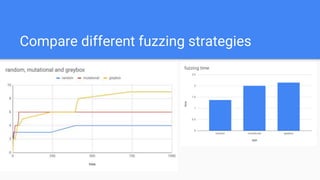
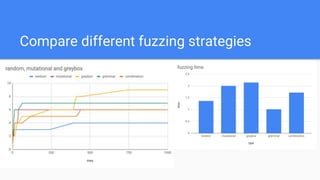
This document introduces different types of fuzzing techniques. It discusses generational fuzzing which generates completely random inputs and is good for detecting parser errors but difficult to generate meaningful inputs. Mutational fuzzing generates inputs by adding random mutations to seed inputs, which can produce more interesting inputs. Coverage-based mutational fuzzing, also called greybox fuzzing, uses code coverage to leverage interesting inputs. Grammar-based fuzzing generates inputs based on grammars defined in formats like BNF to create more structured inputs. Greybox grammar fuzzing combines grammar-based seed generation with mutation and coverage-based selection. Overall, coverage-based techniques are very effective for testing mature applications, while grammars can improve input variety.