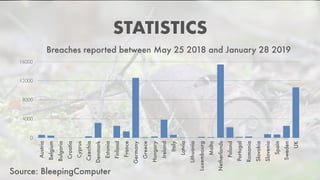
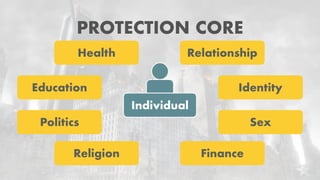
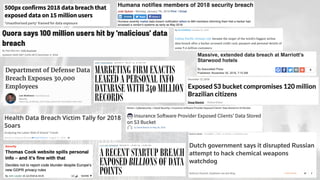
The document reflects on the first six months of the GDPR's implementation in the EU, highlighting ongoing issues such as insufficient staff at data protection authorities and continued corporate non-compliance. It notes significant data breaches affecting major companies, raising concerns about the effectiveness of GDPR protections. The author emphasizes the importance of 'privacy by design' and the shared responsibility of developers to ensure data security.