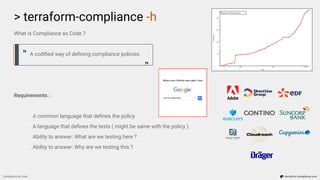
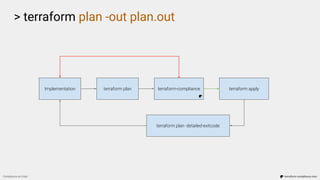
The document discusses 'compliance as code' using Terraform, outlining the importance of codifying compliance policies, requirements for testing, and implementation strategies. It highlights the behavior-driven development (BDD) approach applied to Terraform-compliance tests, which defines scenarios and conditions to enforce compliance with a focus on idempotency and immutability. Additionally, the text emphasizes the necessity of a collaborative workflow in infrastructure management, promoting regular feedback and quick resolution of compliance failures.

![> cat who_is_this_person.tf
resource “human_person” “me” {
name = “Emre Erkunt”
interests {
professional = [“DevOps”, “DevSecOps”, “Security”, “Automation”]
personal = [“Astrophotography”, “Aikido”, “Guitar”, “Apnea Diving”, “Gaming”]
}
recent_focus = [
“terraform”, “terraform-compliance”, “aws”, “tons of aws”, “serverless”,
“pipelines”, “cultural change”, “new ways of working”, “agile”, “#nobuzzwords”
]
twitter = “@3rkunt”
linkedin = “only person with this name and surname”
}
Compliance as Code terraform-compliance.com](https://image.slidesharecdn.com/terraform-compliance-200219093013/85/Compliance-as-Code-with-terraform-compliance-2-320.jpg)




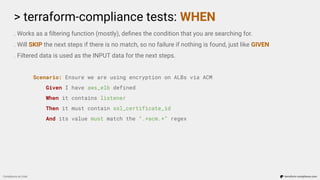
![> terraform-compliance tests: WHEN
Compliance as Code terraform-compliance.com
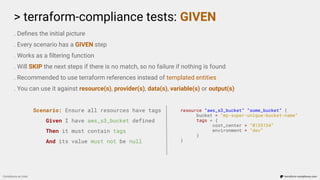
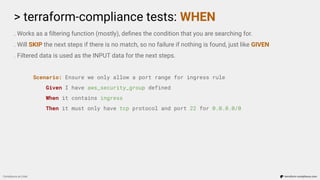
. Works as a filtering function (mostly), defines the condition that you are searching for.
. Will SKIP the next steps if there is no match, so no failure if nothing is found, just like GIVEN
. Filtered data is used as the INPUT data for the next steps.
Scenario: Ensure we only allow a port range for ingress rule
Given I have aws_security_group defined
When it contains ingress
Then it must only have tcp protocol and port 22 for 0.0.0.0/0
resource “aws_security_group” “some_group” {
name = “allow_ssh_publicly_because_we_are_just_crazy”
ingress {
from_port = 22
to_port = 22
protocol = “tcp”
cidr_blocks = [“0.0.0.0/0”]
}
}](https://image.slidesharecdn.com/terraform-compliance-200219093013/85/Compliance-as-Code-with-terraform-compliance-17-320.jpg)
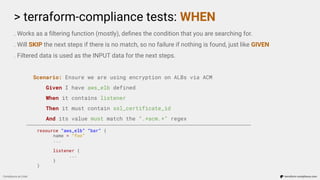
![> terraform-compliance tests: WHEN
Compliance as Code terraform-compliance.com
. Works as a filtering function (mostly), defines the condition that you are searching for.
. Will SKIP the next steps if there is no match, so no failure if nothing is found, just like GIVEN
. Filtered data is used as the INPUT data for the next steps.
Scenario: Ensure we only allow a port range for ingress rule
Given I have aws_security_group defined
When it contains ingress
Then it must only have tcp protocol and port 22 for 0.0.0.0/0
resource “aws_security_group_rule” “port_22_to_public” {
type = “ingress”
from_port = 22
to_port = 22
protocol = “tcp”
cidr_blocks = [“0.0.0.0/0”]
security_group_id = aws_security_group.some_group.id
}](https://image.slidesharecdn.com/terraform-compliance-200219093013/85/Compliance-as-Code-with-terraform-compliance-18-320.jpg)
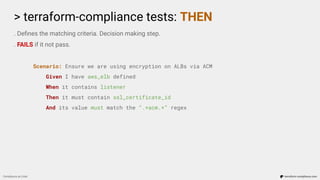

![> terraform-compliance tests: THEN
Compliance as Code terraform-compliance.com
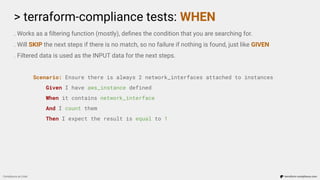
. Defines the matching criteria. Decision making step.
. FAILS if it not pass.
Scenario: Ensure we only allow a port range for ingress rule
Given I have aws_security_group defined
When it contains ingress
Then it must only have tcp protocol and port 22 for 0.0.0.0/0
resource “aws_security_group_rule” “port_22_to_public” {
type = “ingress”
from_port = 22
to_port = 22
protocol = “tcp”
cidr_blocks = [“0.0.0.0/0”]
security_group_id = aws_security_group.some_group.id
}](https://image.slidesharecdn.com/terraform-compliance-200219093013/85/Compliance-as-Code-with-terraform-compliance-26-320.jpg)

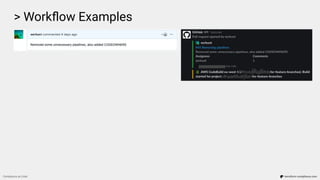
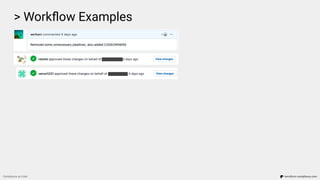
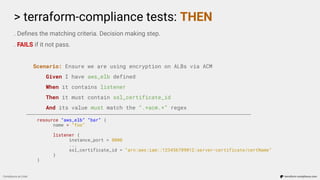
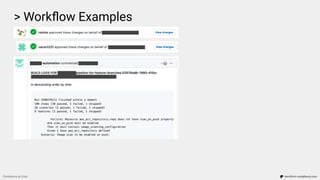
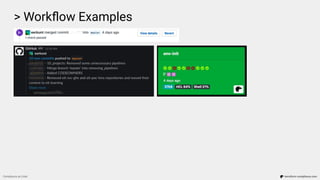
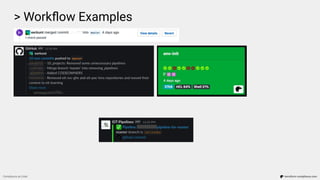
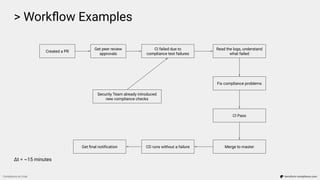
![> Workflow Examples
Compliance as Code terraform-compliance.com
...
Scenario: Image scan to be enabled on push.
Given I have aws_ecr_repository defined
Then it must contain image_scanning_configuration
And scan_on_push must be enabled
Failure: Resource aws_ecr_repository.repo does not have scan_on_push property enabled
(scan_on_push=None)
[Container] 2020/02/13 11:48:40 Phase complete: BUILD State: FAILED](https://image.slidesharecdn.com/terraform-compliance-200219093013/85/Compliance-as-Code-with-terraform-compliance-30-320.jpg)






![> cat who_is_this_person.tf
resource “human_person” “me” {
name = “Emre Erkunt”
interests {
professional = [“DevOps”, “DevSecOps”, “Security”, “Automation”]
personal = [“Astrophotography”, “Aikido”, “Guitar”, “Apnea Diving”, “Gaming”]
}
recent_focus = [
“terraform”, “terraform-compliance”, “aws”, “tons of aws”, “serverless”,
“pipelines”, “cultural change”, “new ways of working”, “agile”, “#nobuzzwords”
]
twitter = “@3rkunt”
linkedin = “only person with this name and surname”
}
Compliance as Code terraform-compliance.com](https://image.slidesharecdn.com/terraform-compliance-200219093013/85/Compliance-as-Code-with-terraform-compliance-43-320.jpg)