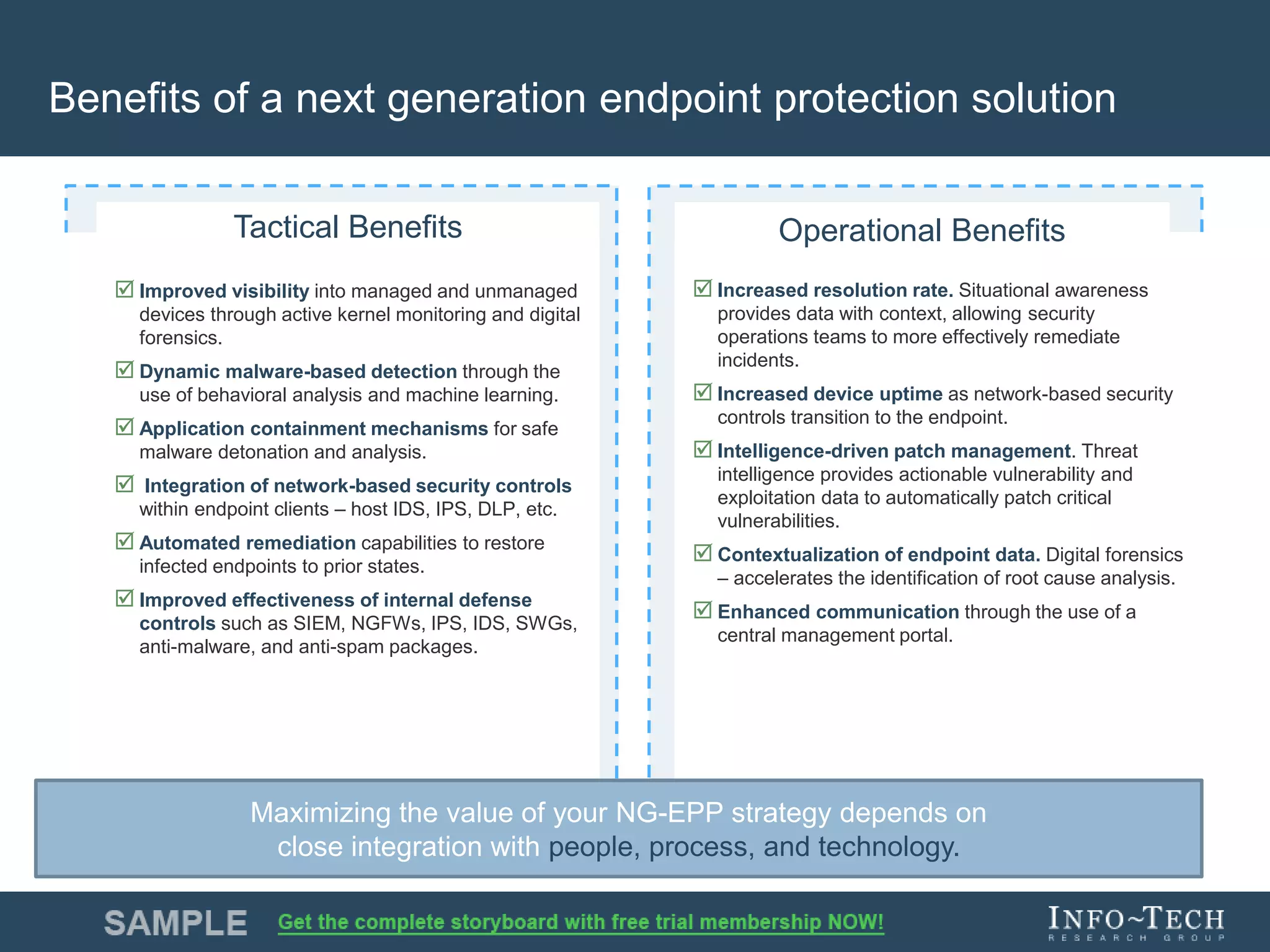
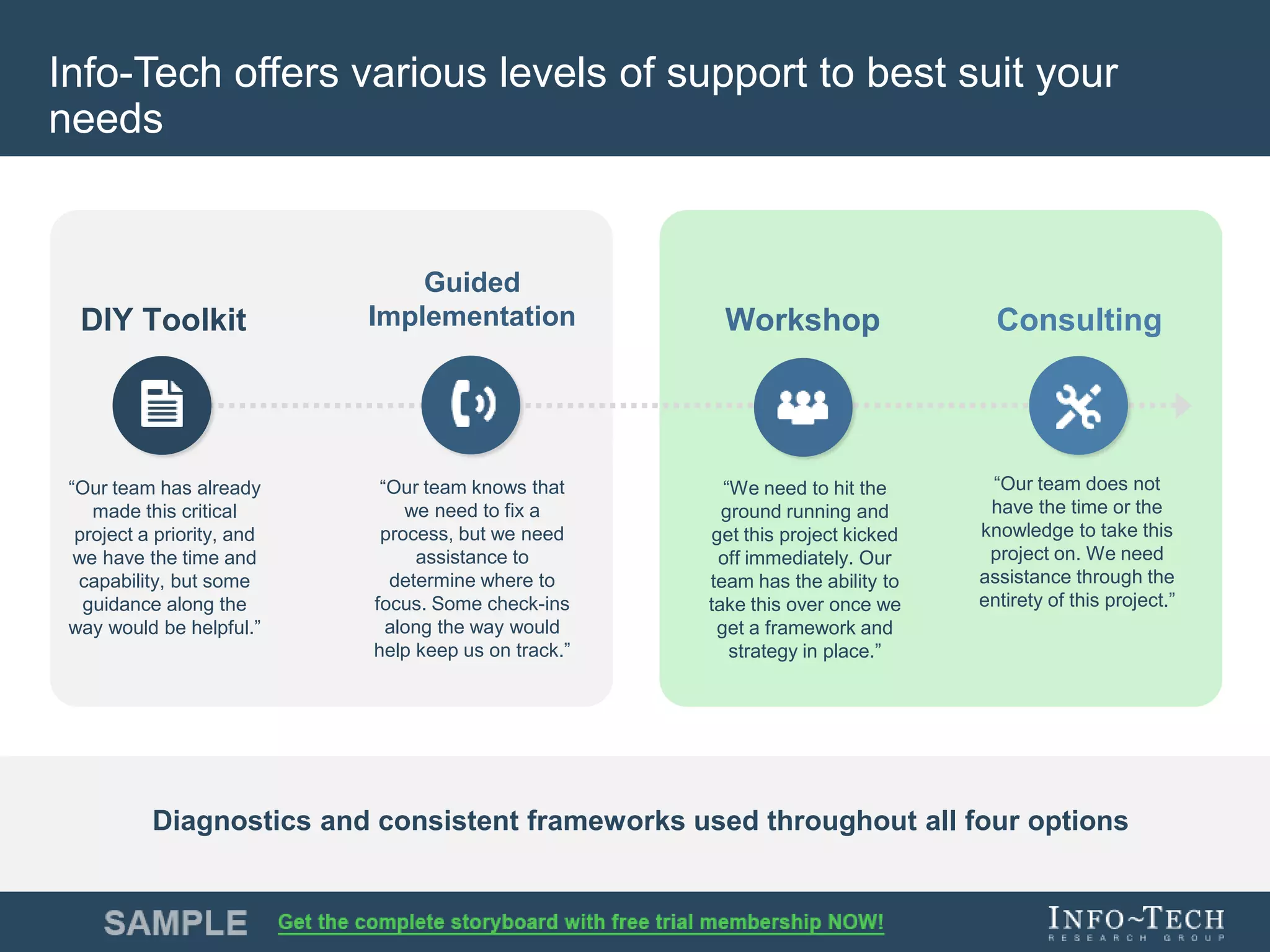
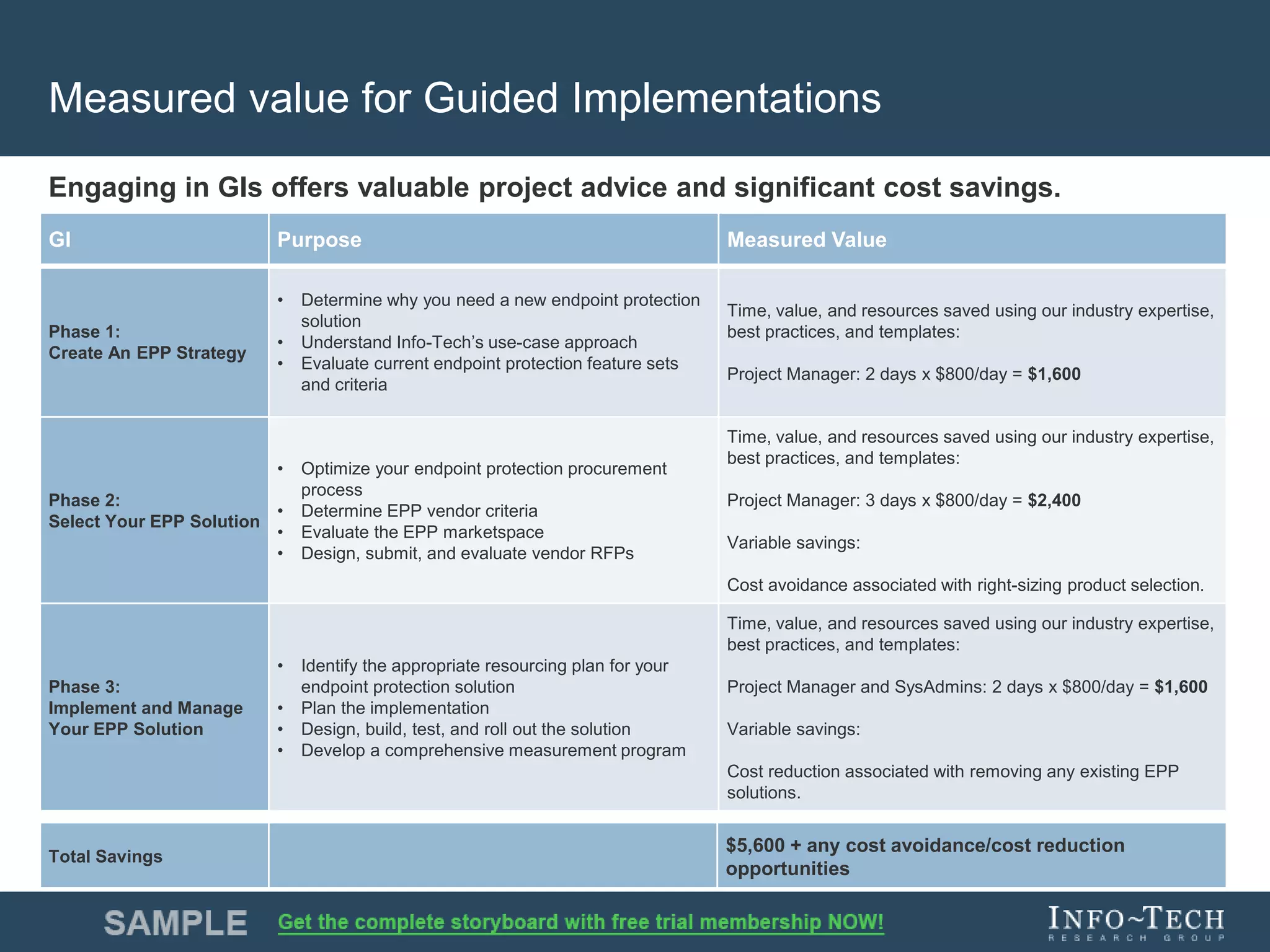
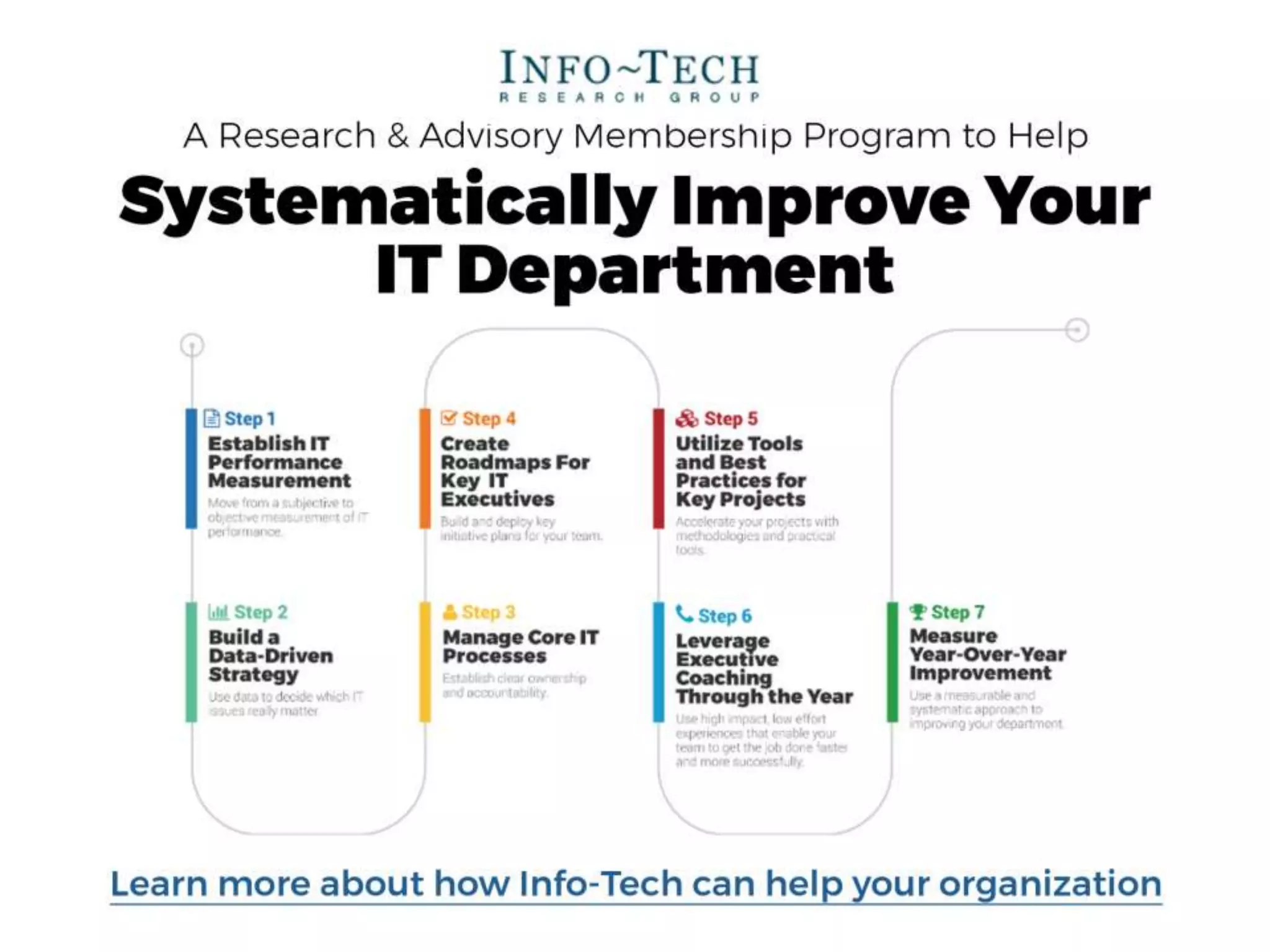
Info-Tech Research Group provides insights and resources for IT professionals to select and implement next-generation endpoint protection solutions amidst evolving cybersecurity threats. The document highlights the challenges in the overcrowded endpoint protection market and outlines a comprehensive strategy for assessing organizational needs, vendor evaluation, and implementation. It emphasizes the importance of proactive measures and tailored solutions to effectively address modern protection challenges while enhancing situational awareness and compliance.