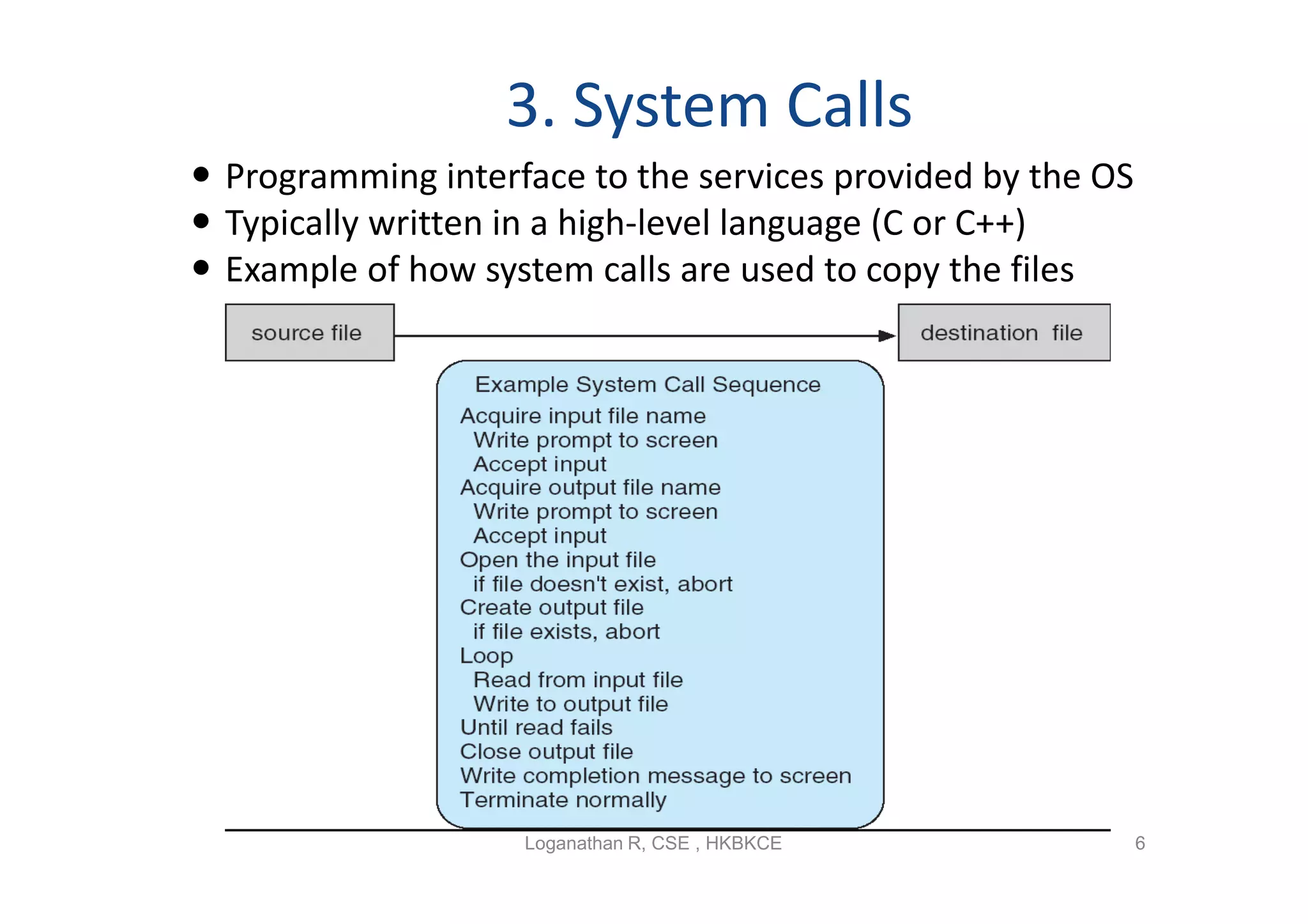
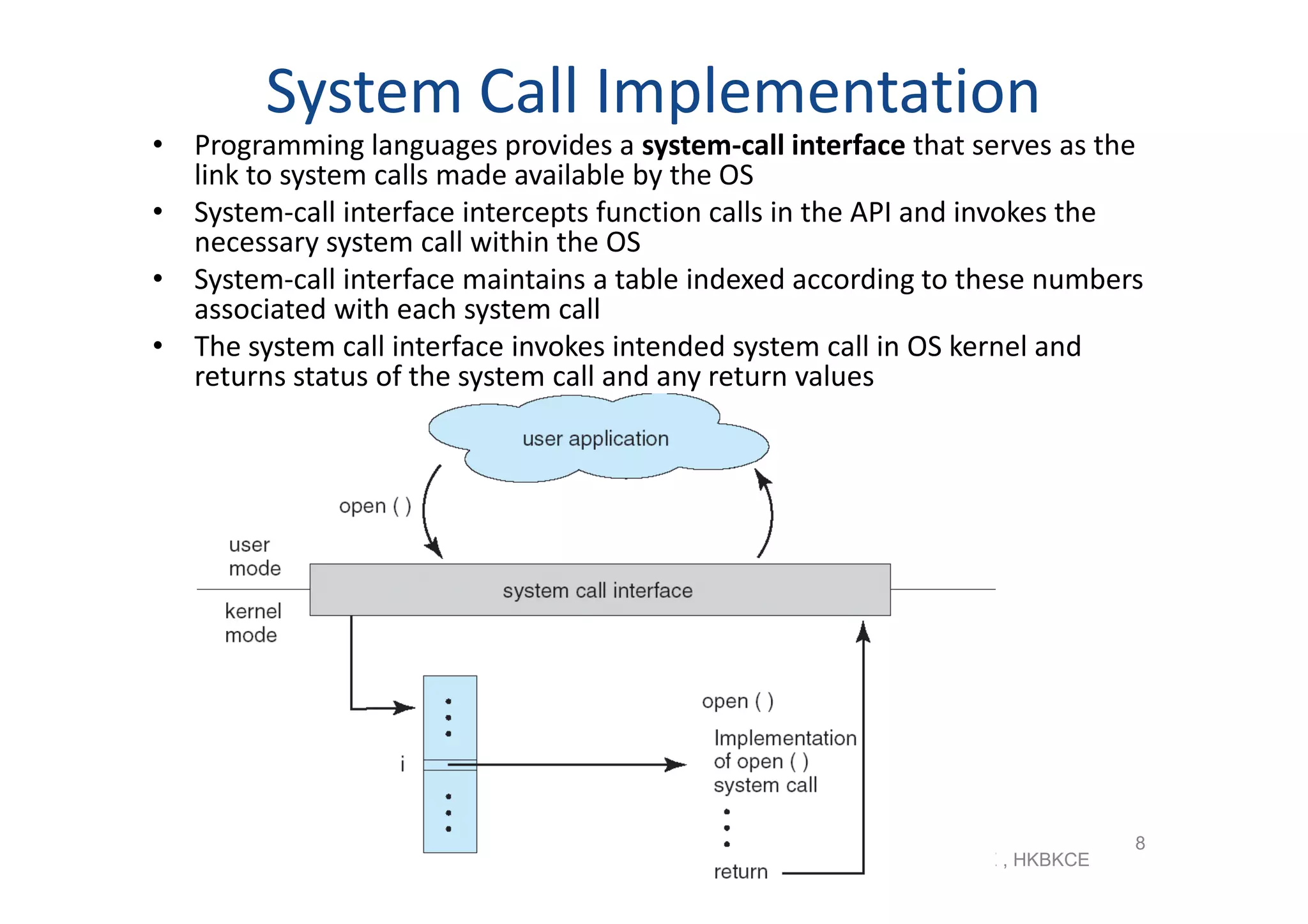
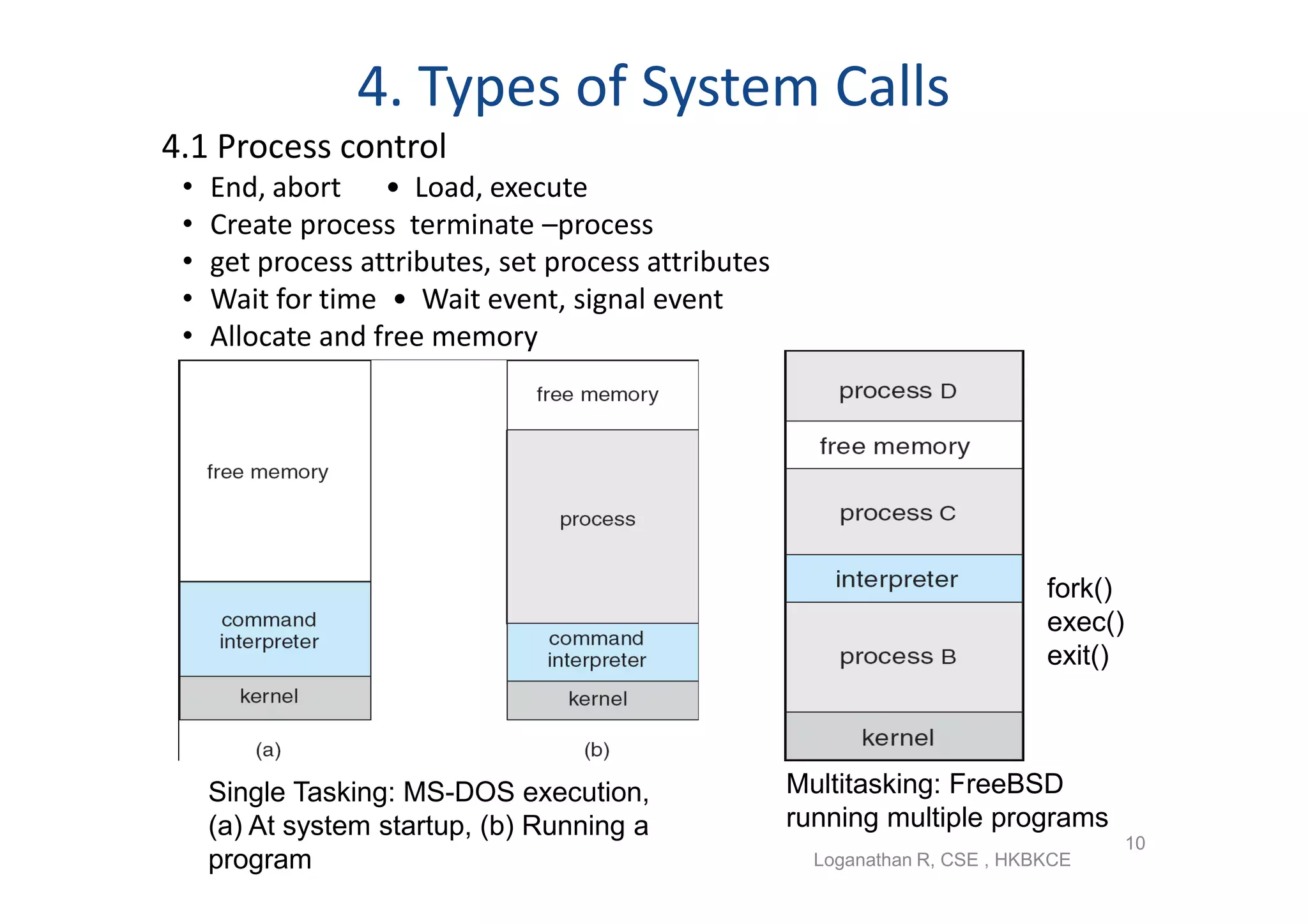
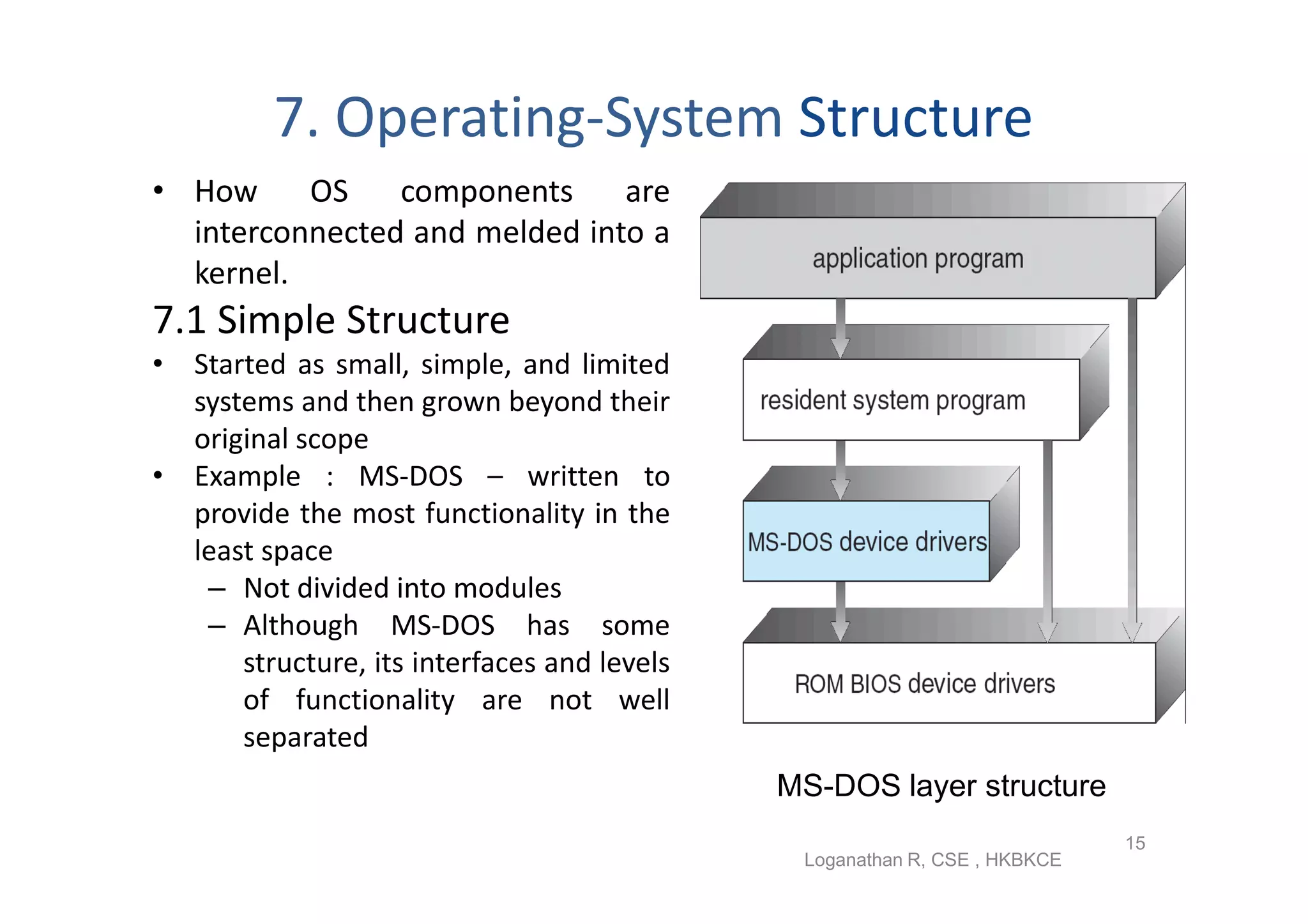
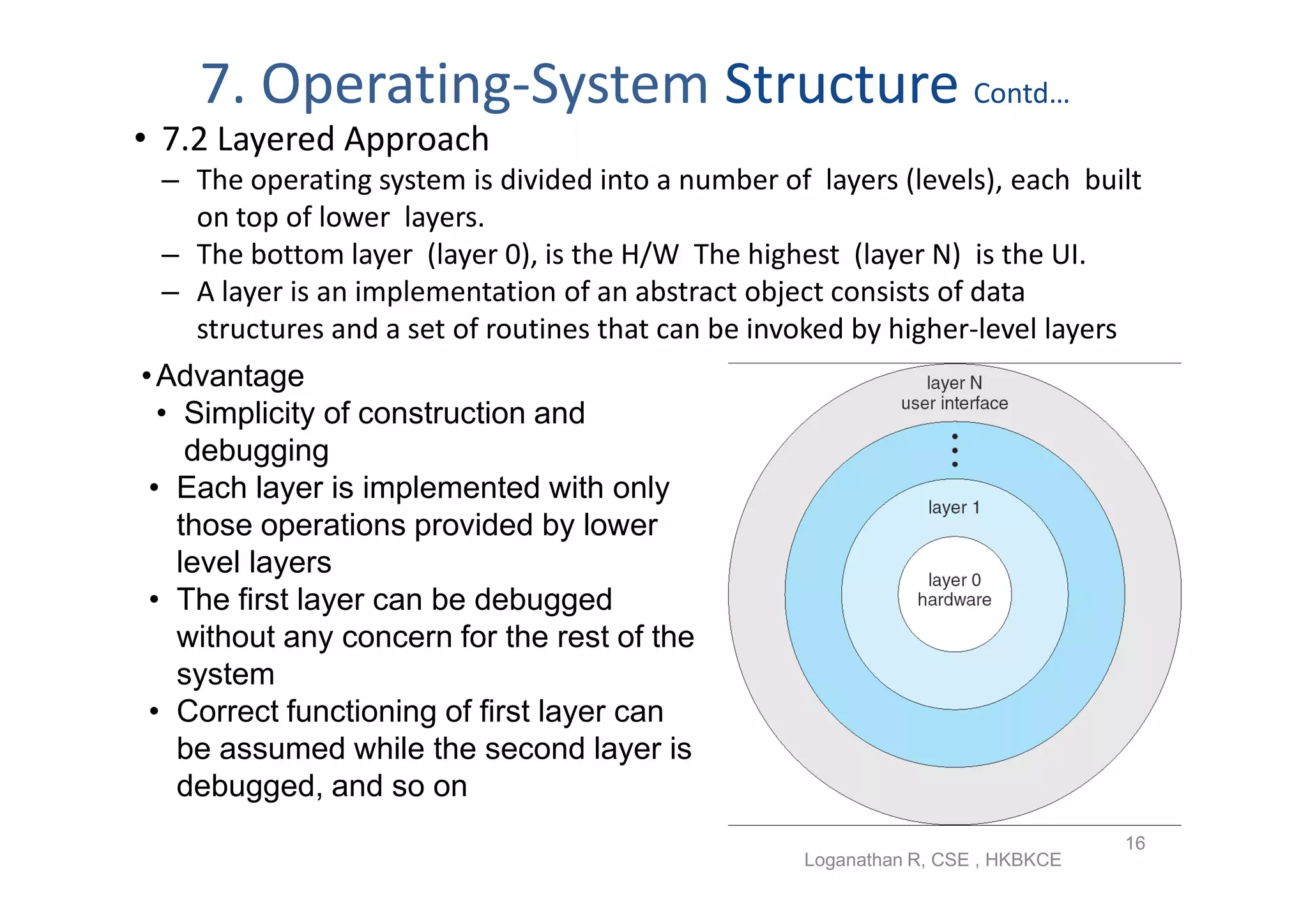
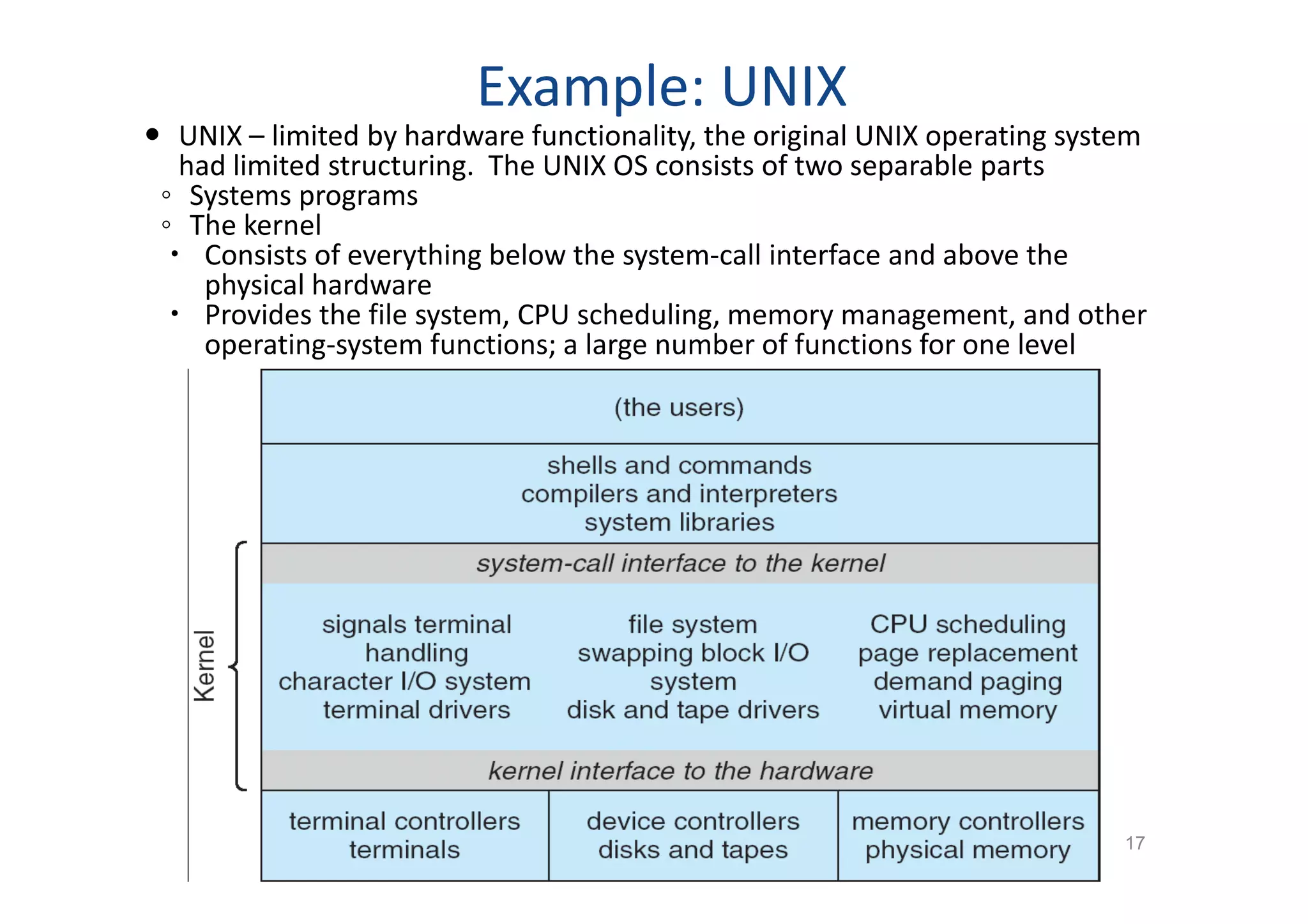
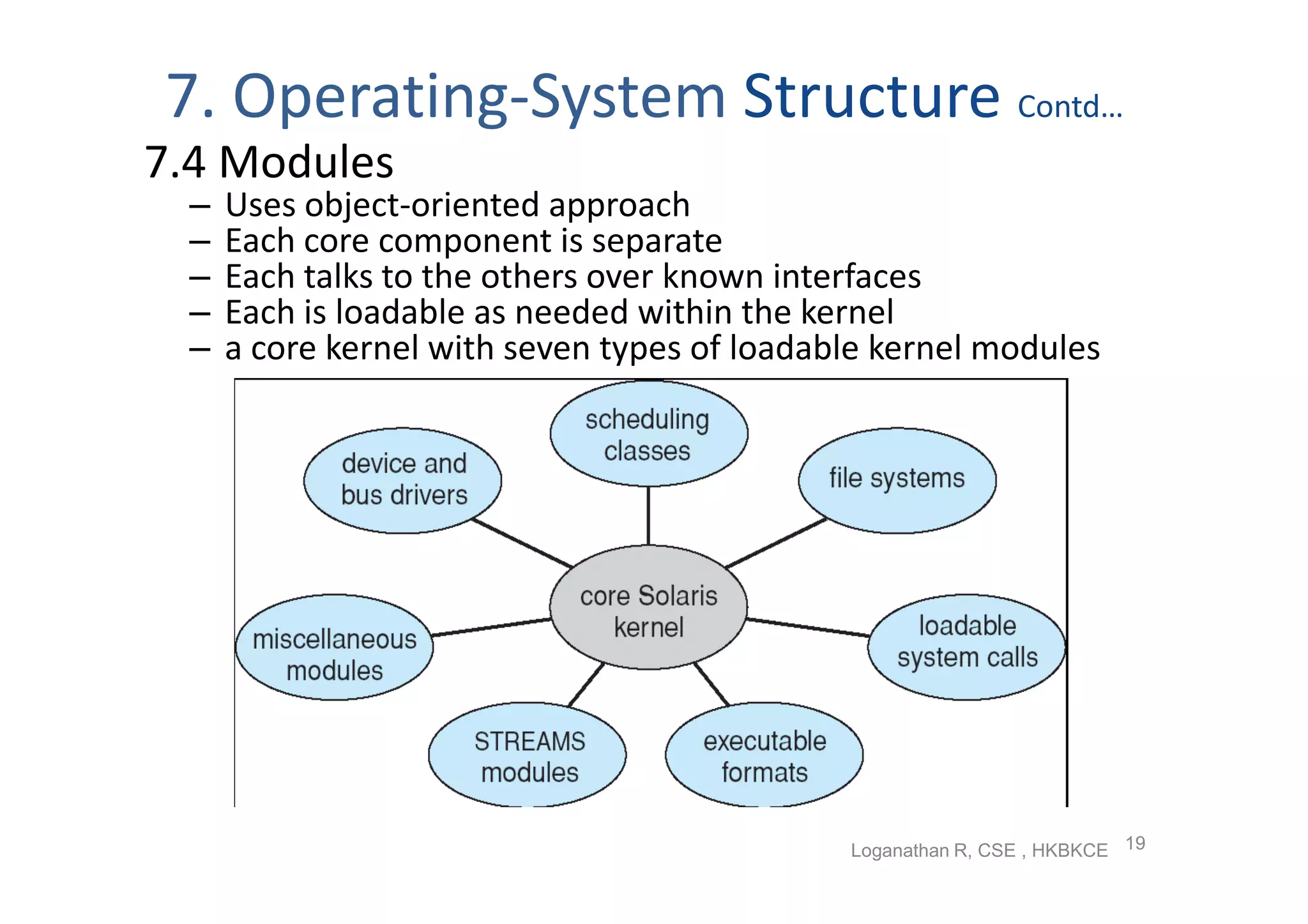
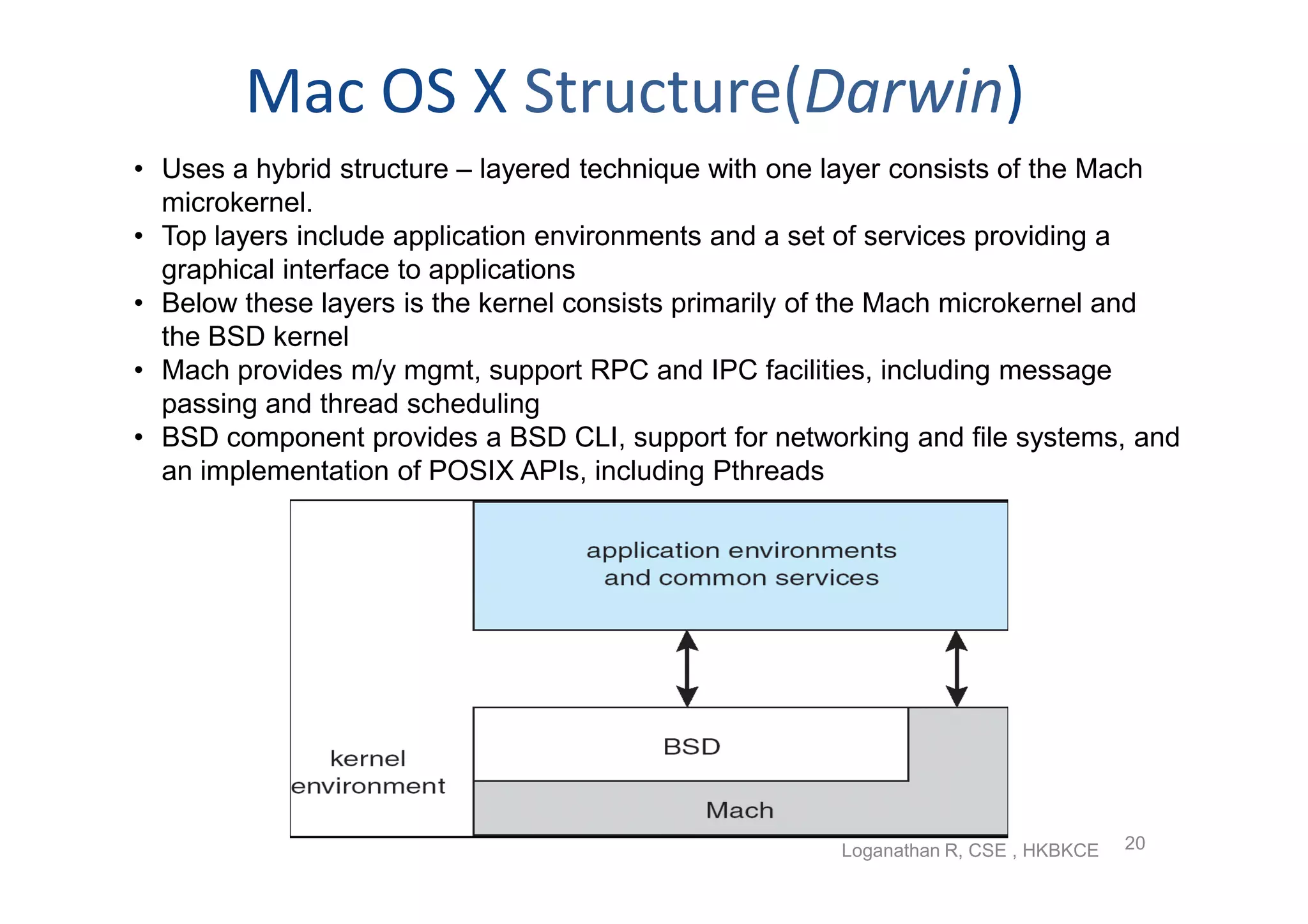
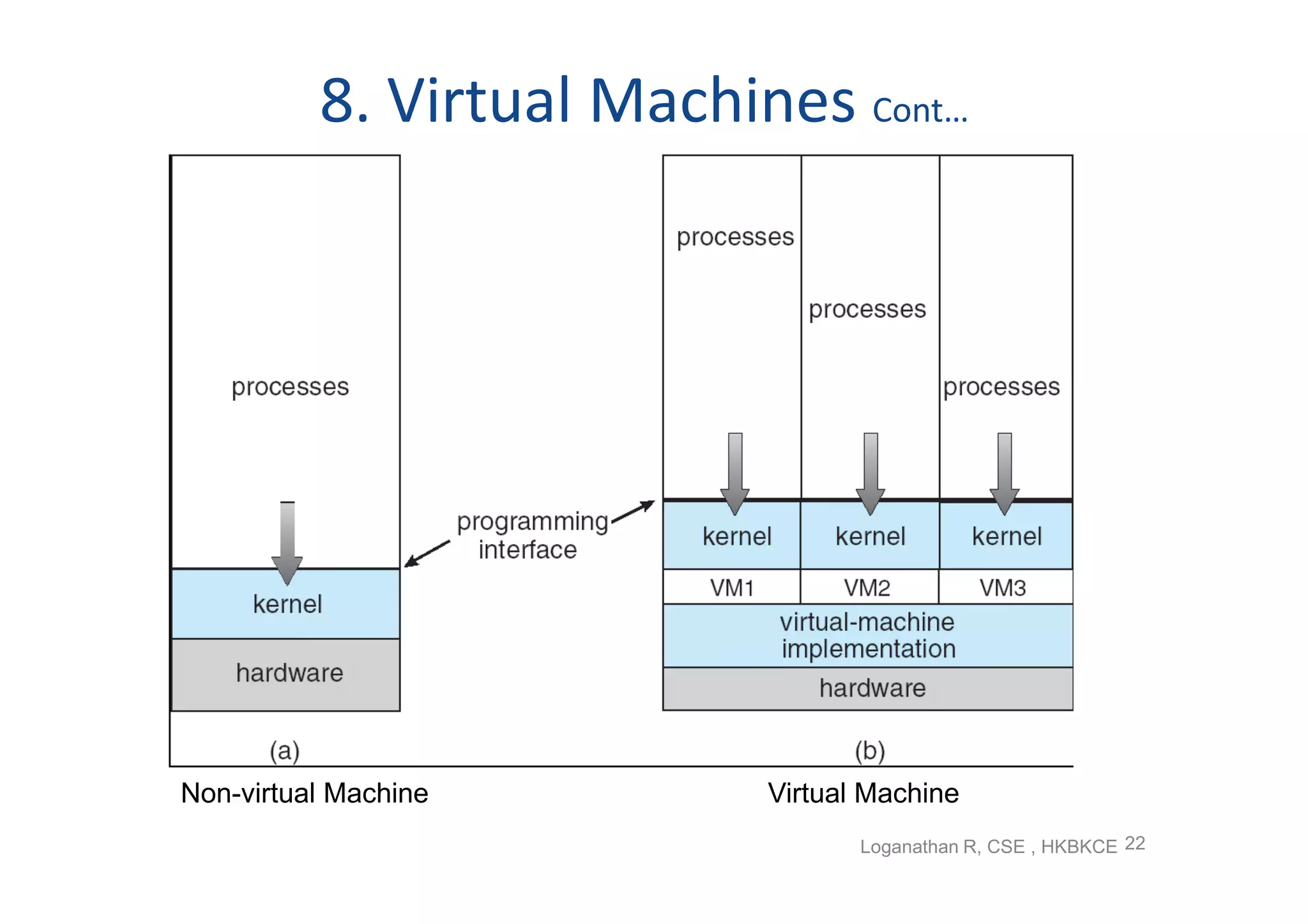
The document discusses the main components of an operating system including operating system services like user interfaces, resource management, and error detection. It describes system calls which are the programming interface to OS services and how they are implemented. The document also outlines different types of system calls for processes, files, devices, and communications and covers system programs that provide file management, system information, and programming language support.