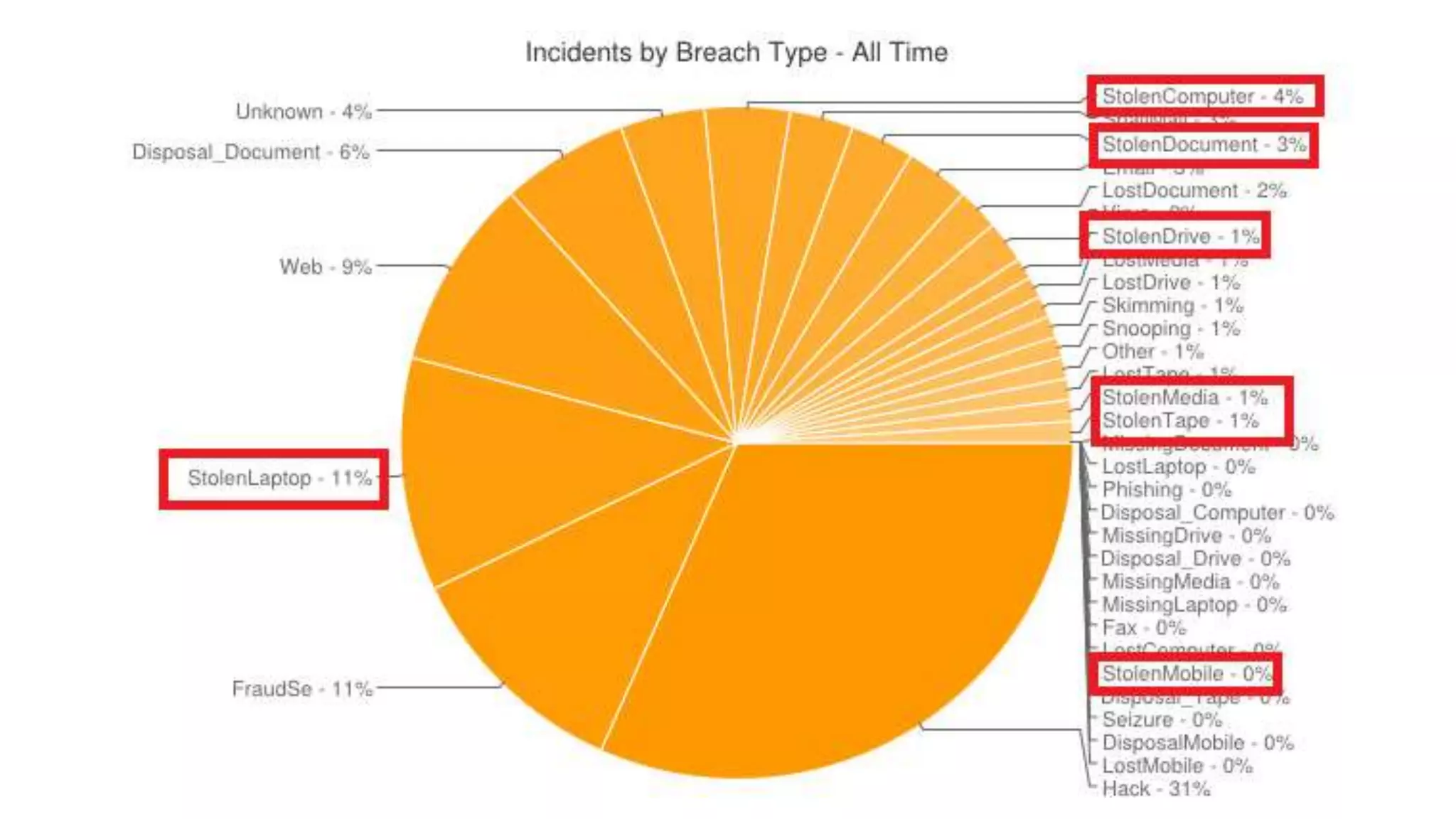
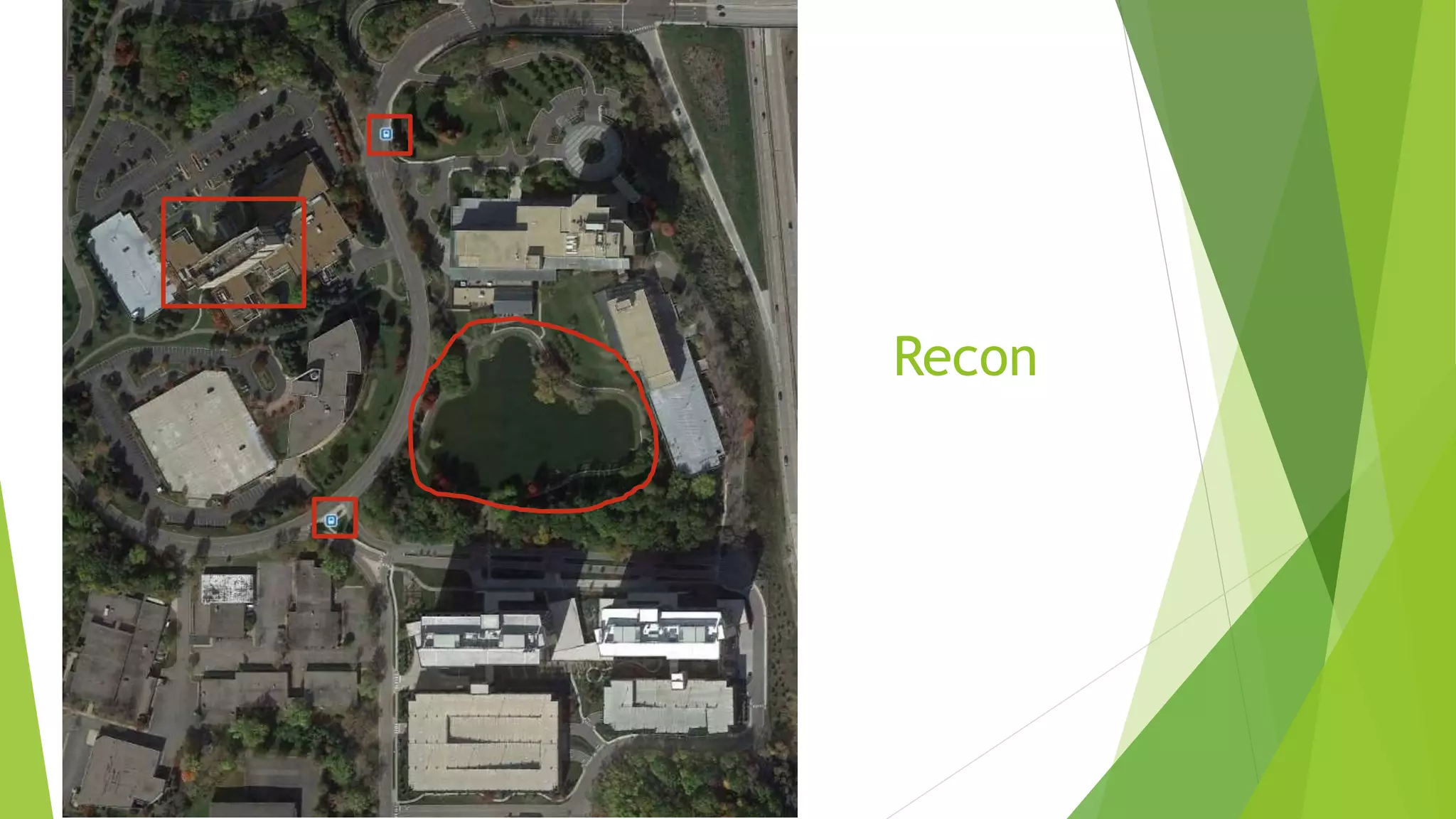
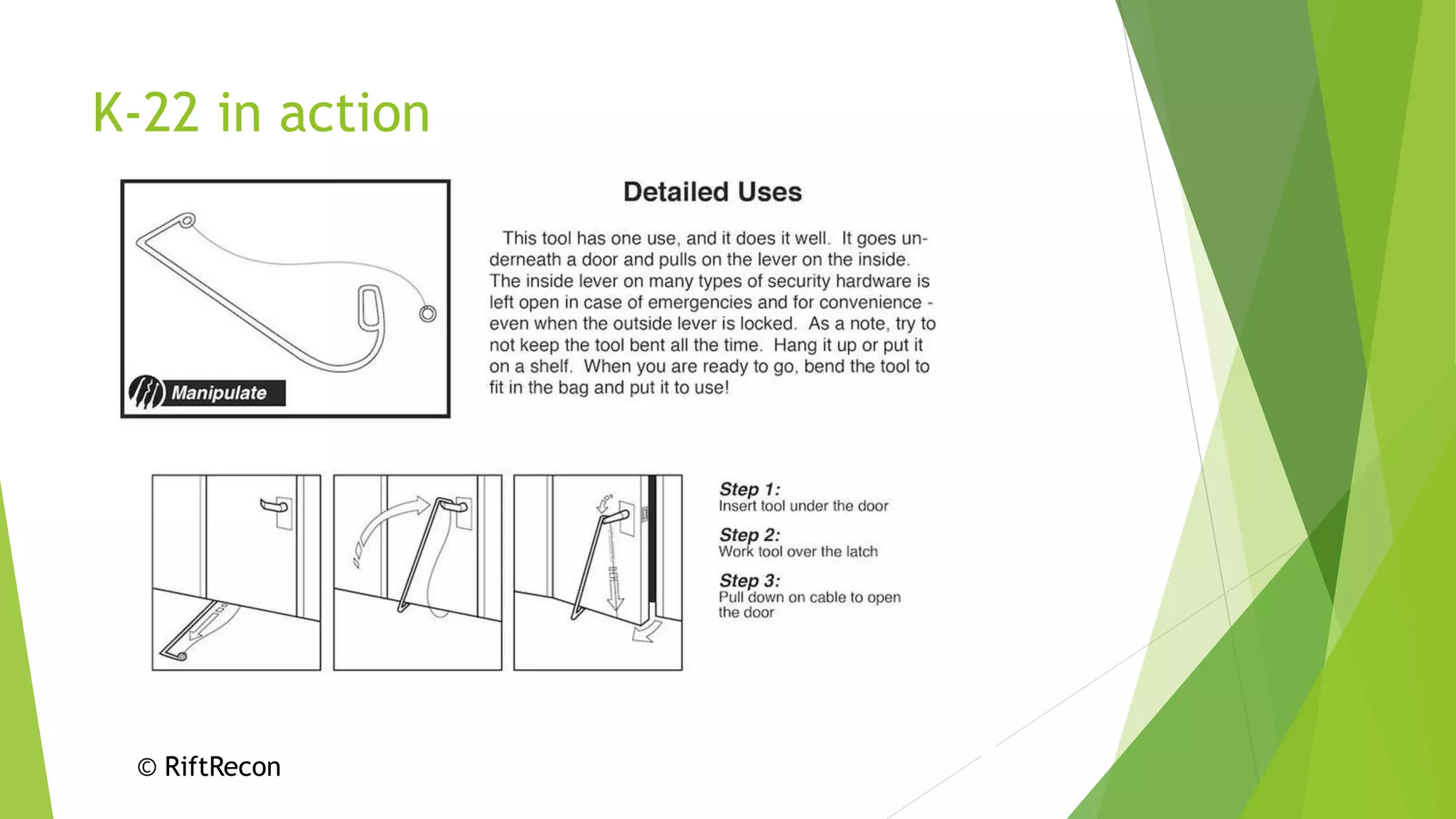
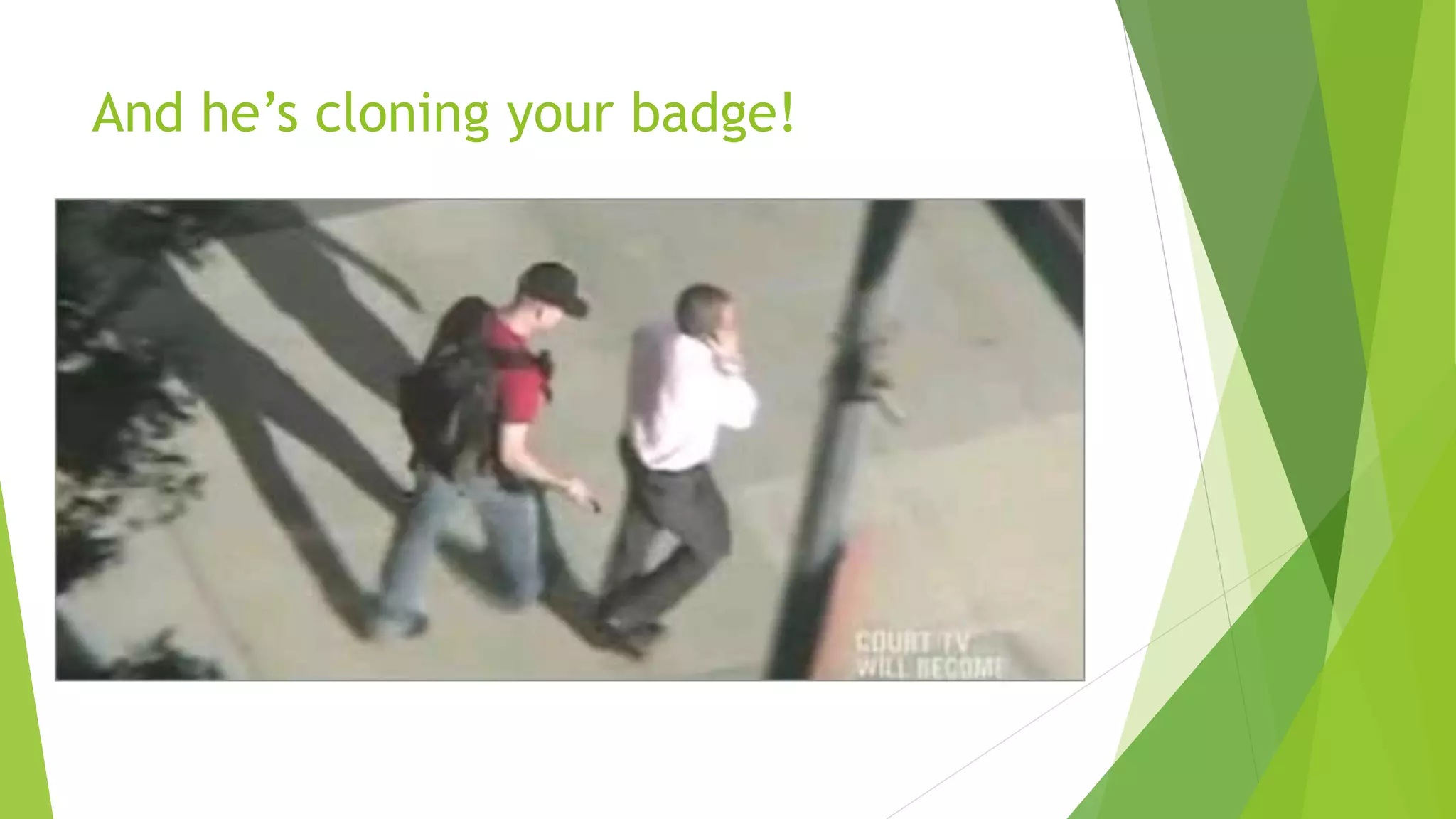
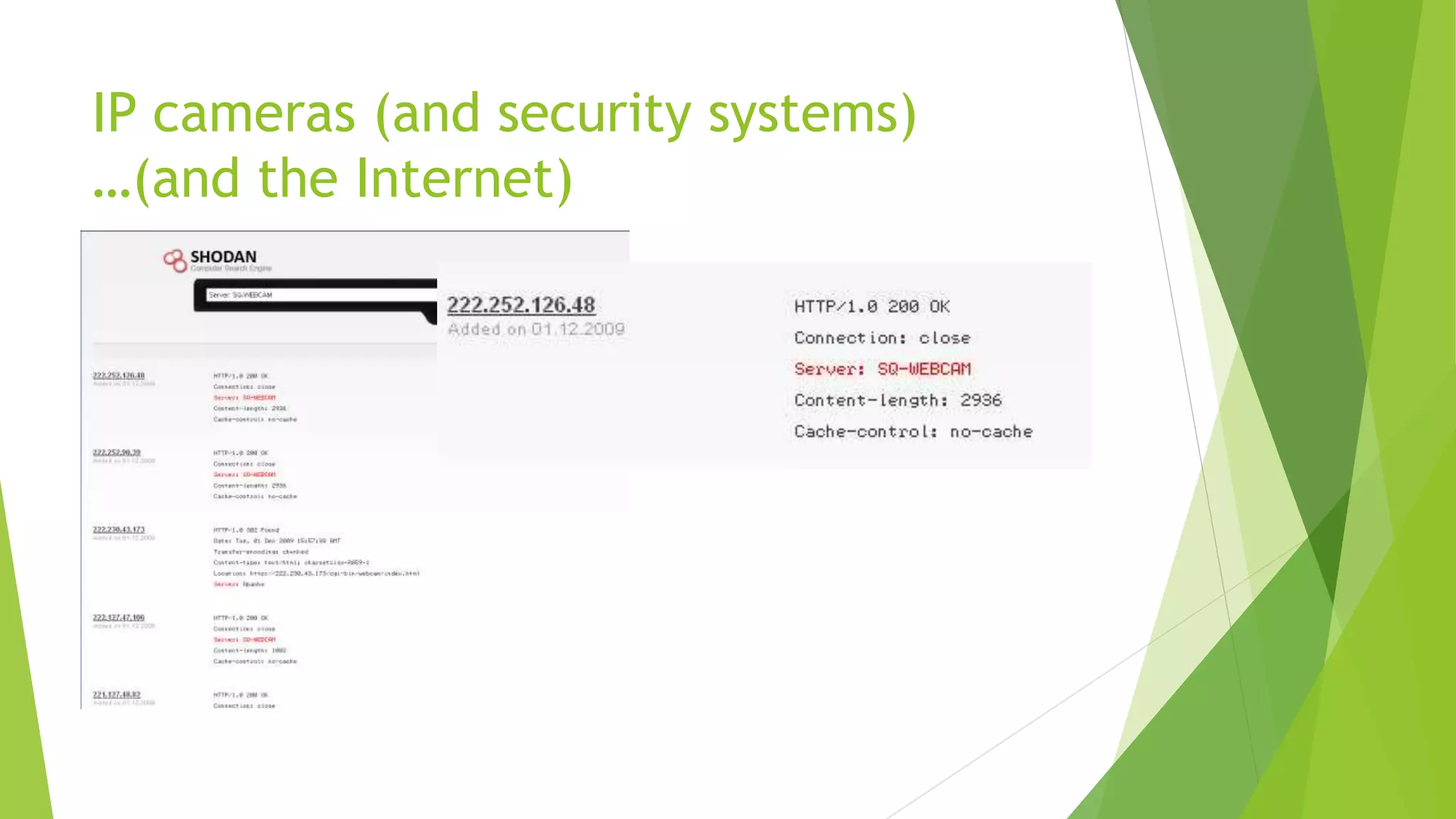
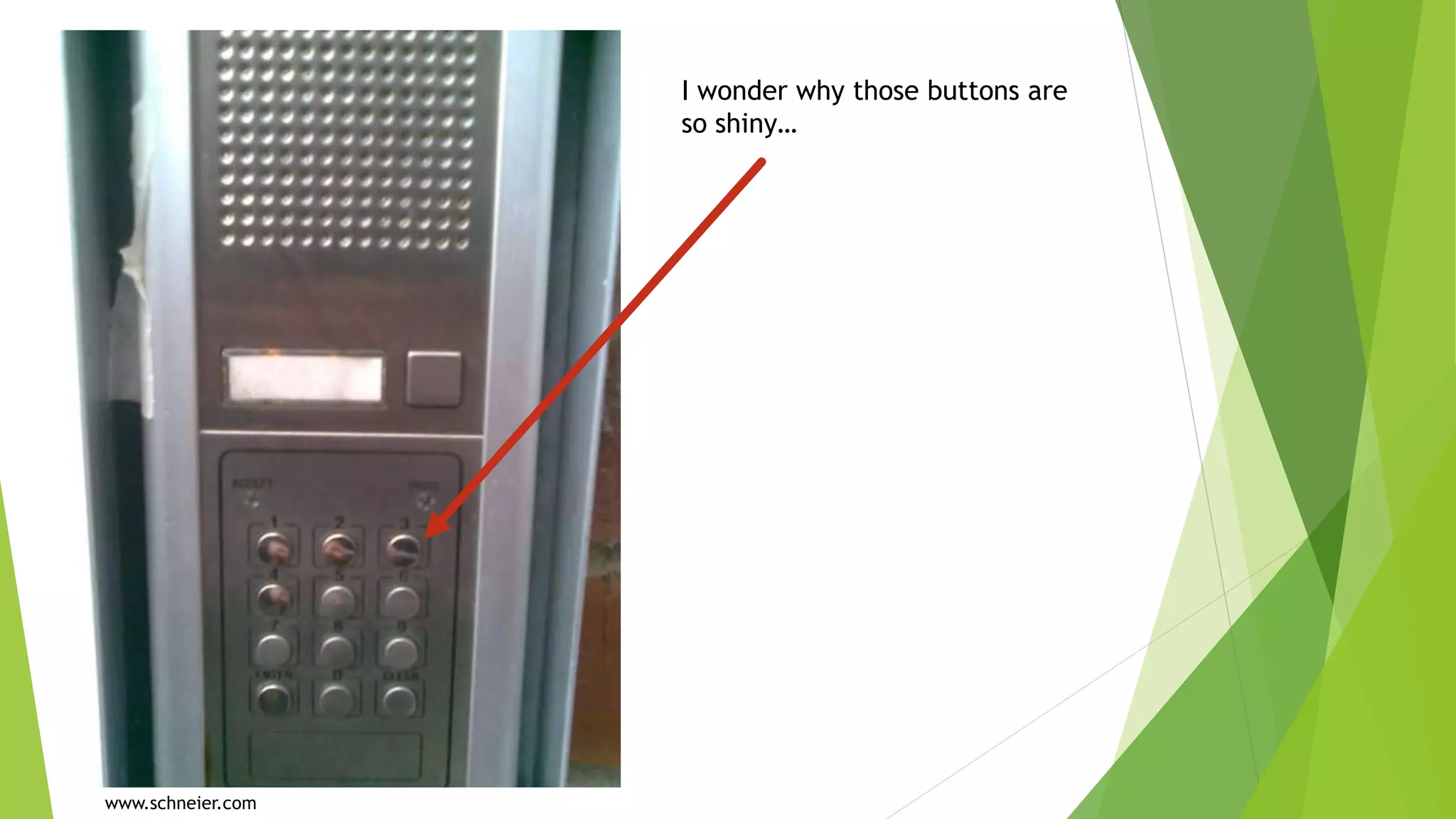
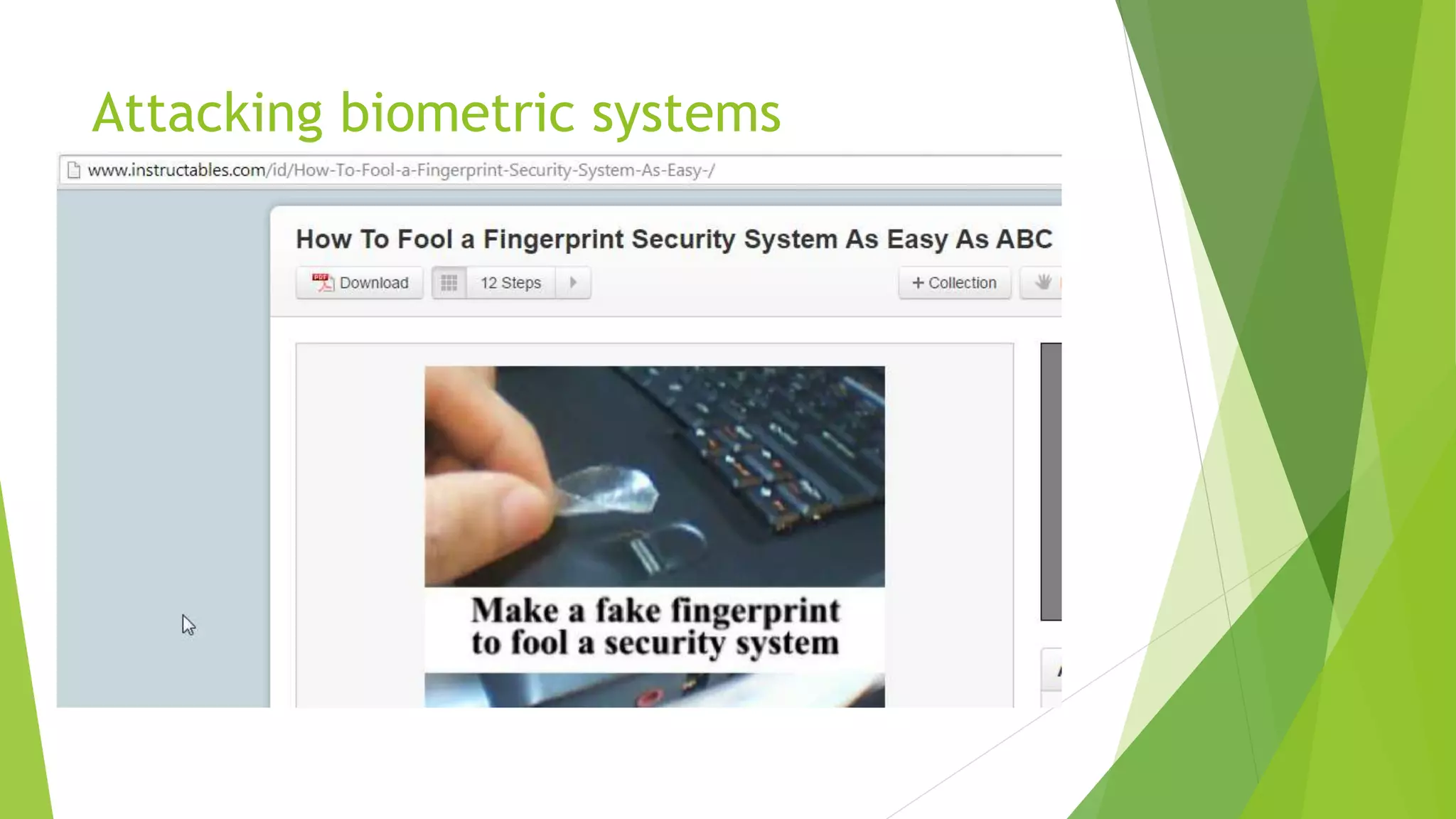
This document discusses how attackers can bypass physical security measures to steal data from organizations. It begins by providing the speaker's background and disclaimer. It then outlines common ways data has been lost through physical theft. The rest of the document demonstrates how attackers could bypass perimeter security, doors, locks, badges, cameras and other controls through methods like social engineering, lock picking, bypass tools and more. It emphasizes the importance of proper physical security implementation and monitoring to detect intrusions.