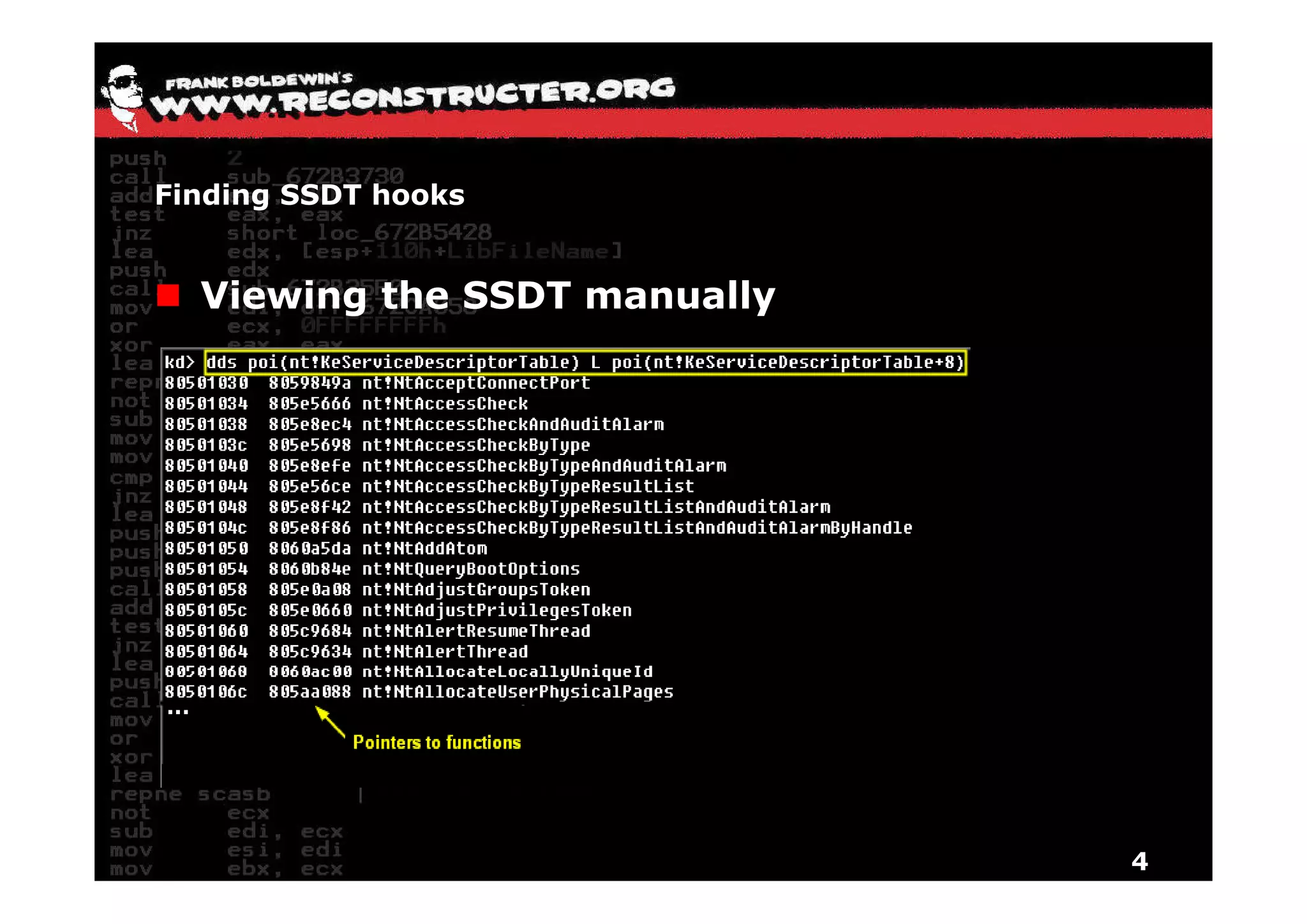
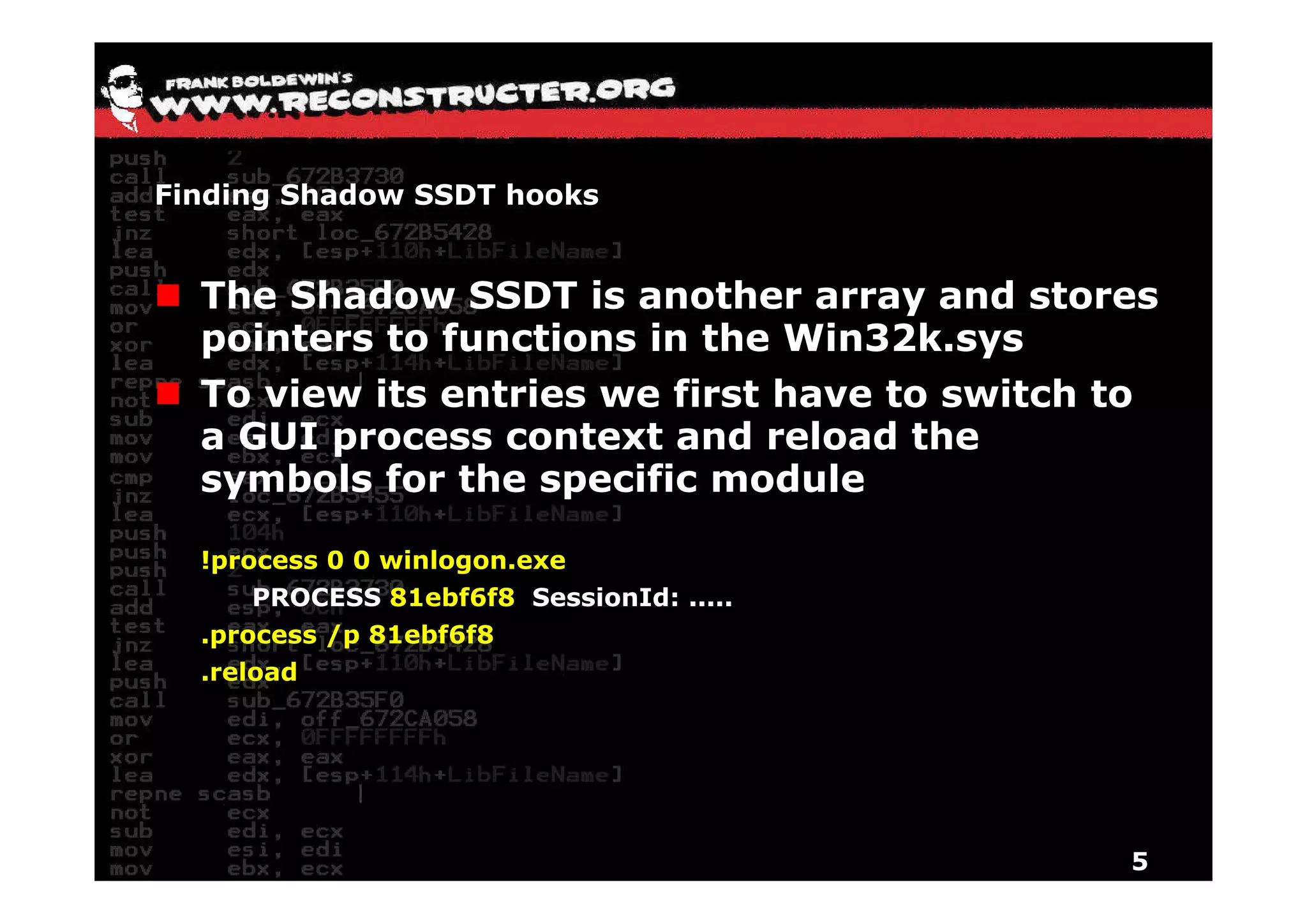
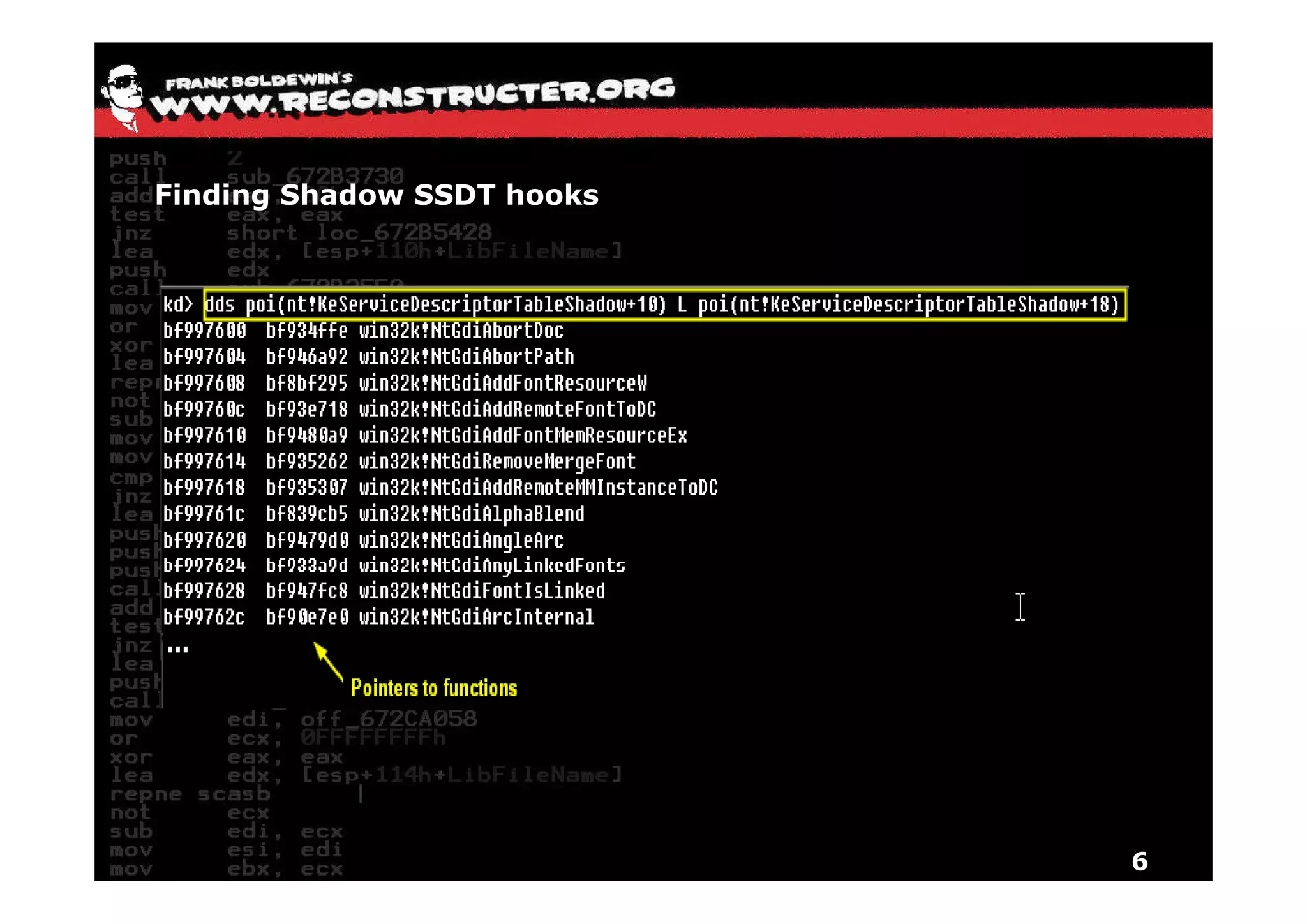
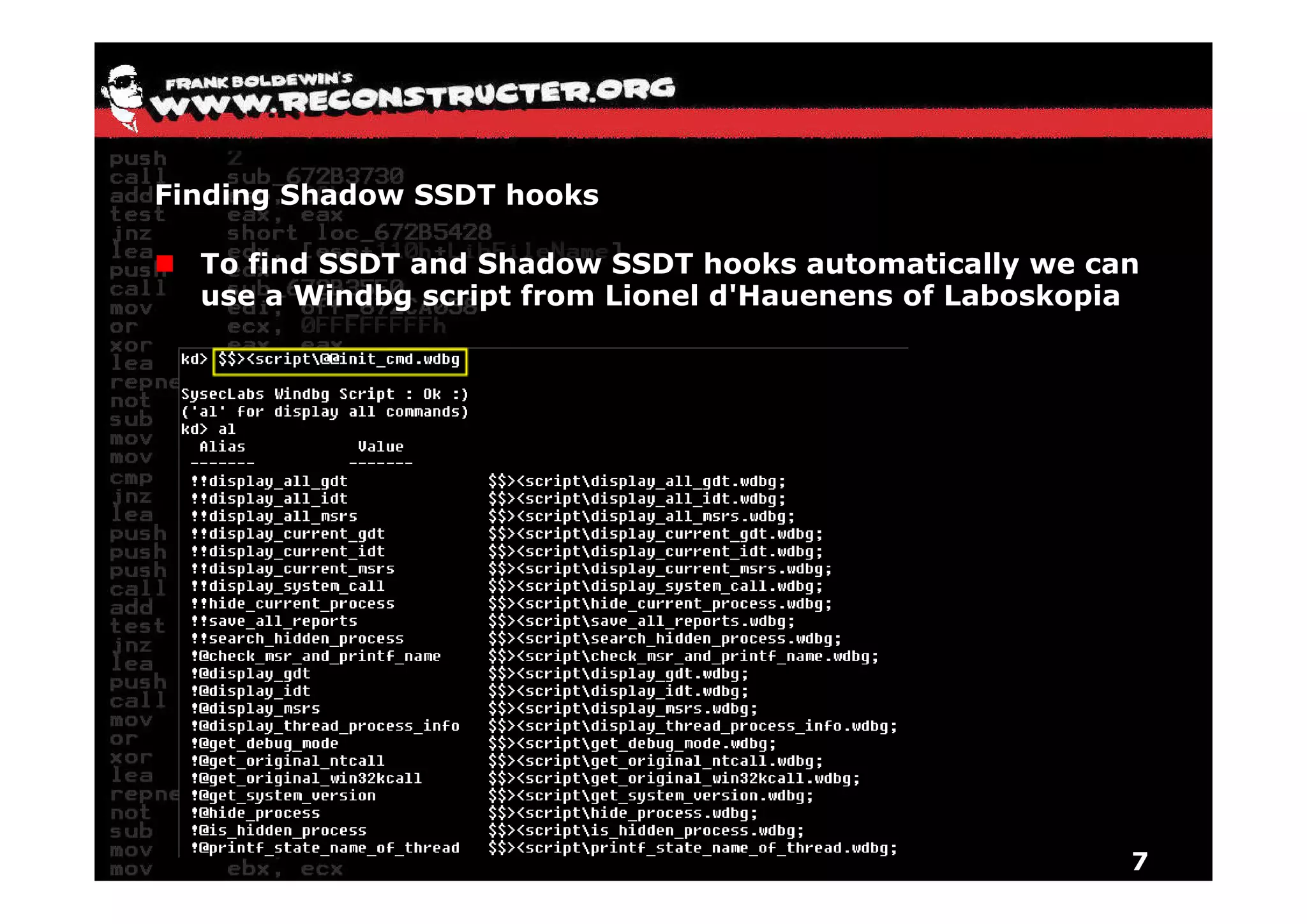
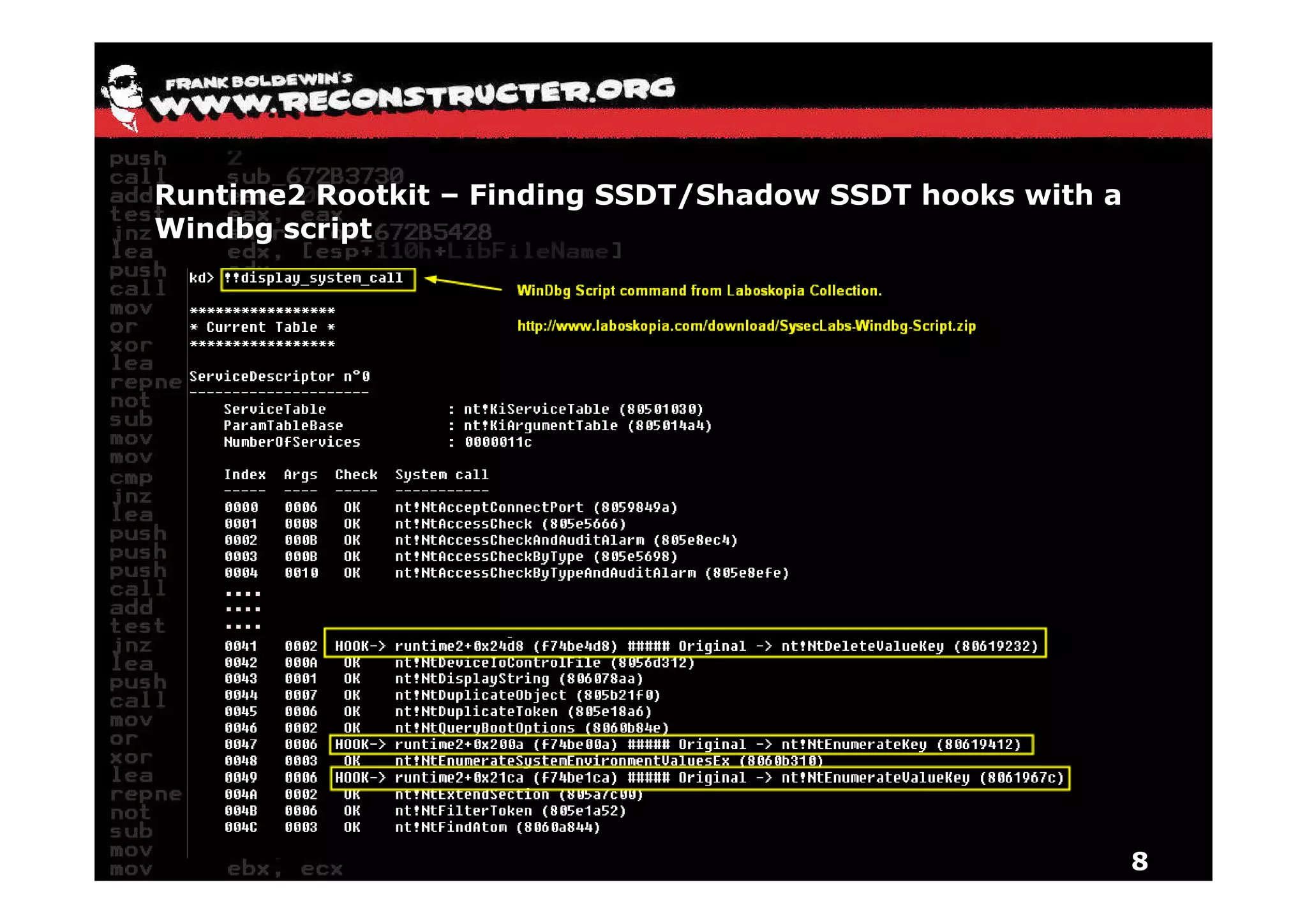
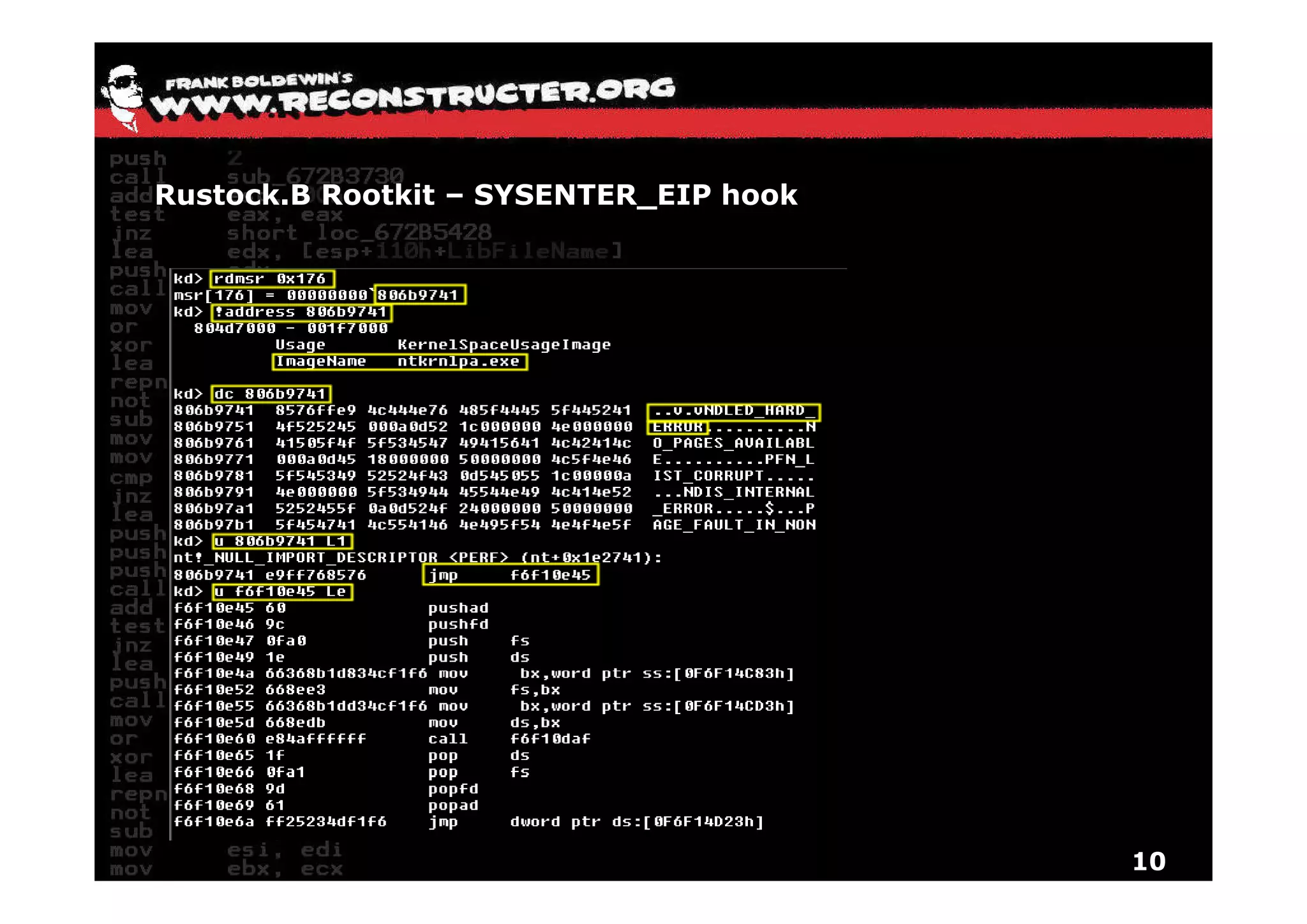
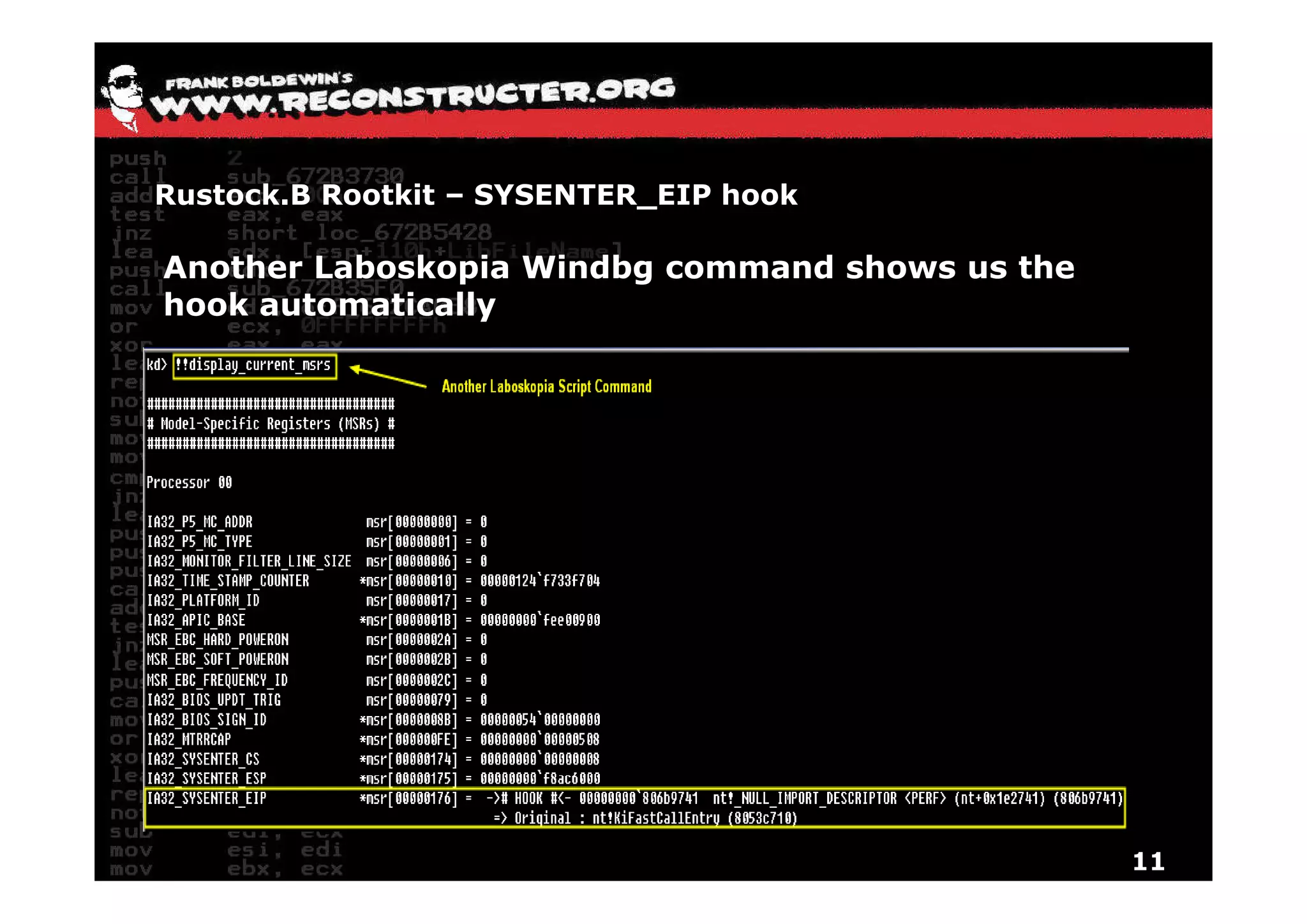
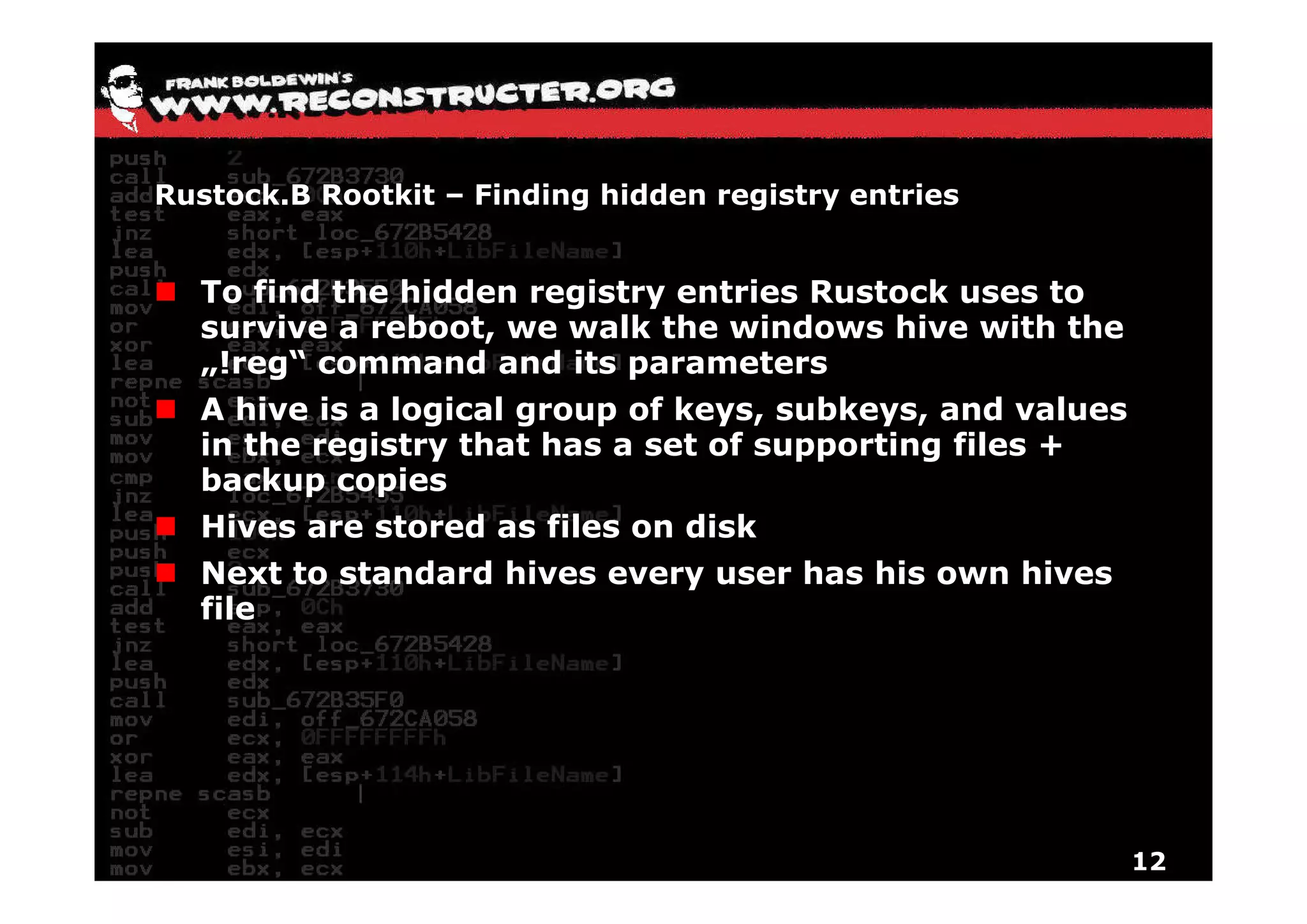
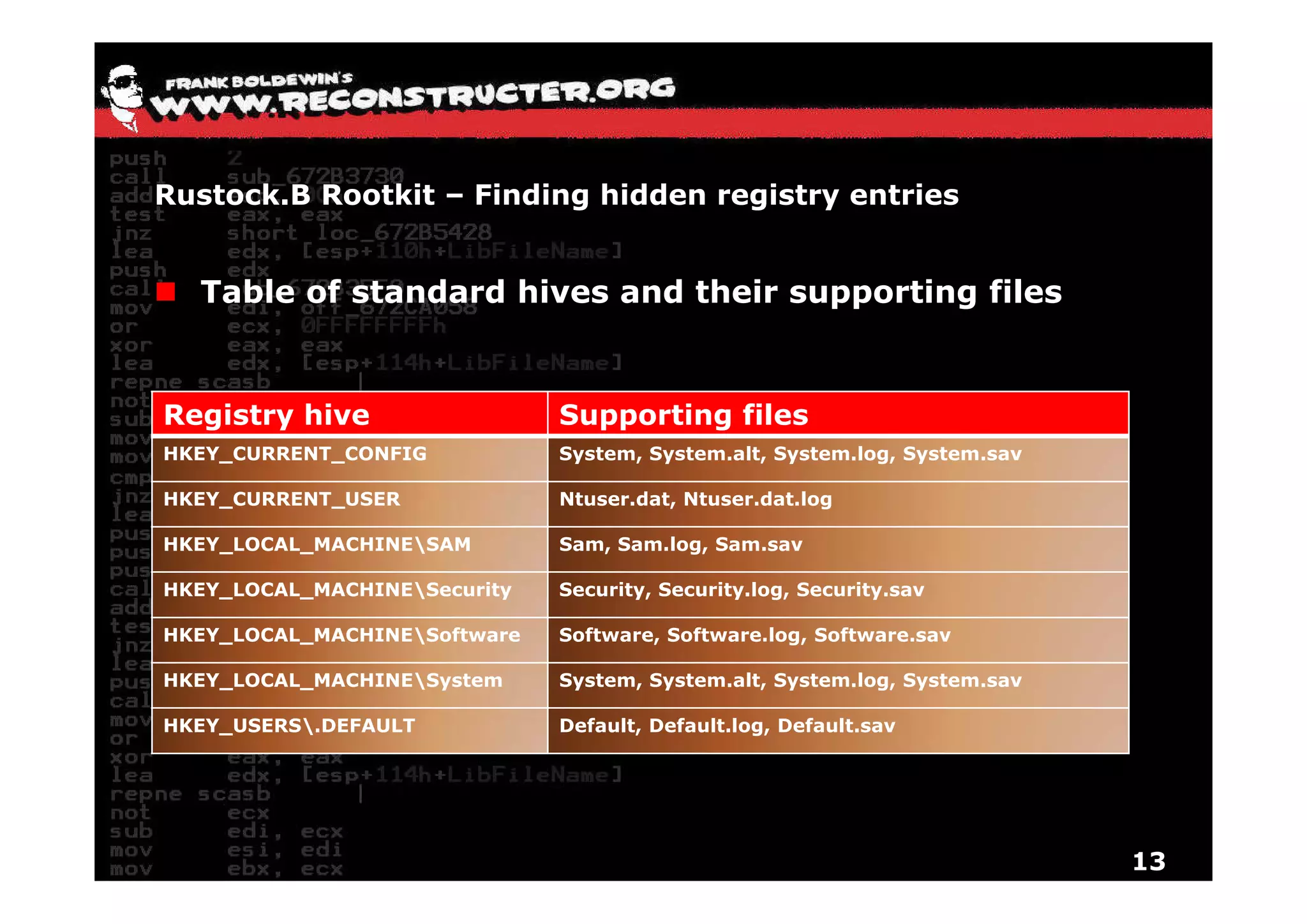
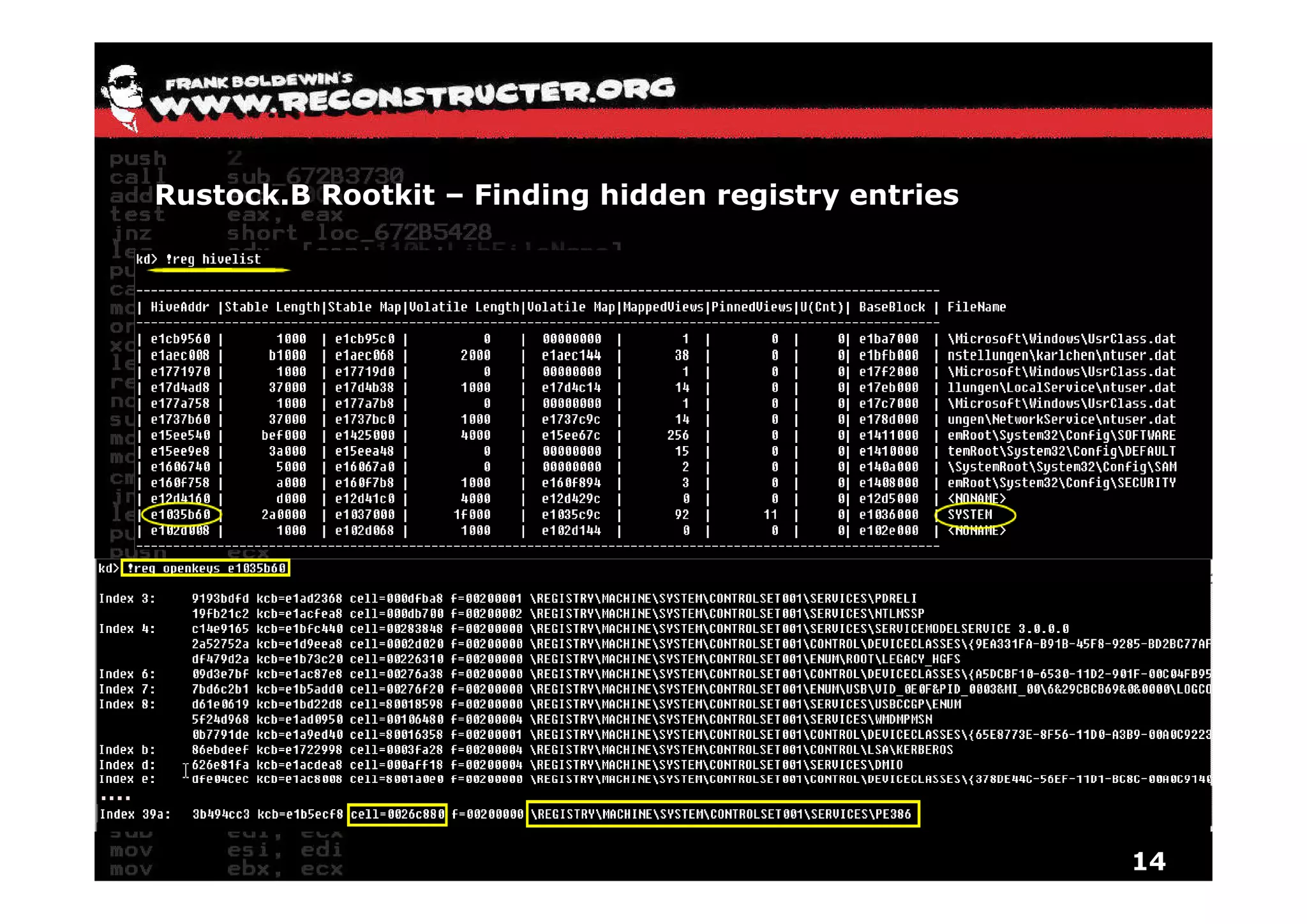
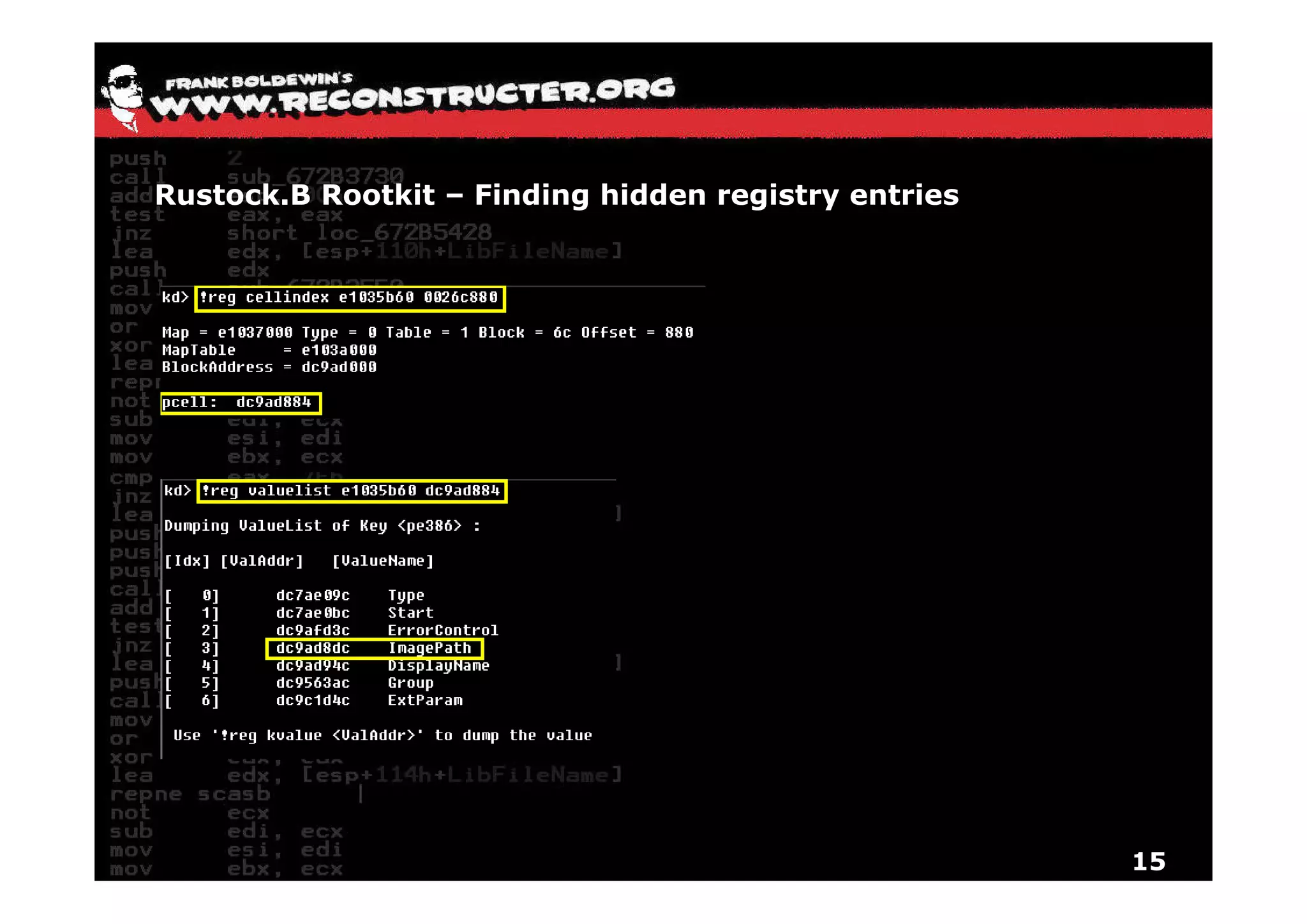
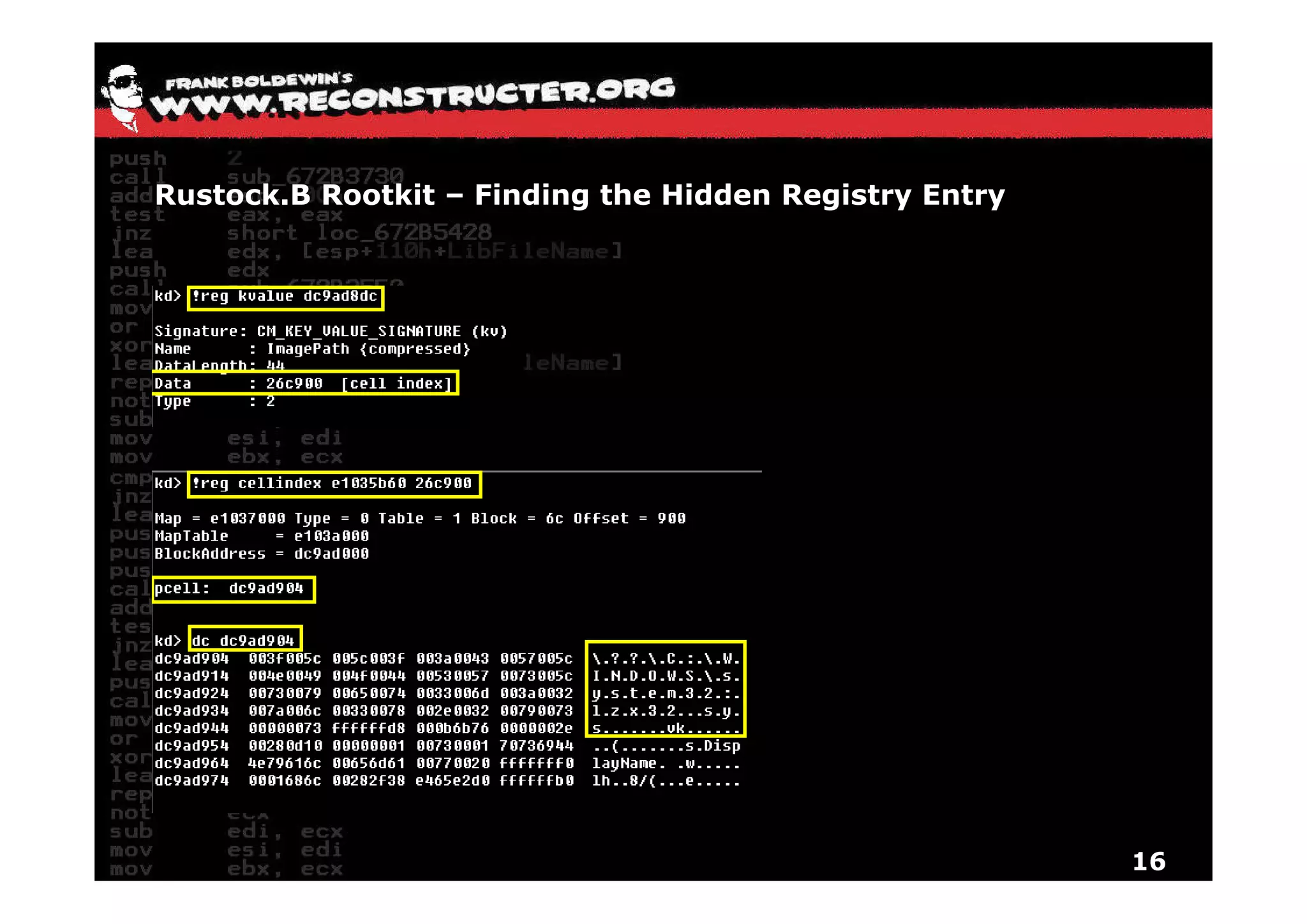
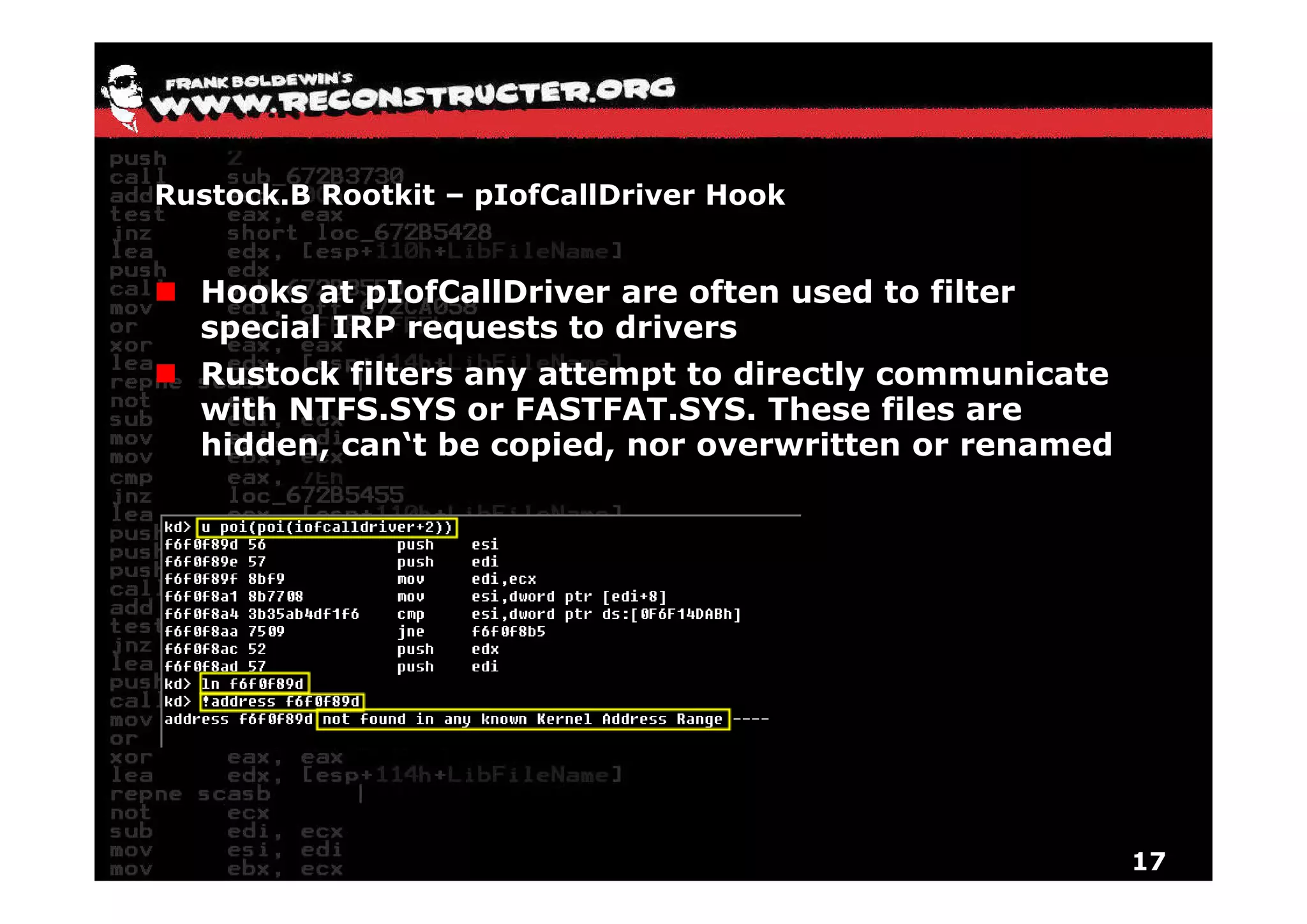
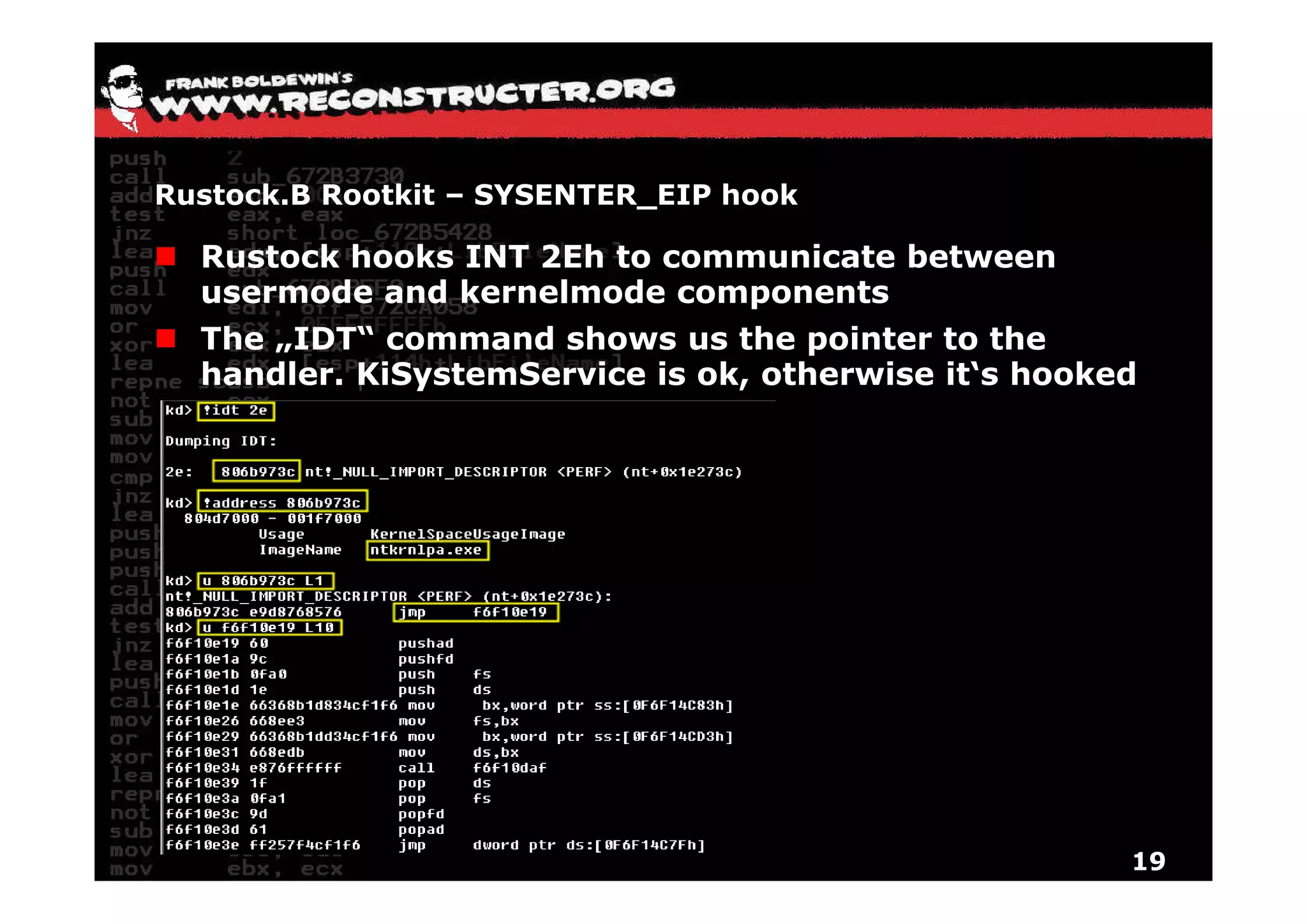
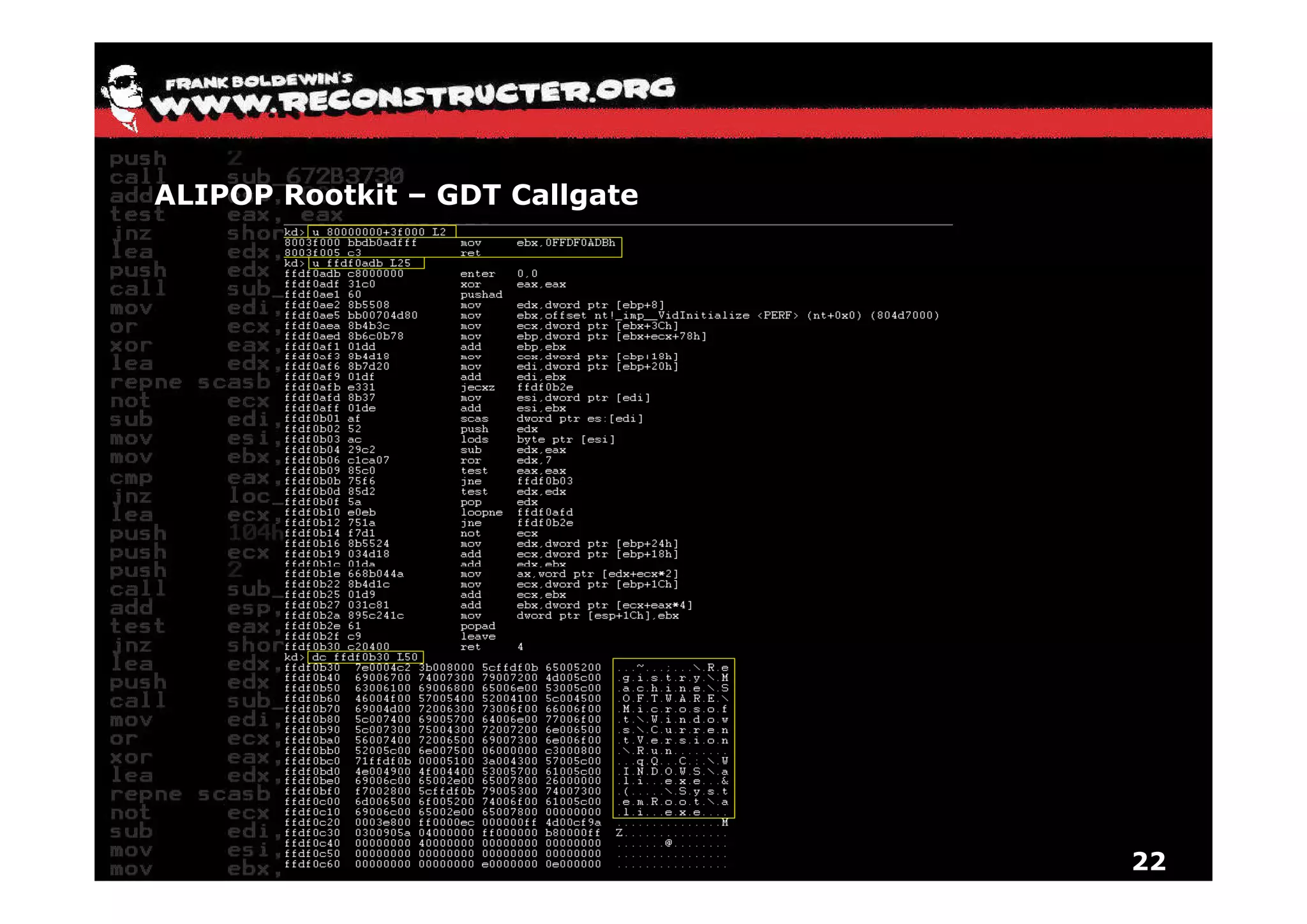
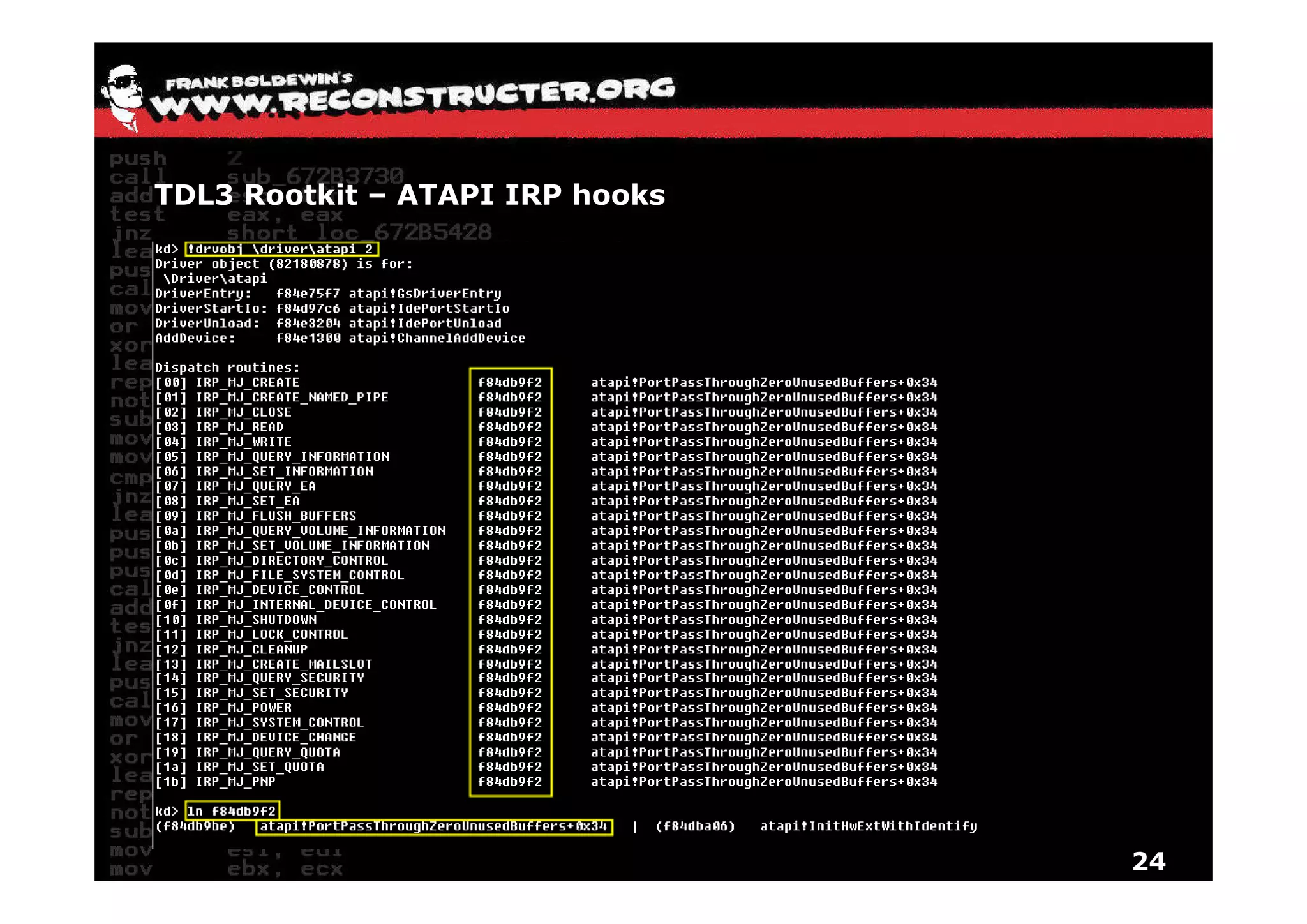
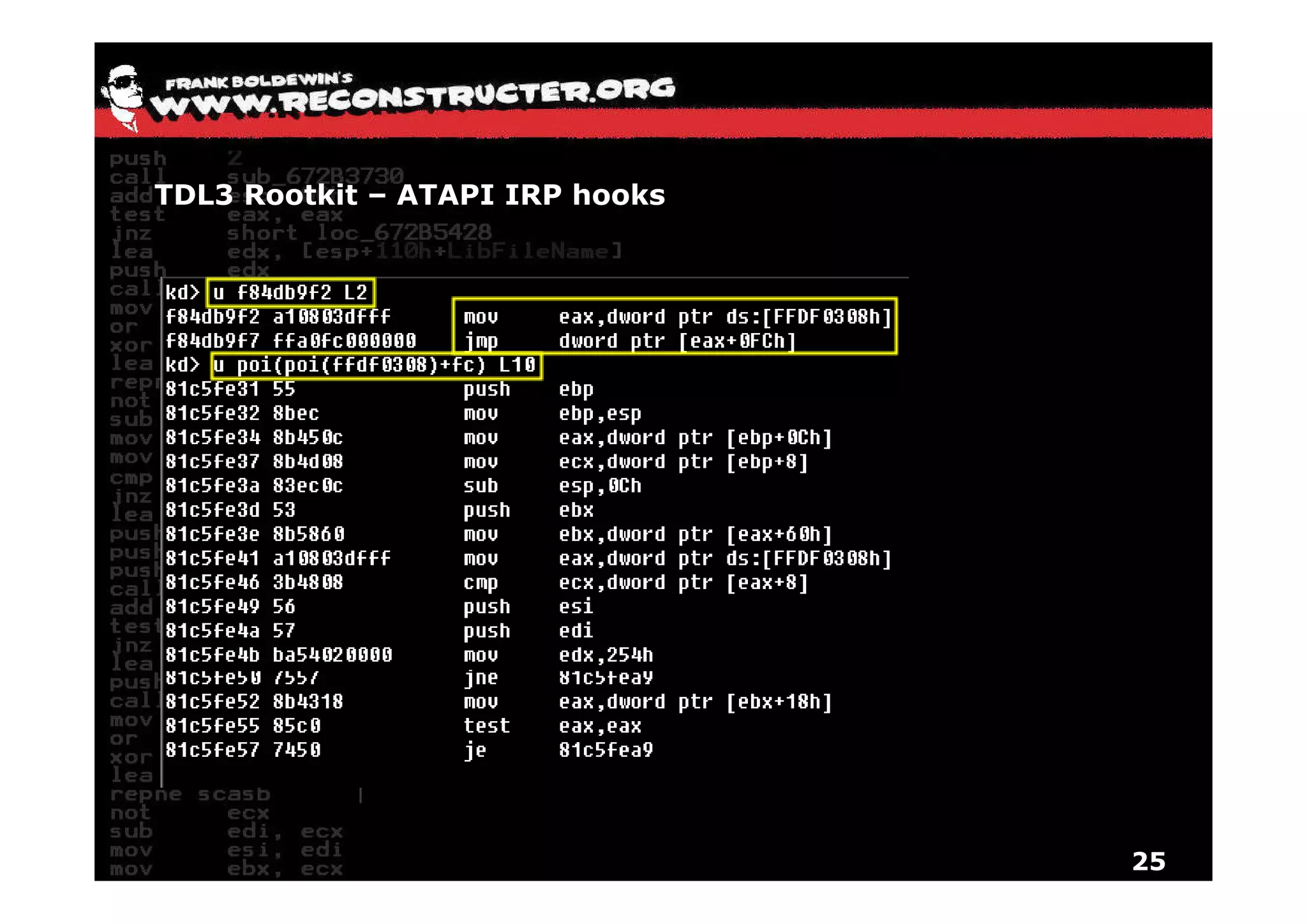
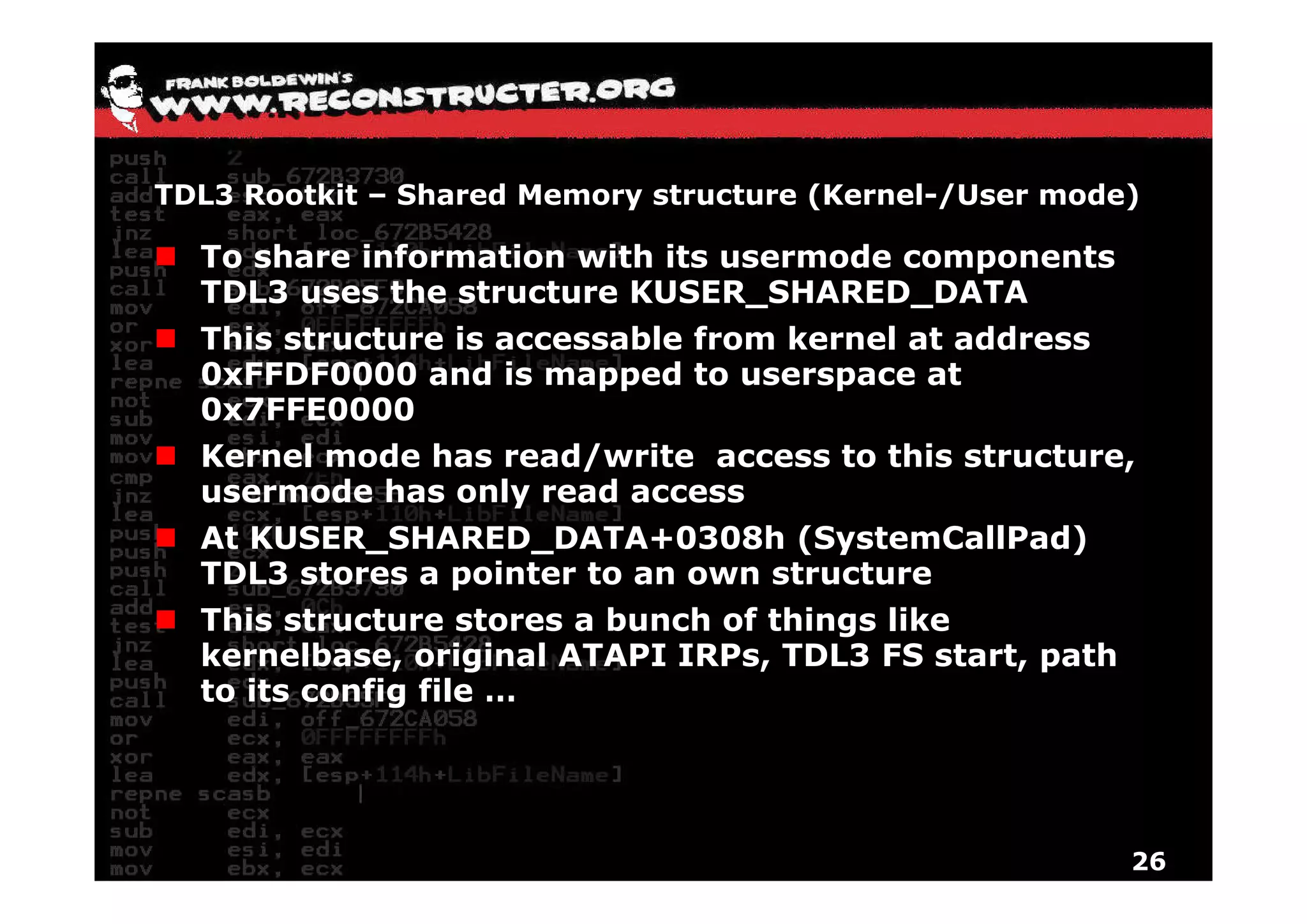
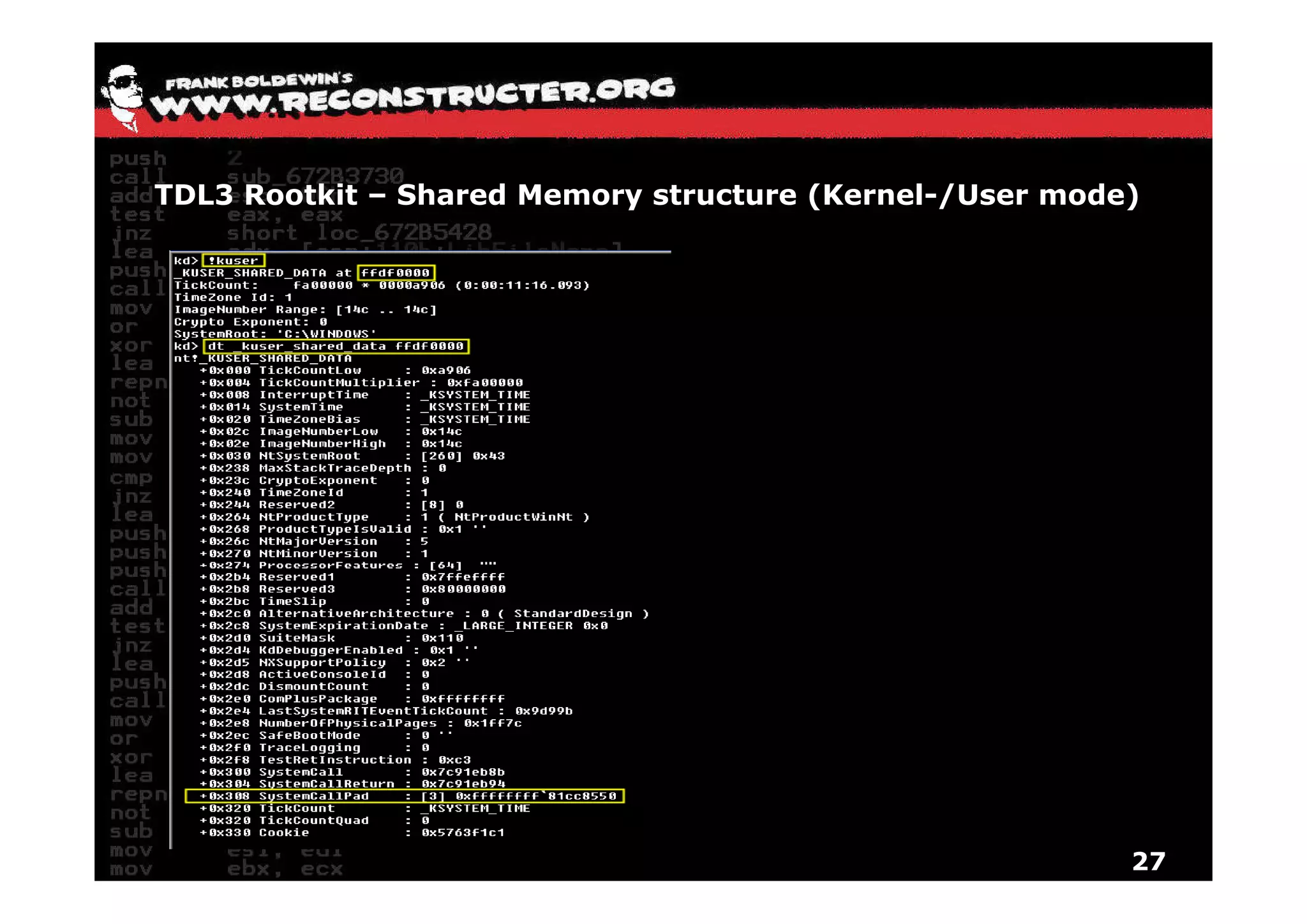
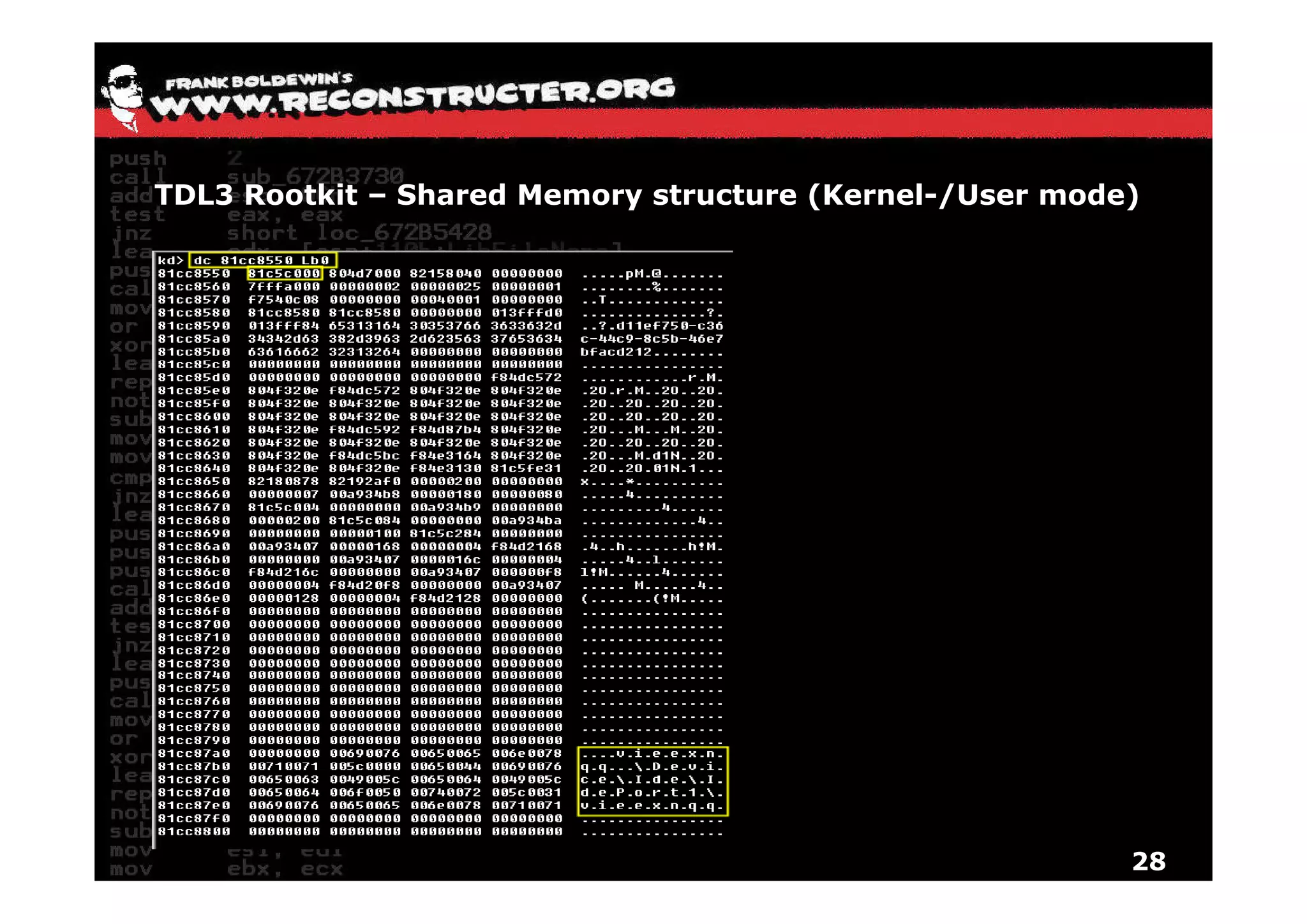
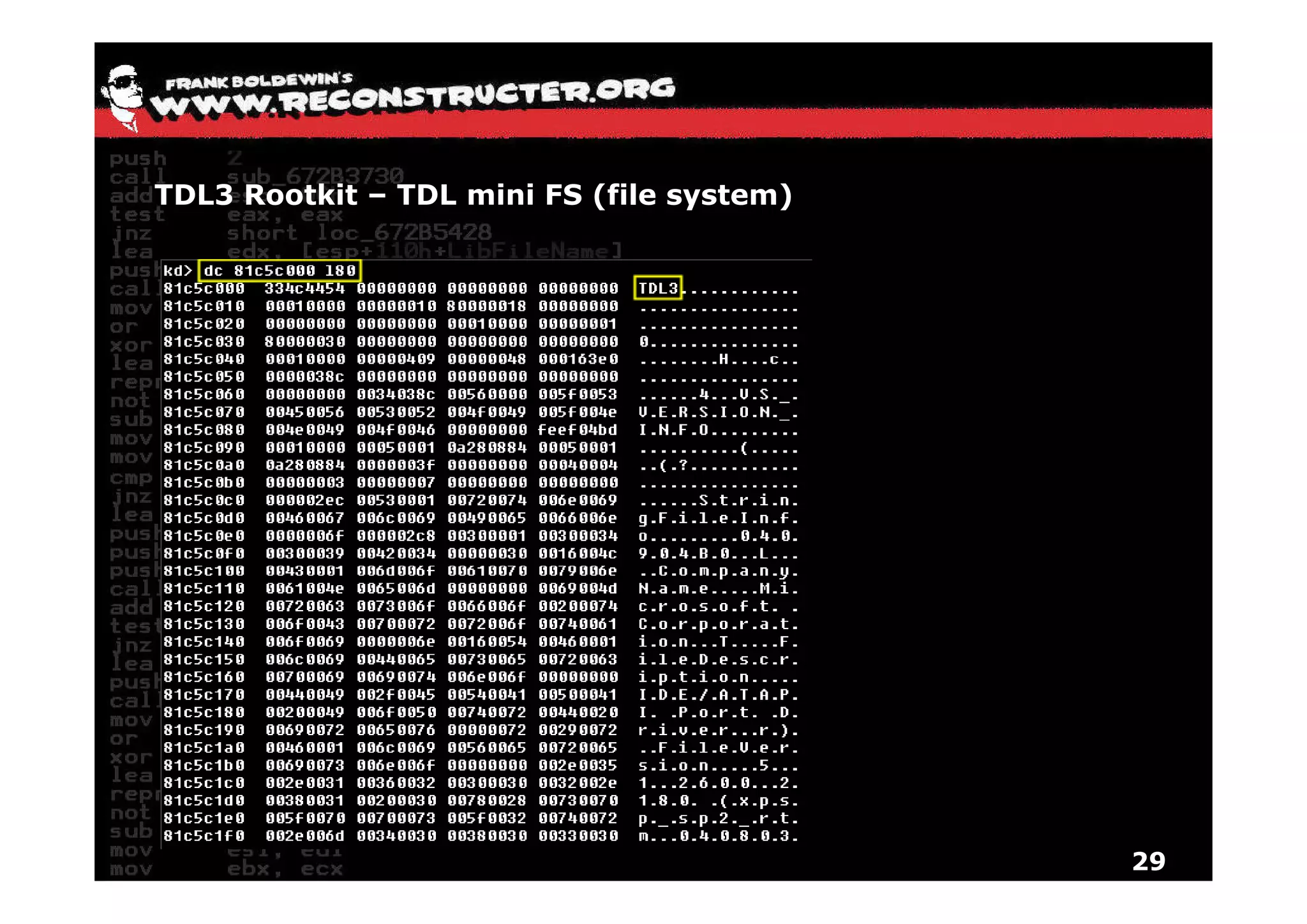
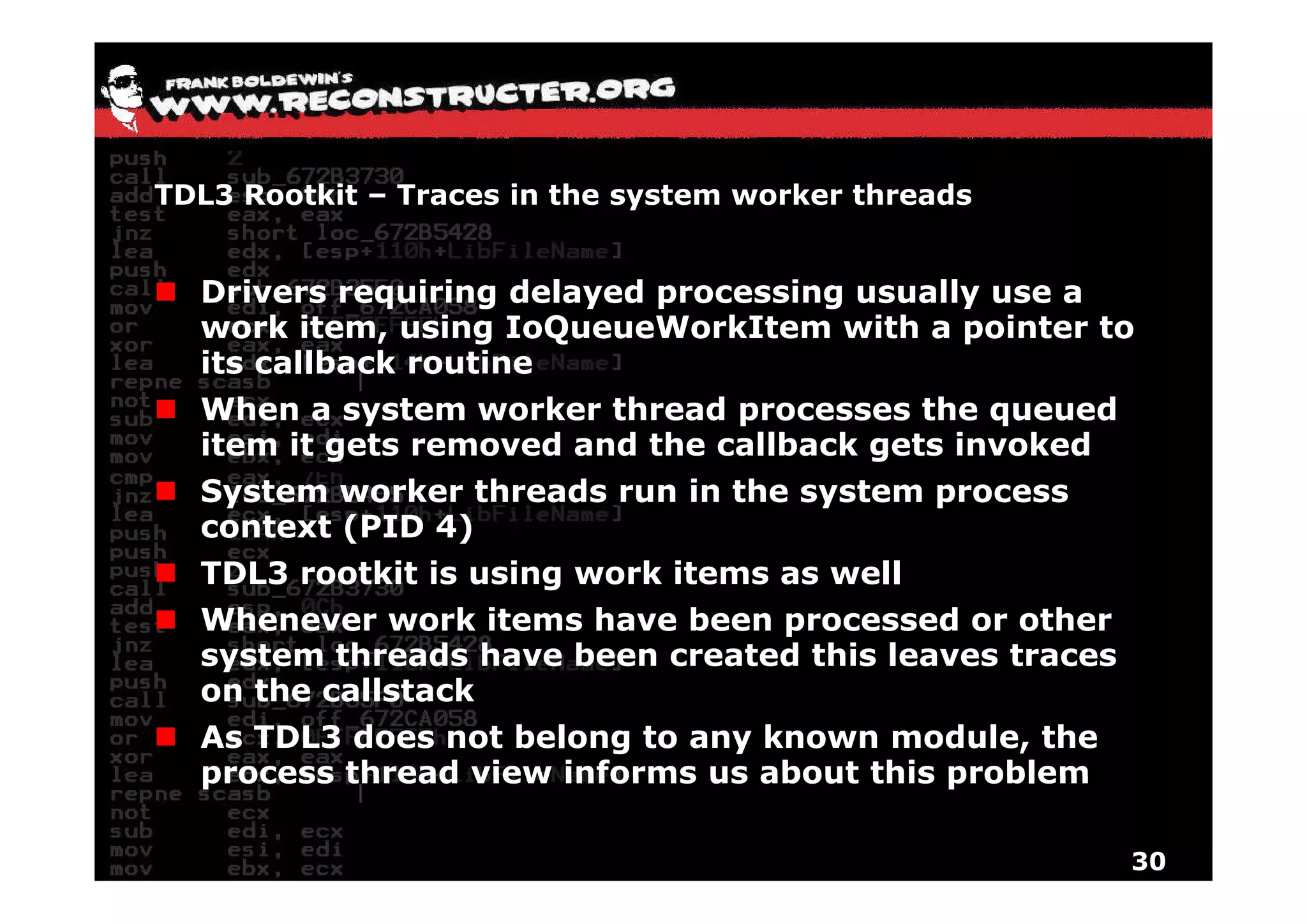
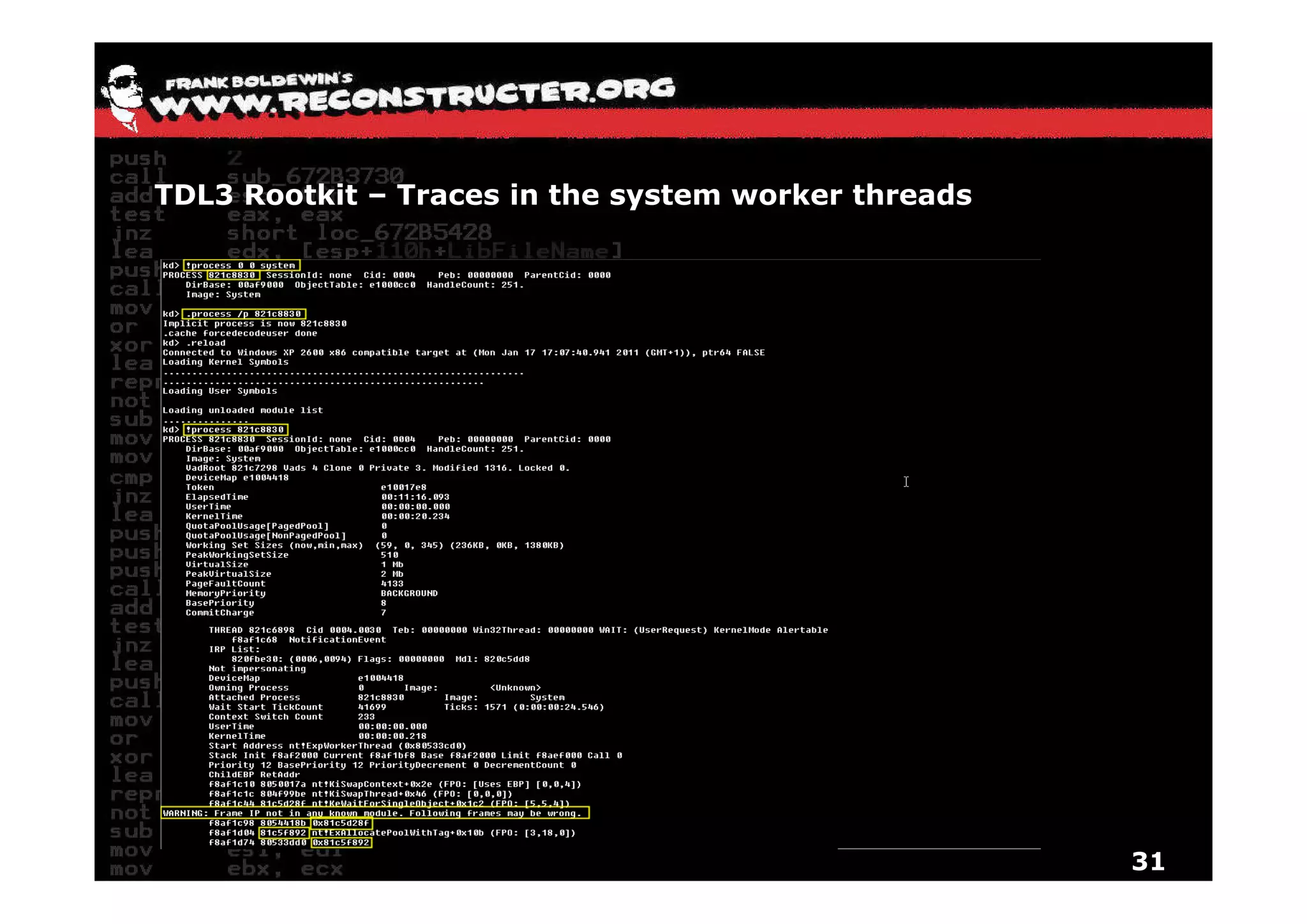
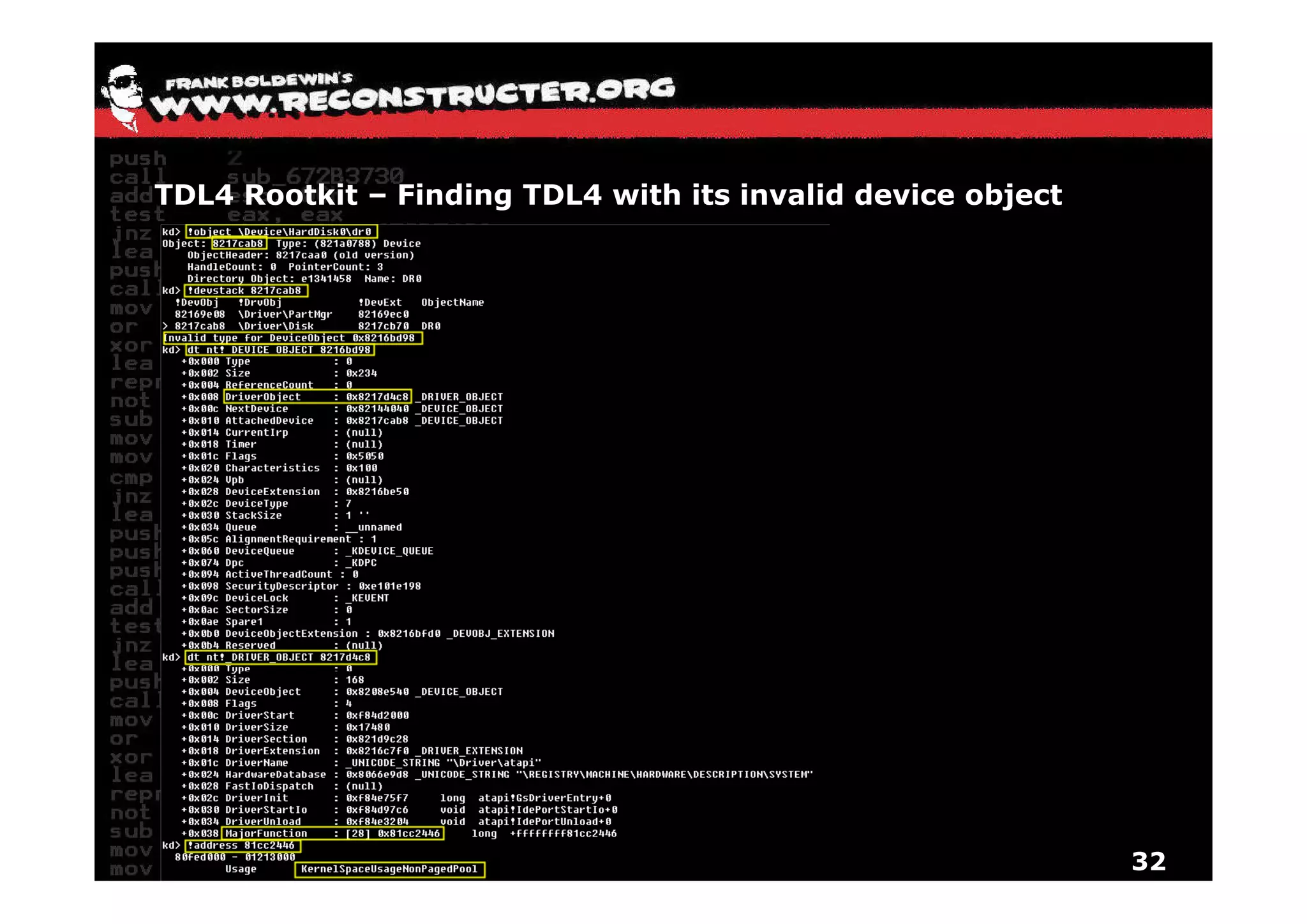
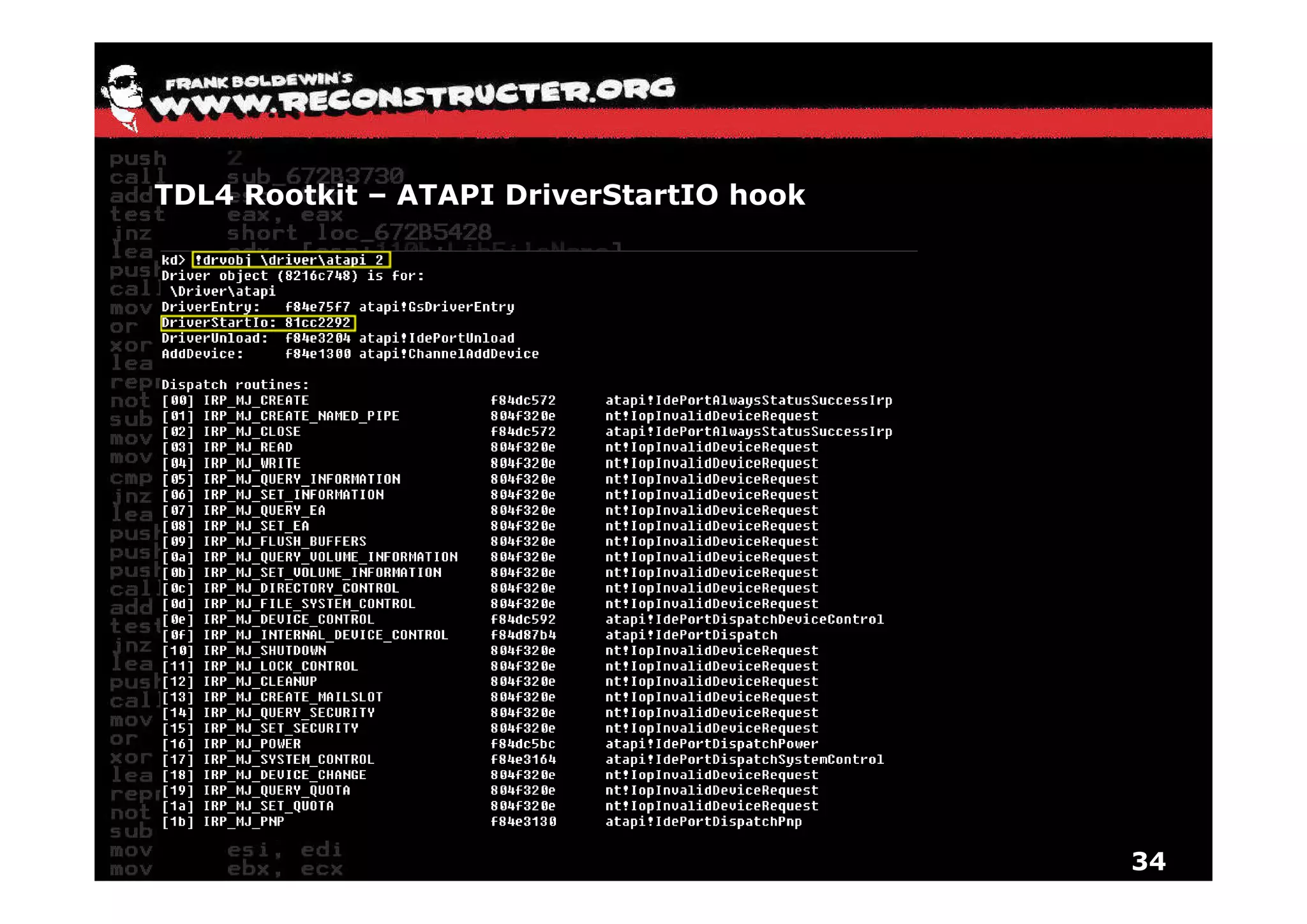
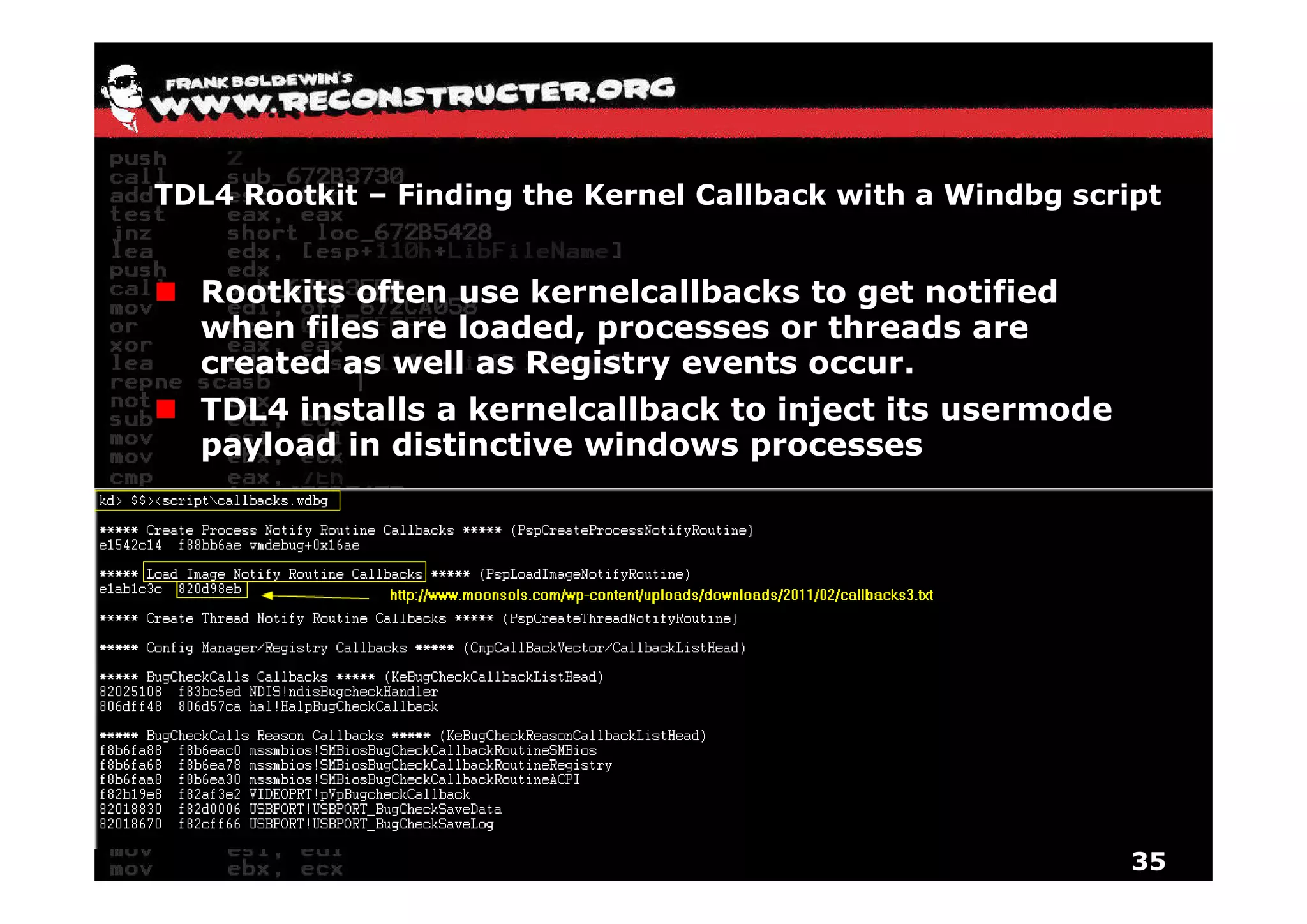
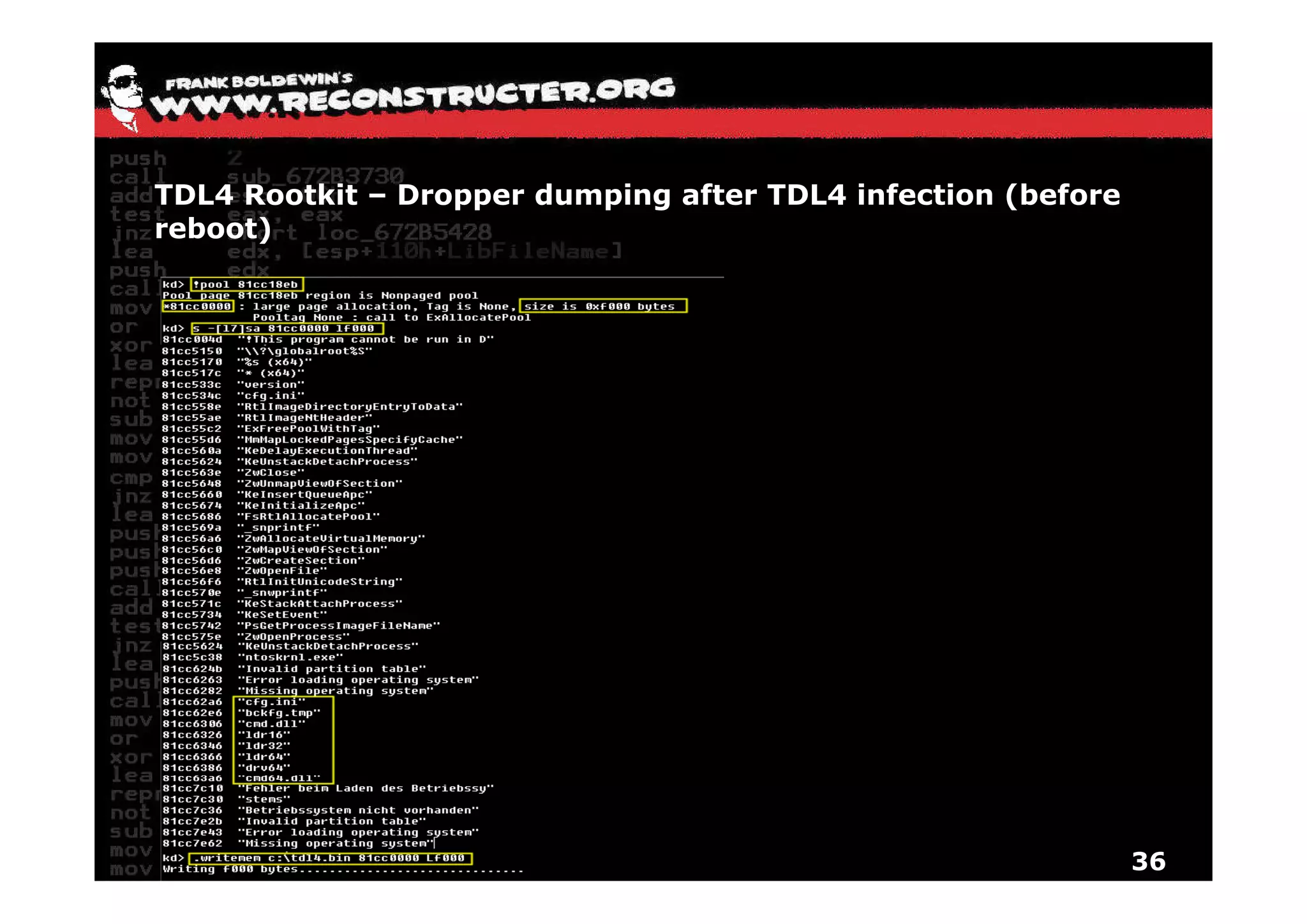
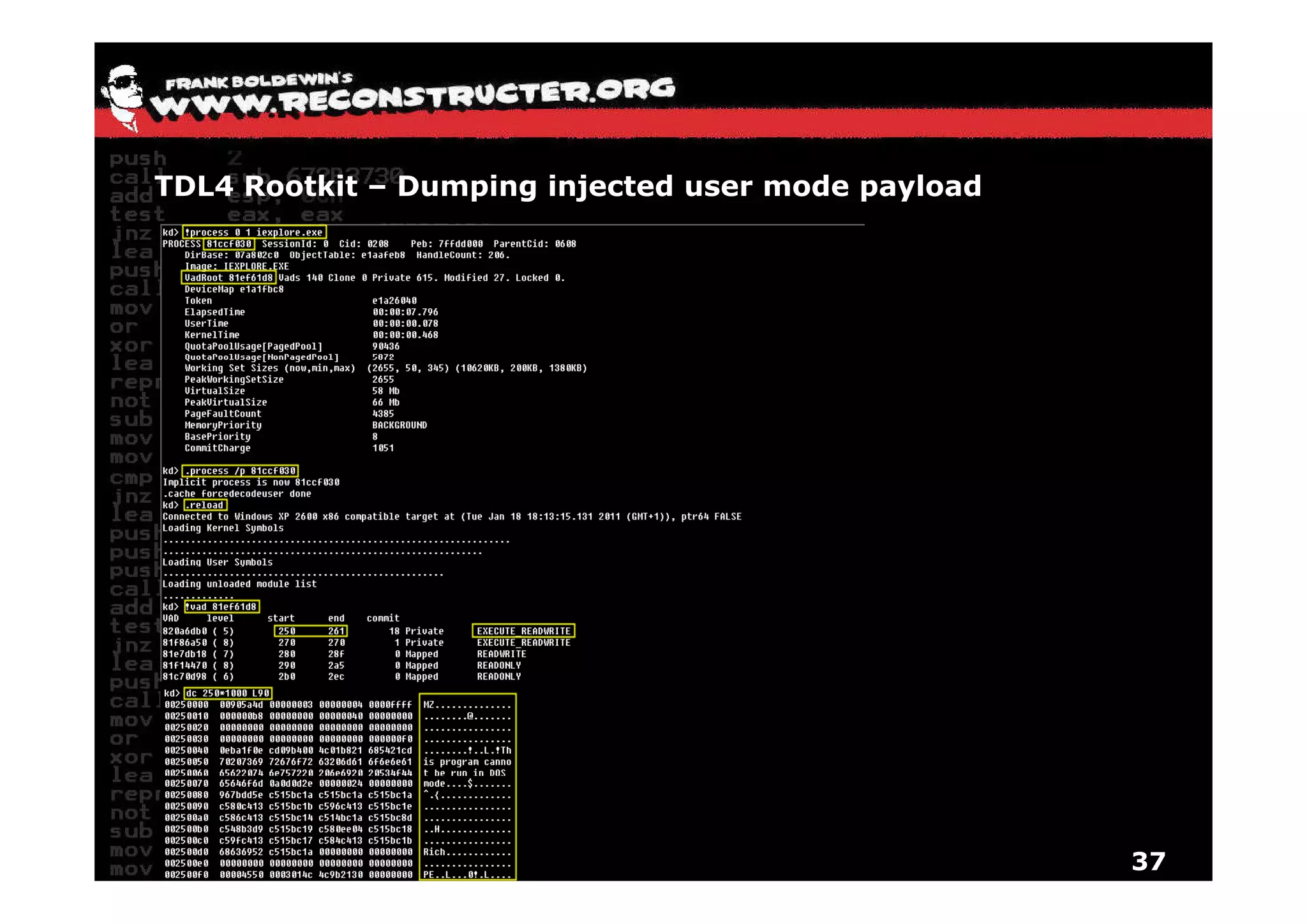
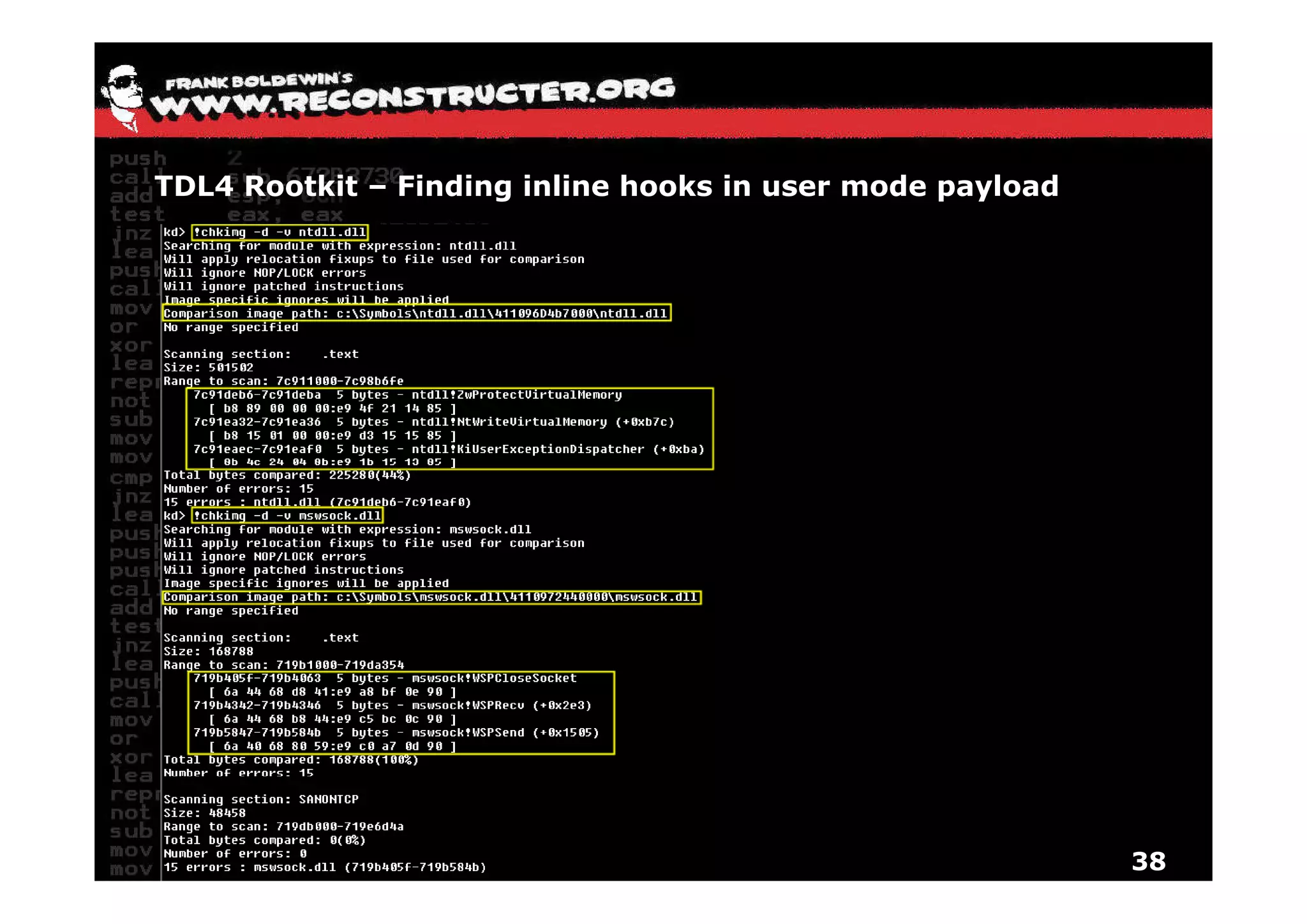
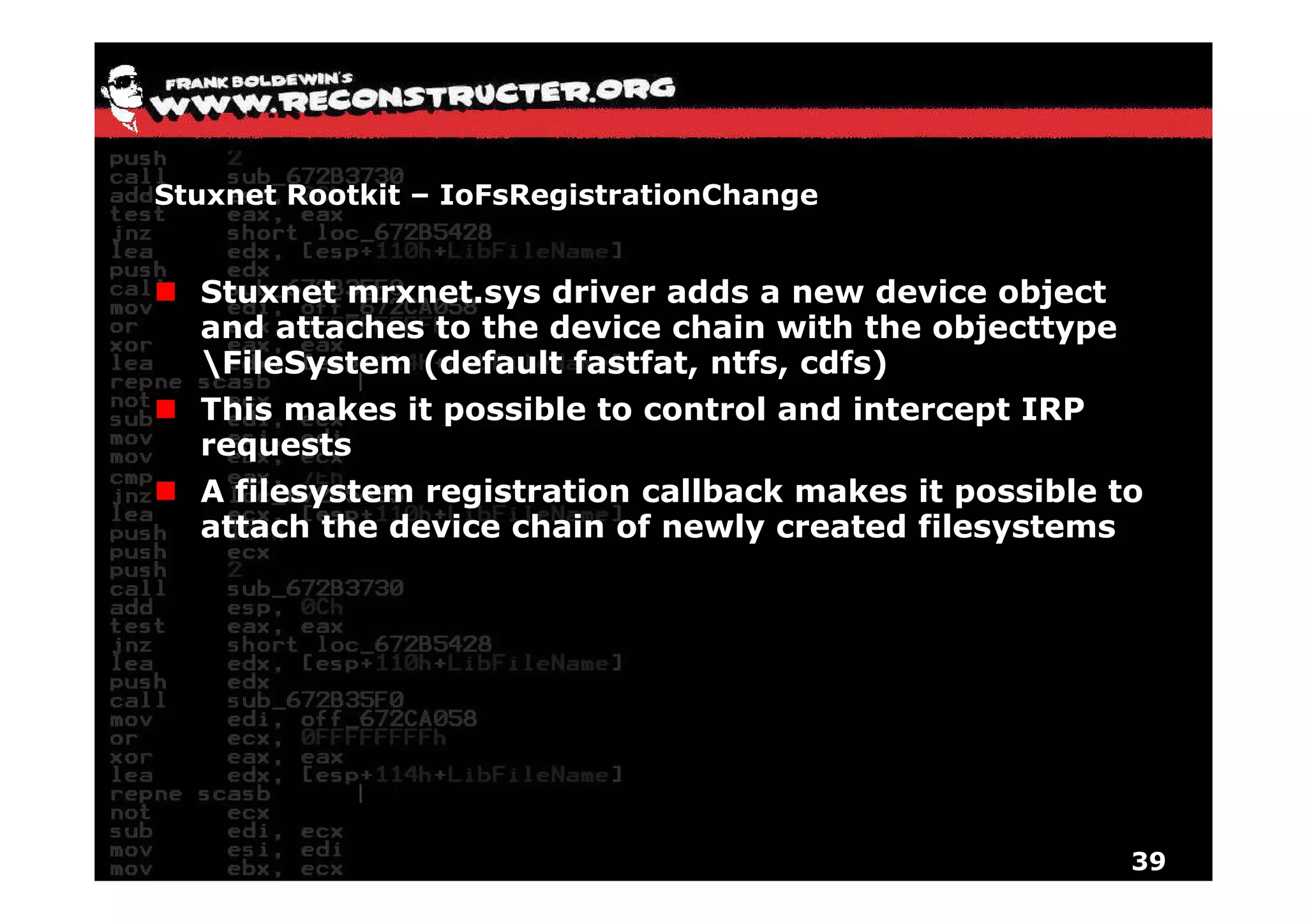
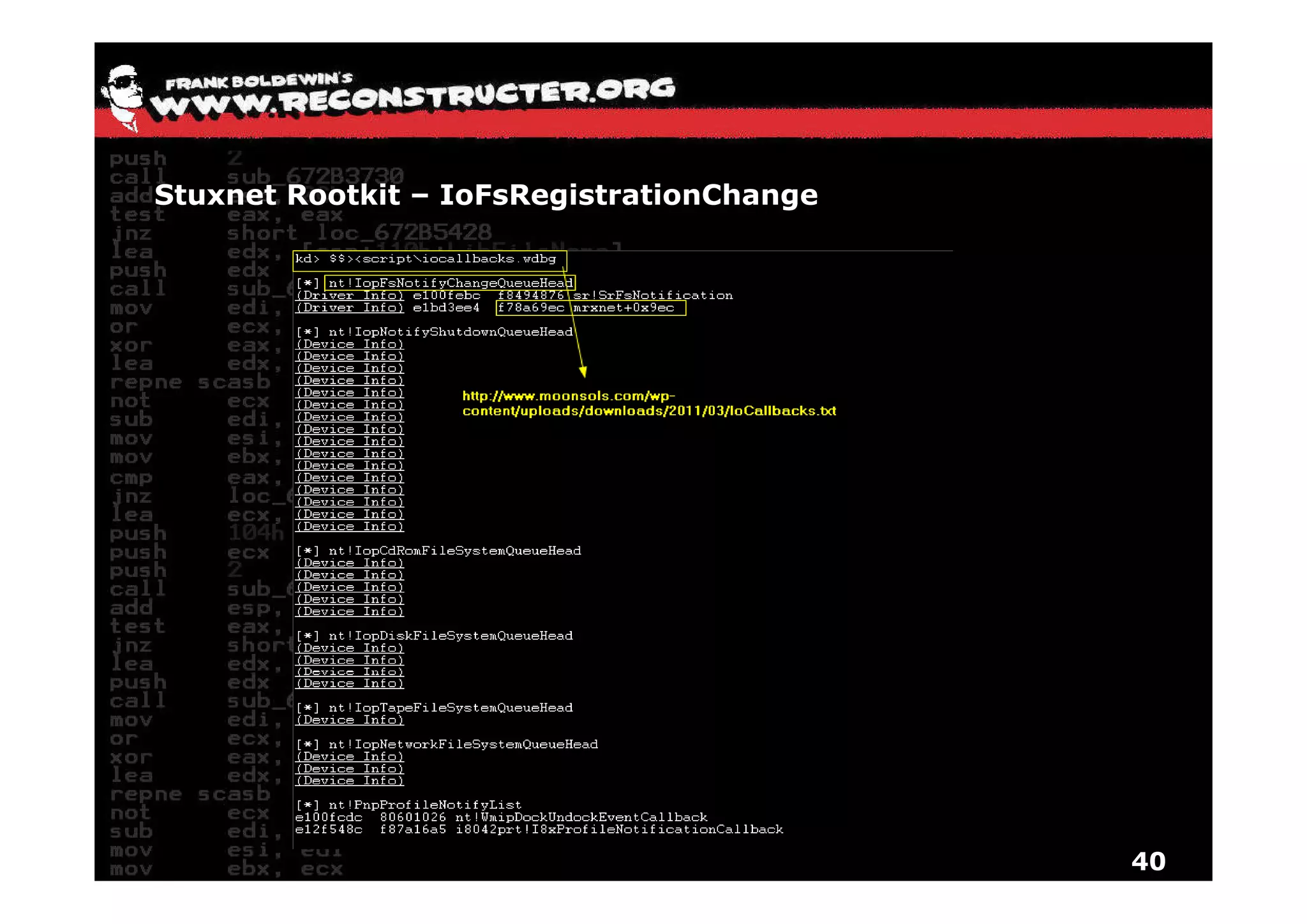
The document provides an overview of techniques for hunting rootkits with Windbg. It discusses how to find SSDT and Shadow SSDT hooks, including examples from the Runtime2, Rustock.B, and Alipop rootkits. It also covers finding hidden registry entries and IDT hooks in Rustock.B, GDT callgates in Alipop, ATAPI IRP hooks in TDL3, shared memory structures between kernel and user mode in TDL3, TDL3's mini file system, traces of TDL3 in system worker threads, how TDL4 hooks the ATAPI driver's DriverStartIO, and how Stuxnet uses IoFsRegistrationChange. The document is intended to