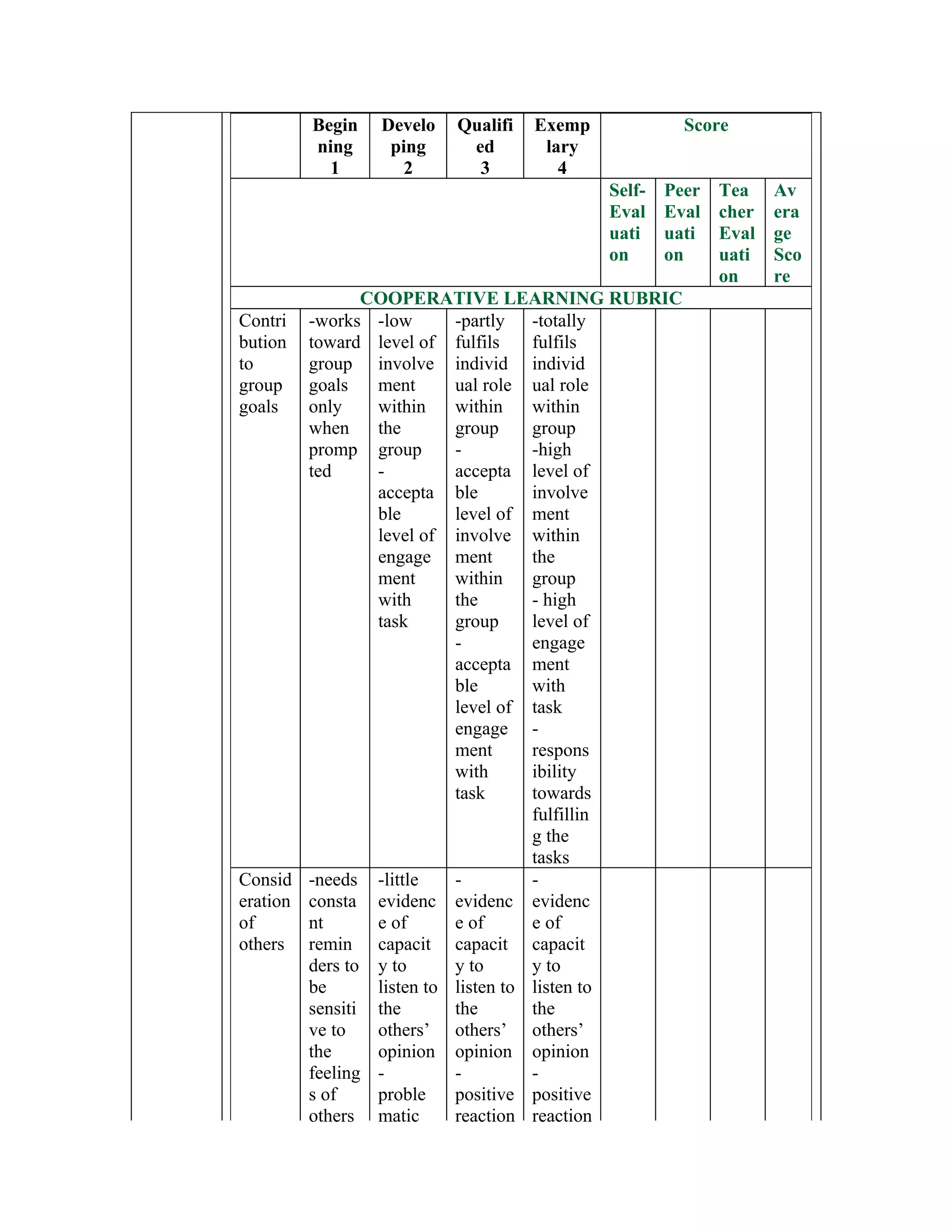
This document provides a 9-step process for students to research cyberbullying and social media safety. The steps include:
1. Forming groups and assigning roles to research assigned questions.
2. Researching what information they post online and how it could affect them.
3. Reading safety tips from various resources on maintaining privacy online.
4. Evaluating their own social media profiles based on the new safety information.
5. Creating a priority plan to update their profiles.
6. Recording spoken updates using Voki to share.
7. Playing an online safety game to test their knowledge.
8. Analyzing a video about cyberbullying risks.