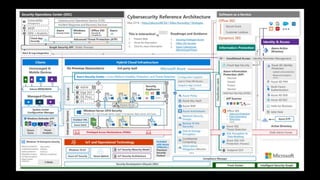
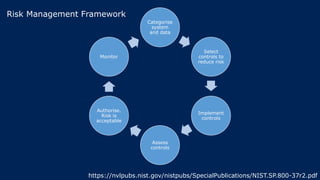
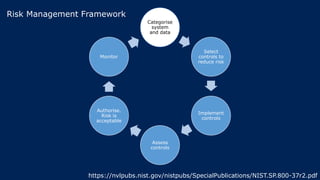
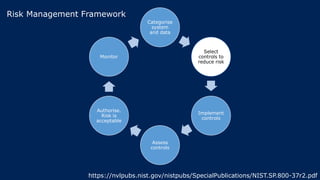
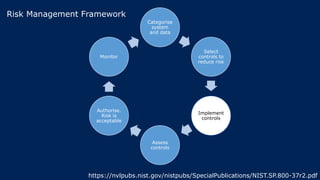
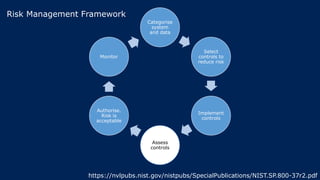
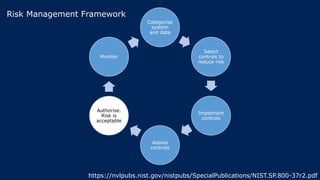
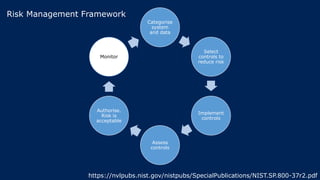
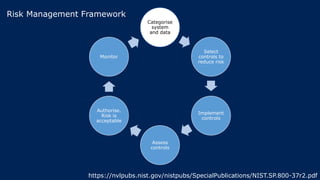
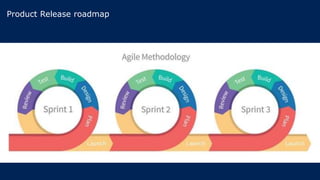
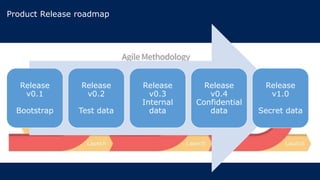
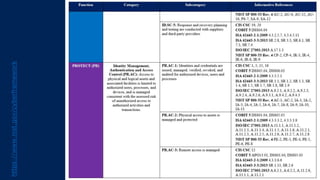
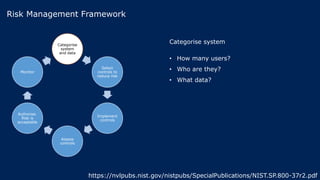
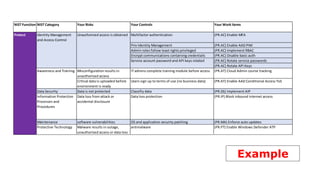
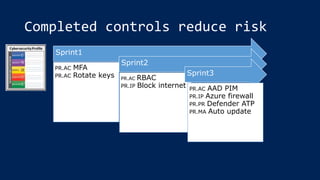
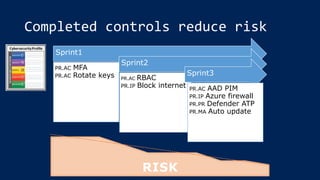
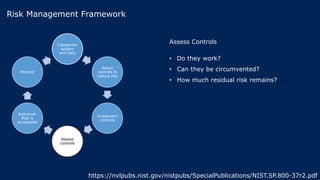
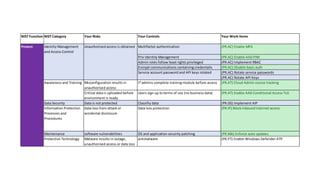
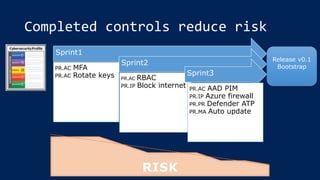
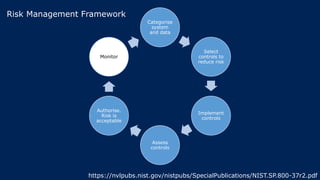
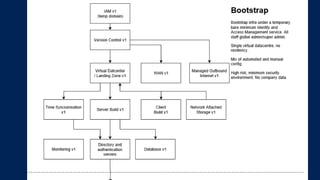
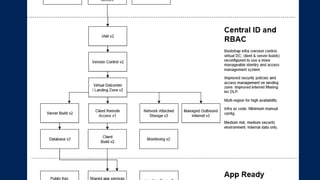
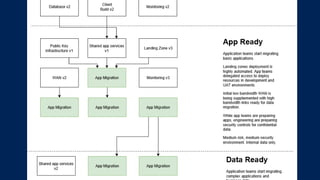
The document outlines KA2, a consultancy specializing in technology change, particularly in cloud migration and security for various sectors. It emphasizes the importance of a collaborative approach and the implementation of the NIST risk management framework to manage security risks on public clouds. Additionally, it highlights the significance of program management and innovation in delivering effective technology solutions to clients.