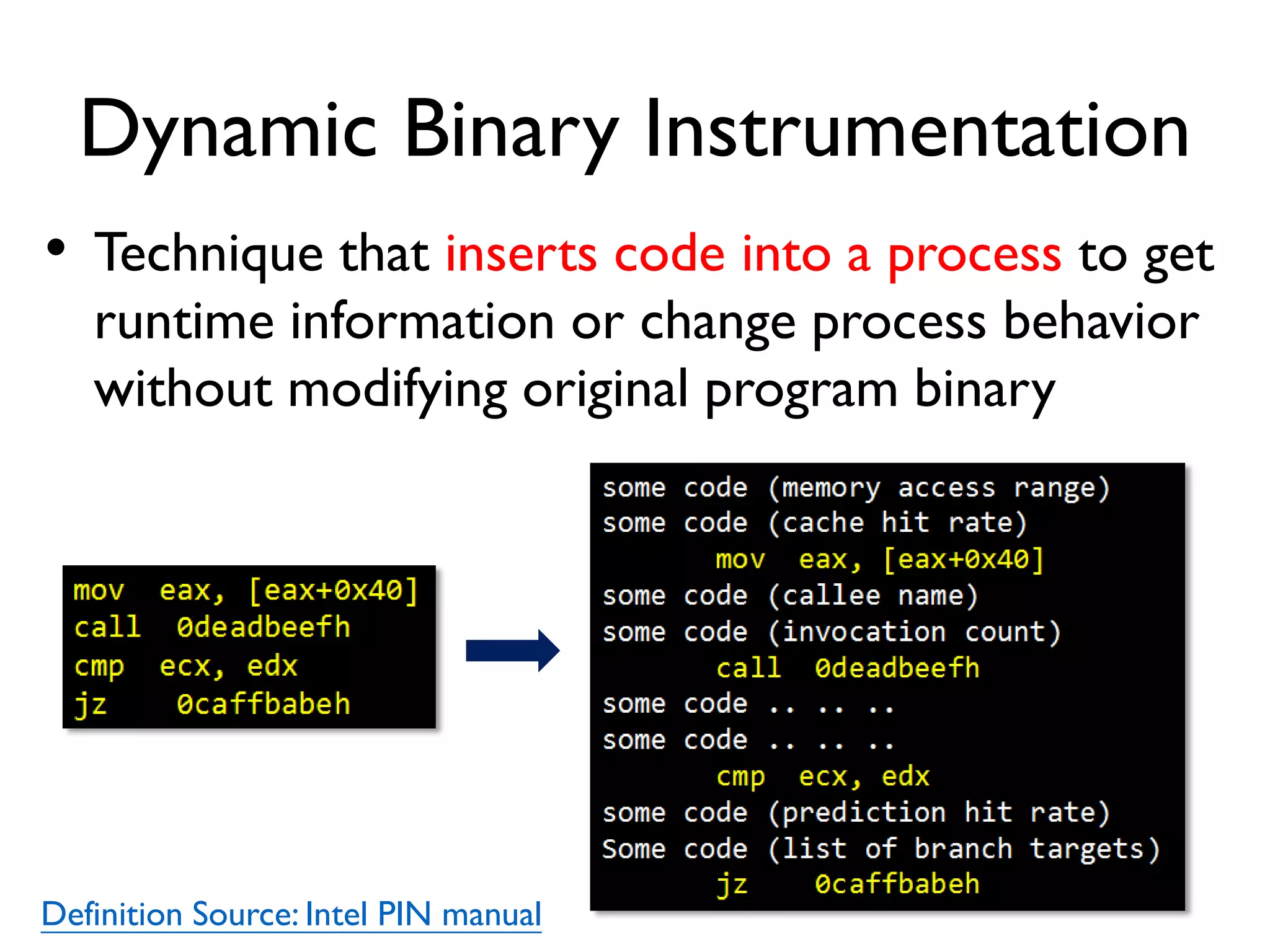
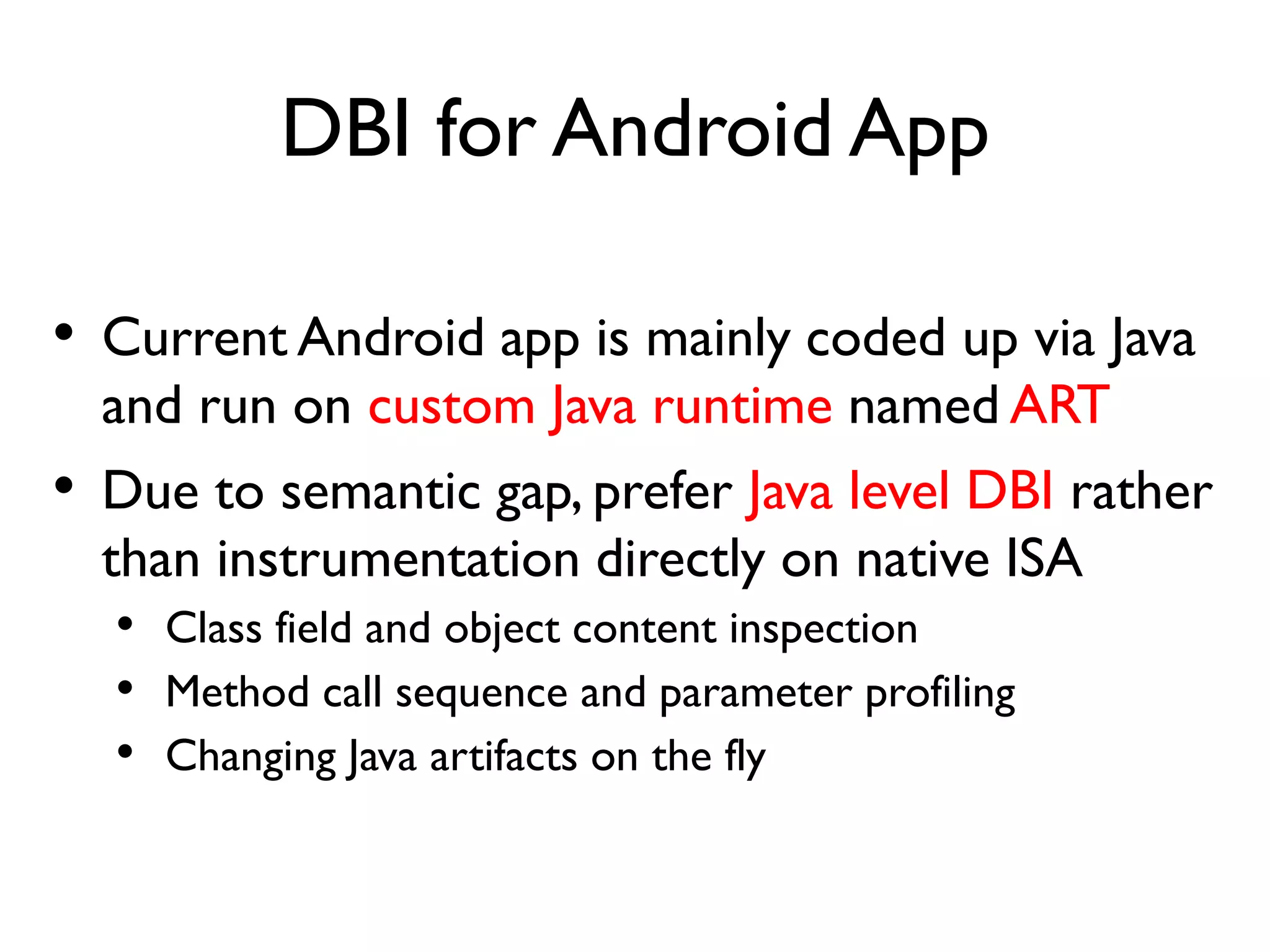
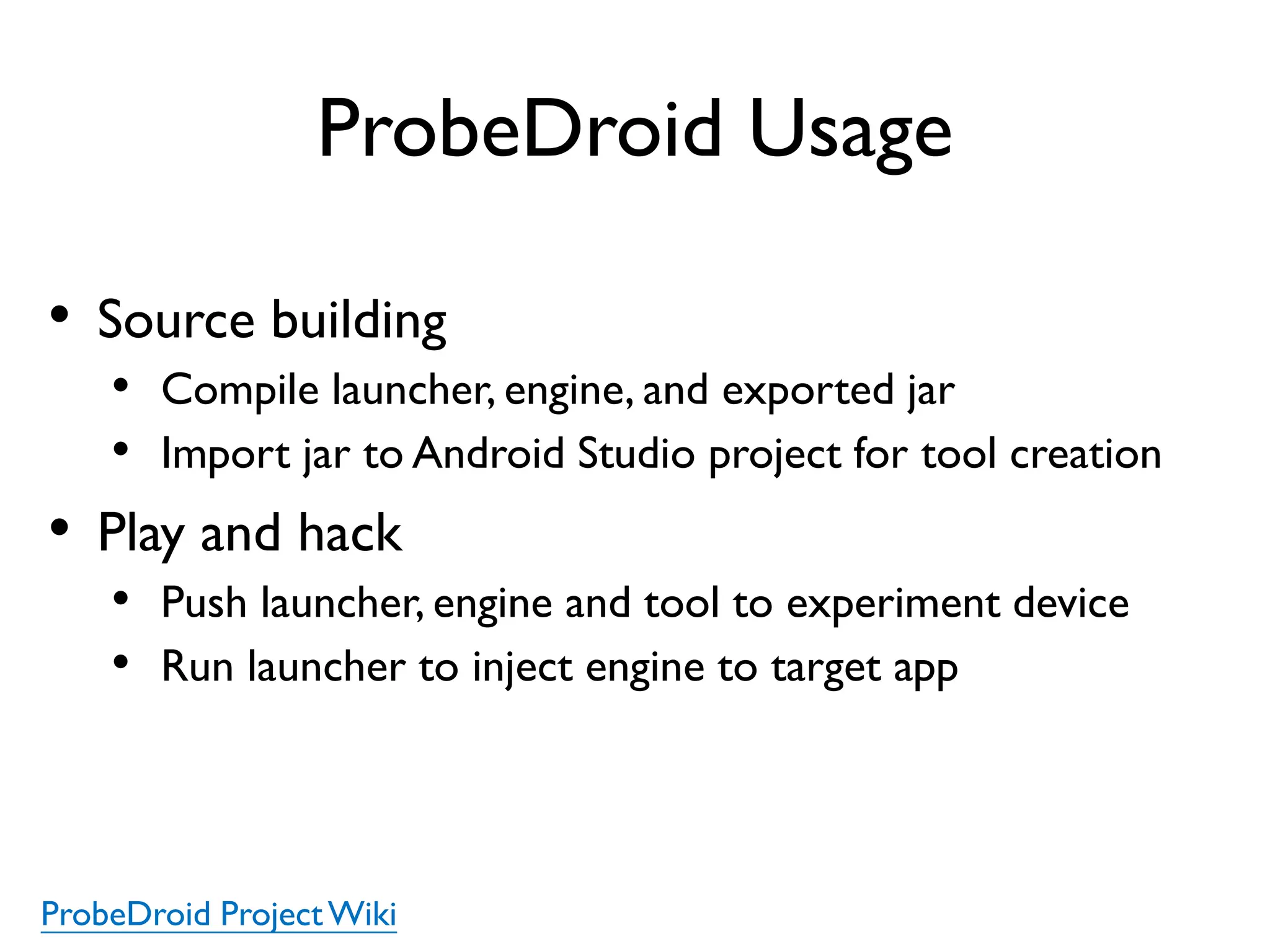
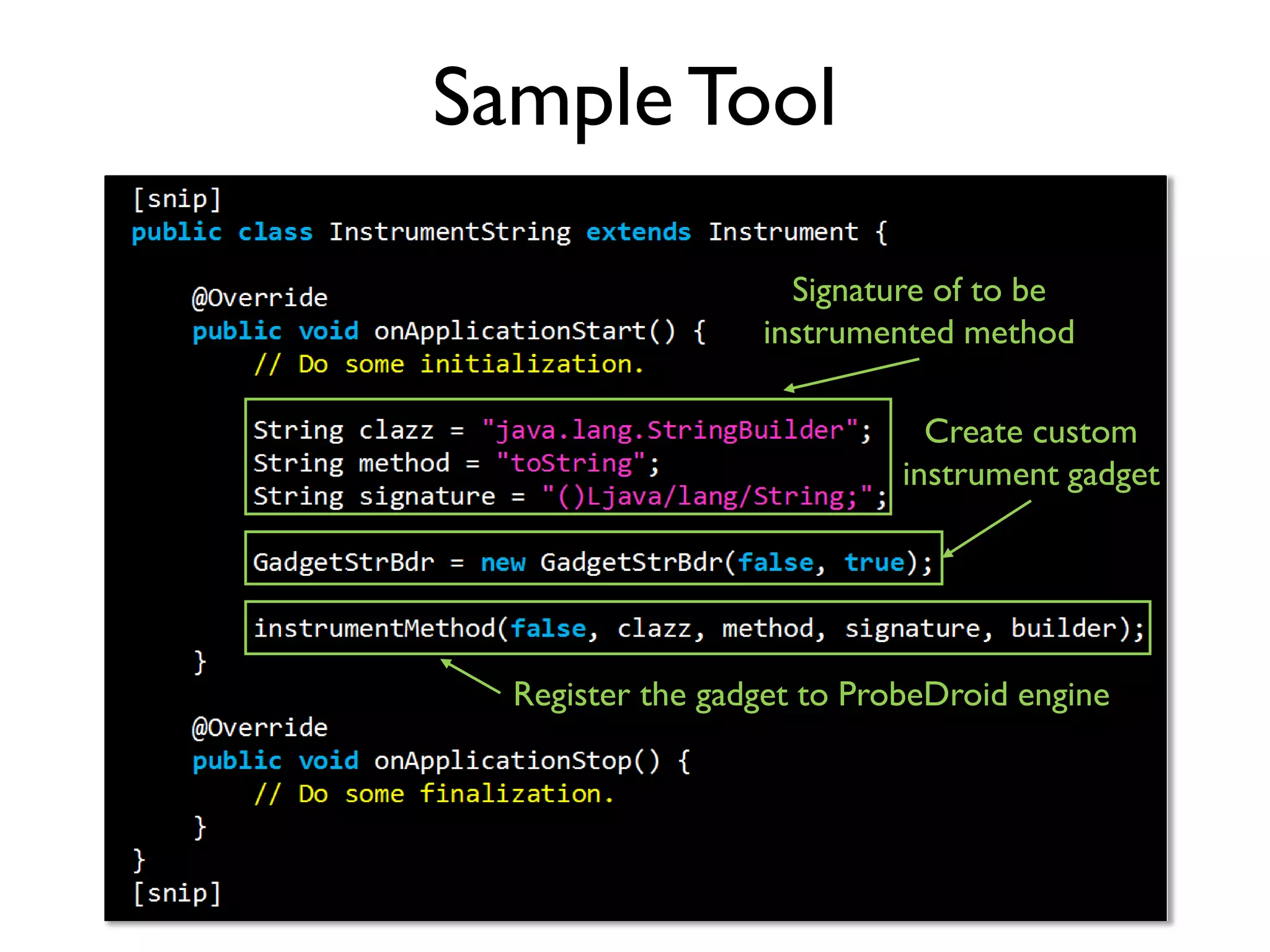
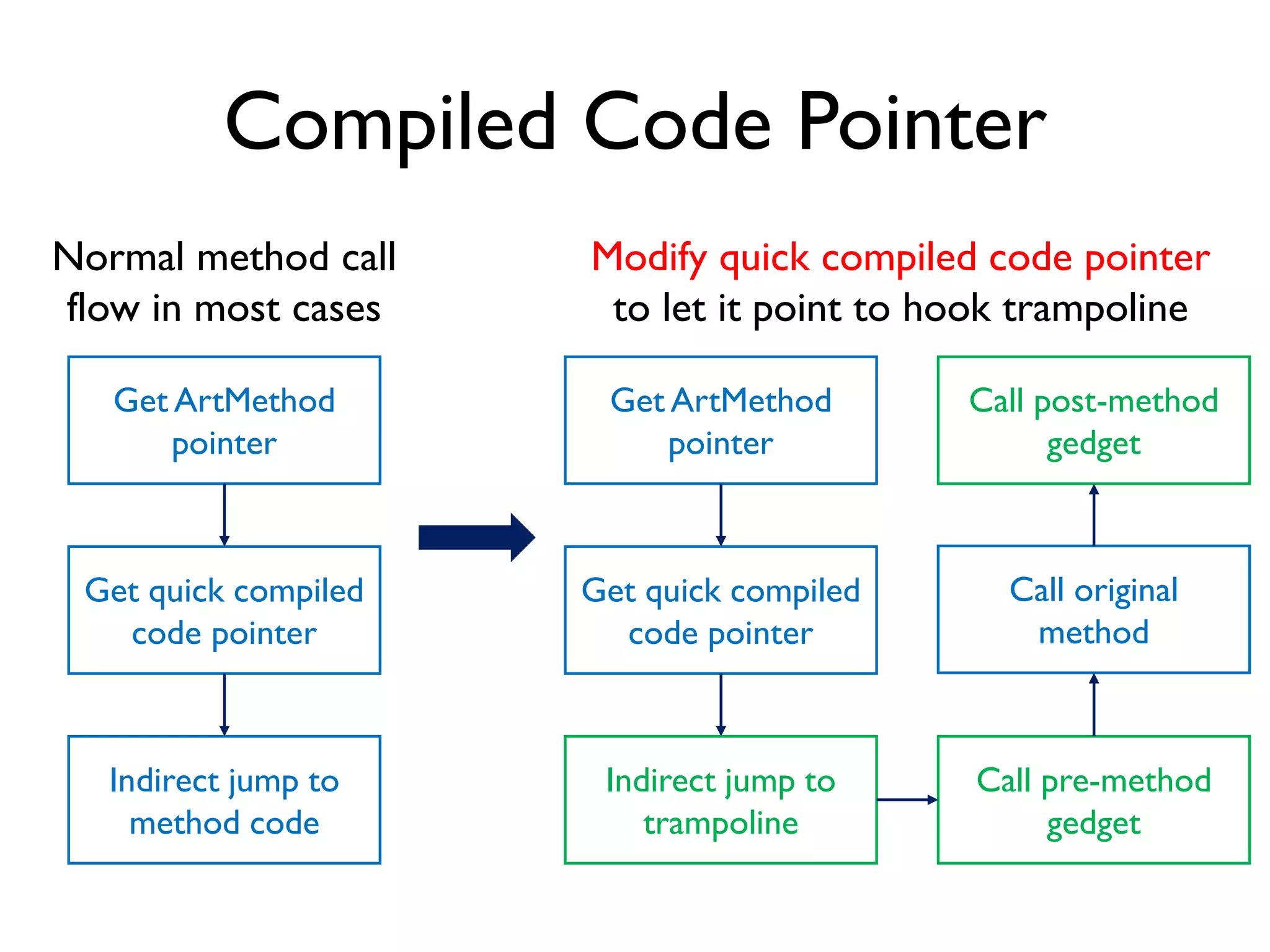
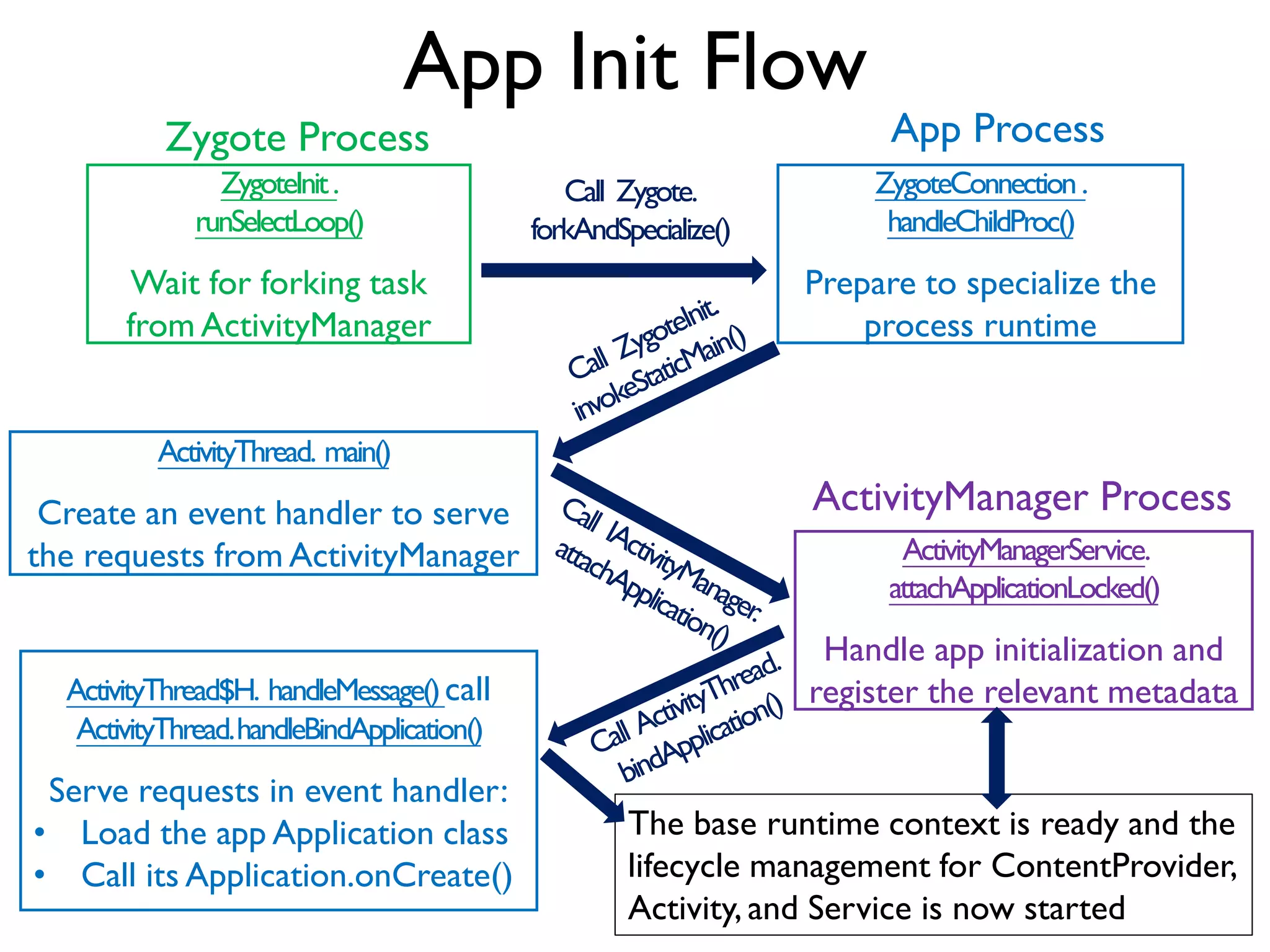
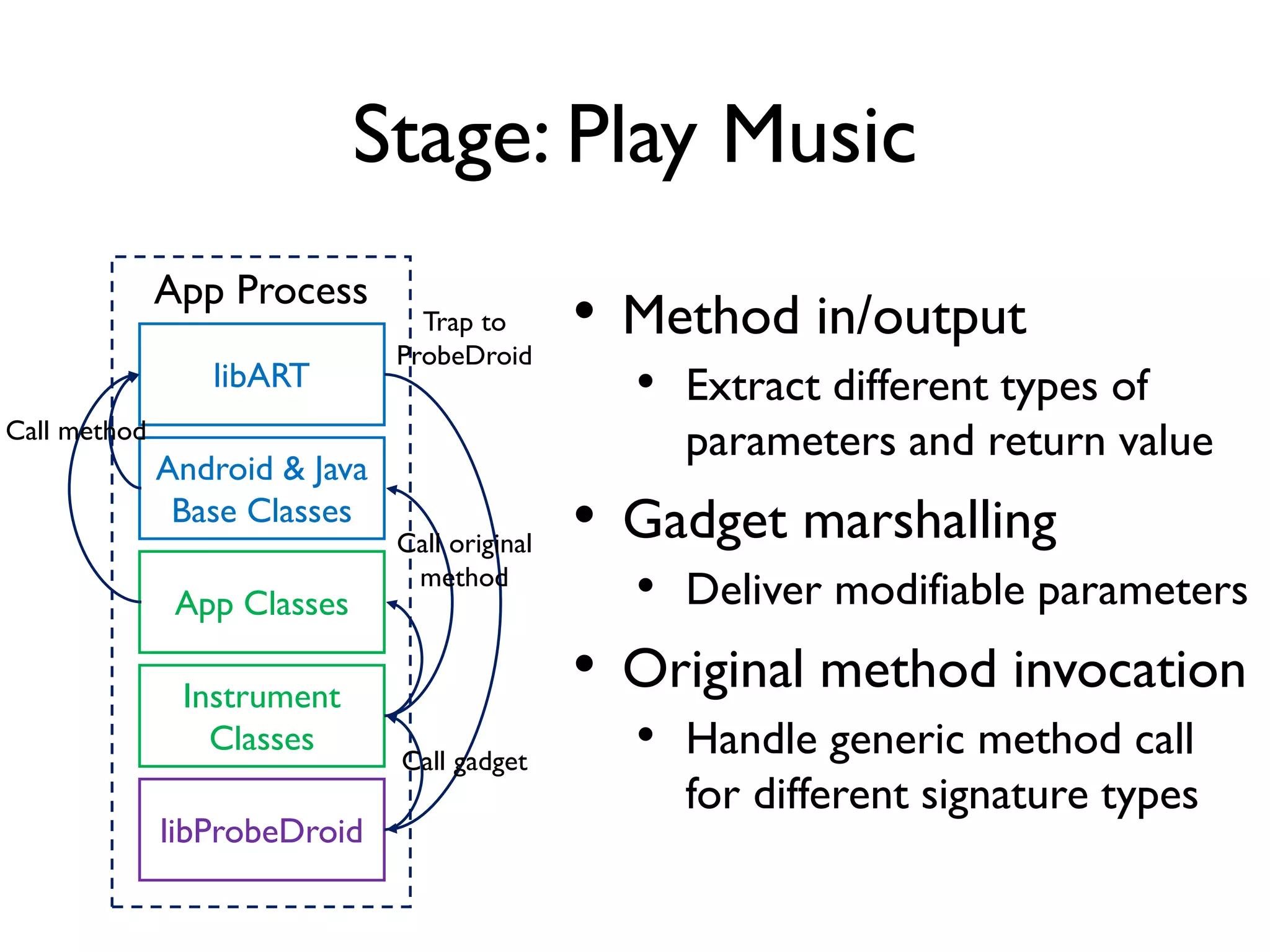
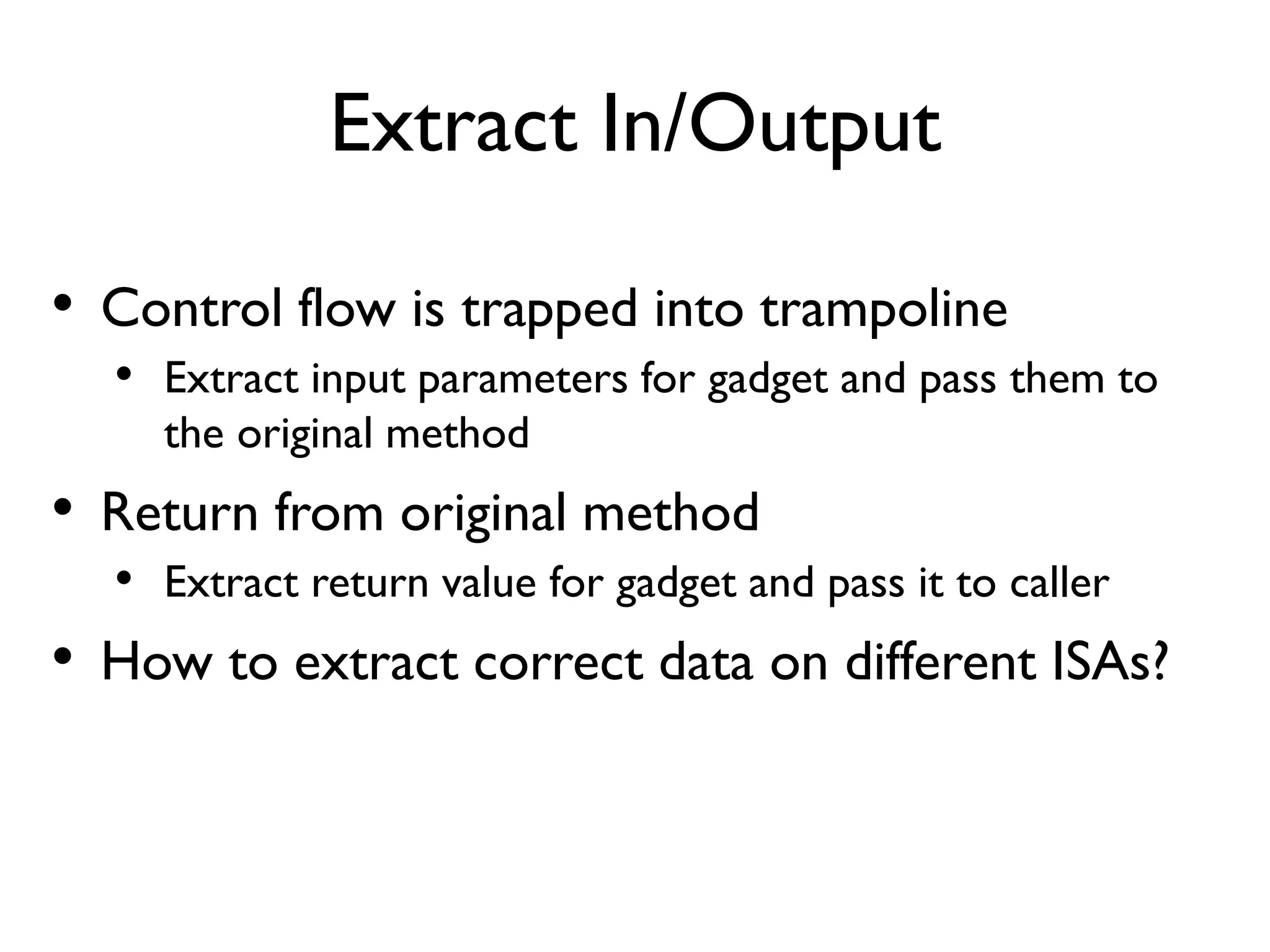
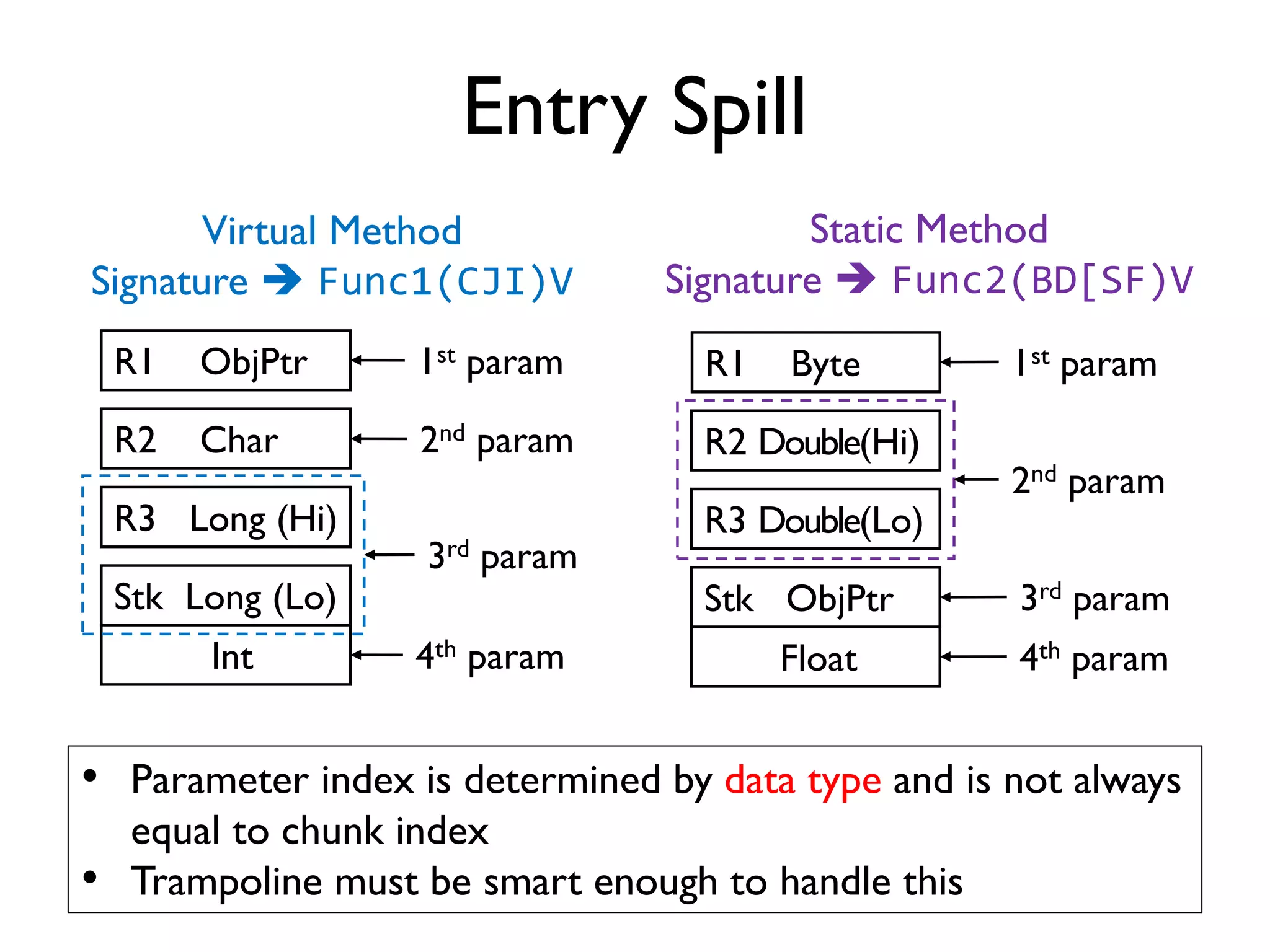
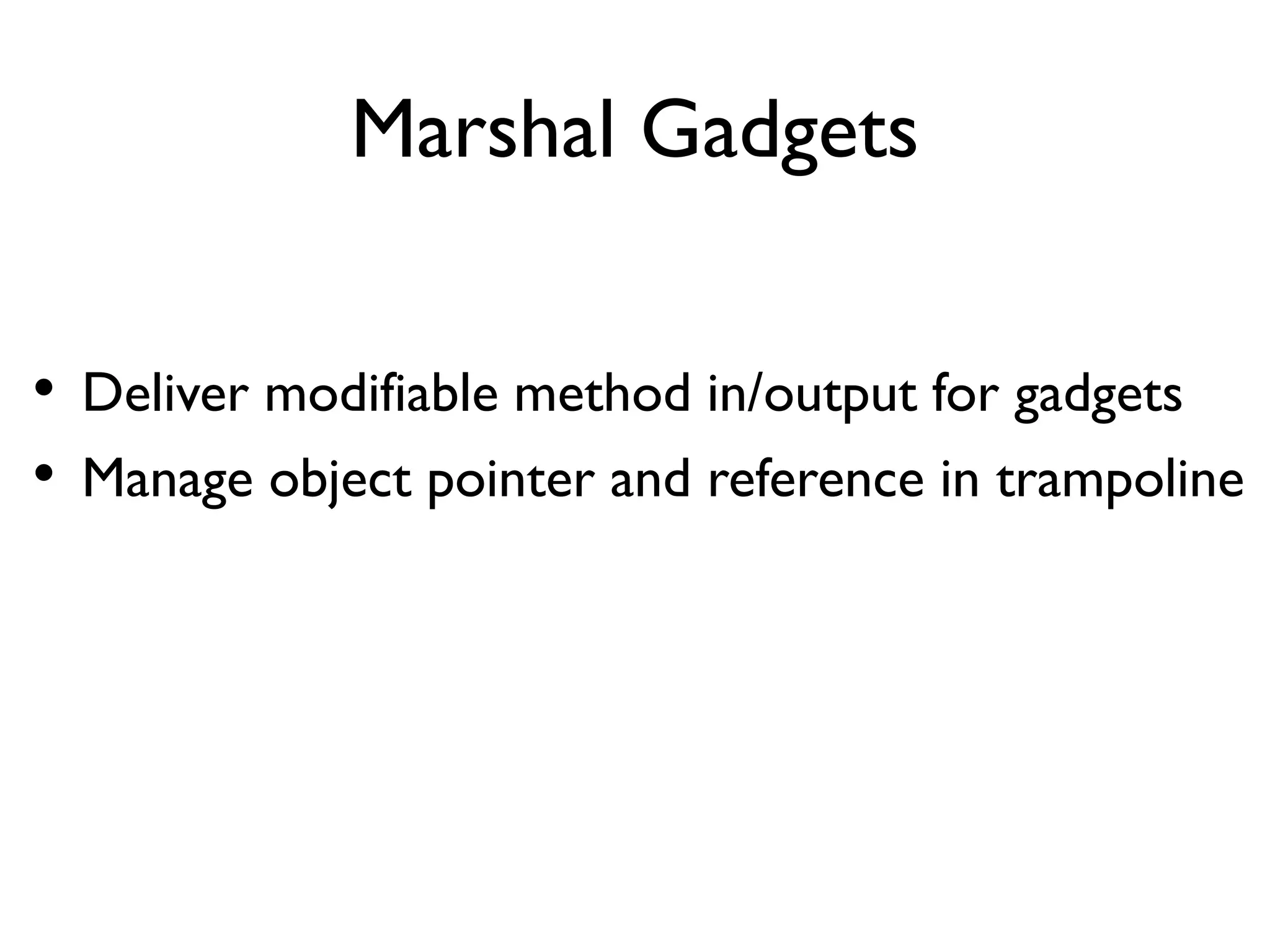
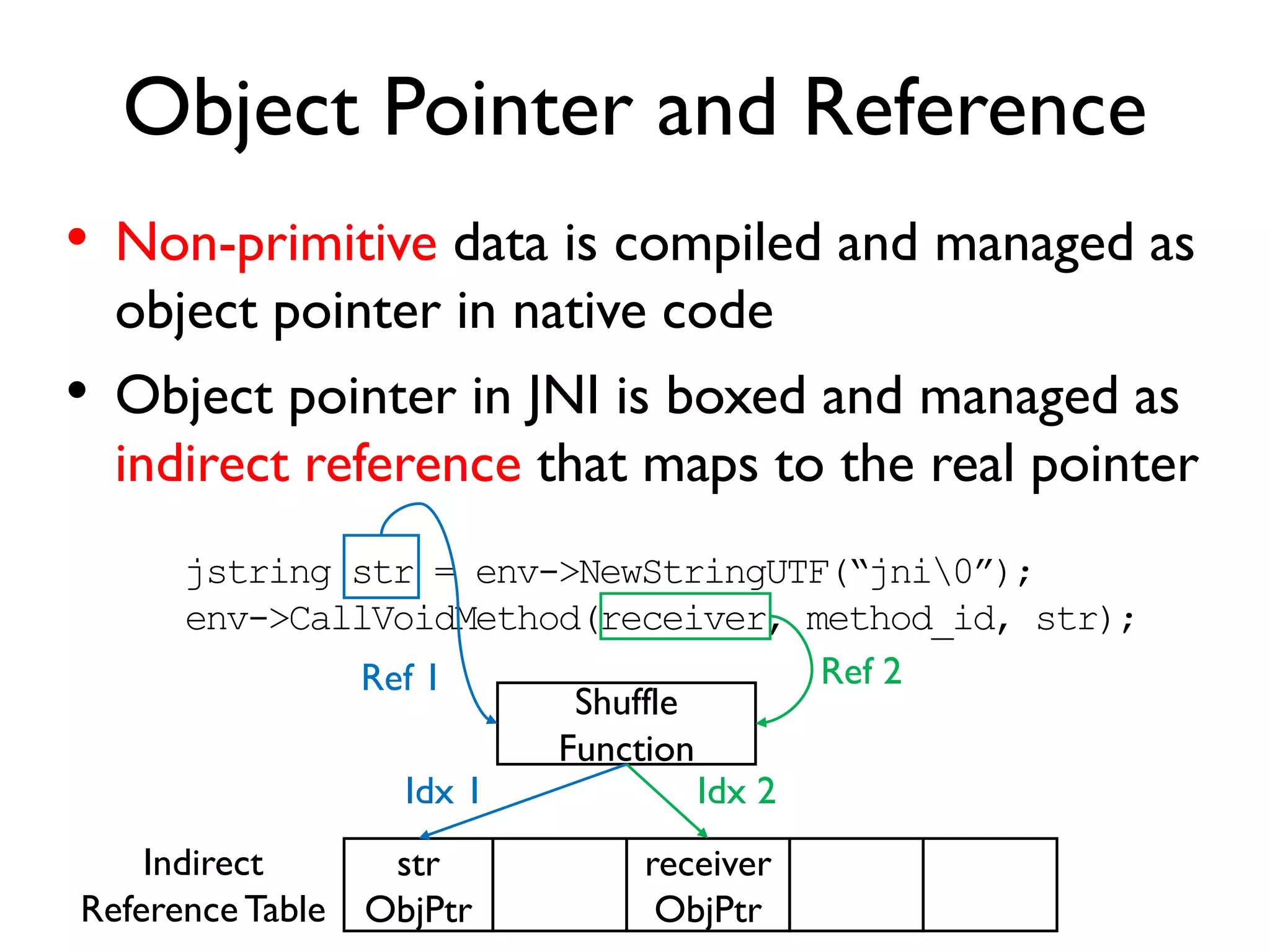
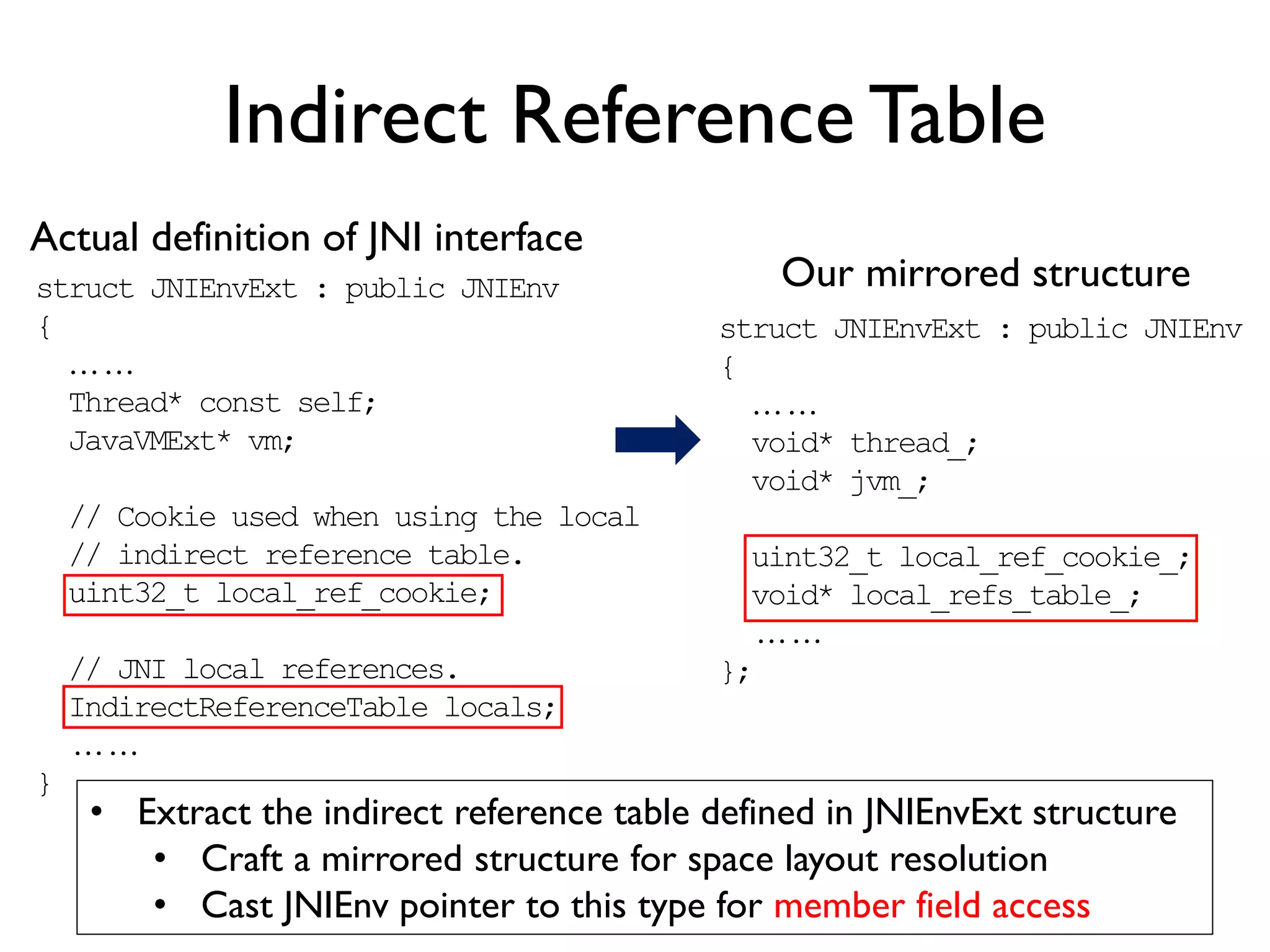
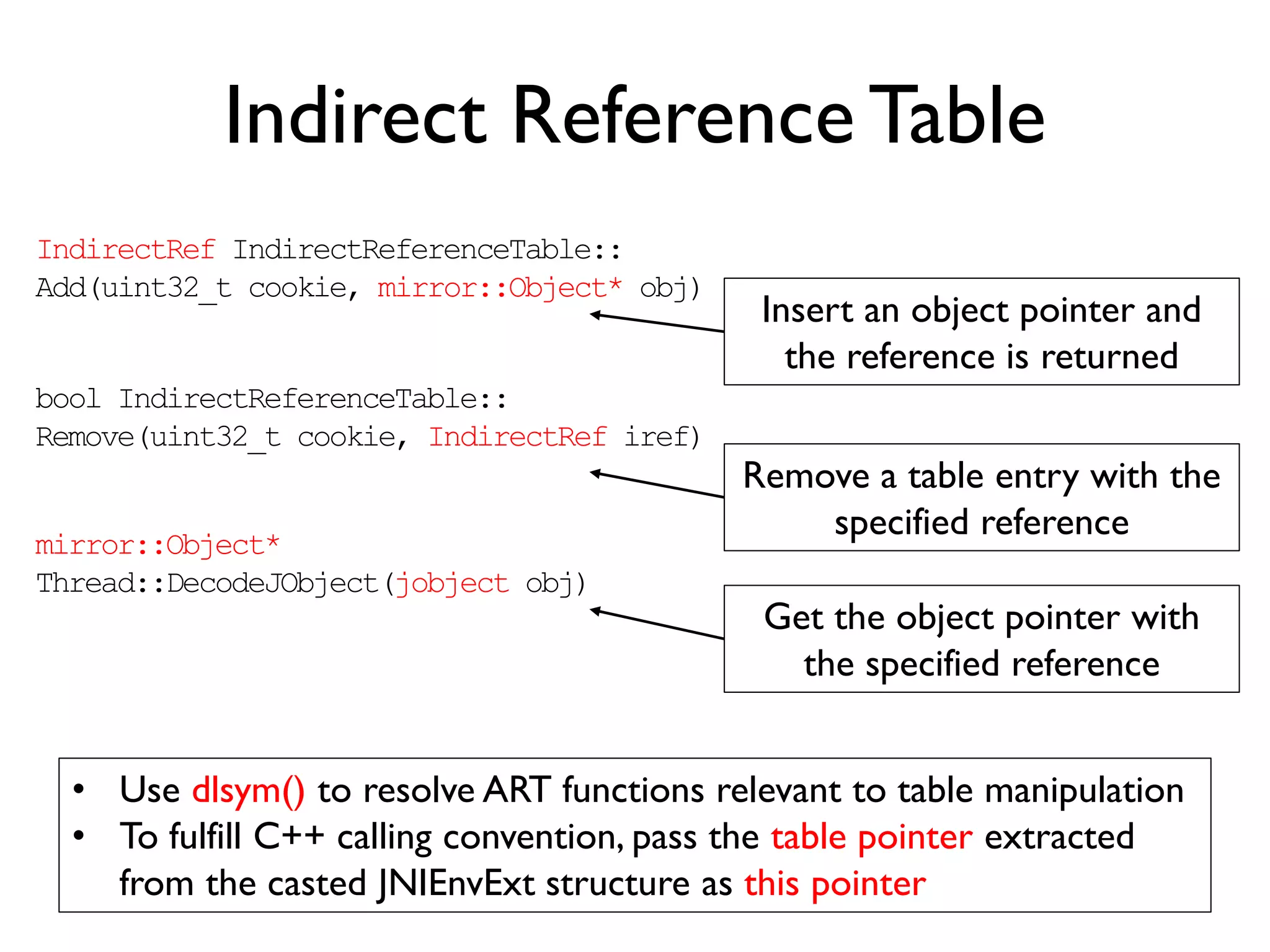
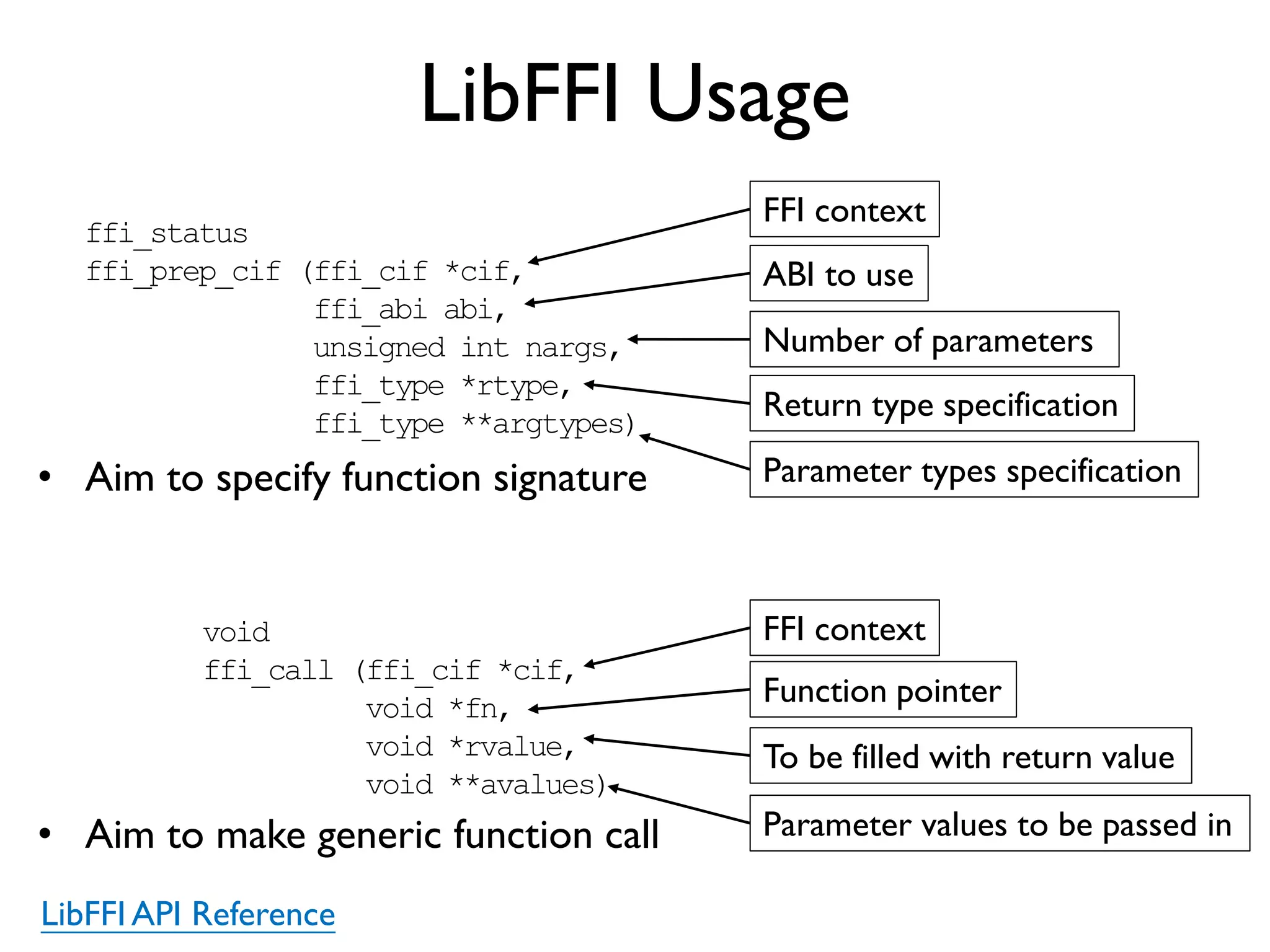
The document discusses Probedroid, a dynamic binary instrumentation tool for Android app behavior exploration, designed by Zongxian Shen. It details its features including the ability to manipulate methods, capture runtime information, and inject custom instrumentation into Android applications utilizing the ART runtime. The document also outlines the design, implementation, and usage of Probedroid, along with examples of its applications in app analysis and debugging.










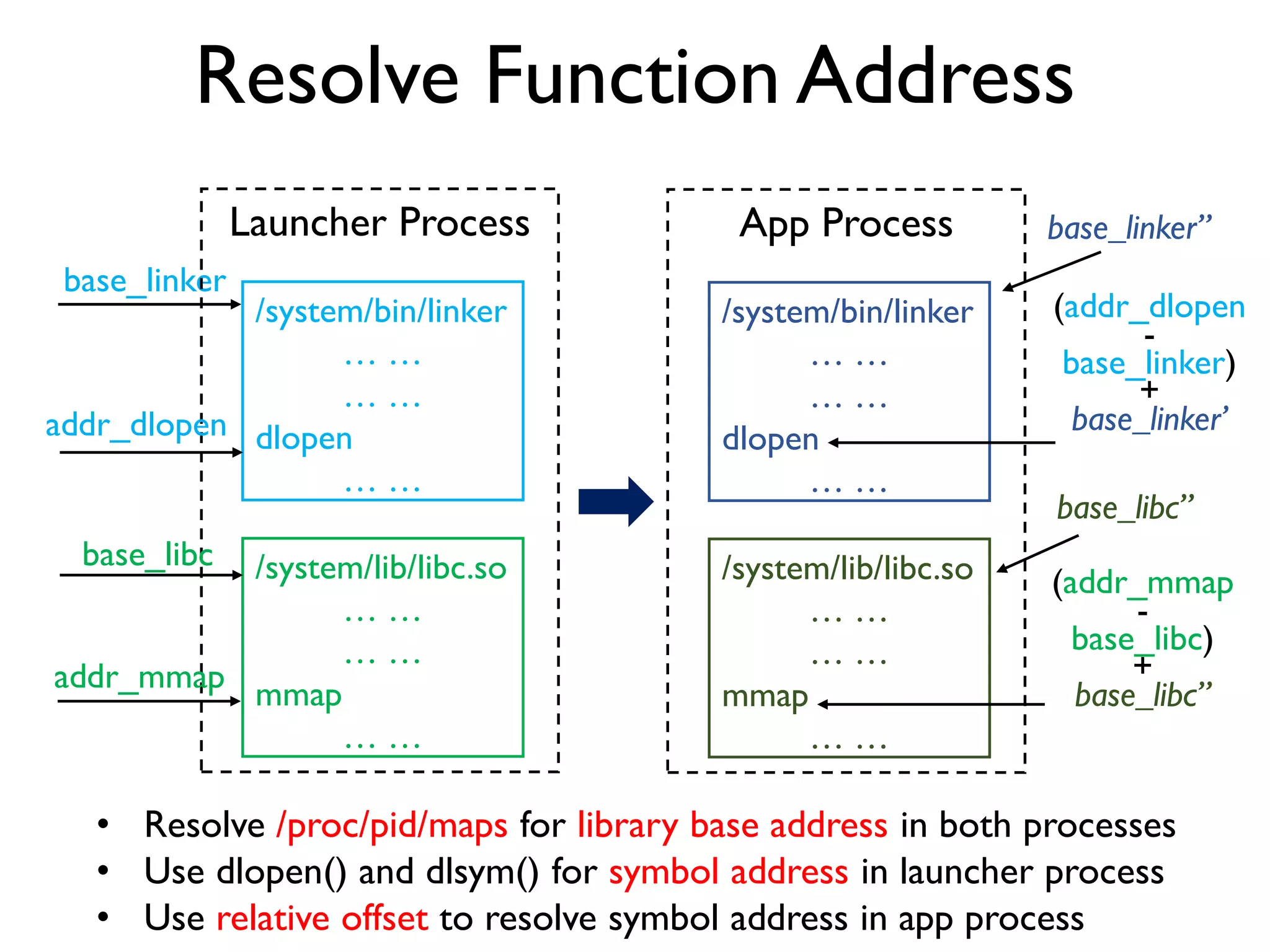
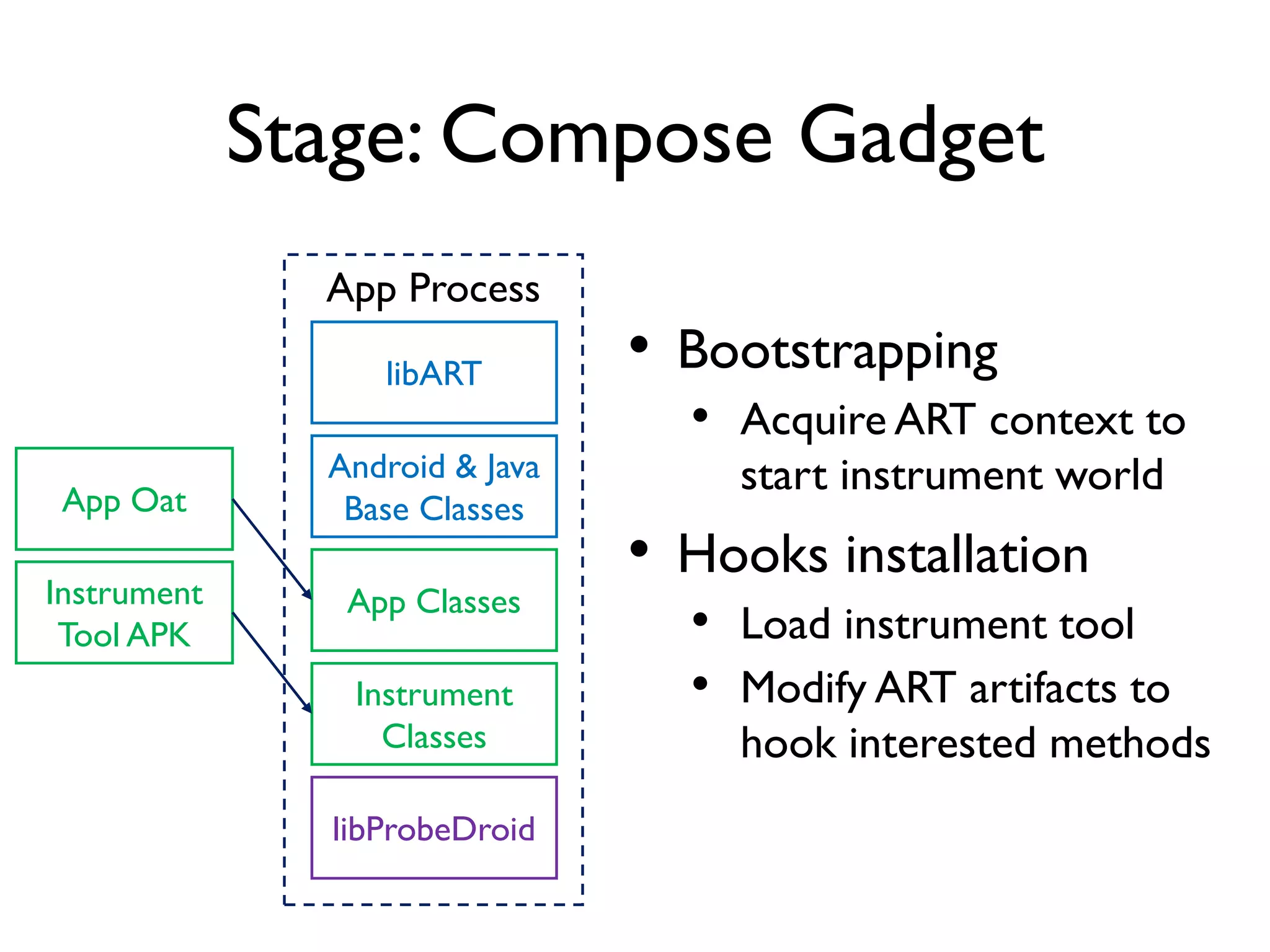

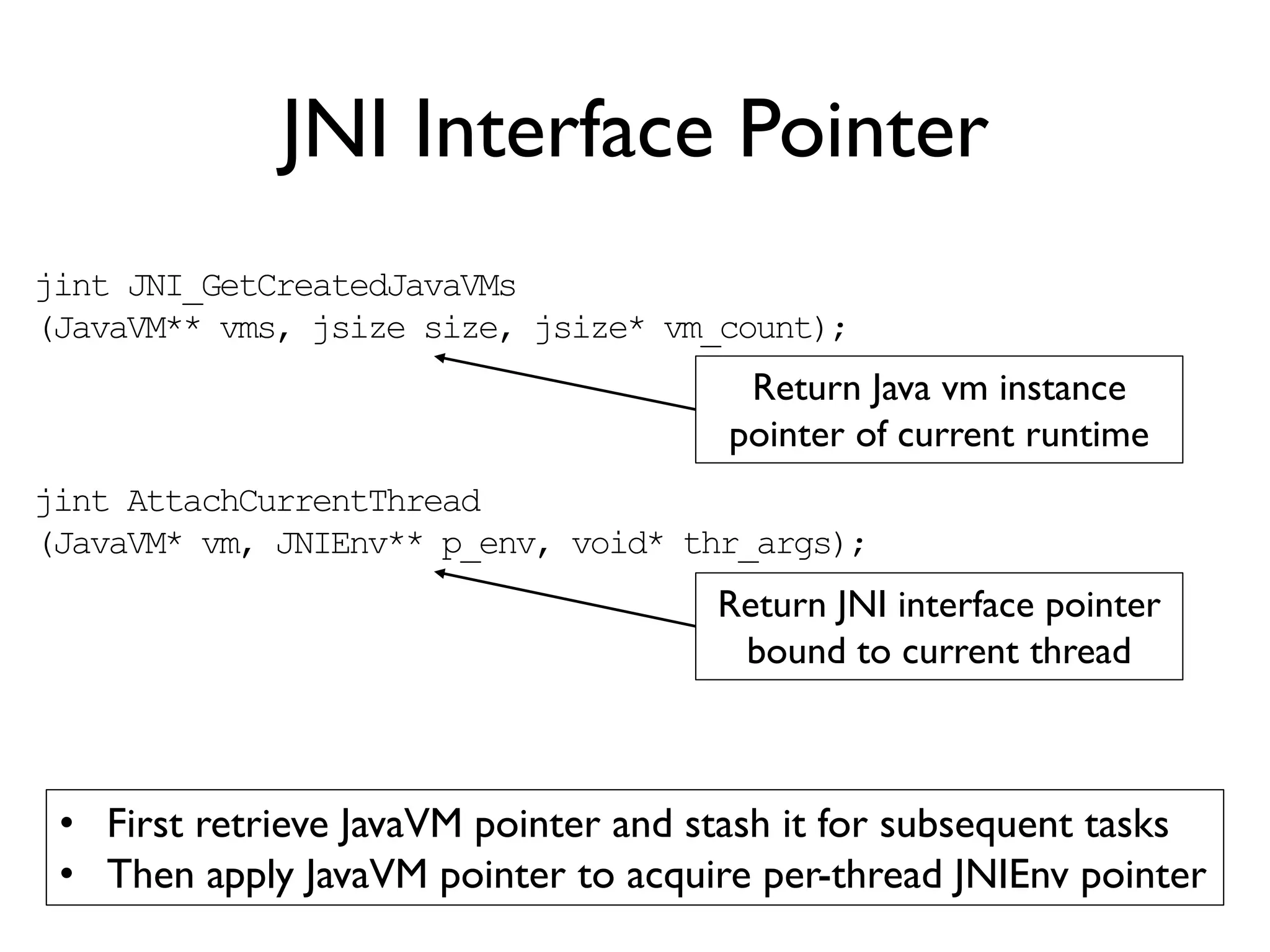

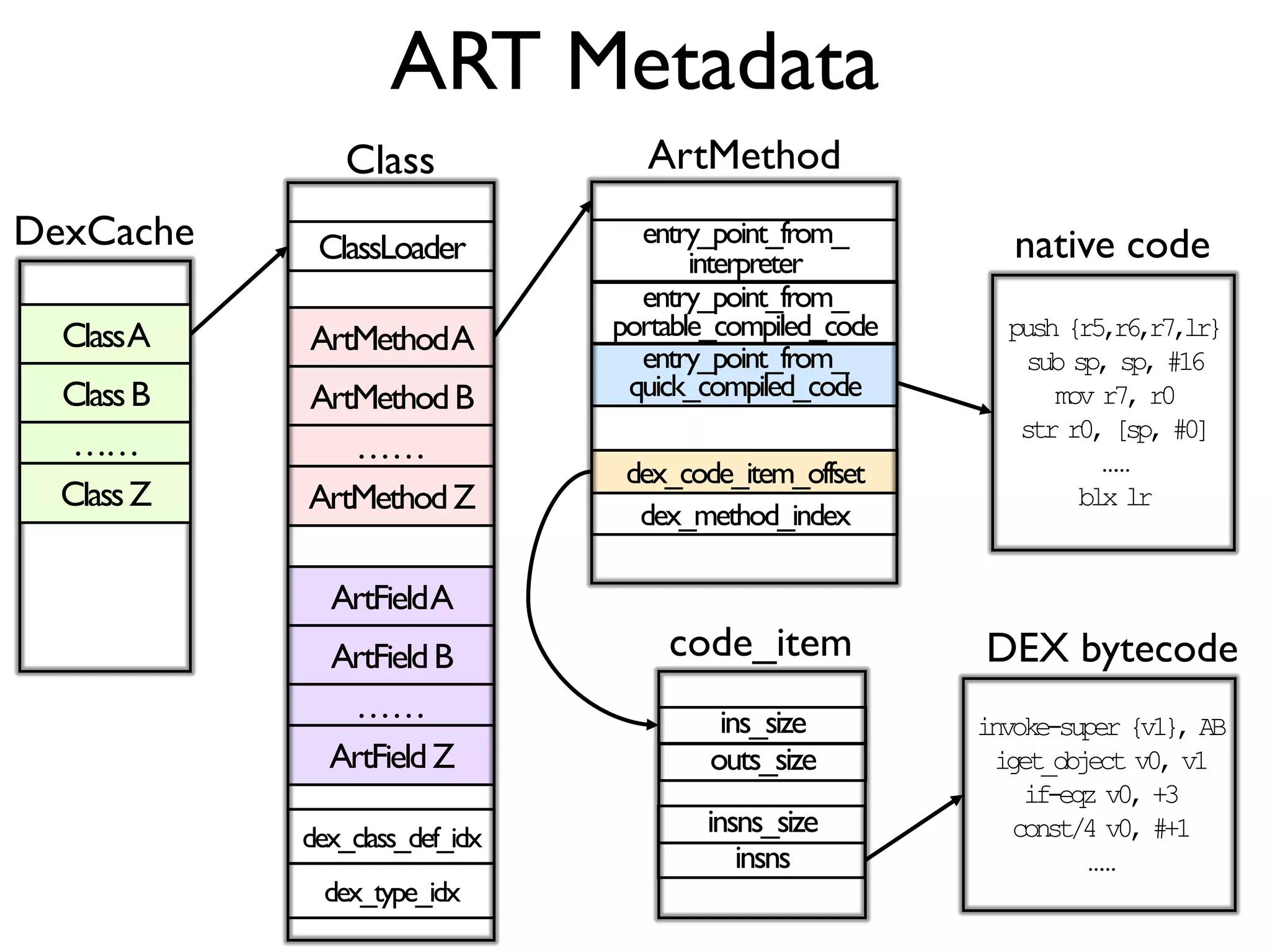
![ART Metadata
ClassA
ClassB
ClassZ
……
DexCache
ArtMethodA
ArtMethodB
ArtMethodZ
……
ArtFieldA
ArtFieldB
ArtFieldZ
……
ClassLoader
dex_class_def_idx
dex_type_idx
Class
entry_point_from_
interpreter
entry_point_from_
portable_compiled_code
entry_point_from_
quick_compiled_code
dex_code_item_offset
dex_method_index
ArtMethod
push {r5,r6,r7,lr}
sub sp, sp, #16
mov r7, r0
str r0, [sp, #0]
……
blx lr
code_item
ins_size
outs_size
insns_size
insns
invoke-super {v1}, AB
iget_object v0, v1
if-eqz v0, +3
const/4 v0, #+1
……
native code
DEX bytecode](https://image.slidesharecdn.com/probedroid-craftingyourowndynamicinstrumenttoolonandroidforappbehaviorexploration-160818070429/75/ProbeDroid-Crafting-Your-Own-Dynamic-Instrument-Tool-on-Android-for-App-Behavior-Exploration-27-2048.jpg)
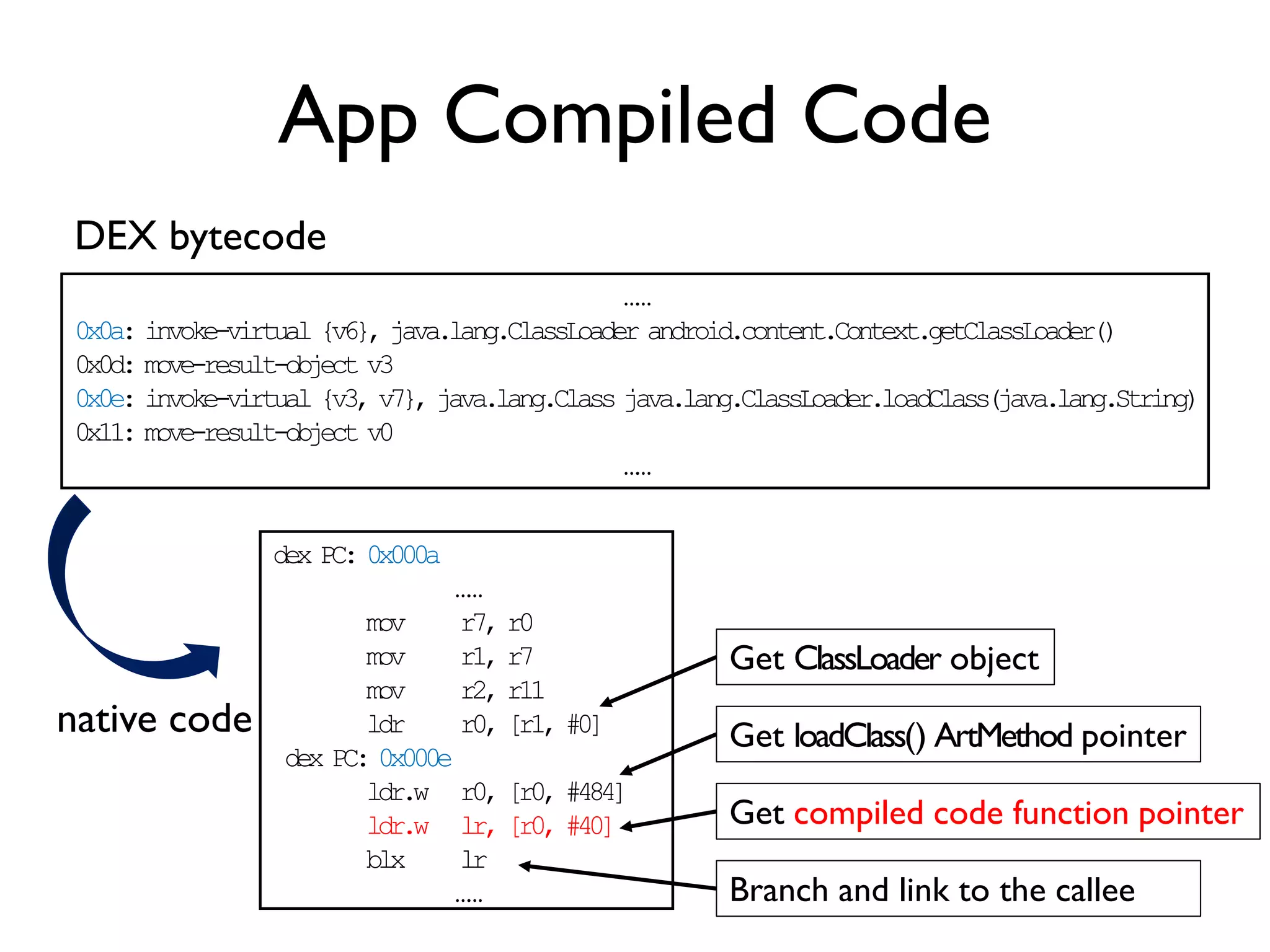
![App Compiled Code
……
0x0a: invoke-virtual {v6}, java.lang.ClassLoader android.content.Context.getClassLoader()
0x0d: move-result-object v3
0x0e: invoke-virtual {v3, v7}, java.lang.Class java.lang.ClassLoader.loadClass(java.lang.String)
0x11: move-result-object v0
……
DEX bytecode
dex PC: 0x000a
……
mov r7, r0
mov r1, r7
mov r2, r11
ldr r0, [r1, #0]
dex PC: 0x000e
ldr.w r0, [r0, #484]
ldr.w lr, [r0, #40]
blx lr
……
native code
Get ClassLoader object
Get loadClass() ArtMethod pointer
Get compiled code function pointer
Branch and link to the callee](https://image.slidesharecdn.com/probedroid-craftingyourowndynamicinstrumenttoolonandroidforappbehaviorexploration-160818070429/75/ProbeDroid-Crafting-Your-Own-Dynamic-Instrument-Tool-on-Android-for-App-Behavior-Exploration-28-2048.jpg)

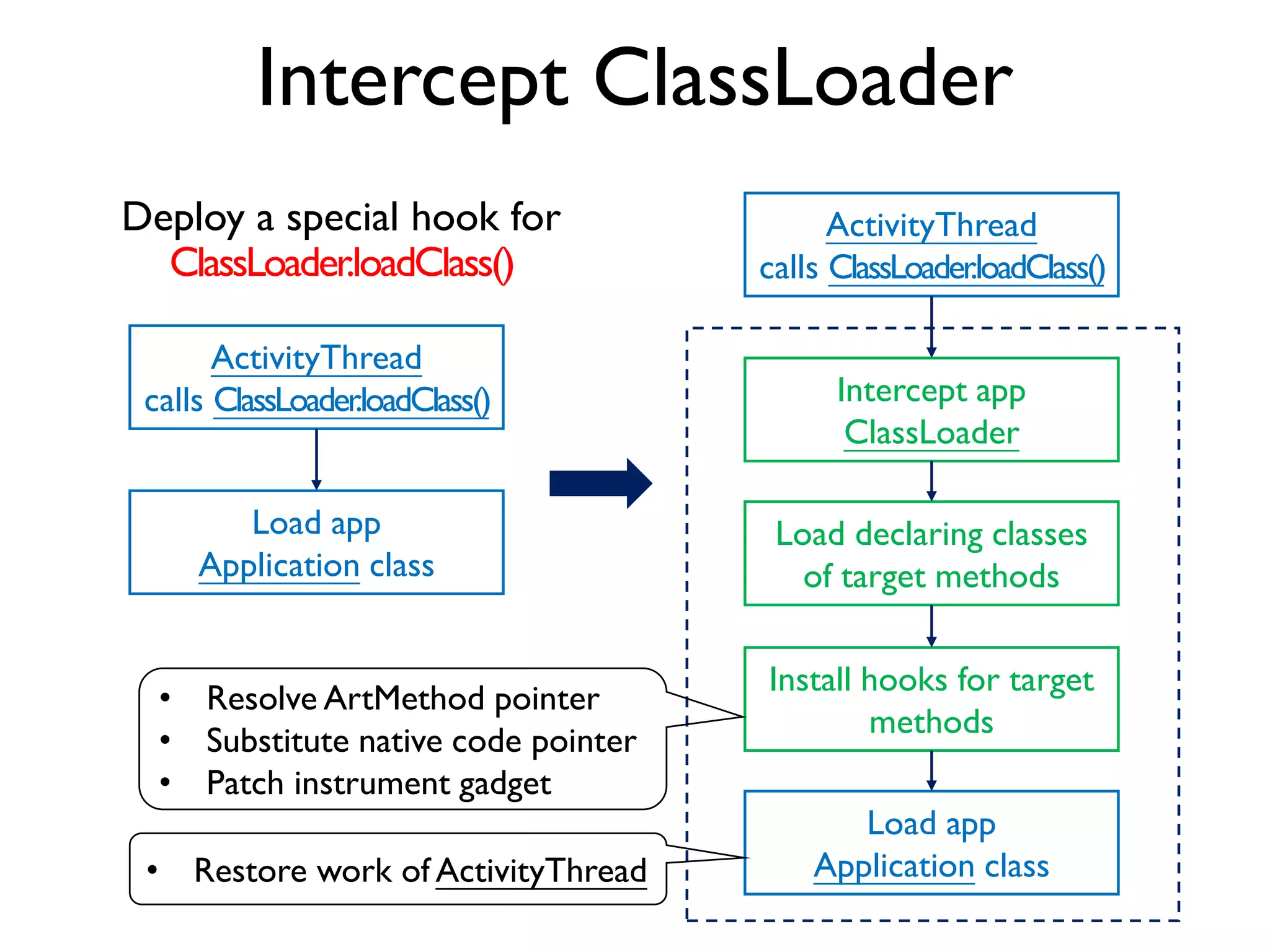










![Obfuscated App
• Detect dynamic code loading and intercept the payload
DexClassLoader
<init>(String dexPath, String optimizedDirectory,
String librarySearchPath, ClassLoader parent)
More relevant methods … …
Field Class.getDeclaredField(String name)
Method Class.getDeclaredMethod(String name)
Object Field.get(Object object)
Object Method.invoke(Object receiver, Object[] args)
More relevant methods … …
• Resolve the method and field mutated via Java reflection](https://image.slidesharecdn.com/probedroid-craftingyourowndynamicinstrumenttoolonandroidforappbehaviorexploration-160818070429/75/ProbeDroid-Crafting-Your-Own-Dynamic-Instrument-Tool-on-Android-for-App-Behavior-Exploration-51-2048.jpg)

