Wanna-cry Ransome ware
•Download as PPTX, PDF•
0 likes•98 views
Hy this is Abhay ,here in this ppt we describe the concept of wanna cry and some critical reports,and this is the ppt for all professional and non professional also
Report
Share
Report
Share
More Related Content
What's hot (20)
Malicious android-applications-risks-exploitation 33578

Malicious android-applications-risks-exploitation 33578
Similar to Wanna-cry Ransome ware
Ransomware Gang Masquerades as Real Company to Recruit Tech Talent

Ransomware Gang Masquerades as Real Company to Recruit Tech TalentLUMINATIVE MEDIA/PROJECT COUNSEL MEDIA GROUP
Similar to Wanna-cry Ransome ware (20)
What’s the Difference Between Identity Fraud and Identity Theft?

What’s the Difference Between Identity Fraud and Identity Theft?
What’s the Difference Between Identity Fraud and Identity Theft.docx.pptx

What’s the Difference Between Identity Fraud and Identity Theft.docx.pptx
Crypto-Jacking, Ransomware & Worming Malware's Frightening Future (Keynote an...

Crypto-Jacking, Ransomware & Worming Malware's Frightening Future (Keynote an...
Invincea fake british airways ticket spear-phish malware 03-21-2014

Invincea fake british airways ticket spear-phish malware 03-21-2014
Invincea fake british airways ticket spear-phish malware 03-21-2014

Invincea fake british airways ticket spear-phish malware 03-21-2014
Ransomware Gang Masquerades as Real Company to Recruit Tech Talent

Ransomware Gang Masquerades as Real Company to Recruit Tech Talent
Recently uploaded
Call Us -/9953056974- Call Girls In Vikaspuri-/- Delhi NCR

Call Us -/9953056974- Call Girls In Vikaspuri-/- Delhi NCR9953056974 Low Rate Call Girls In Saket, Delhi NCR
VICTOR MAESTRE RAMIREZ - Planetary Defender on NASA's Double Asteroid Redirec...

VICTOR MAESTRE RAMIREZ - Planetary Defender on NASA's Double Asteroid Redirec...VICTOR MAESTRE RAMIREZ
Recently uploaded (20)
Gurgaon ✡️9711147426✨Call In girls Gurgaon Sector 51 escort service

Gurgaon ✡️9711147426✨Call In girls Gurgaon Sector 51 escort service
CCS355 Neural Network & Deep Learning UNIT III notes and Question bank .pdf

CCS355 Neural Network & Deep Learning UNIT III notes and Question bank .pdf
Biology for Computer Engineers Course Handout.pptx

Biology for Computer Engineers Course Handout.pptx
Arduino_CSE ece ppt for working and principal of arduino.ppt

Arduino_CSE ece ppt for working and principal of arduino.ppt
What are the advantages and disadvantages of membrane structures.pptx

What are the advantages and disadvantages of membrane structures.pptx
An experimental study in using natural admixture as an alternative for chemic...

An experimental study in using natural admixture as an alternative for chemic...
Sachpazis Costas: Geotechnical Engineering: A student's Perspective Introduction

Sachpazis Costas: Geotechnical Engineering: A student's Perspective Introduction
Decoding Kotlin - Your guide to solving the mysterious in Kotlin.pptx

Decoding Kotlin - Your guide to solving the mysterious in Kotlin.pptx
Study on Air-Water & Water-Water Heat Exchange in a Finned Tube Exchanger

Study on Air-Water & Water-Water Heat Exchange in a Finned Tube Exchanger
Call Us -/9953056974- Call Girls In Vikaspuri-/- Delhi NCR

Call Us -/9953056974- Call Girls In Vikaspuri-/- Delhi NCR
Exploring_Network_Security_with_JA3_by_Rakesh Seal.pptx

Exploring_Network_Security_with_JA3_by_Rakesh Seal.pptx
VICTOR MAESTRE RAMIREZ - Planetary Defender on NASA's Double Asteroid Redirec...

VICTOR MAESTRE RAMIREZ - Planetary Defender on NASA's Double Asteroid Redirec...
complete construction, environmental and economics information of biomass com...

complete construction, environmental and economics information of biomass com...
Wanna-cry Ransome ware
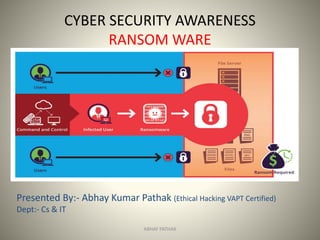
- 1. CYBER SECURITY AWARENESS RANSOM WARE ABHAY PATHAK Presented By:- Abhay Kumar Pathak (Ethical Hacking VAPT Certified) Dept:- Cs & IT
- 2. Ransom ware The Biggest Attack on Internet History As it is called a malicious program - that locks the device your computer, tablet, Smartphone and demands a ransom(Money) to unlock it. It hits the device when navigating through the various hacked websites, downloading a file or on clicking wrong link. Every 40 seconds, a company gets hit by a ransom ware. Unfortunately, it’s more sophisticated and disruptive to your operations. 2017 is being swept by the ransom ware, and this does not seem to end. ABHAY PATHAK
- 3. 2017’s biggest ransom ware cyber attack Petya-The second massive cyber attack, a variant of the ransom ware petya re-arranged using the same eternal blue exploit and hits organisations world wide, especially Ukraine, is found to exploit MS office and SMBv1 vulnerabilities and has worm capabilities, allows it to spread, quickly across infected networks. ABHAY PATHAK
- 4. Wanna-Cry Ransom Ware The first Ransom Ware was called AIDS trojan which emerged in 1989, it was spread through Floppy Disk, and the victims were asked to send an amount of $189 to a postal address of PANAMA as Ransom. May 12, 2017 witnessed the biggest ever cyber attack in the internet history. A Ransom ware named Wanna-cry stormed through the network. It targeted computers running windows OS that are not up-to-date and brought computer systems from Russia to china and the US to their knees. ABHAY PATHAK
- 5. Who was responsible? The Vulnerability ,which was discovered was called ETERNAL BLUE , which was released by a unknown hacking group calling themselves Shadow Groups who was responsible for the Cyber Attack ,and the code was written by EQATION GROUP (according to NSA). ABHAY PATHAK
- 6. Carbon Black Report on Wanna-Cry Carbon Black estimates that about 6,300 vendors of ransom ware exist on the dark web, with more than 45,000 listings. These are websites where anyone can buy anything from software for $1 that can lock up a Smartphone to customized ransom ware packages complete with source code for $1,000 or more, according to the report. ABHAY PATHAK
- 7. Some Other Attacks of Ransom Ware Skype Fireball Delta Charlie ABHAY PATHAK