Top5 protectiondomains infographic_final
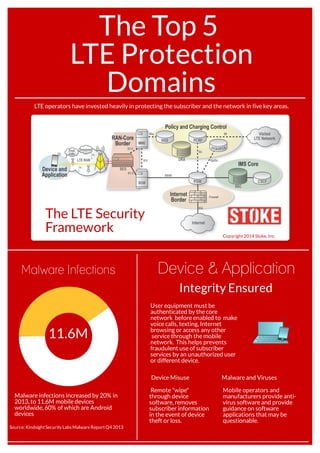
- 1. The Top 5 LTE Protection Domains LTE operators have invested heavily in protecting the subscriber and the network in five key areas. Copyright2014 Stoke, Inc. The LTE Security Framework User equipment must be authenticated by the core network before enabled to make voice calls, texting, Internet browsing or access any other service through the mobile network. This helps prevents fraudulent use of subscriber services by an unauthorized user or different device. Malware infections increased by 20% in 2013, to 11.6M mobile devices worldwide, 60% of which are Android devices Device & Application Integrity Ensured Malware Infections 11.6M Source: KindsightSecurity Labs MalwareReportQ4 2013 Mobile operators and manufacturers provide anti- virus software and provide guidance on software applications that may be questionable. Remote "wipe" through device software, removes subscriber information in the event of device theft or loss. Device Misuse Malware and Viruses
- 2. A security gateway (SEG) provides secure aggregation of traffic and ensures correct authentication of cell sites. RAN-Core Border Malicious Access Averted Intensified Backhaul Risks 53% By 2017, over half of LTE cell sites are forecast to encrypt traffic using IPsec. 60M Small Cells Source: Small Cells Forum, 2016 forecast Small cells are especially vulnerable to hacker interception and spoofing as they are often deployed in less secure locations and connected with untrusted backhaul. Source: Heavy Reading Encrypted The SEG protects core network assets and further ensures subscriber confidentiality. With almost $3 B in projected service revenues, operators must protect premium voice (VoLTE) from malicious intrusion, unauthorized access, and poor quality of experience (QoE). Diameter Routing Agents (DRA) and Session Border Controllers (SBC) support critical core functions. Security gateways protect privacy without adding perceivable latency that would impair voice quality. IMS Core & PCC Vulnerable VoLTE Policy Charging and Control Elements provide secure access to authorized services and accurate billing. IP Multimedia Subsystems enable voice over LTE (VoLTE) and ensure that only authorized sessions are allowed access. Source: Infonetics $2.7 B 2017 VoLTE Service Revenue Authorized Service Use Malicious denial-of-service attacks are more commonly initiated through the Internet, but can enter through an unsecured RAN-Core border or through roaming partner interfaces. Firewalls, IDS and security gateways are deployed to protect against DDoS attacks that can cause widescale service outages or otherwise disrupt service access and quality. DDoS Defense Service Disruption 20% Source: Arbor Networks Internet Border 20 % of mobile operators have had a customer visible outage due to a security incident. 25% have seen DDoS attacks targeting users or network. Denial-of-service attacks cause service outages by flooding the network with so much traffic that a network element is overwhelmed and cannot provide service to legitimate traffic. 25% Copyright2014 Stoke, Inc., All Rights Reserved www.stoke.com
