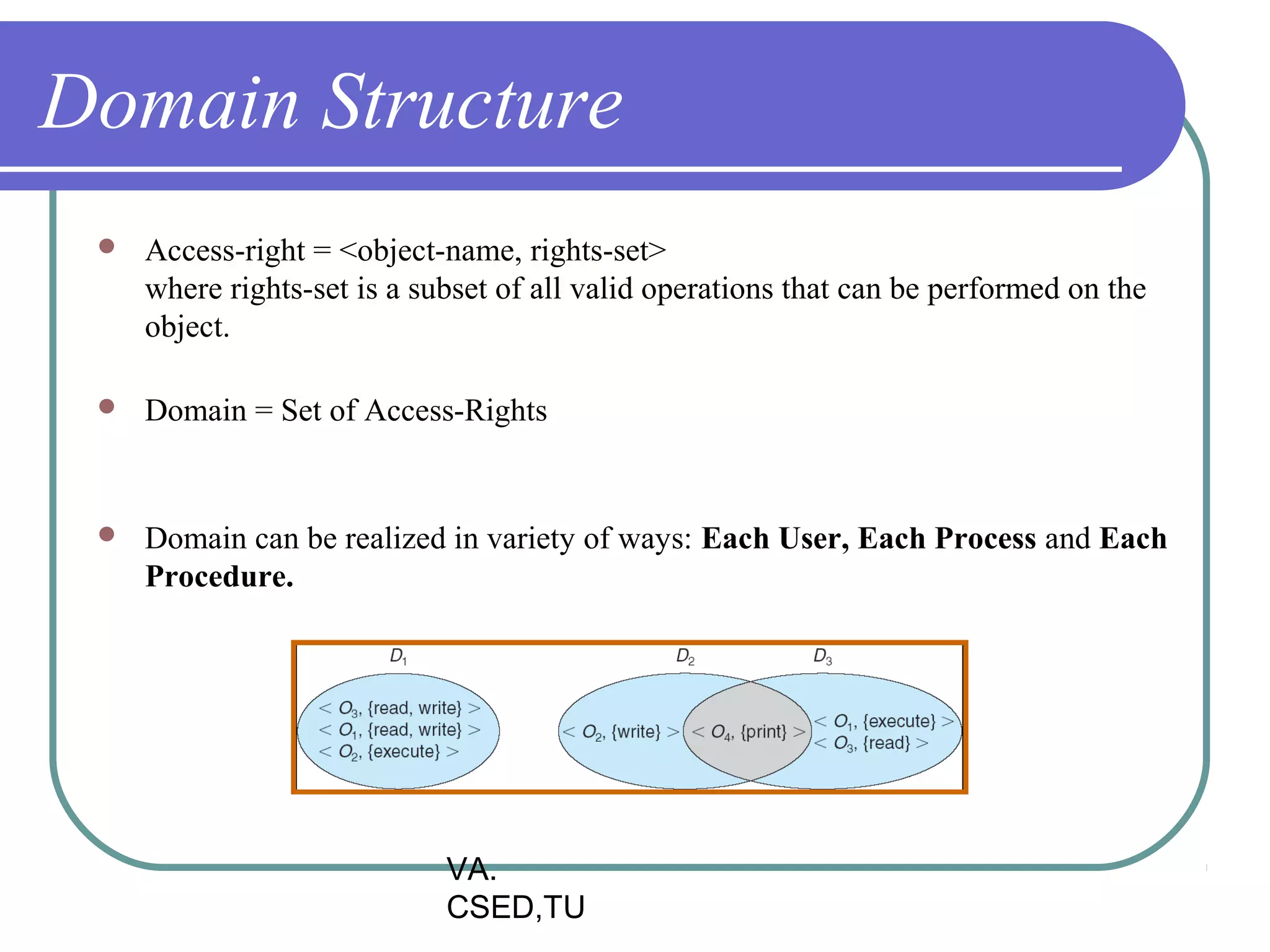
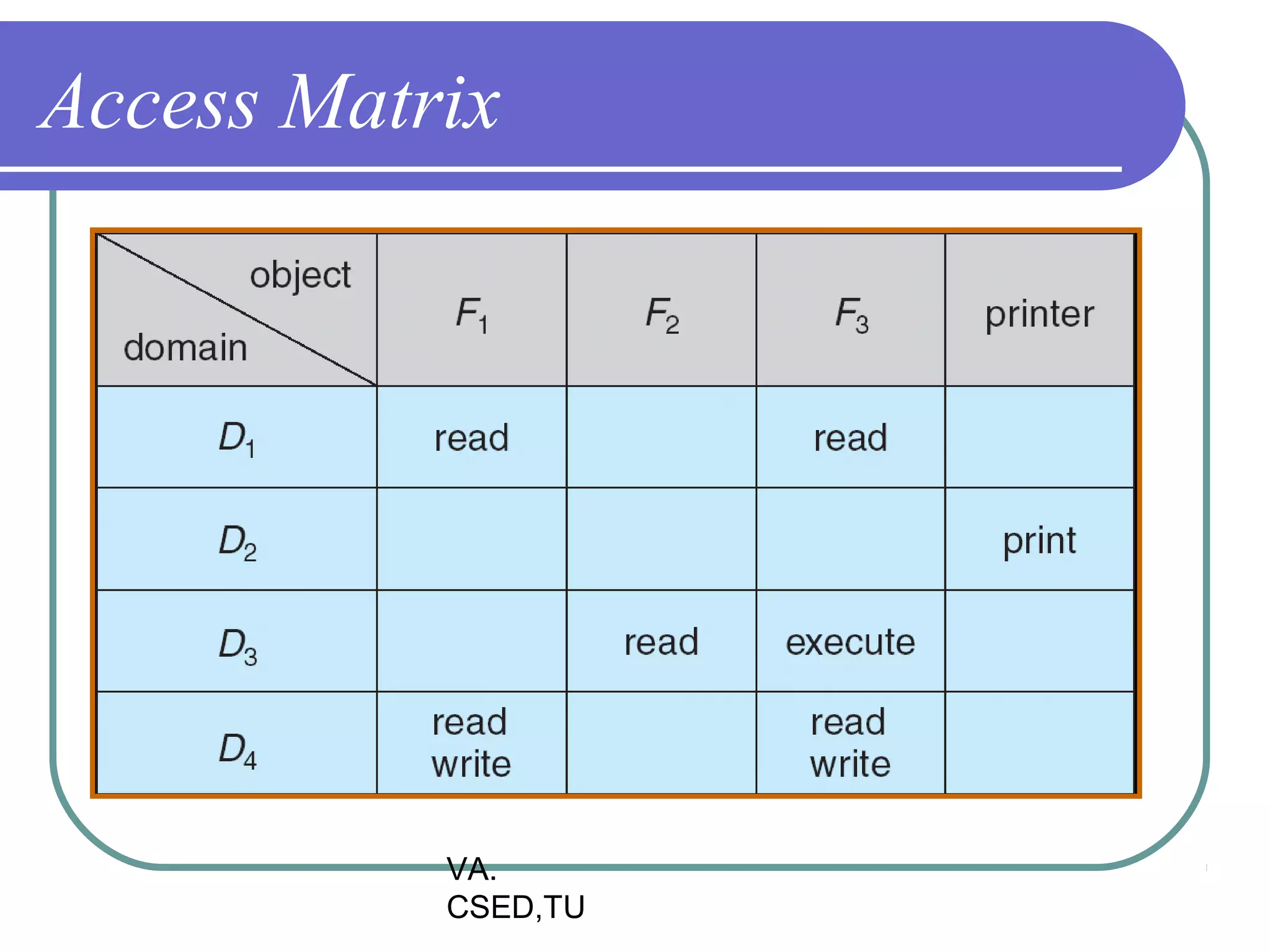
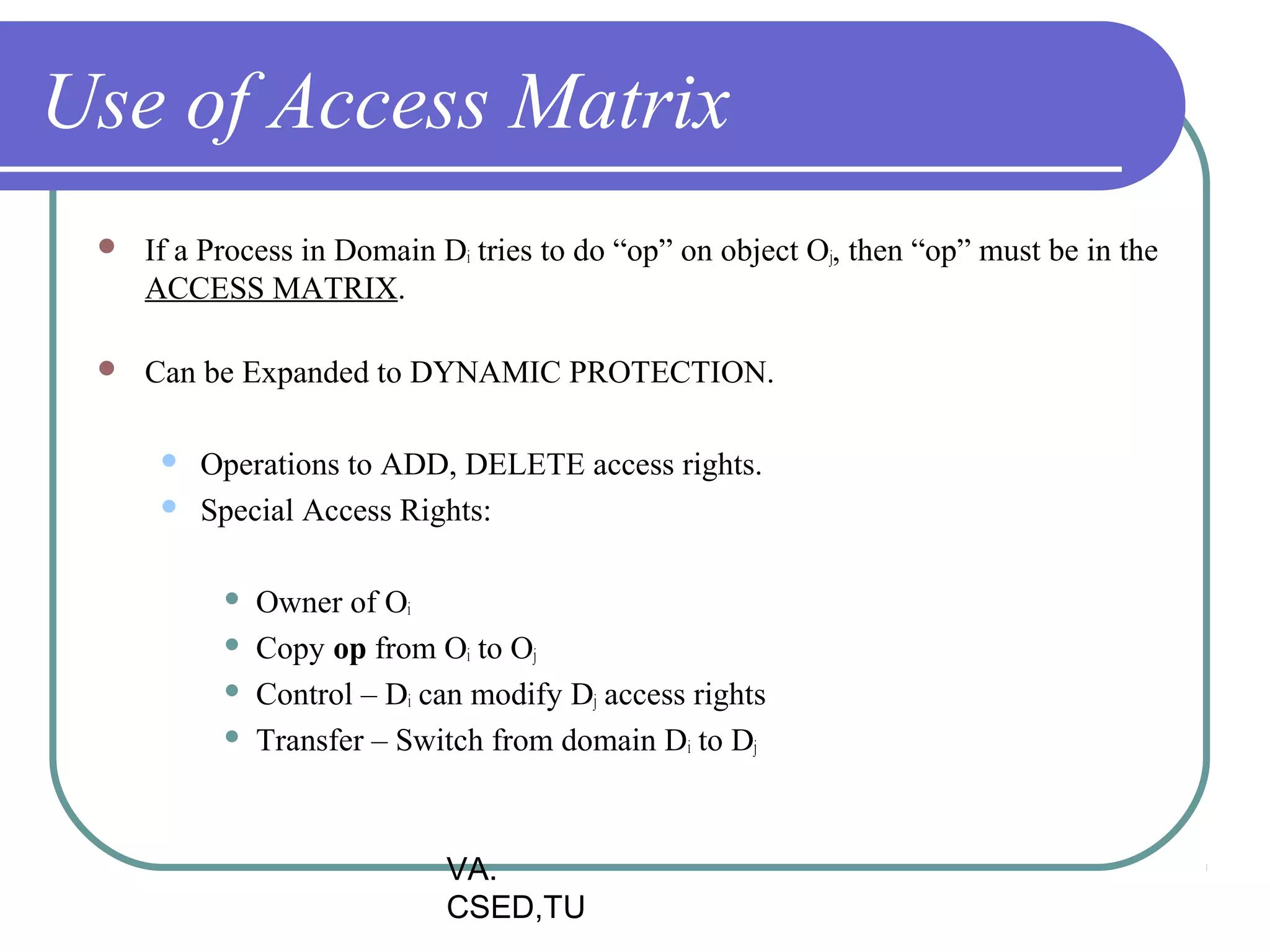
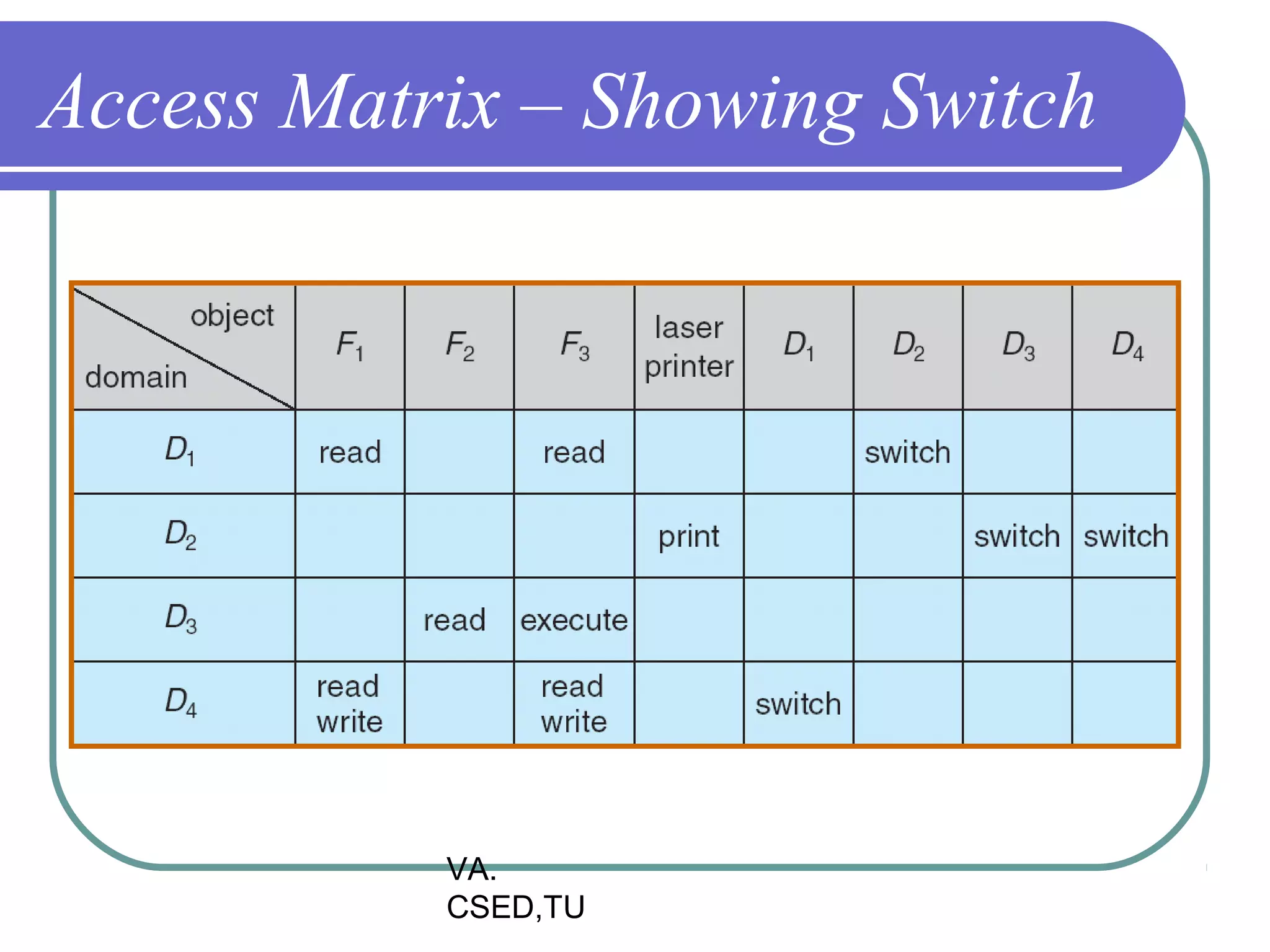
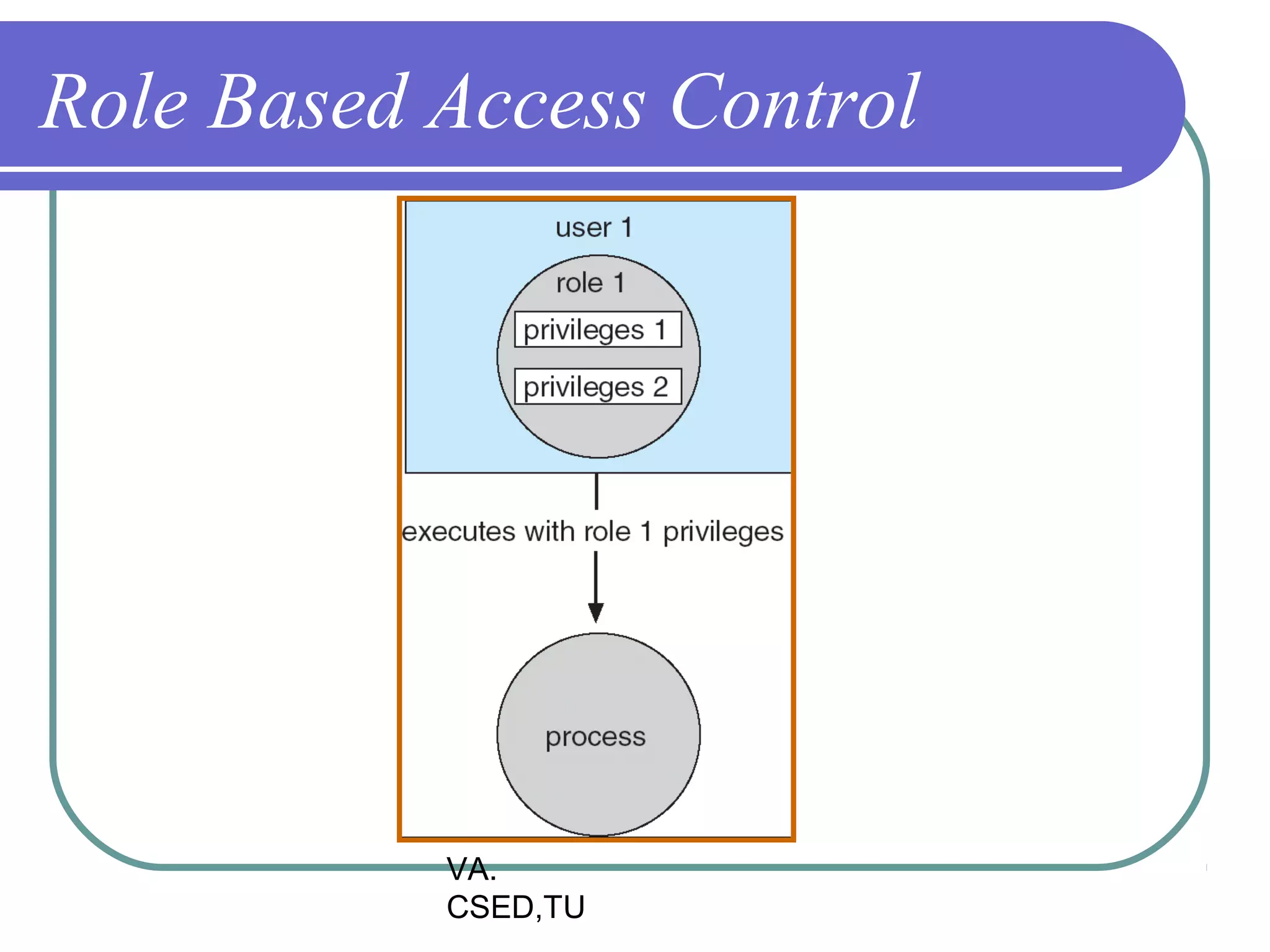
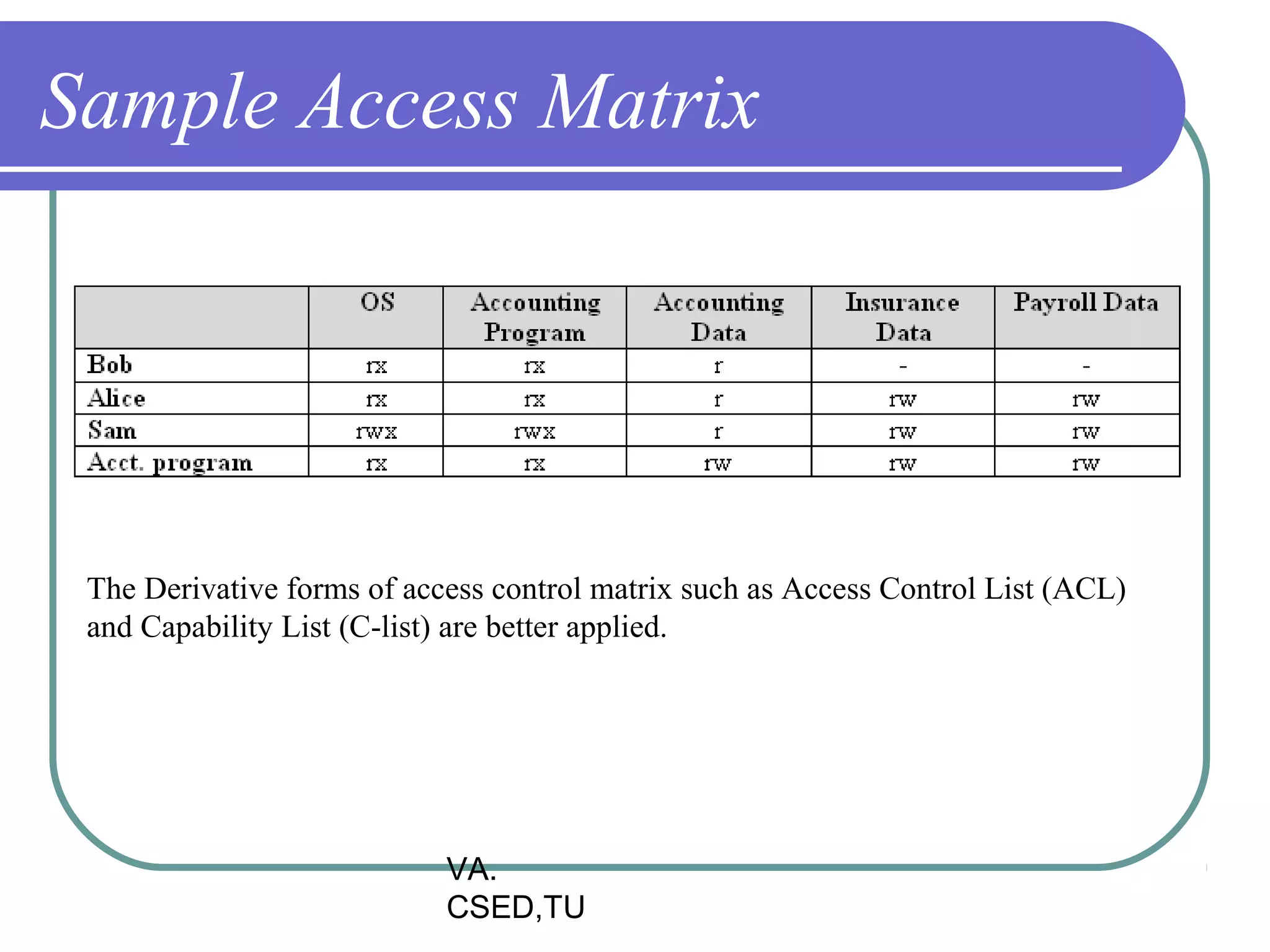
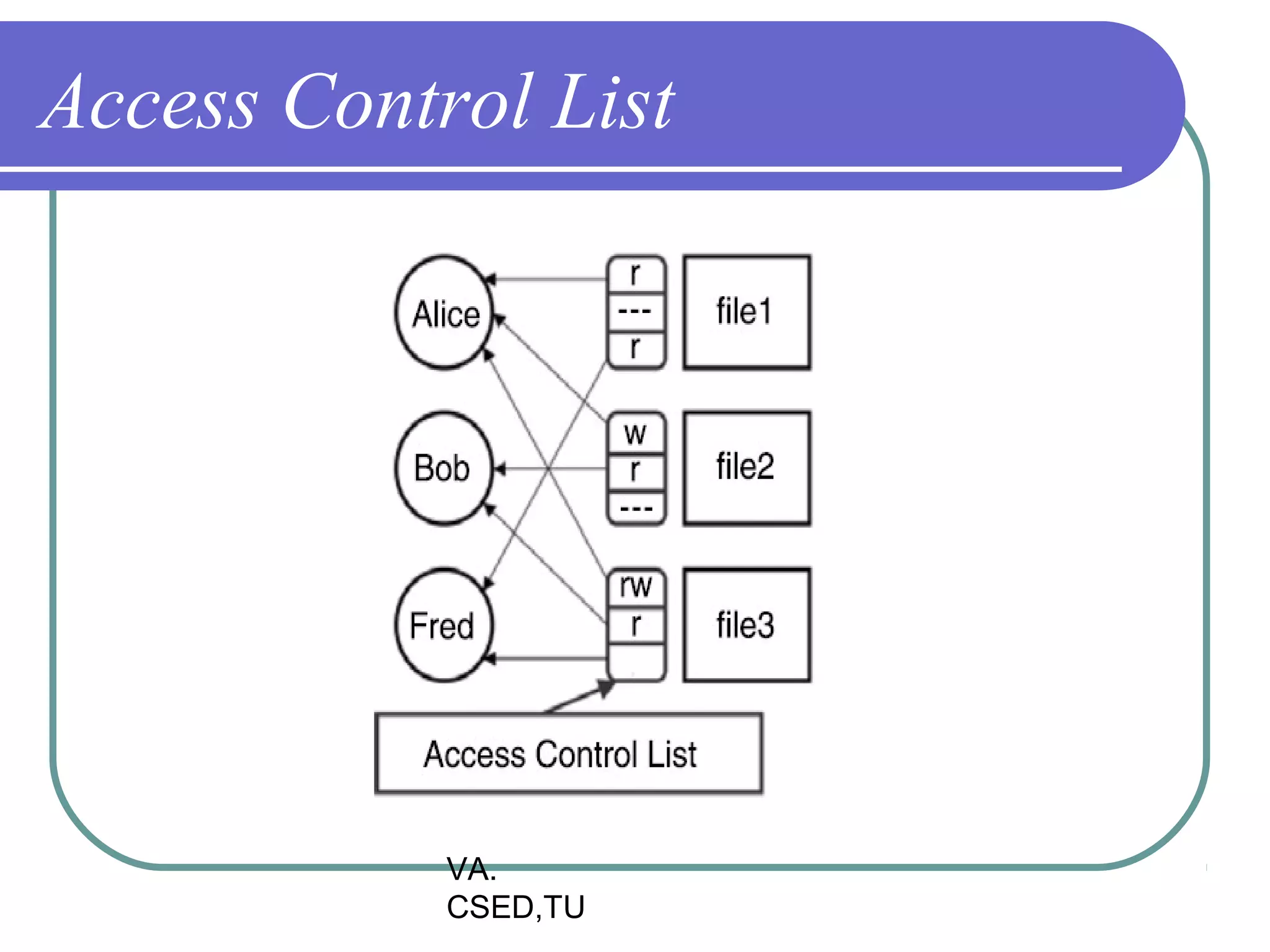
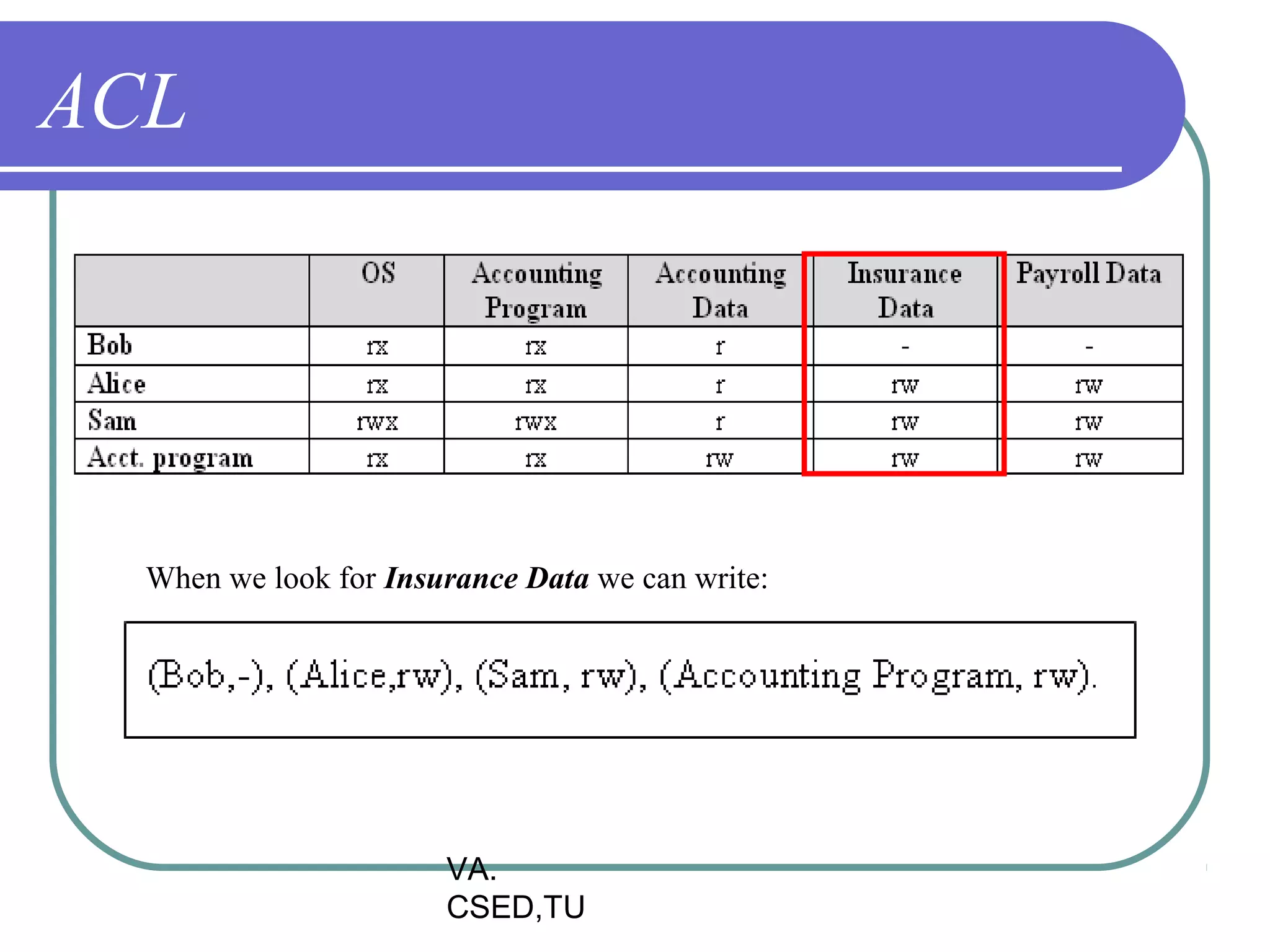
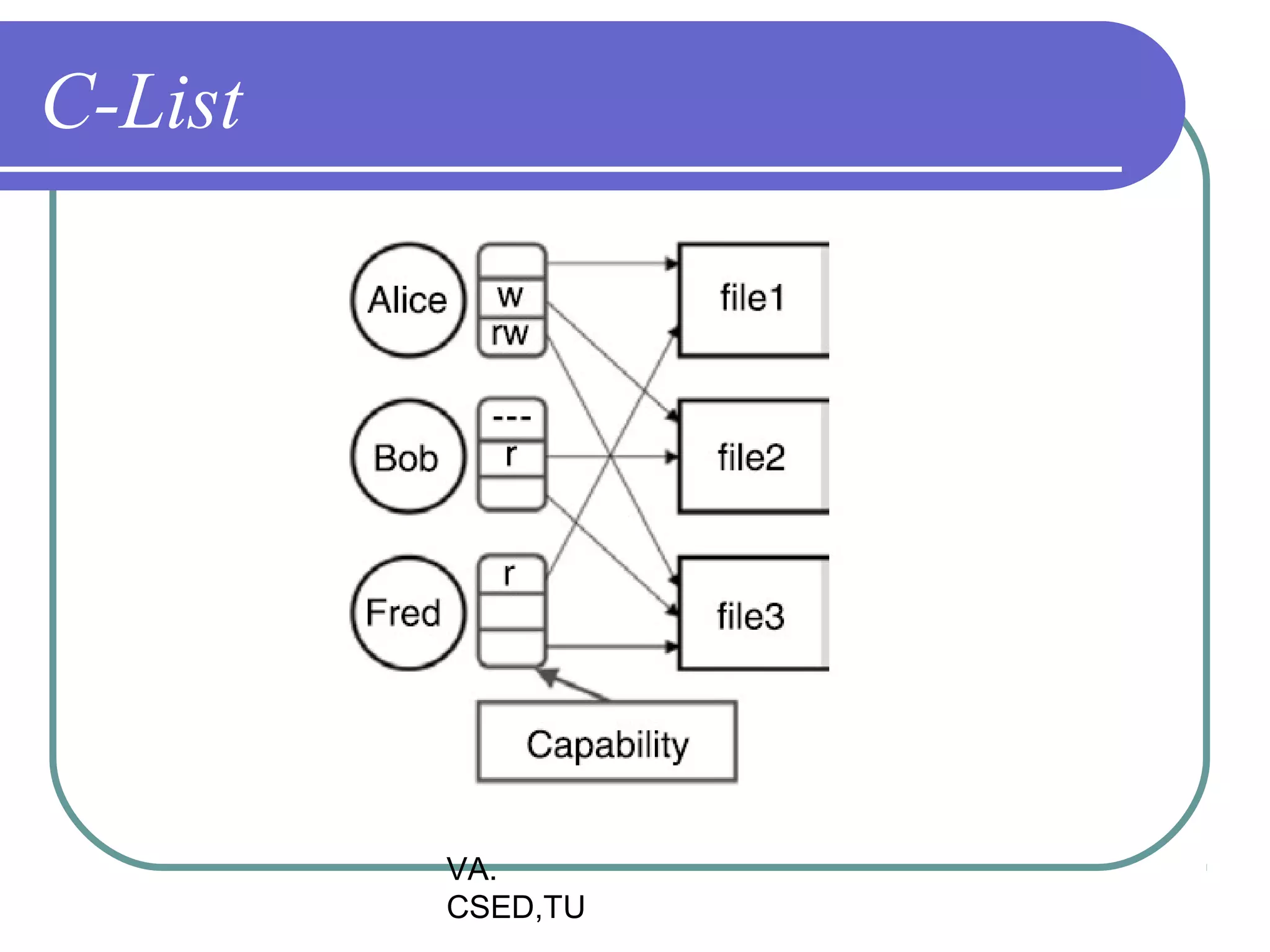
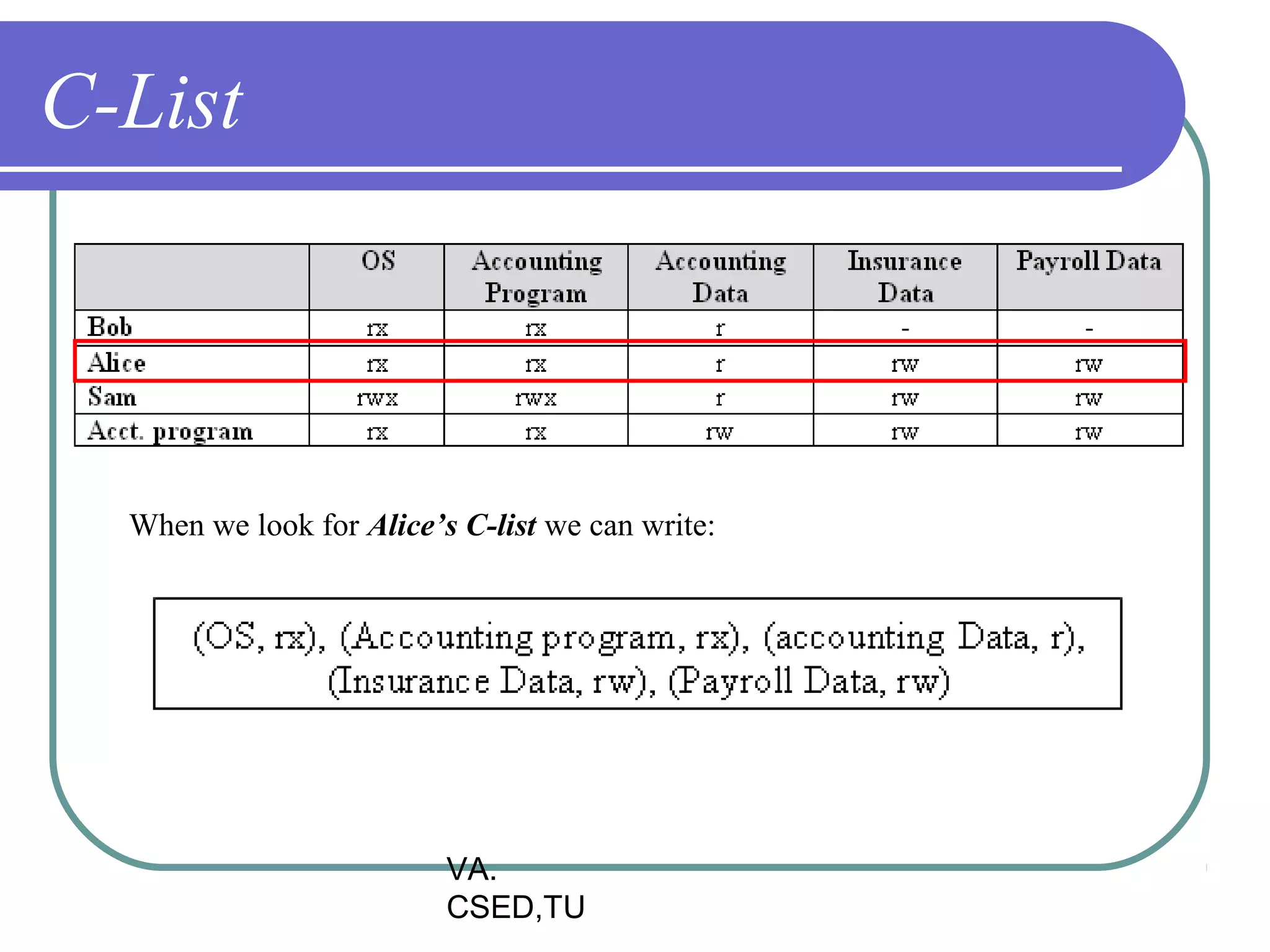
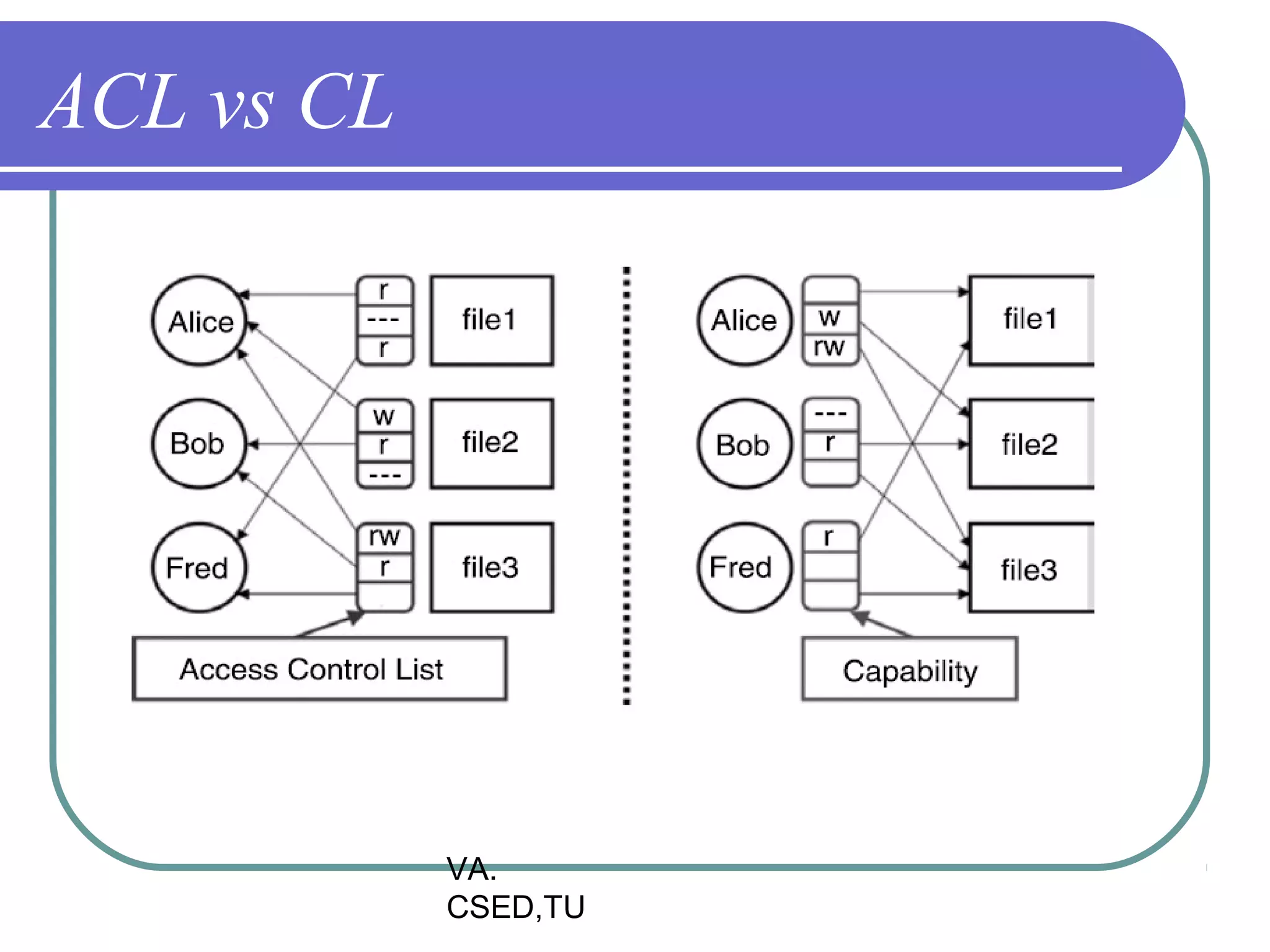
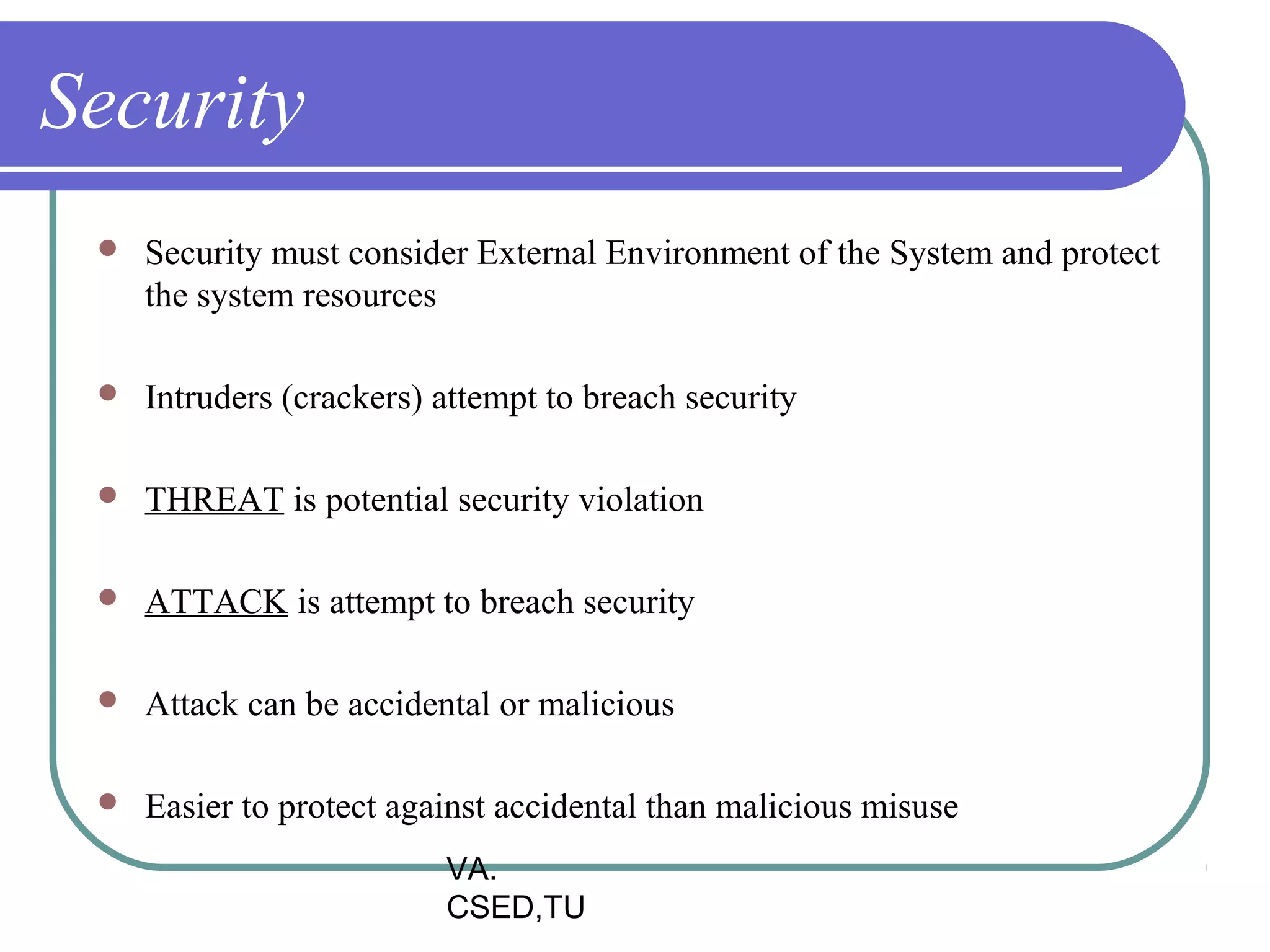
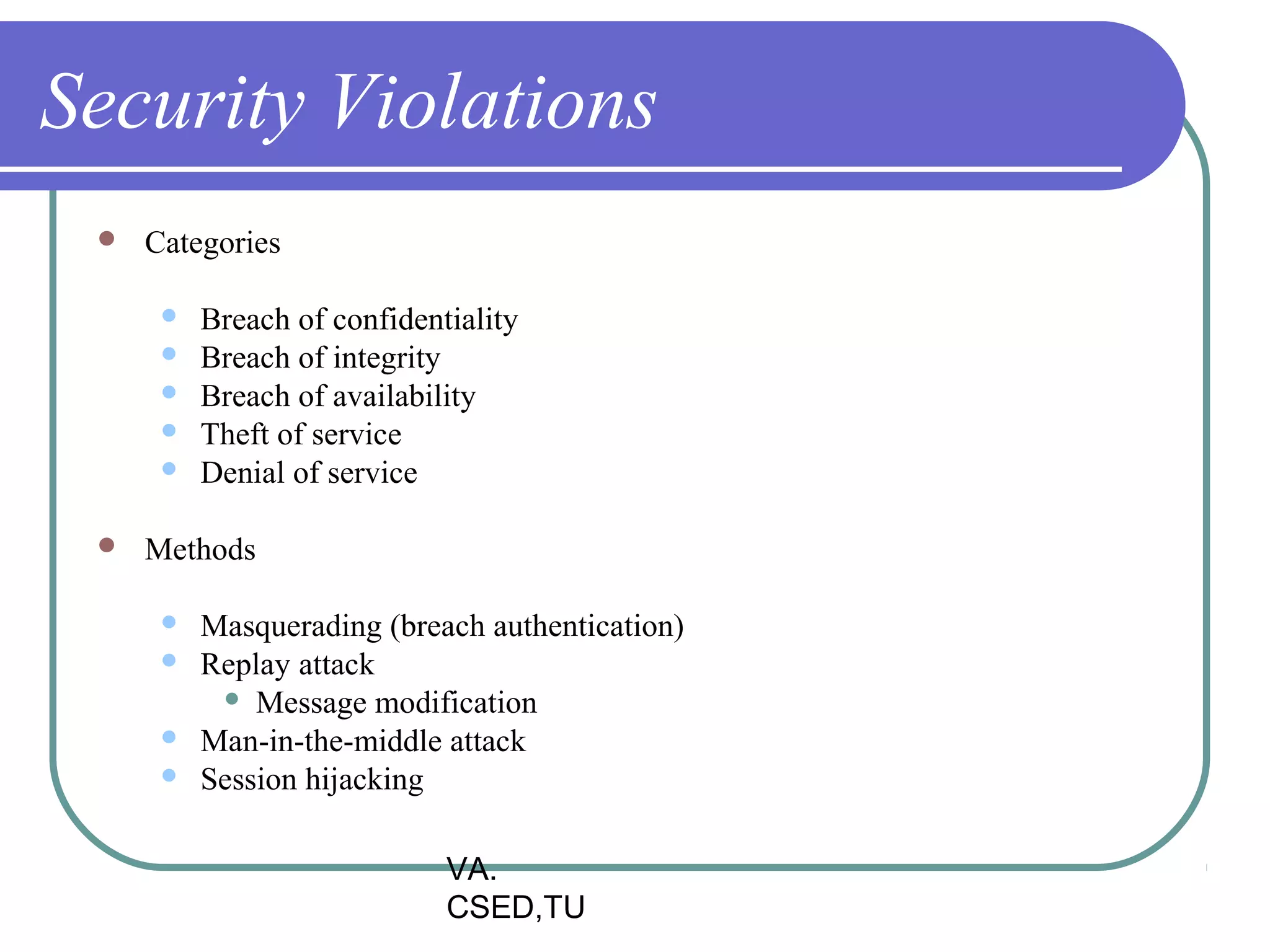
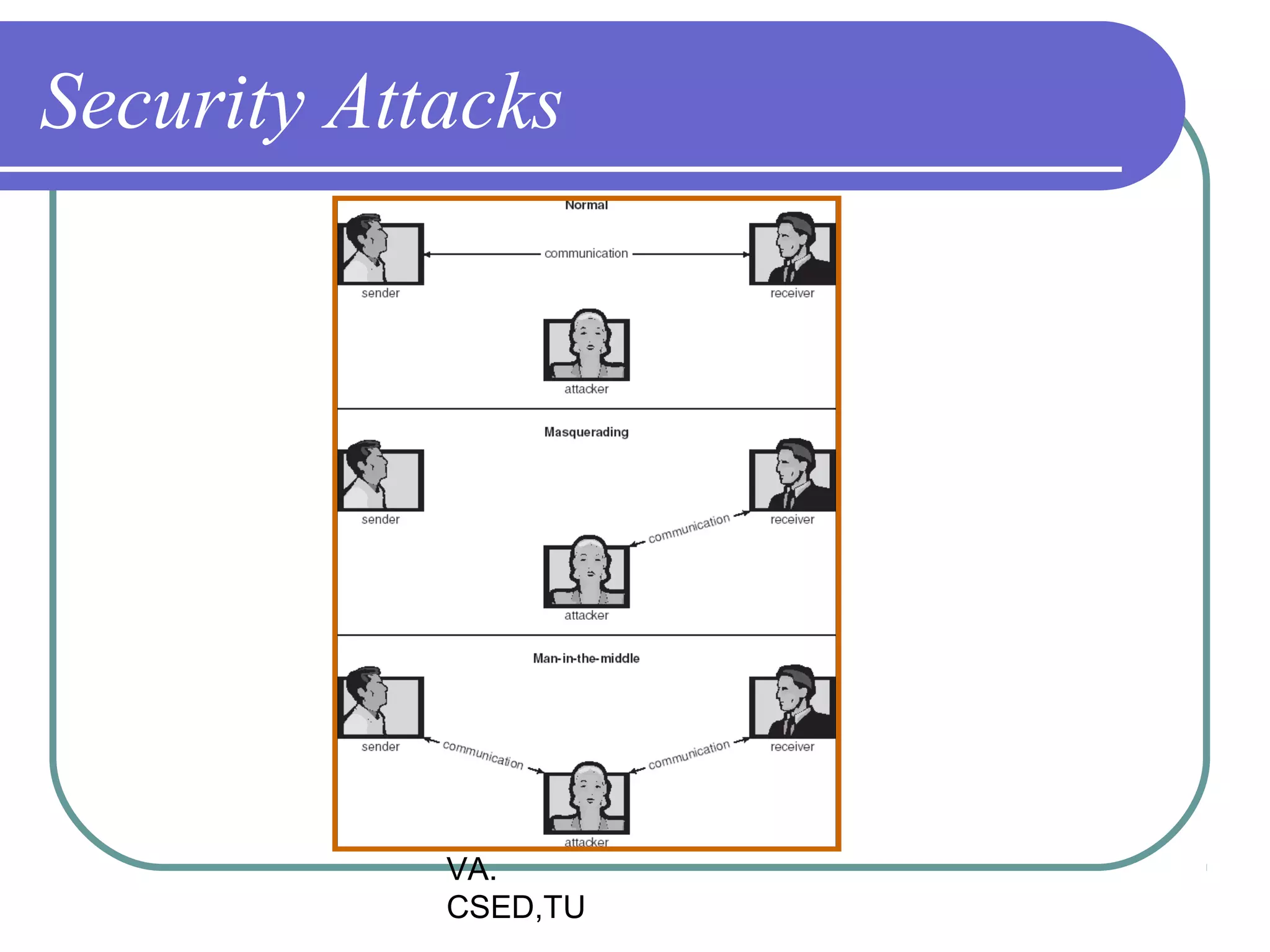
This document discusses protection and security in operating systems. It covers goals of protection like ensuring each object can only be accessed correctly by allowed processes. The principle of least privilege is introduced. Domain structure and access matrix models for protection are described. Access control matrix consists of subjects, objects, and access operations. Access control list and capability list are derivative and better forms. Security threats like intruders attempting to breach security are addressed. Categories of security violations like breach of confidentiality and methods of attacks are outlined. References from textbooks and websites on related topics are listed at the end.