Field journal pt.4
•Download as PPTX, PDF•
0 likes•173 views
Report
Share
Report
Share
Recommended
More Related Content
Viewers also liked
Viewers also liked (16)
Cracking the Data Conundrum: How Successful Companies Make #BigData Operational

Cracking the Data Conundrum: How Successful Companies Make #BigData Operational
Braskem day international business unit presentation - roberto ramos

Braskem day international business unit presentation - roberto ramos
February 10, 2011: Lunch on the Avenue XII @ Flamingo 

February 10, 2011: Lunch on the Avenue XII @ Flamingo
How to make create financial planning process design 6 powerpoint presentatio...

How to make create financial planning process design 6 powerpoint presentatio...
Recently uploaded
Recently uploaded (20)
Cyber Insurance - RalphGilot - Embry-Riddle Aeronautical University.pptx

Cyber Insurance - RalphGilot - Embry-Riddle Aeronautical University.pptx
Harnessing Passkeys in the Battle Against AI-Powered Cyber Threats.pptx

Harnessing Passkeys in the Battle Against AI-Powered Cyber Threats.pptx
Frisco Automating Purchase Orders with MuleSoft IDP- May 10th, 2024.pptx.pdf

Frisco Automating Purchase Orders with MuleSoft IDP- May 10th, 2024.pptx.pdf
State of the Smart Building Startup Landscape 2024!

State of the Smart Building Startup Landscape 2024!
How to Check CNIC Information Online with Pakdata cf

How to Check CNIC Information Online with Pakdata cf
(Explainable) Data-Centric AI: what are you explaininhg, and to whom?

(Explainable) Data-Centric AI: what are you explaininhg, and to whom?
Intro to Passkeys and the State of Passwordless.pptx

Intro to Passkeys and the State of Passwordless.pptx
Introduction to FIDO Authentication and Passkeys.pptx

Introduction to FIDO Authentication and Passkeys.pptx
Microsoft CSP Briefing Pre-Engagement - Questionnaire

Microsoft CSP Briefing Pre-Engagement - Questionnaire
Continuing Bonds Through AI: A Hermeneutic Reflection on Thanabots

Continuing Bonds Through AI: A Hermeneutic Reflection on Thanabots
Human Expert Website Manual WCAG 2.0 2.1 2.2 Audit - Digital Accessibility Au...

Human Expert Website Manual WCAG 2.0 2.1 2.2 Audit - Digital Accessibility Au...
Field journal pt.4
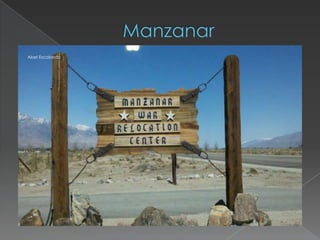
- 5. Abel Escobedo Name of the Prisoners that were once in Manzanar when it was being constructed.
- 6. This is a blade made out of Obsidian that was found near Cinder Hill and Fossil Falls. This is a prime example of a weapon that the Native Americans used. Abel Escobedo
- 7. Abel Escobedo Owens Valley follows through within these mountains…