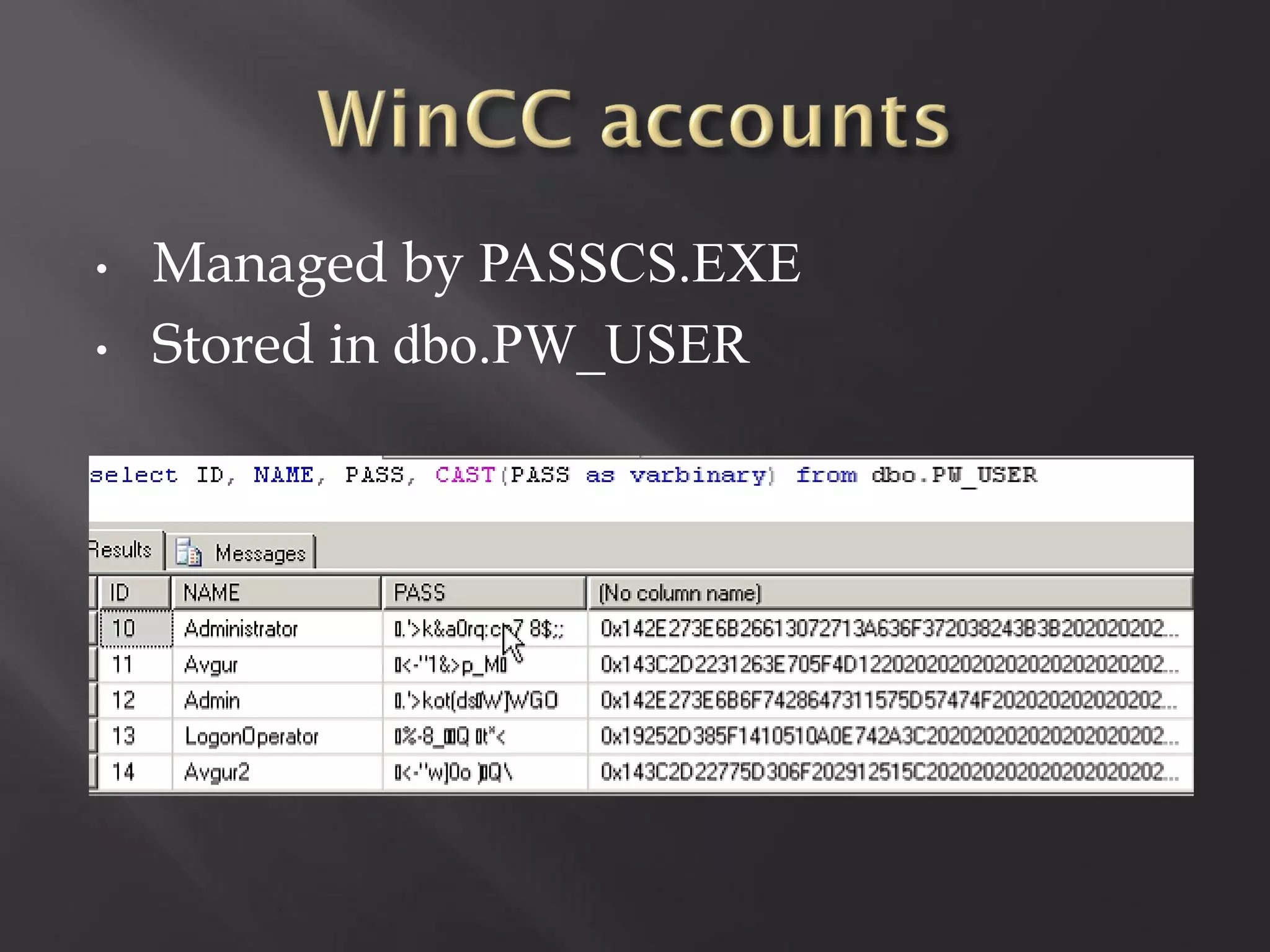
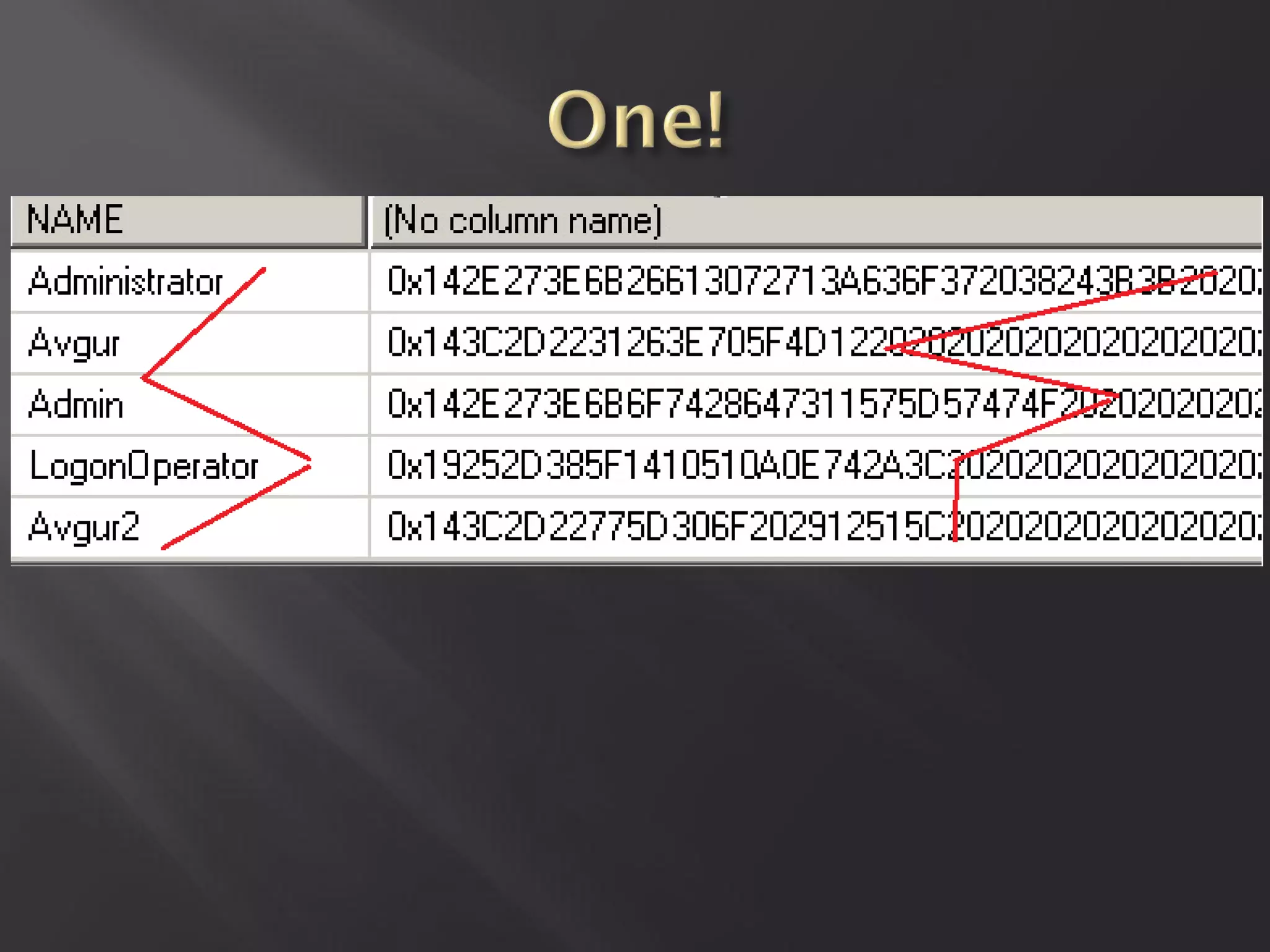
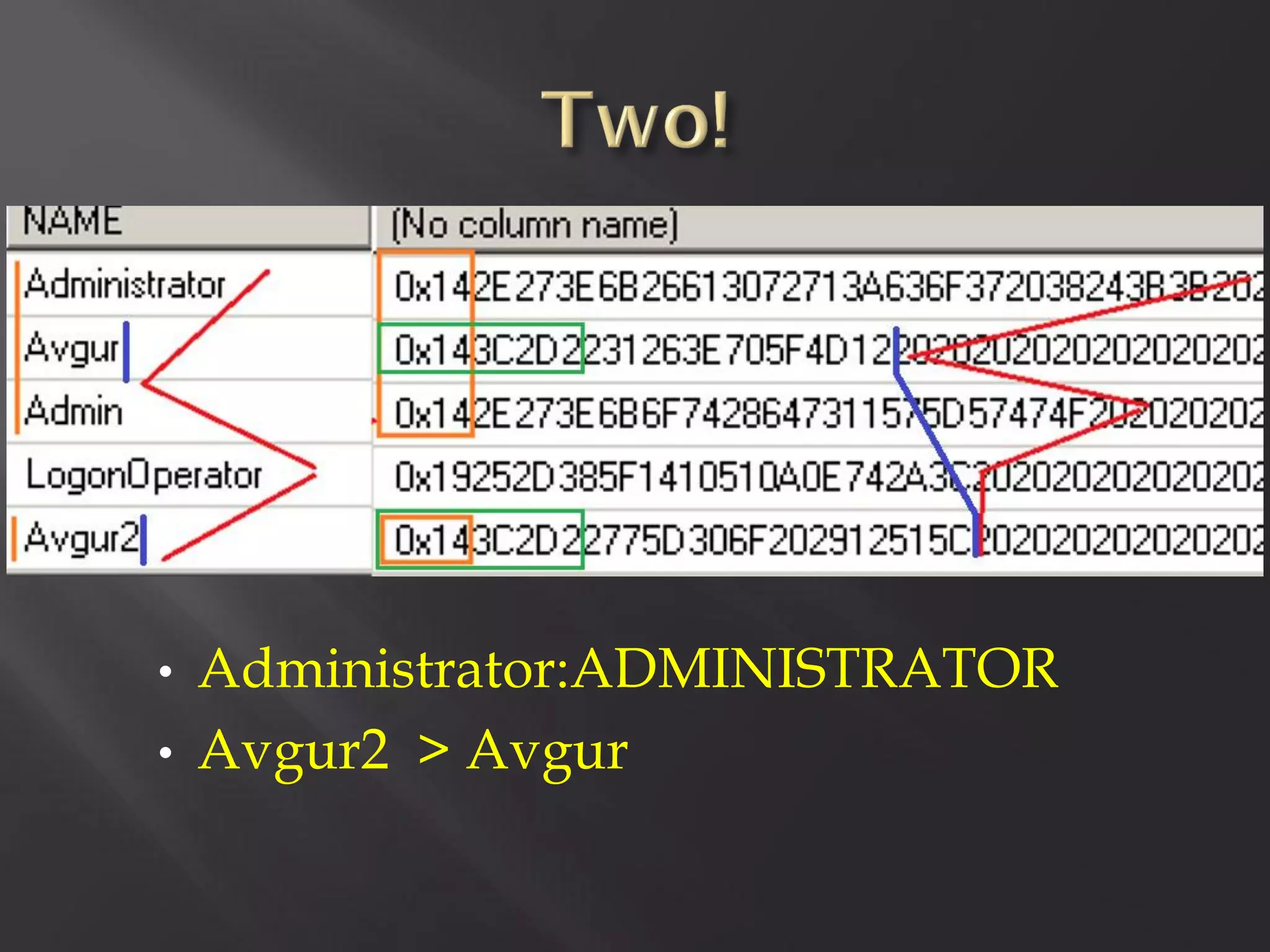
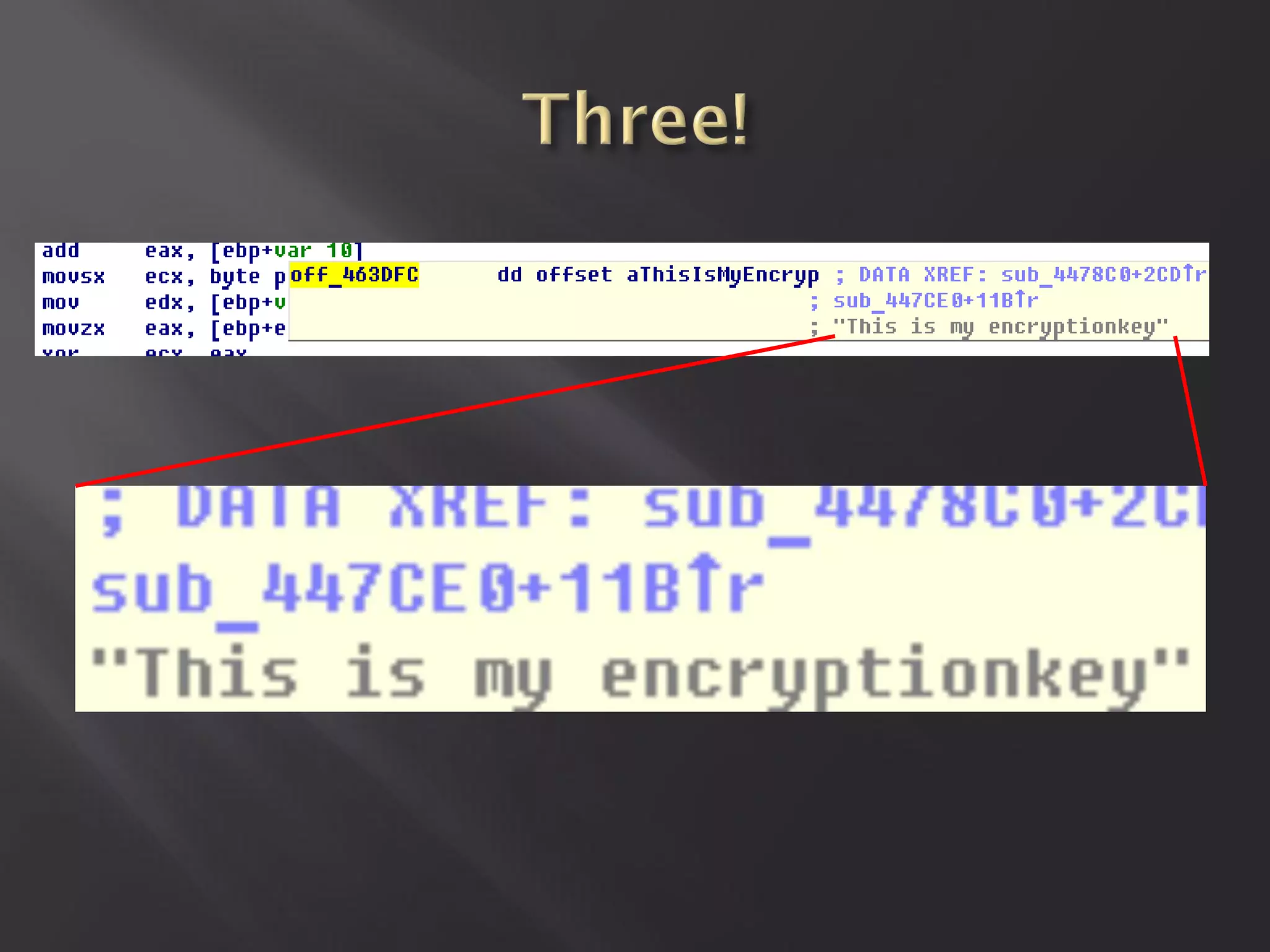
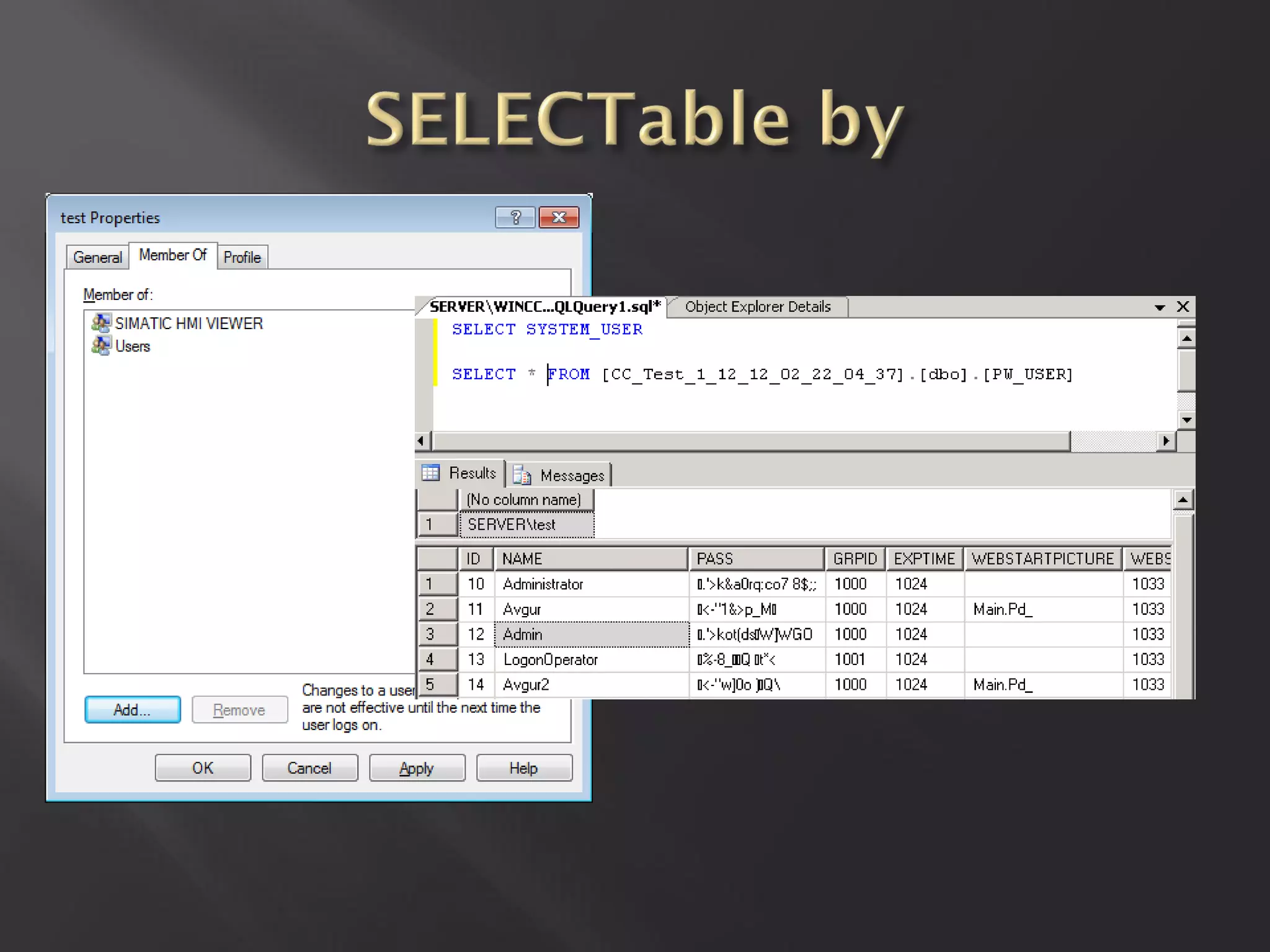
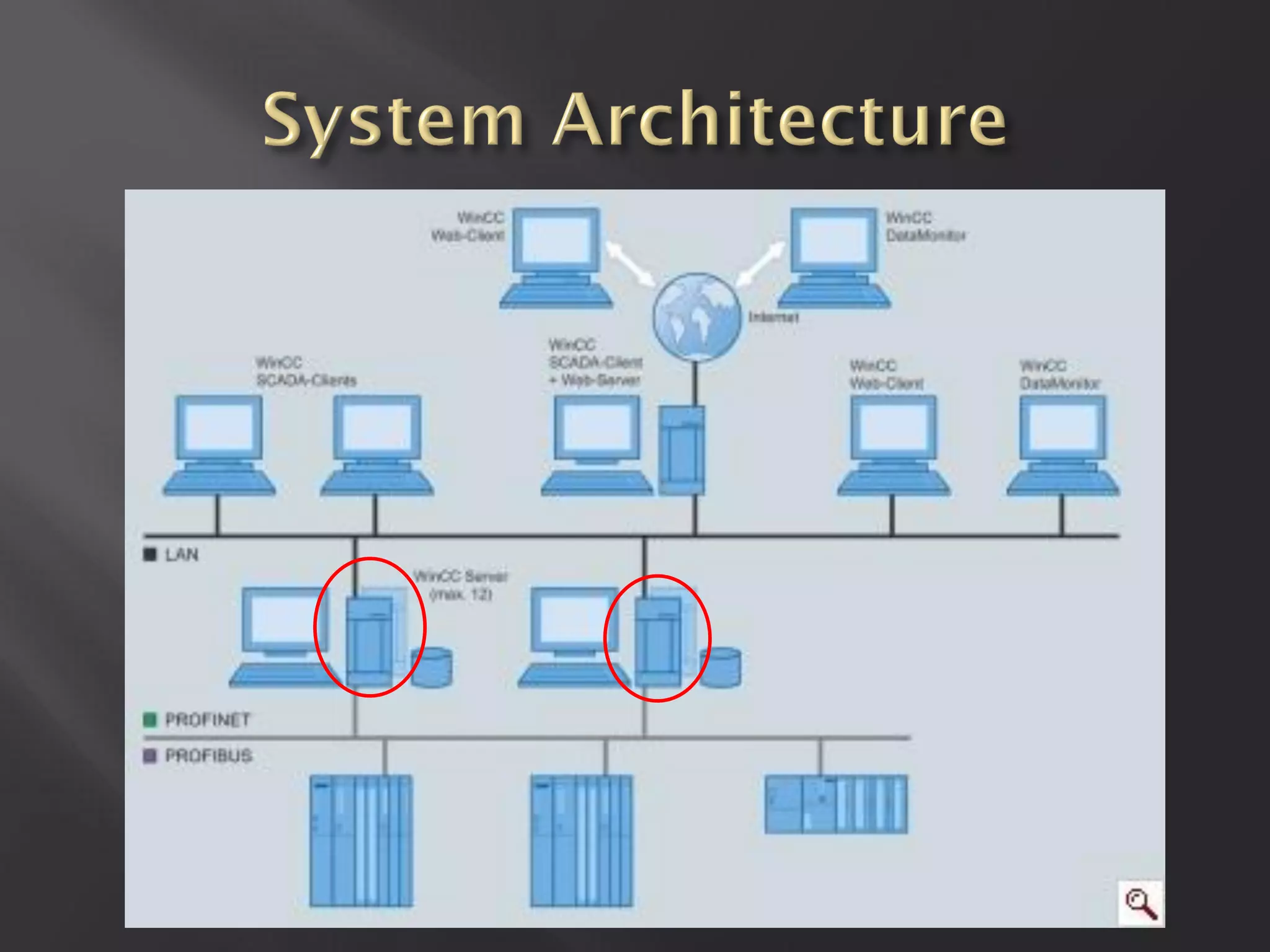
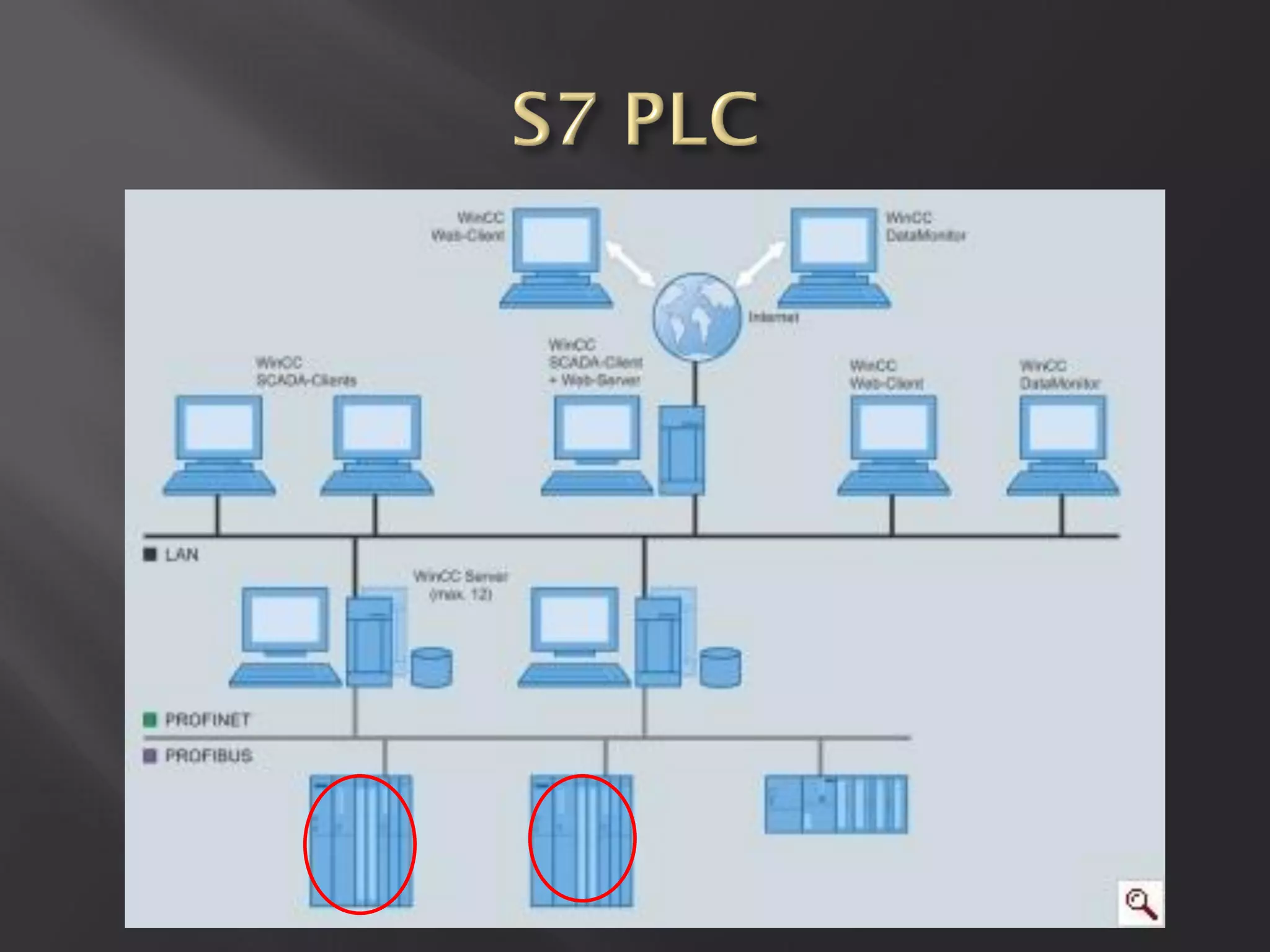
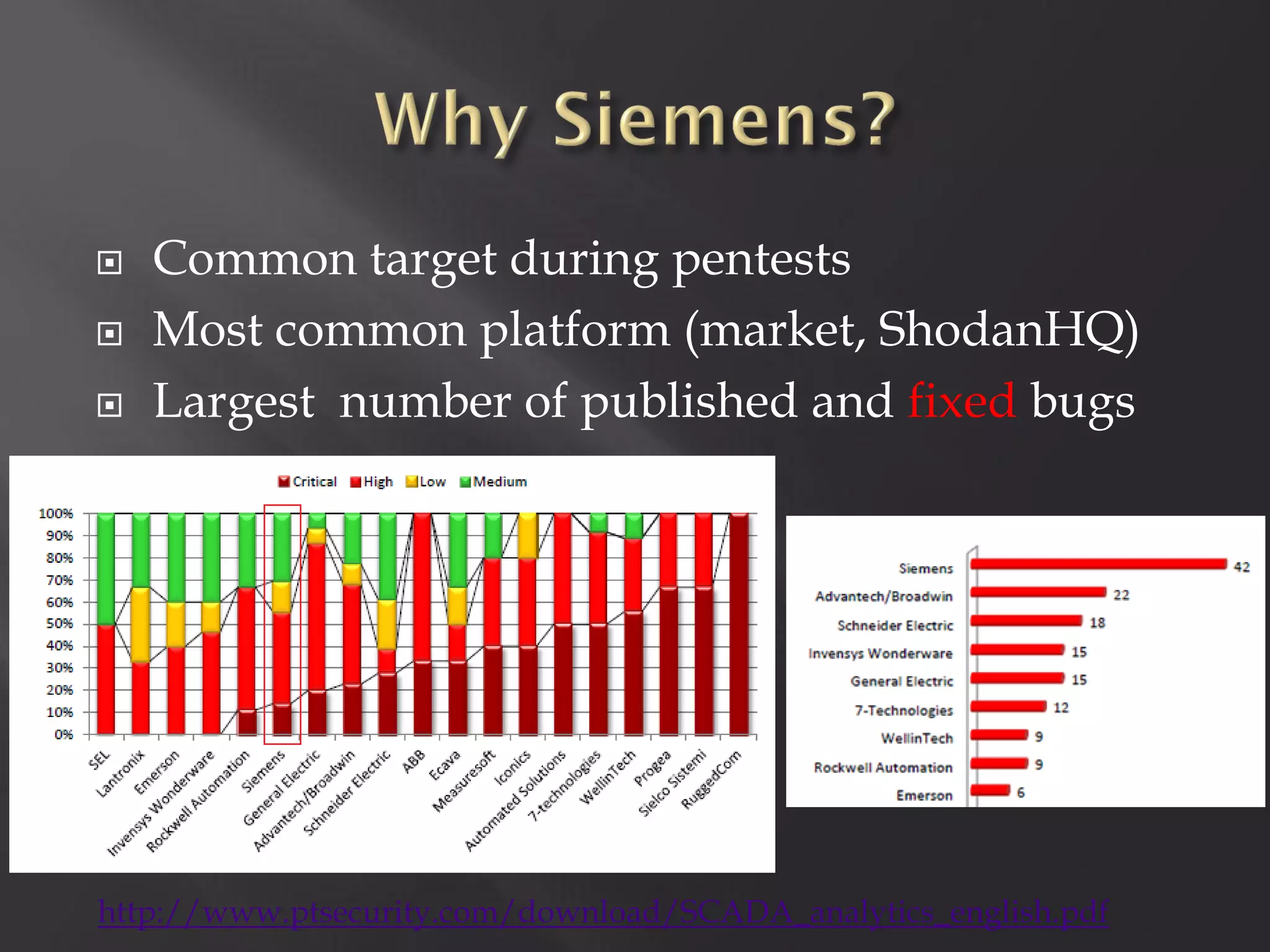
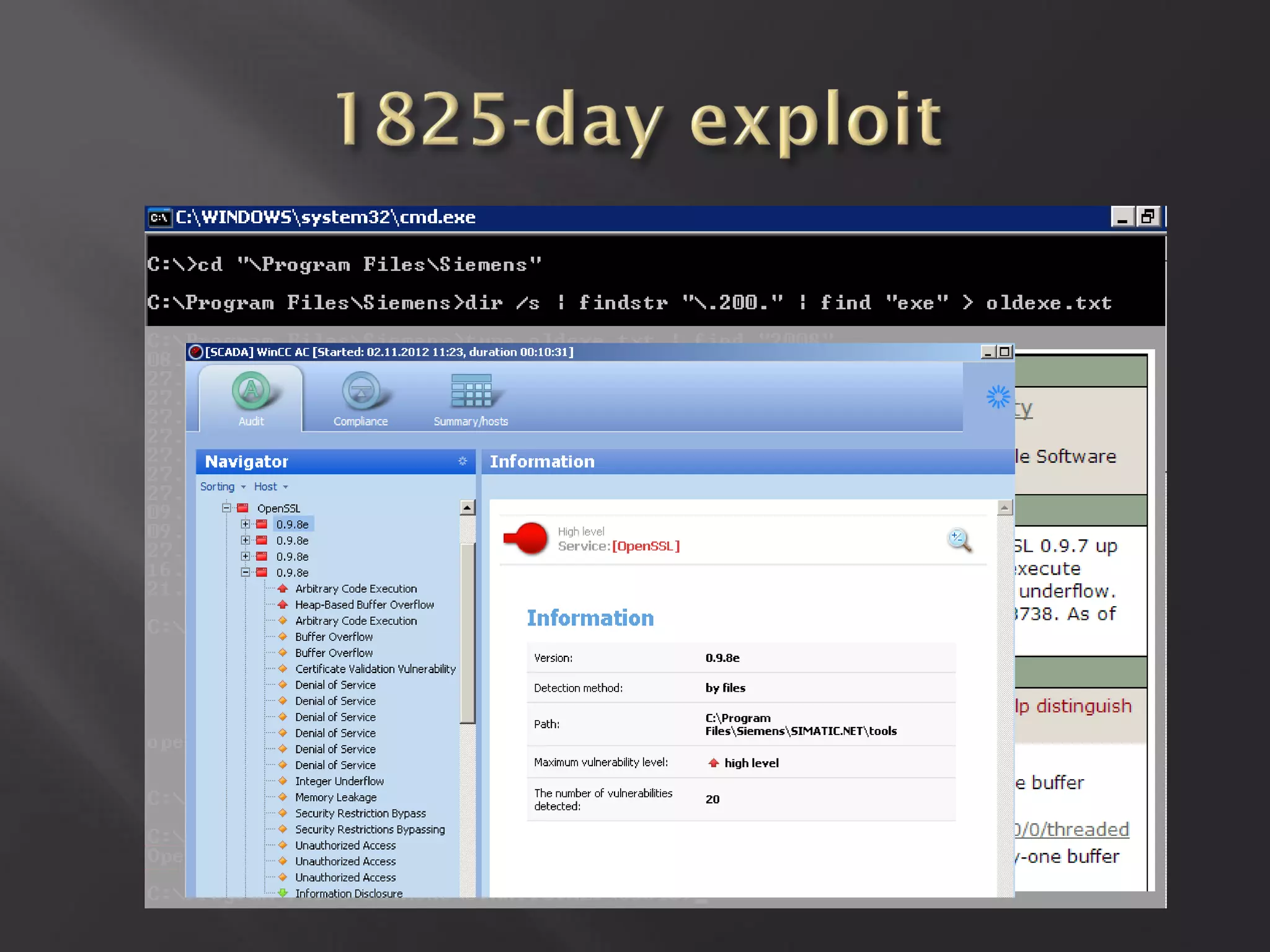
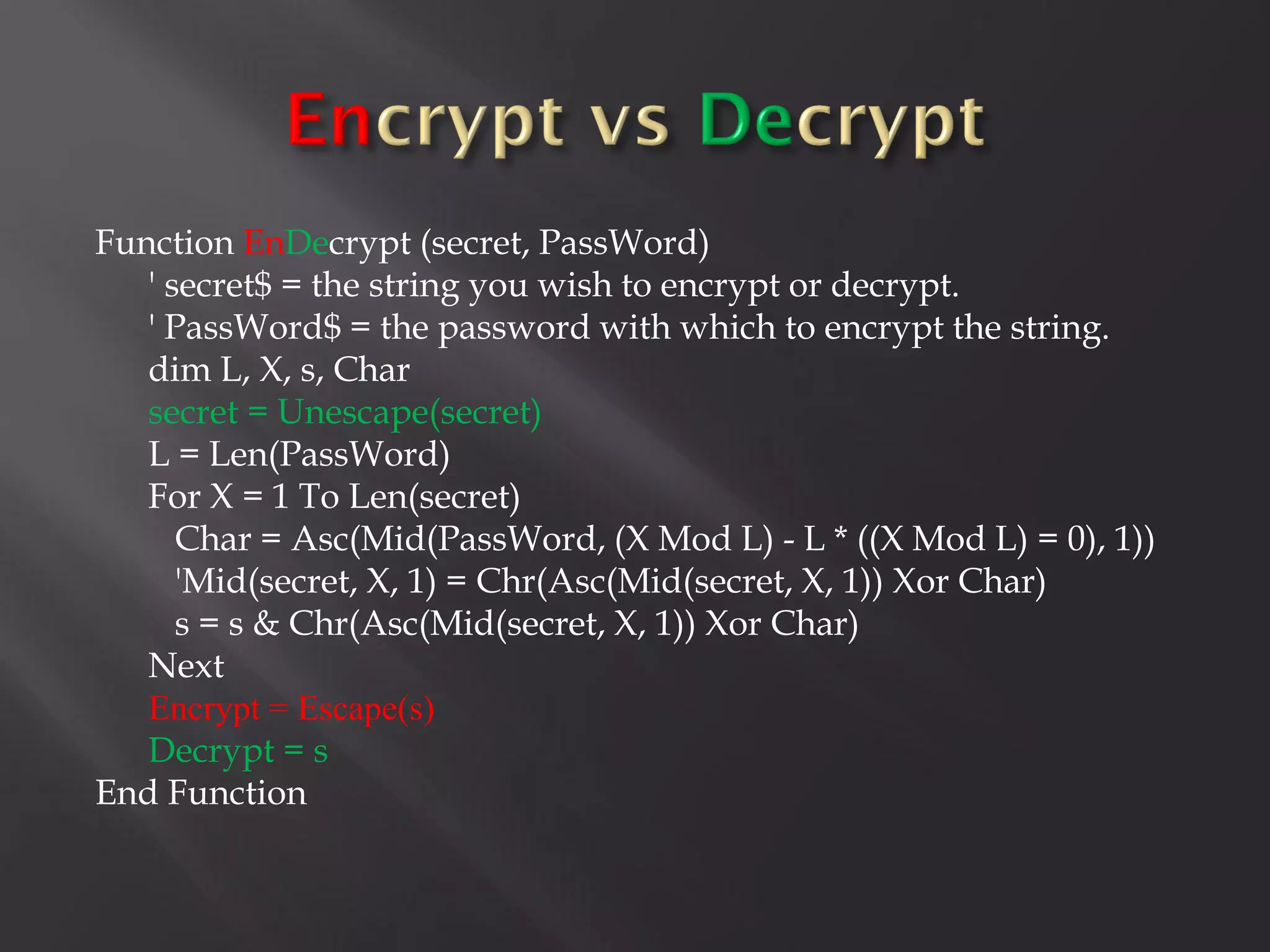
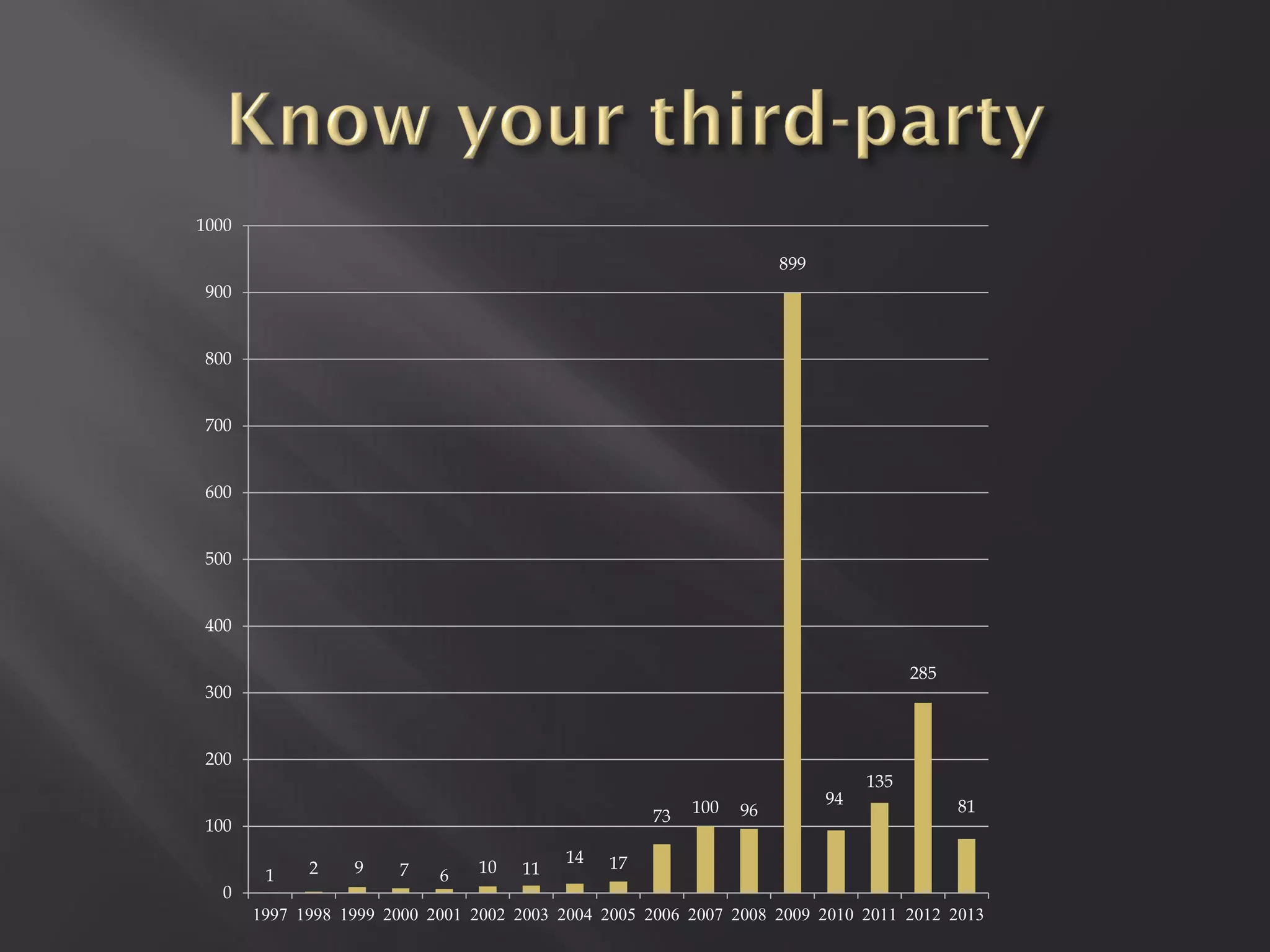
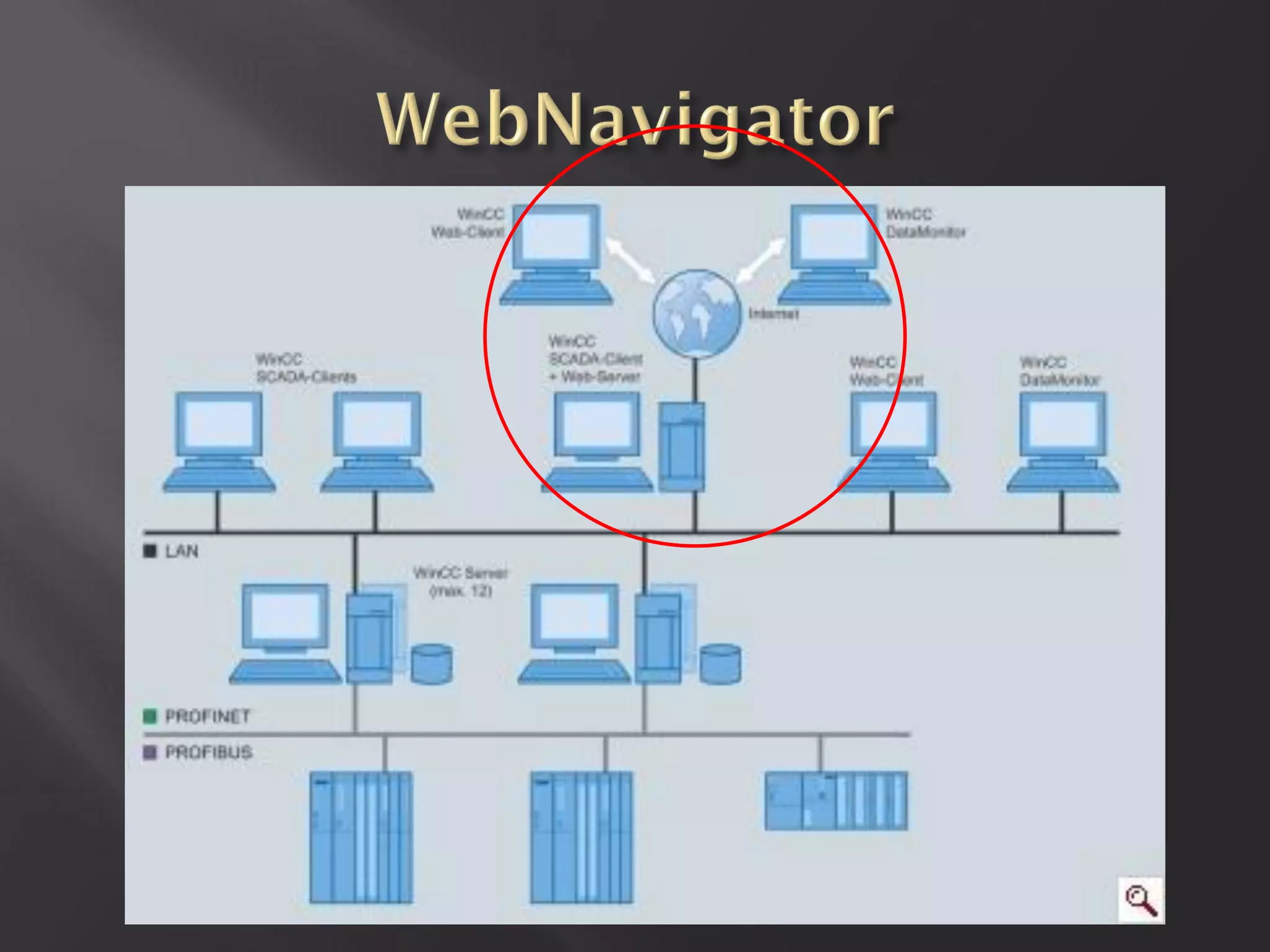
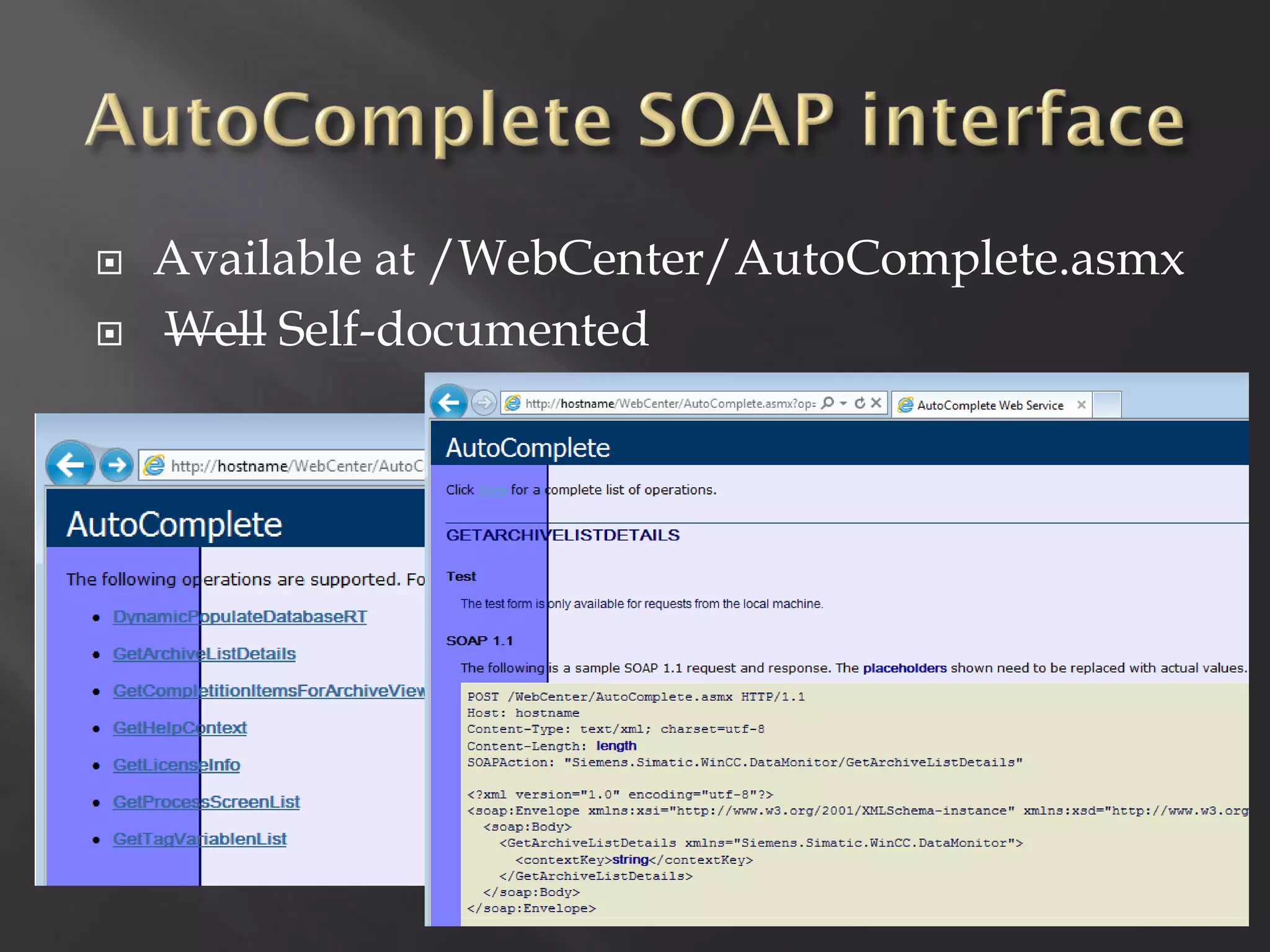
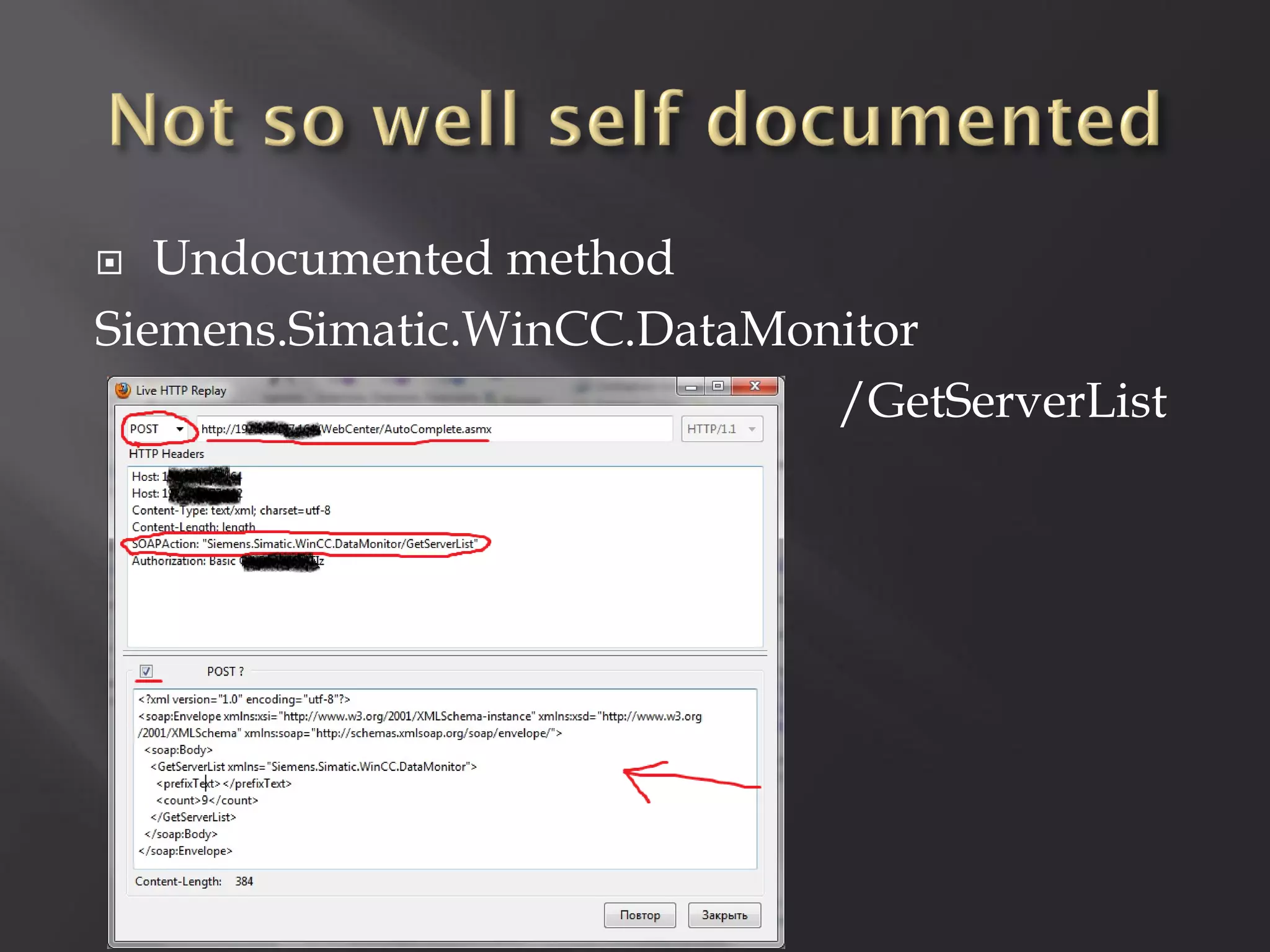
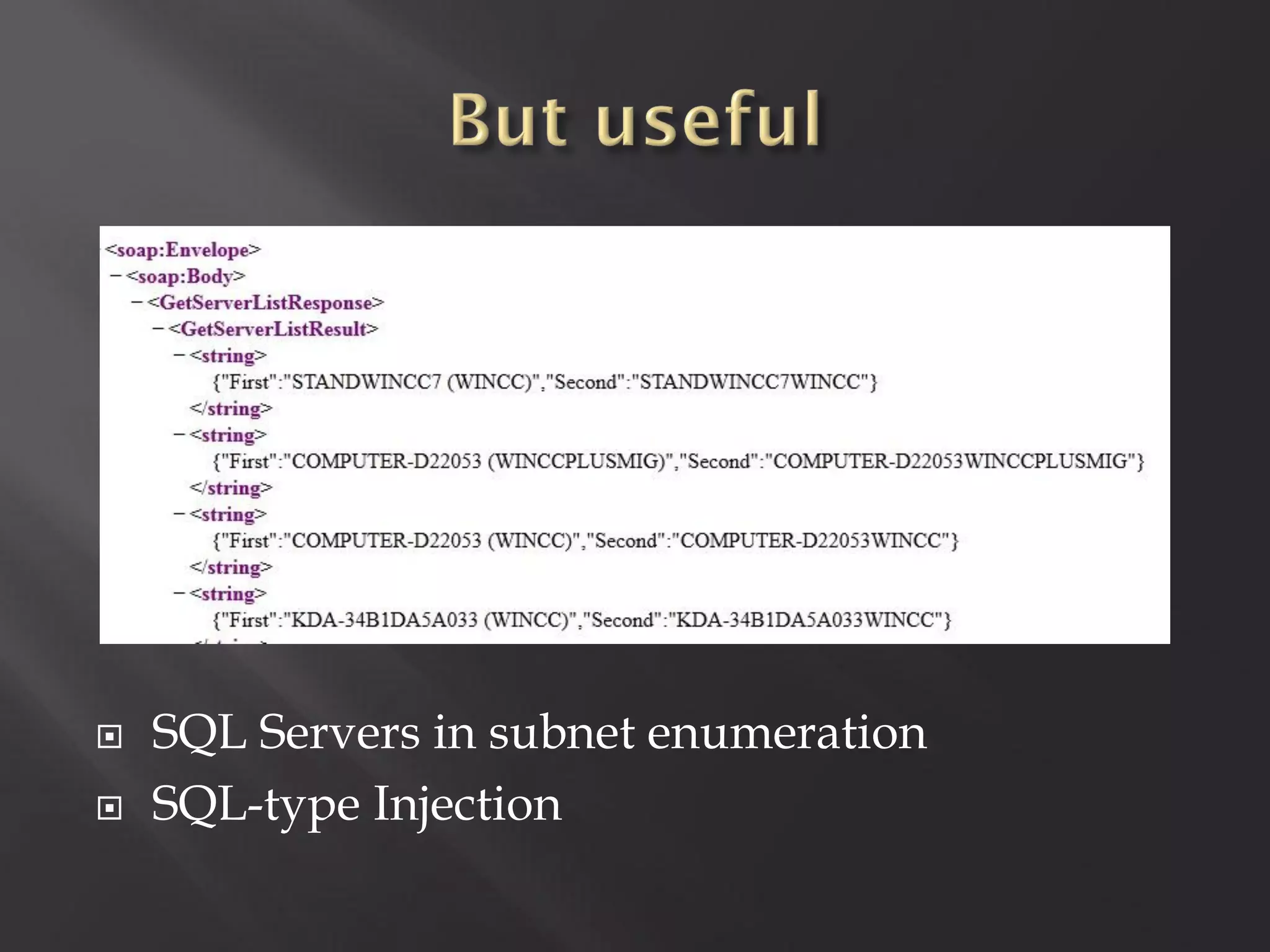
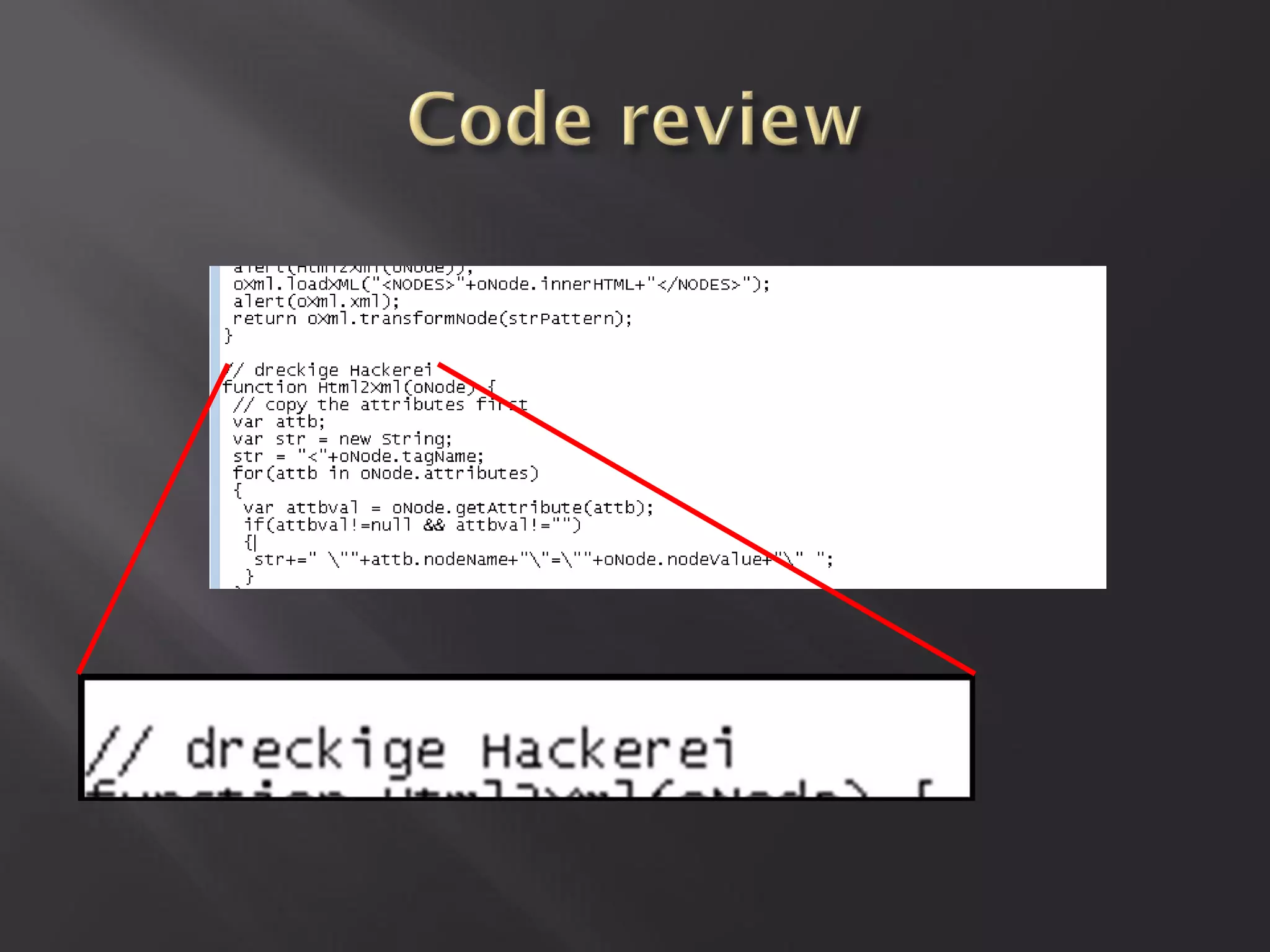
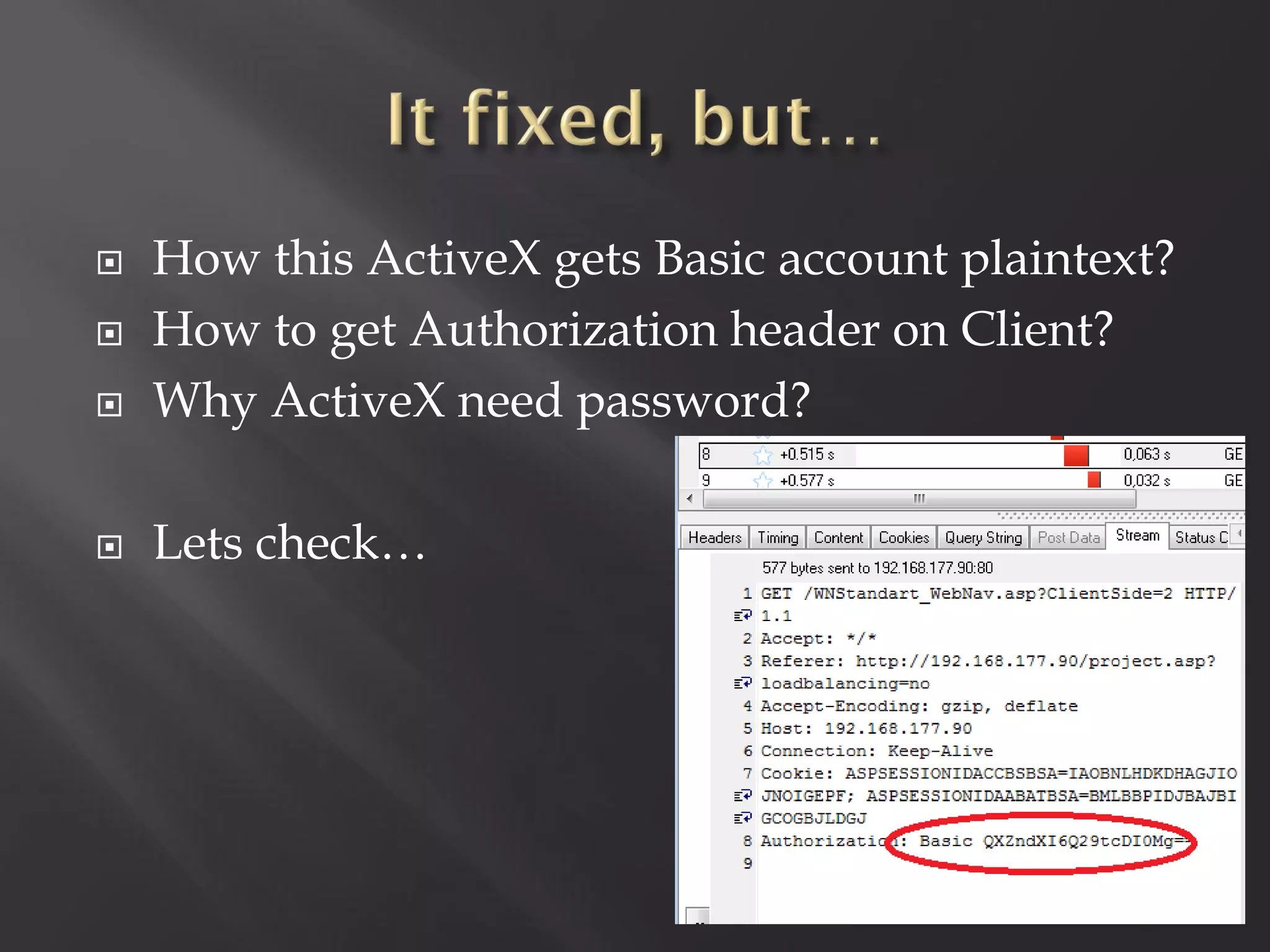
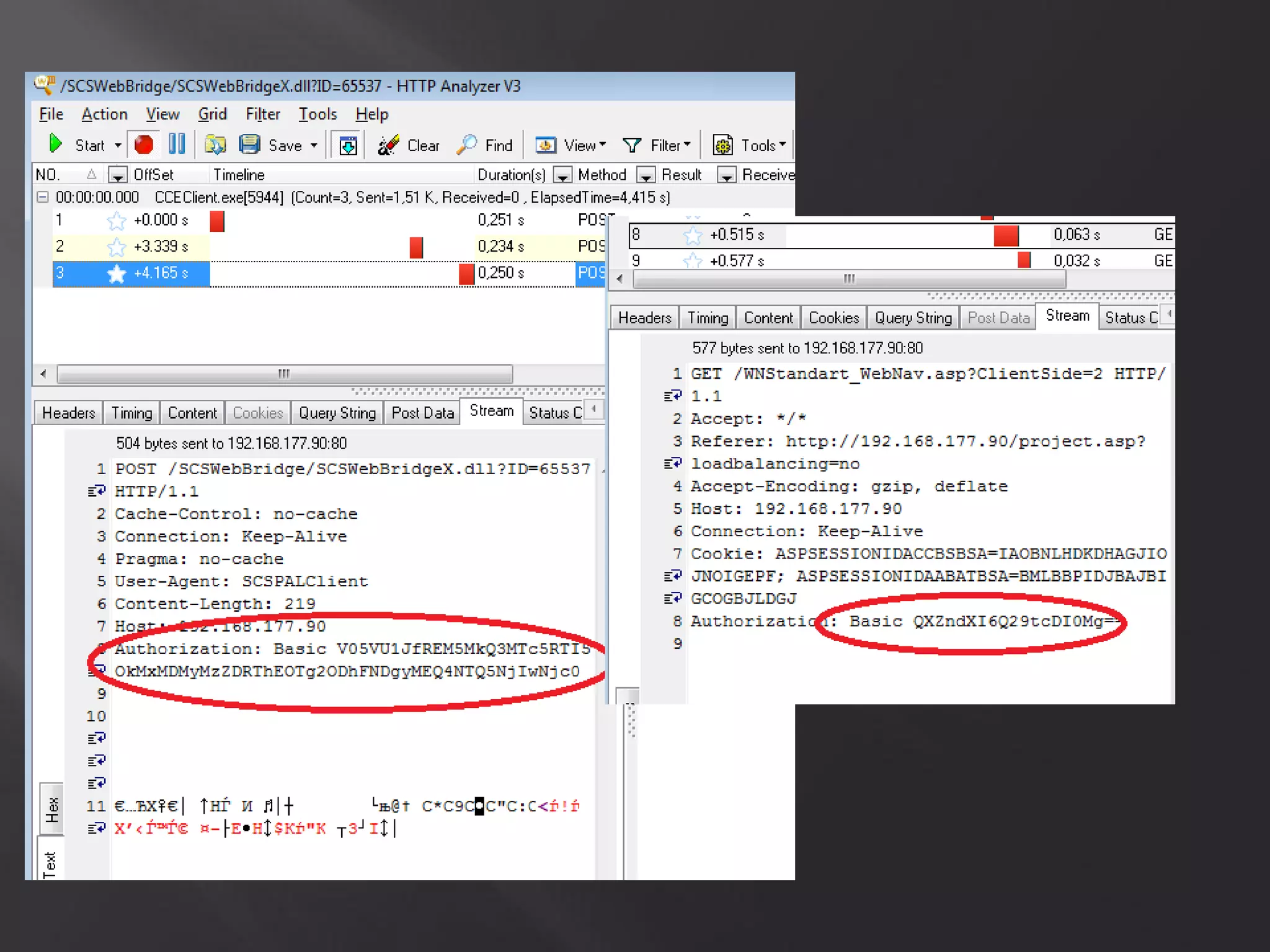
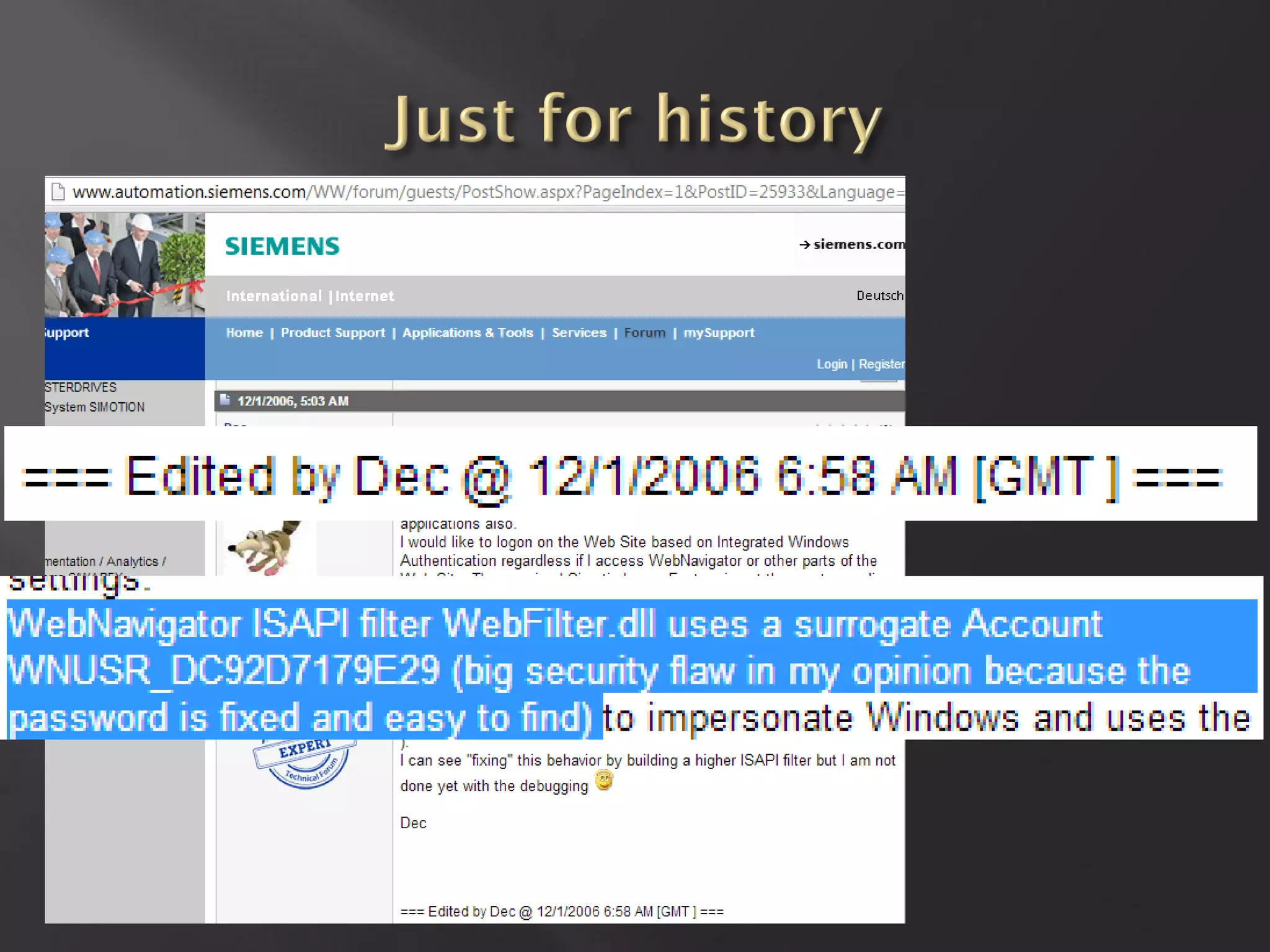
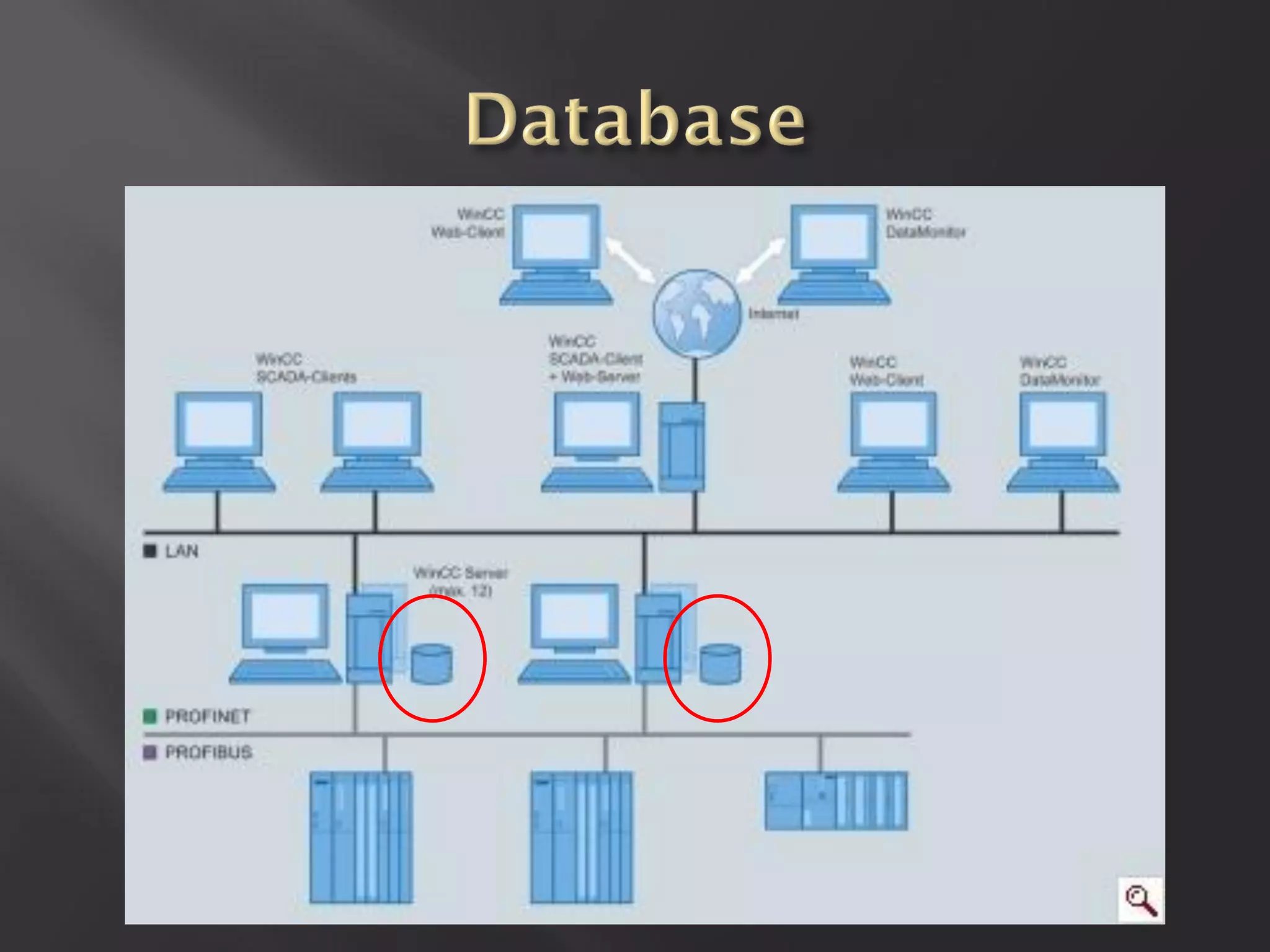
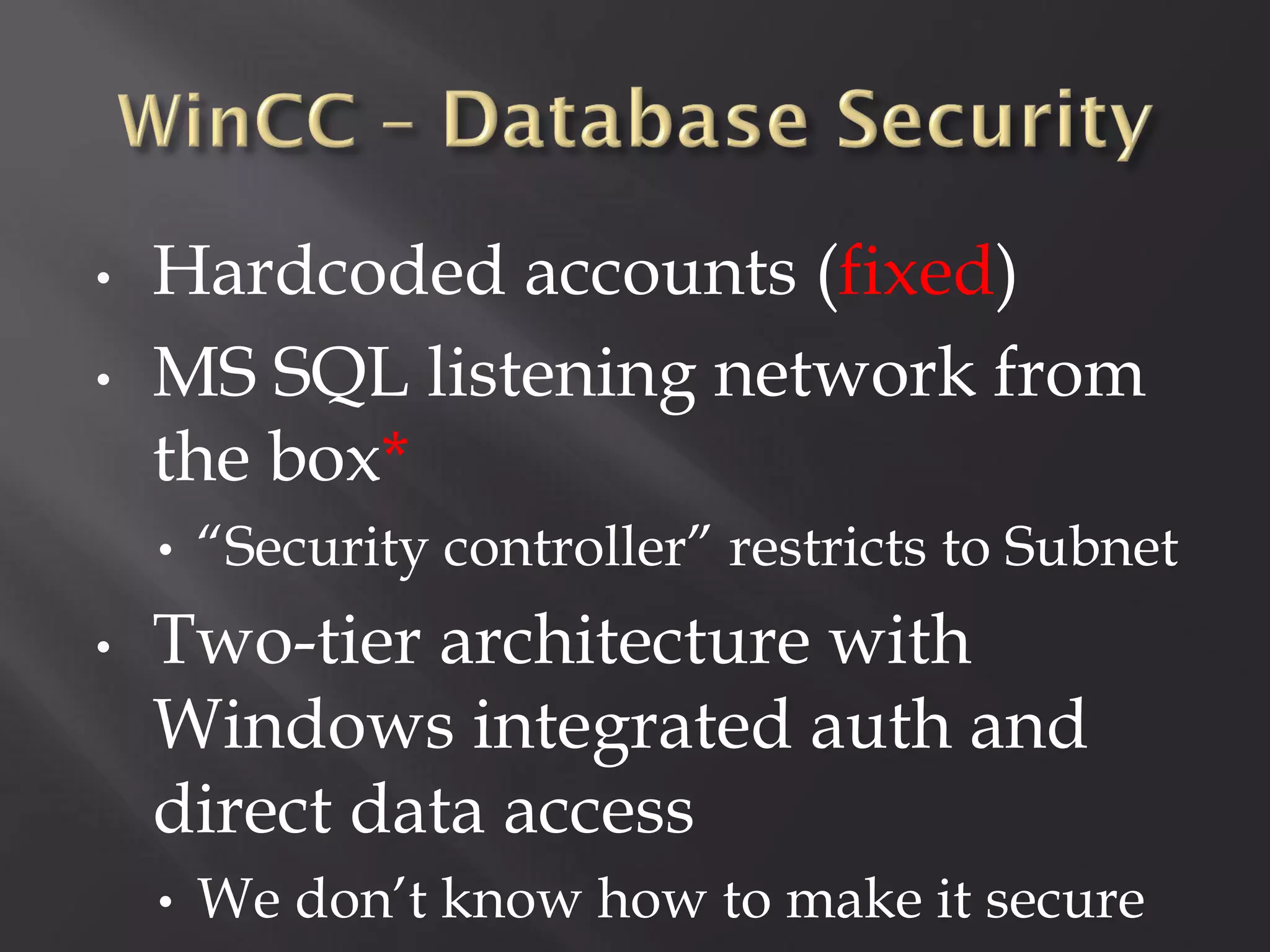
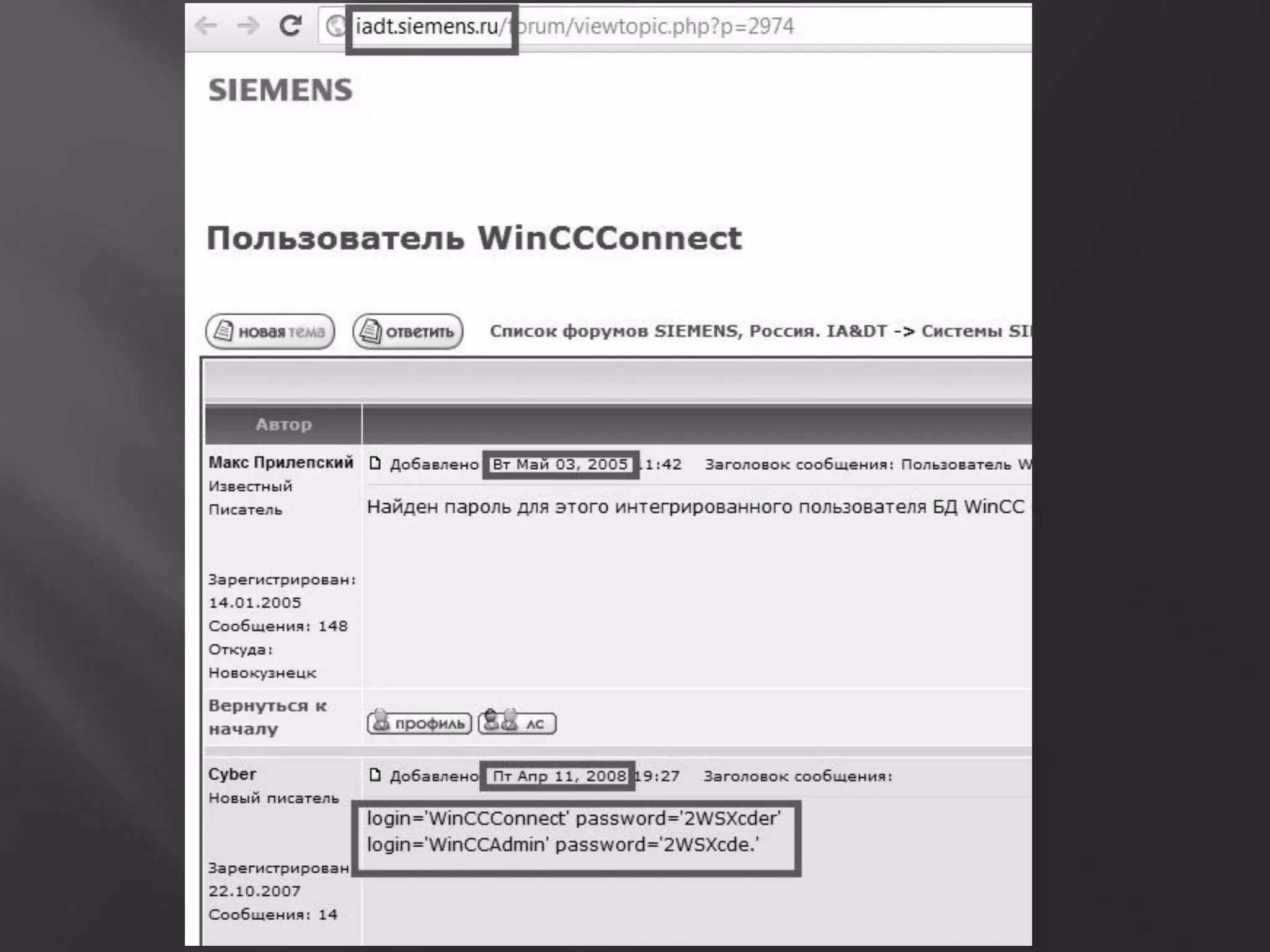
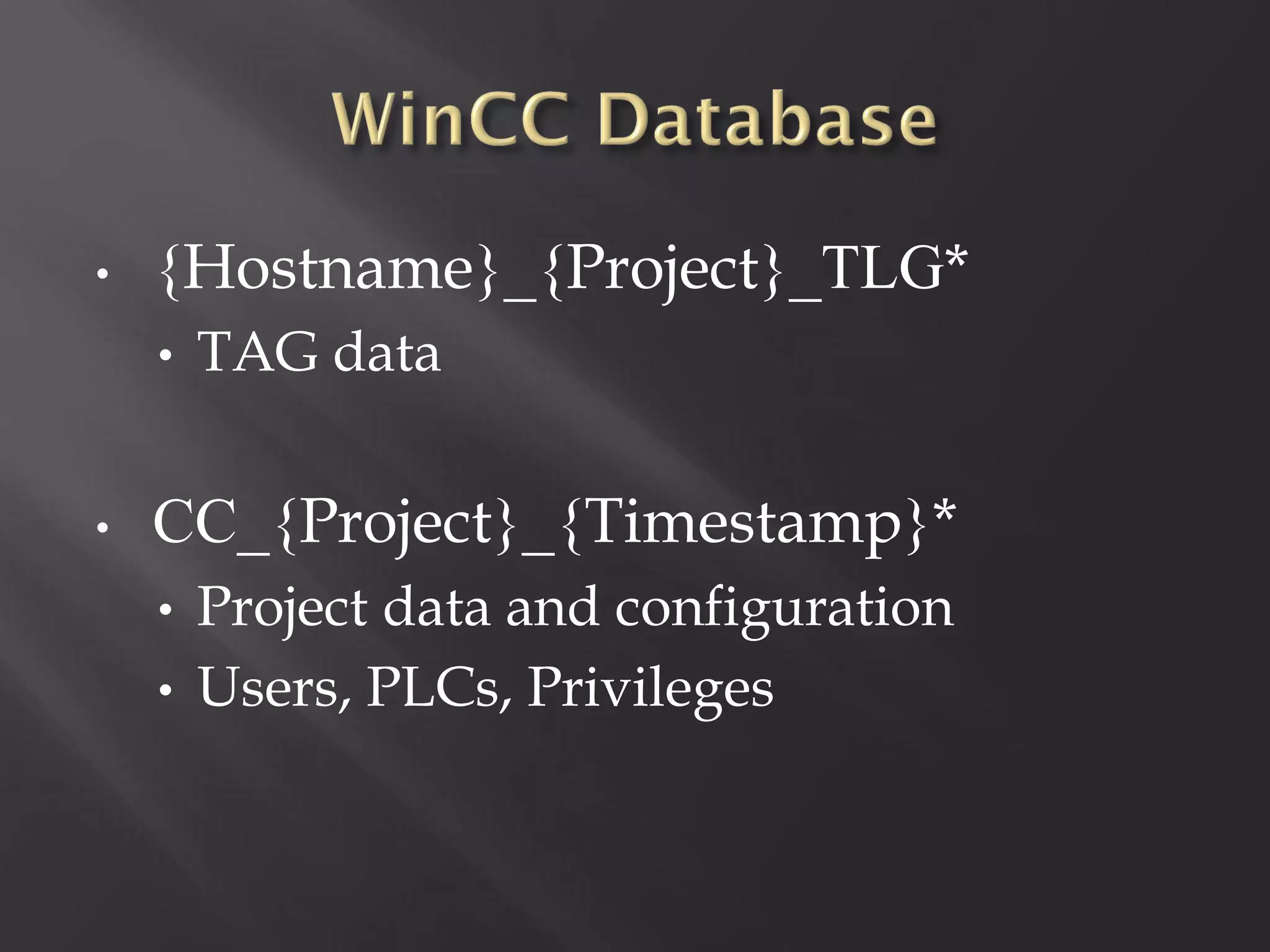
This document summarizes a presentation given by Sergey Gordeychik, Gleb Gritsai, and Denis Baranov on analyzing the security of WinCC SCADA software. It introduces the presenters and their backgrounds in industrial control system security research. They discuss common vulnerabilities found in WinCC like SQL injection, XSS, and password disclosure. The researchers provide an overview of the WinCC architecture and its various components. They analyze vulnerabilities in the WinCC project files and communication protocols. The presentation aims to bring more attention to automating security assessments of industrial control systems.














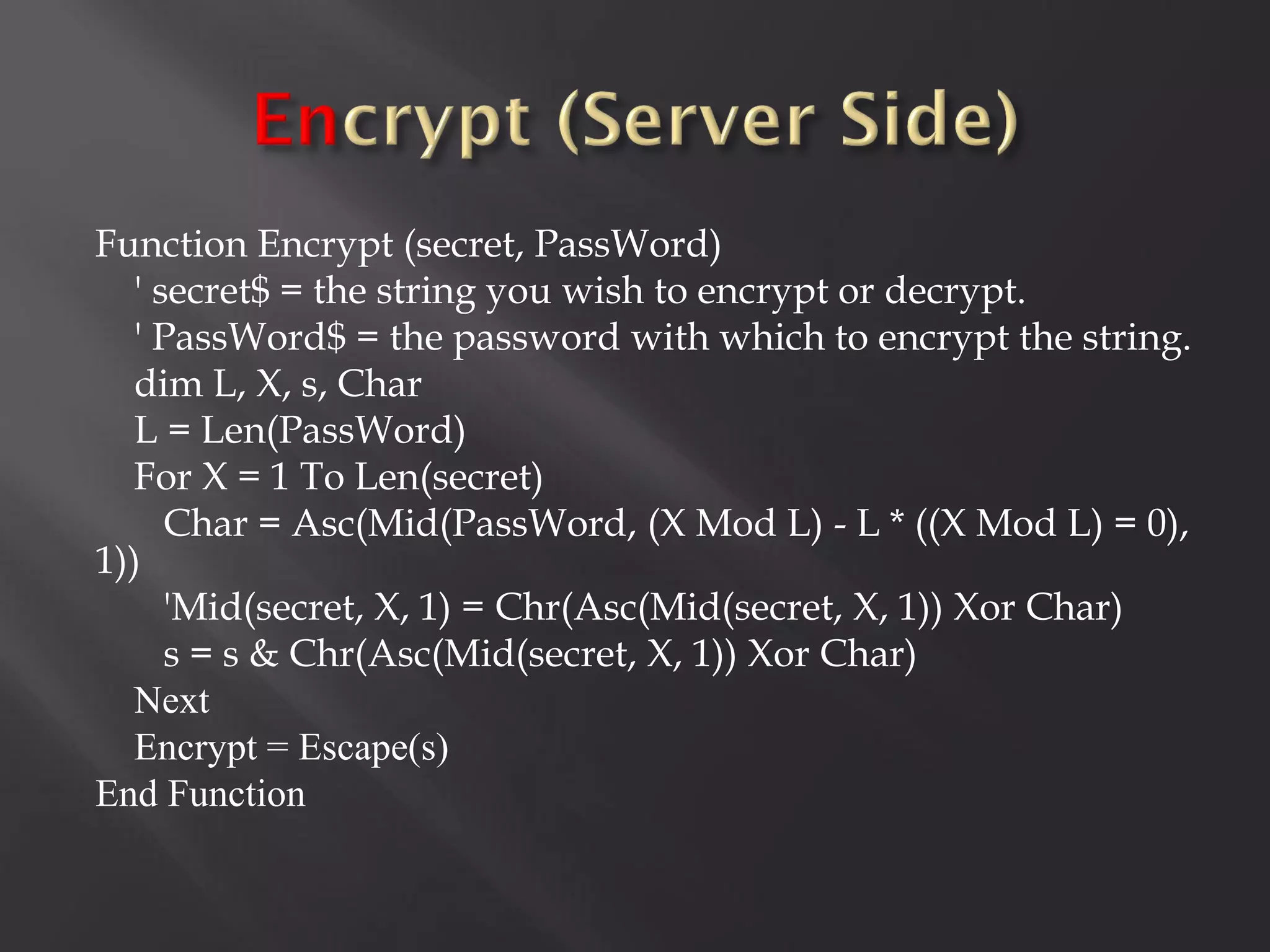
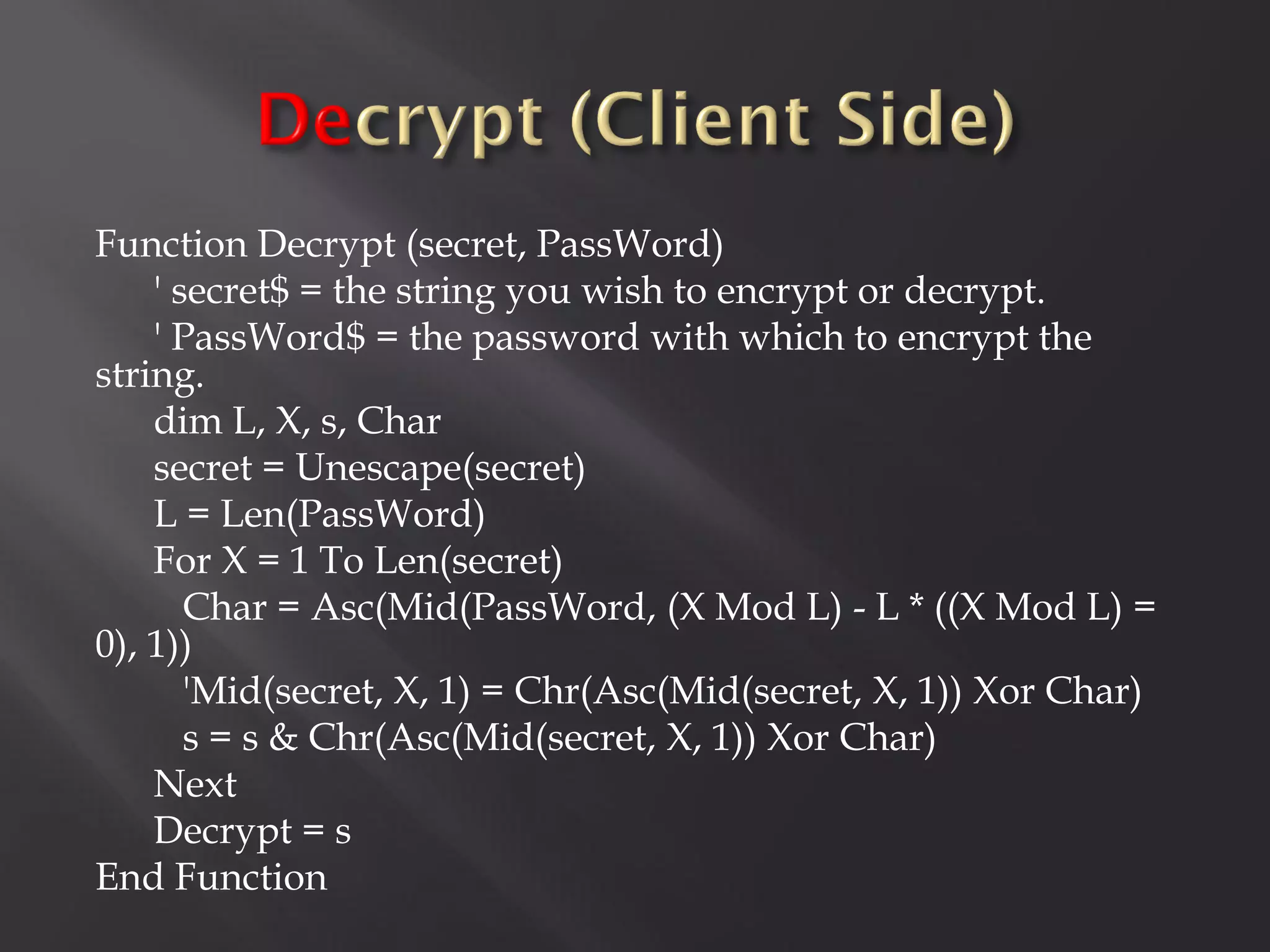







![Oh! En/c(r)ypt[10]n!](https://image.slidesharecdn.com/pt-s42013-scadaunderxrays-130117081345-phpapp01/75/Positive-Technologies-S4-Scada-under-x-rays-41-2048.jpg)



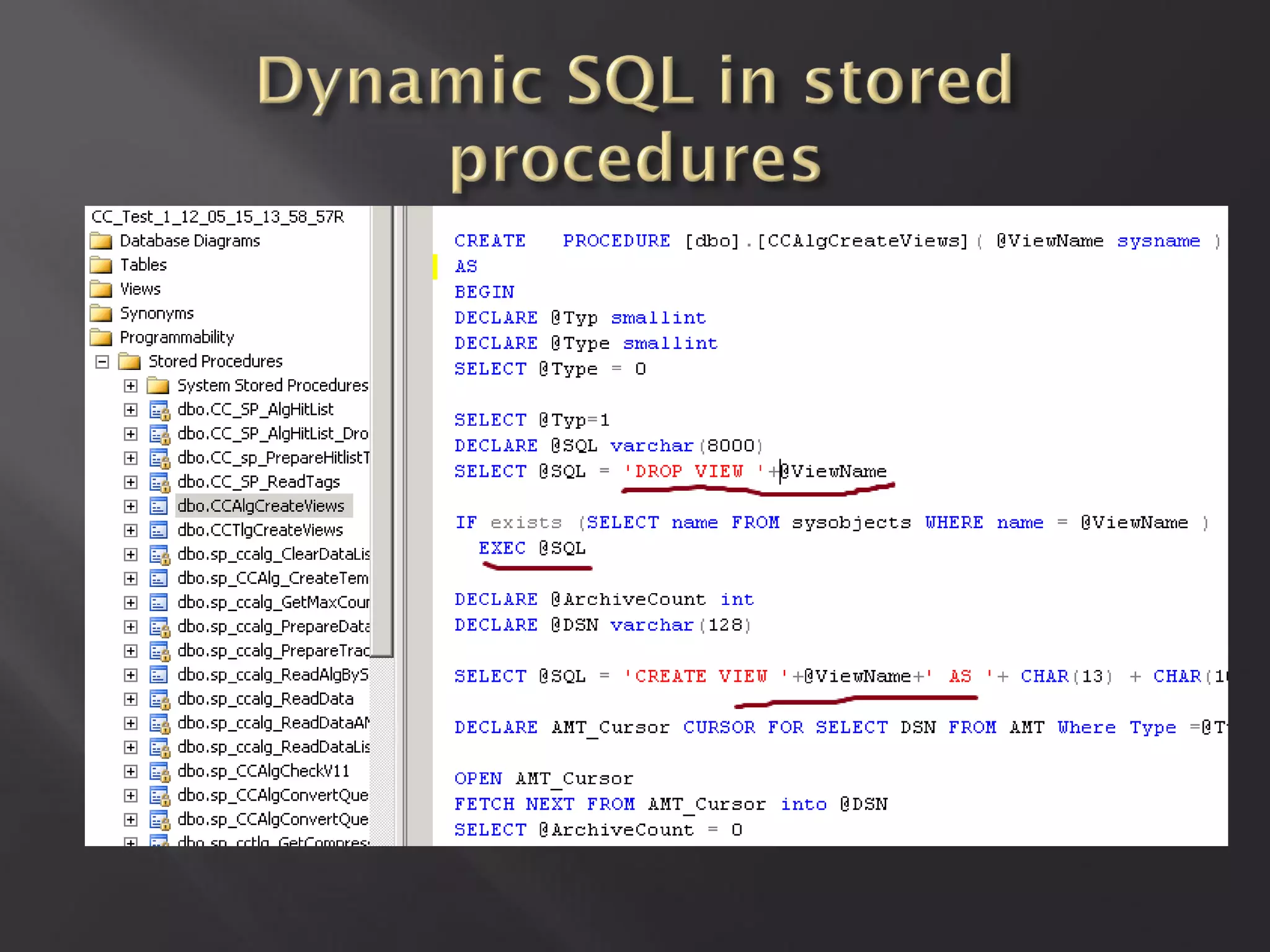
![ Other procedures with SQLi
[dbo].[sp_CCAlg_CreateTempTable]
[dbo].[sp_ccalg_PrepareDataList]
[dbo].[sp_ccalg_PrepareTraceDataList]
[dbo].[sp_ccalg_ReadAlgBySchema]
[dbo].[sp_ccalg_ReadData]
[dbo].[sp_ccalg_ReadDataAMTPreselect]
No way to exploit
Or we don’t know
Yet](https://image.slidesharecdn.com/pt-s42013-scadaunderxrays-130117081345-phpapp01/75/Positive-Technologies-S4-Scada-under-x-rays-51-2048.jpg)