Report
Share
Download to read offline
Recommended
Recommended
iOS Threats - Malicious Configuration Profiles, Threat, Detection & Mitigation

iOS Threats - Malicious Configuration Profiles, Threat, Detection & MitigationLacoon Mobile Security
More Related Content
What's hot
iOS Threats - Malicious Configuration Profiles, Threat, Detection & Mitigation

iOS Threats - Malicious Configuration Profiles, Threat, Detection & MitigationLacoon Mobile Security
What's hot (20)
CIS14: Protecting Your APIs from Threats and Hacks

CIS14: Protecting Your APIs from Threats and Hacks
iOS Threats - Malicious Configuration Profiles, Threat, Detection & Mitigation

iOS Threats - Malicious Configuration Profiles, Threat, Detection & Mitigation
Android in the healthcare workplace - GrrCON and DerbyCON

Android in the healthcare workplace - GrrCON and DerbyCON
The Ultimate Security Checklist Before Launching Your Android App

The Ultimate Security Checklist Before Launching Your Android App
Llevando la autenticación de sus clientes a un siguiente nivel

Llevando la autenticación de sus clientes a un siguiente nivel
Security Testing: 8 Key Roles in Healthcare Applications

Security Testing: 8 Key Roles in Healthcare Applications
Android security a survey of issues, malware penetration, and defenses

Android security a survey of issues, malware penetration, and defenses
Similar to How To Protect Mobile Apps and APIs from Attackers
Similar to How To Protect Mobile Apps and APIs from Attackers (20)
Mobile Application Security: Safeguarding Apps in the Digital Age

Mobile Application Security: Safeguarding Apps in the Digital Age
Keep Up with the Demands of IT Security on a Nonprofit Budget

Keep Up with the Demands of IT Security on a Nonprofit Budget
Trylogic- Cyber security by Vikalp Sharma- FDP Presentation July 9 2020

Trylogic- Cyber security by Vikalp Sharma- FDP Presentation July 9 2020
Безопасность данных мобильных приложений. Мифы и реальность.

Безопасность данных мобильных приложений. Мифы и реальность.
Secure your app against DDOS, API Abuse, Hijacking, and Fraud

Secure your app against DDOS, API Abuse, Hijacking, and Fraud
F5 on AWS: How MailControl Improved their Application Visbility and Security 

F5 on AWS: How MailControl Improved their Application Visbility and Security
More from Centextech
More from Centextech (20)
Security at the Core: Unraveling Secure by Design Principles

Security at the Core: Unraveling Secure by Design Principles
Cybersecurity Incident Management for Small and Medium-sized Businesses

Cybersecurity Incident Management for Small and Medium-sized Businesses
Incident Management for Ransomware Attacks Best Practices for Response and Re...

Incident Management for Ransomware Attacks Best Practices for Response and Re...
10 Essentials Of Effective Cyber Security Strategy

10 Essentials Of Effective Cyber Security Strategy
Recently uploaded
Recently uploaded (20)
Grateful 7 speech thanking everyone that has helped.pdf

Grateful 7 speech thanking everyone that has helped.pdf
The Coffee Bean & Tea Leaf(CBTL), Business strategy case study

The Coffee Bean & Tea Leaf(CBTL), Business strategy case study
Lucknow 💋 Escorts in Lucknow - 450+ Call Girl Cash Payment 8923113531 Neha Th...

Lucknow 💋 Escorts in Lucknow - 450+ Call Girl Cash Payment 8923113531 Neha Th...
BEST ✨ Call Girls In Indirapuram Ghaziabad ✔️ 9871031762 ✔️ Escorts Service...

BEST ✨ Call Girls In Indirapuram Ghaziabad ✔️ 9871031762 ✔️ Escorts Service...
Cash Payment 9602870969 Escort Service in Udaipur Call Girls

Cash Payment 9602870969 Escort Service in Udaipur Call Girls
VIP Kolkata Call Girl Howrah 👉 8250192130 Available With Room

VIP Kolkata Call Girl Howrah 👉 8250192130 Available With Room
Ensure the security of your HCL environment by applying the Zero Trust princi...

Ensure the security of your HCL environment by applying the Zero Trust princi...
7.pdf This presentation captures many uses and the significance of the number...

7.pdf This presentation captures many uses and the significance of the number...
Call Girls In Panjim North Goa 9971646499 Genuine Service

Call Girls In Panjim North Goa 9971646499 Genuine Service
9599632723 Top Call Girls in Delhi at your Door Step Available 24x7 Delhi

9599632723 Top Call Girls in Delhi at your Door Step Available 24x7 Delhi
Russian Faridabad Call Girls(Badarpur) : ☎ 8168257667, @4999

Russian Faridabad Call Girls(Badarpur) : ☎ 8168257667, @4999
Regression analysis: Simple Linear Regression Multiple Linear Regression

Regression analysis: Simple Linear Regression Multiple Linear Regression
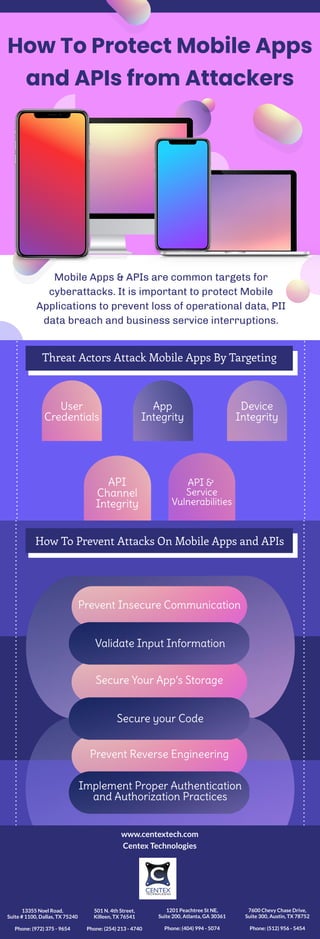
How To Protect Mobile Apps and APIs from Attackers
- 1. Mobile Apps & APIs are common targets for cyberattacks. It is important to protect Mobile Applications to prevent loss of operational data, PII data breach and business service interruptions. How To Protect Mobile Apps and APIs from Attackers Threat Actors Attack Mobile Apps By Targeting Device Integrity App Integrity User Credentials API Channel Integrity API & Service Vulnerabilities Prevent Insecure Communication Validate Input Information Secure Your App’s Storage Secure your Code Prevent Reverse Engineering Implement Proper Authentication and Authorization Practices How To Prevent Attacks On Mobile Apps and APIs www.centextech.com Centex Technologies 13355 Noel Road, Suite # 1100, Dallas, TX 75240 Phone: (972) 375 - 9654 501 N. 4th Street, Killeen, TX 76541 Phone: (254) 213 - 4740 1201 Peachtree St NE, Suite 200, Atlanta, GA 30361 Phone: (404) 994 - 5074 7600 Chevy Chase Drive, Suite 300, Austin, TX 78752 Phone: (512) 956 - 5454