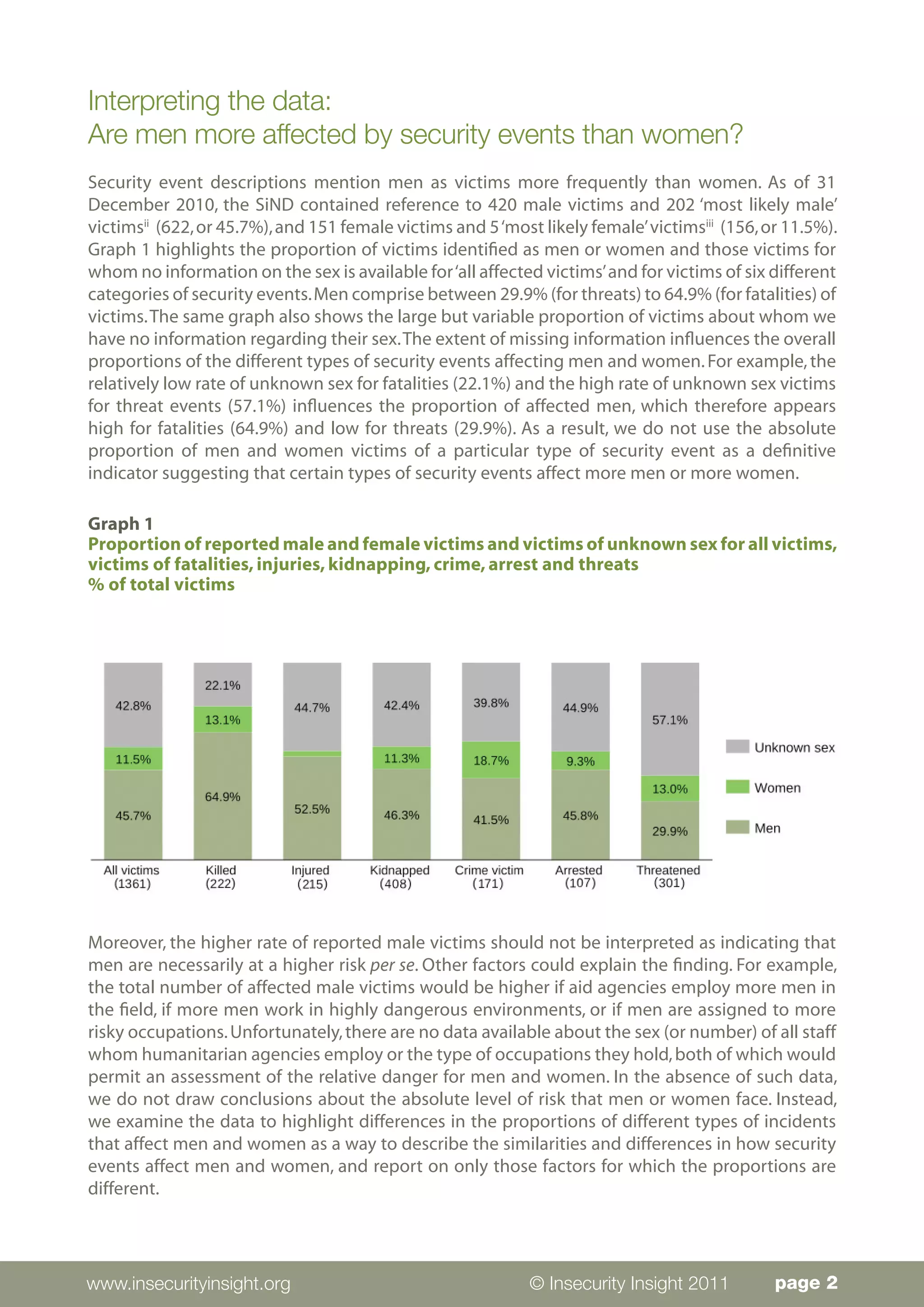
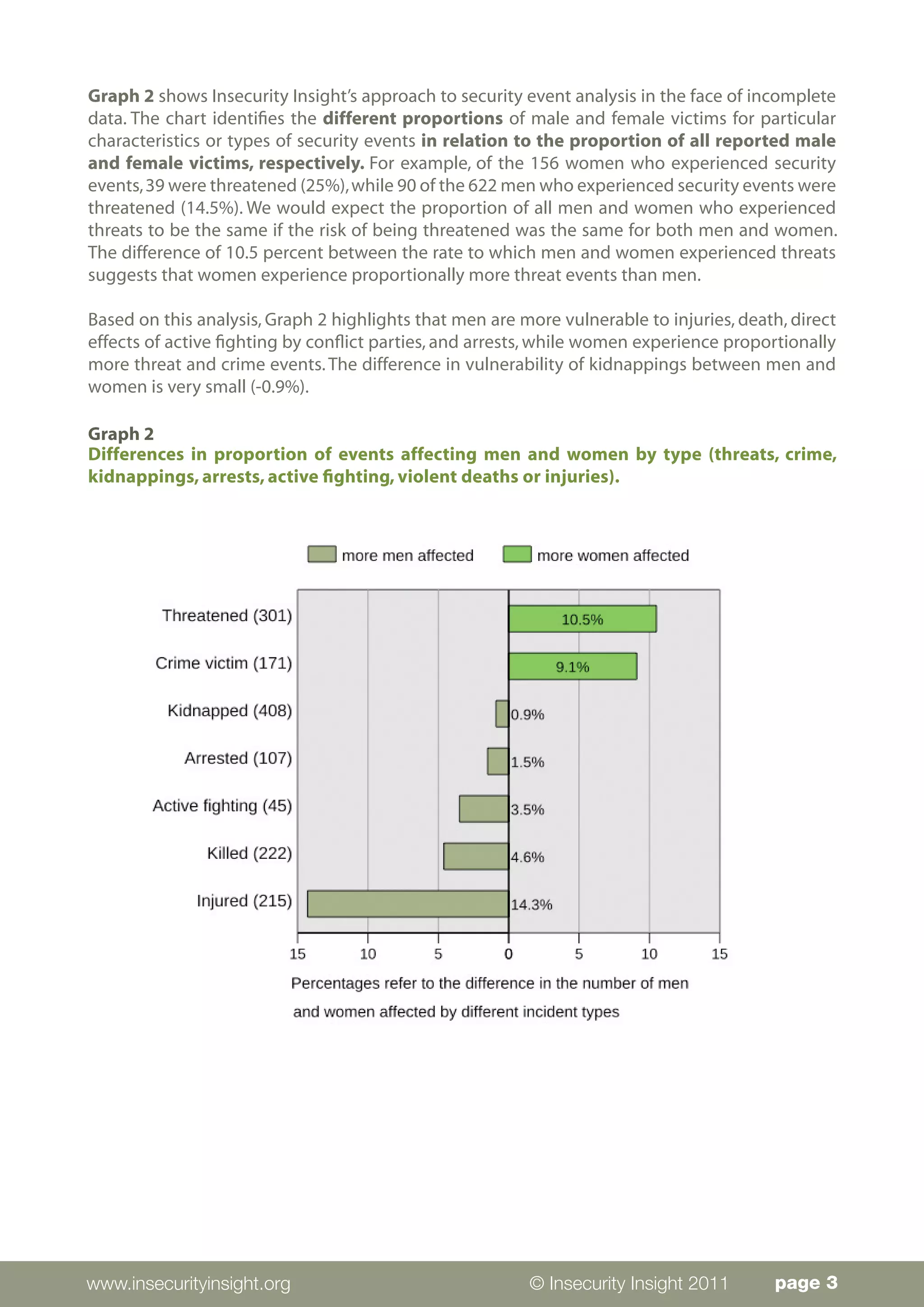
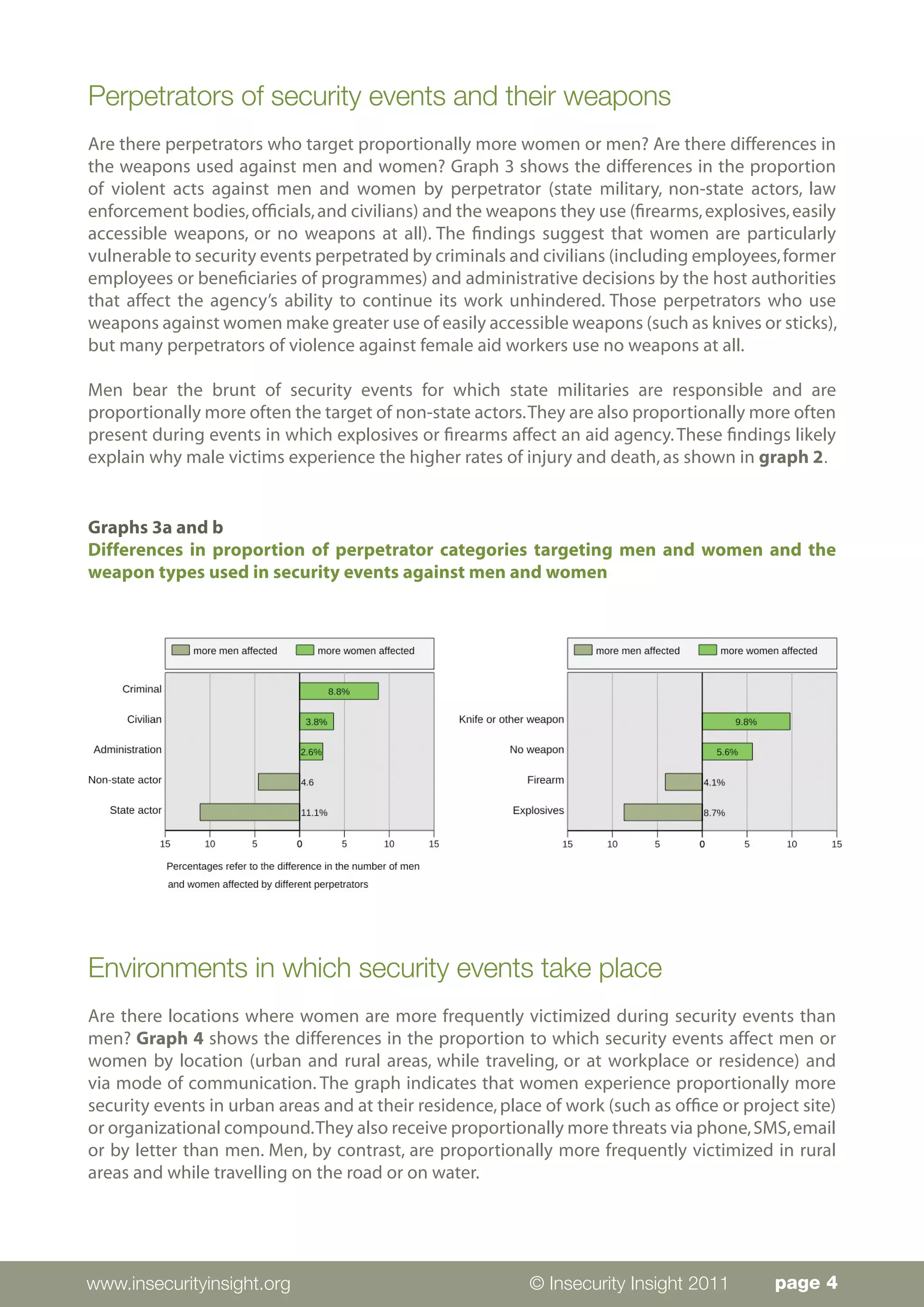
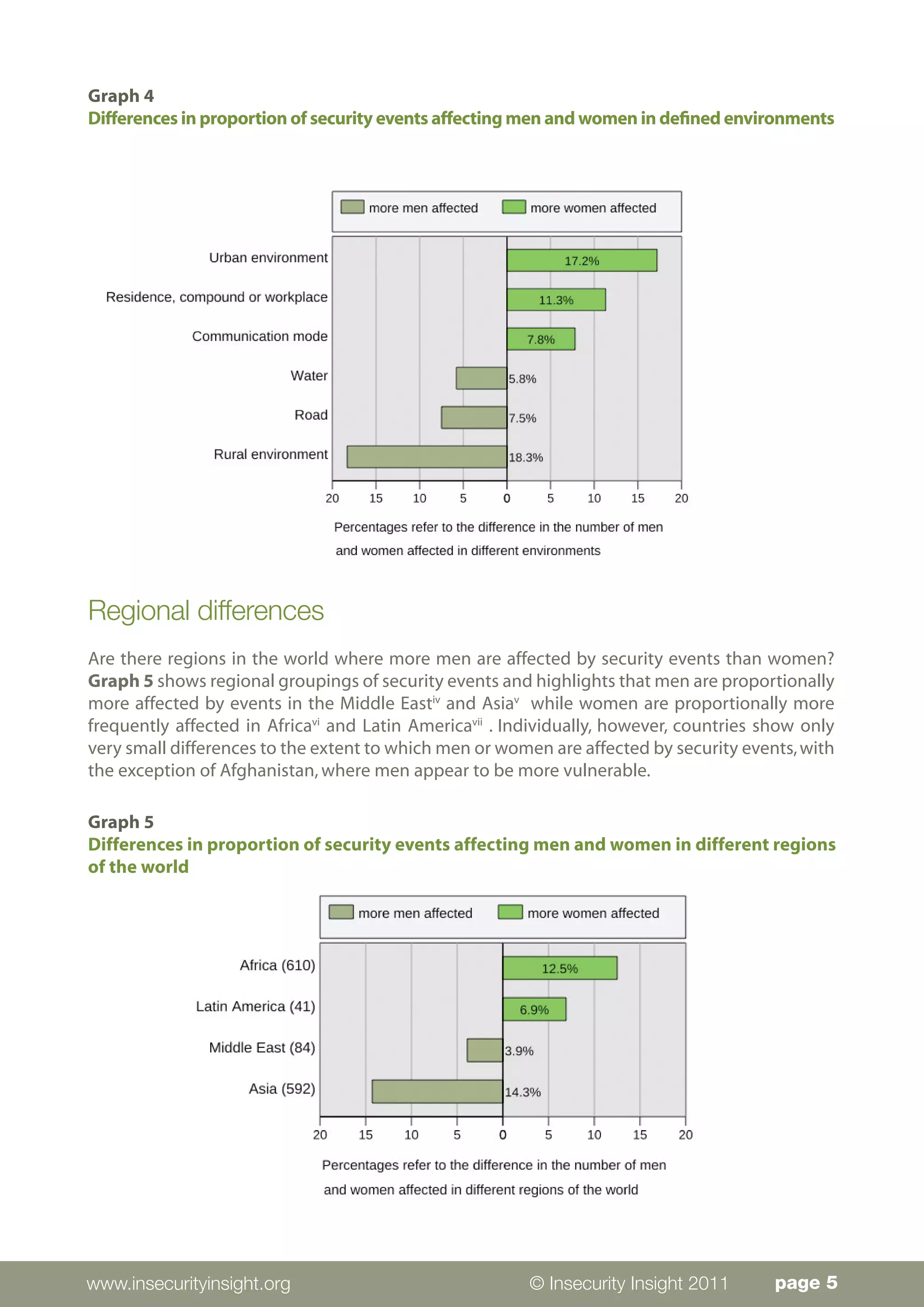
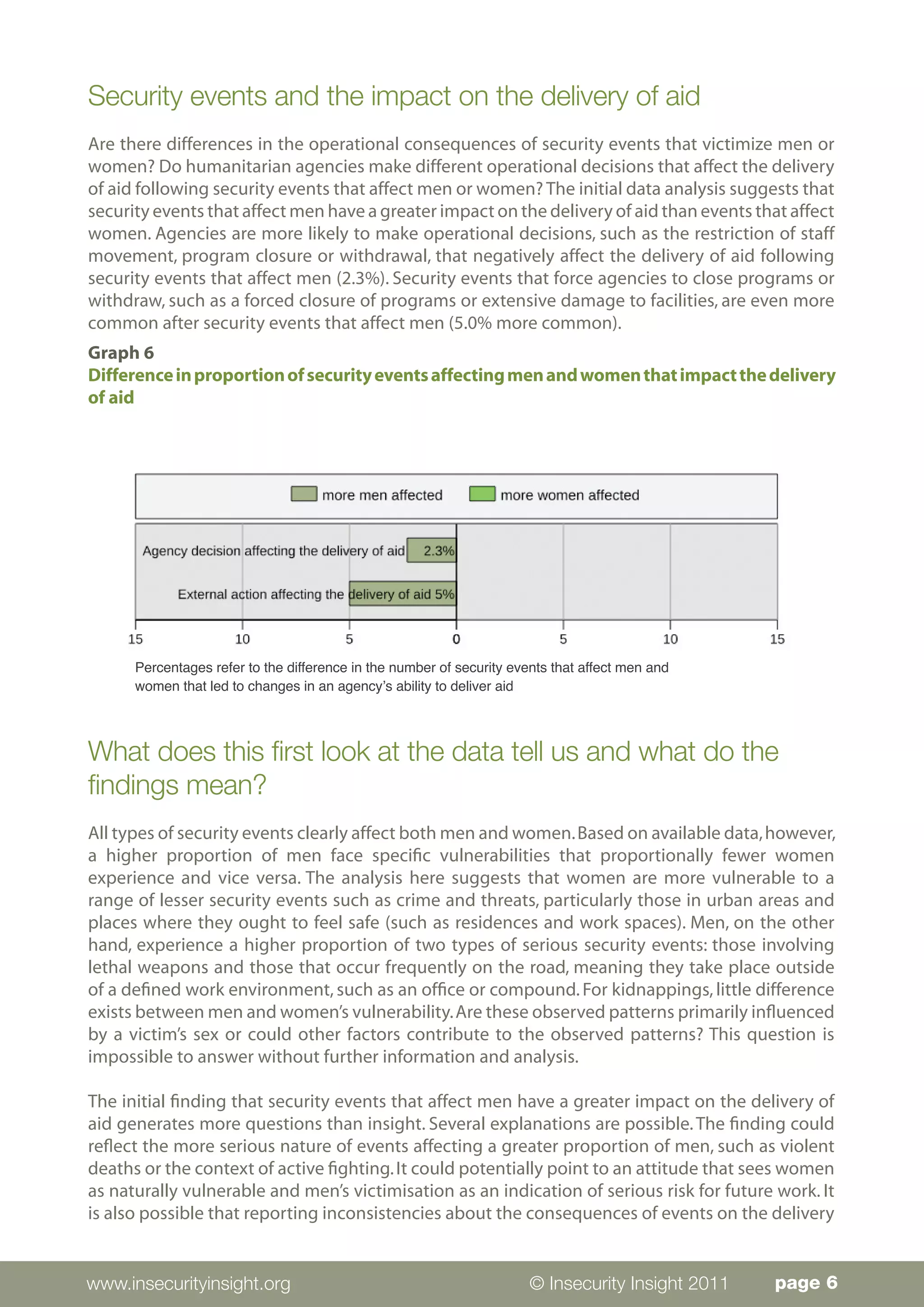
Men and women experience security events affecting aid workers in gendered ways. The data analyzed comes from 1,361 aid workers affected in 615 incidents between 2008-2010, though gender information was missing for 583 victims. While men comprised the majority (622) of reported victims, the data is limited and does not indicate differing risk levels. The analysis found that women experience proportionally more threats and crime-related events in urban areas and at residences/workplaces. Men experience more injuries/deaths from state militaries and non-state actors during travel or in rural areas. Regionally, men are more affected in the Middle East and Asia while women face more events in Africa and Latin America.