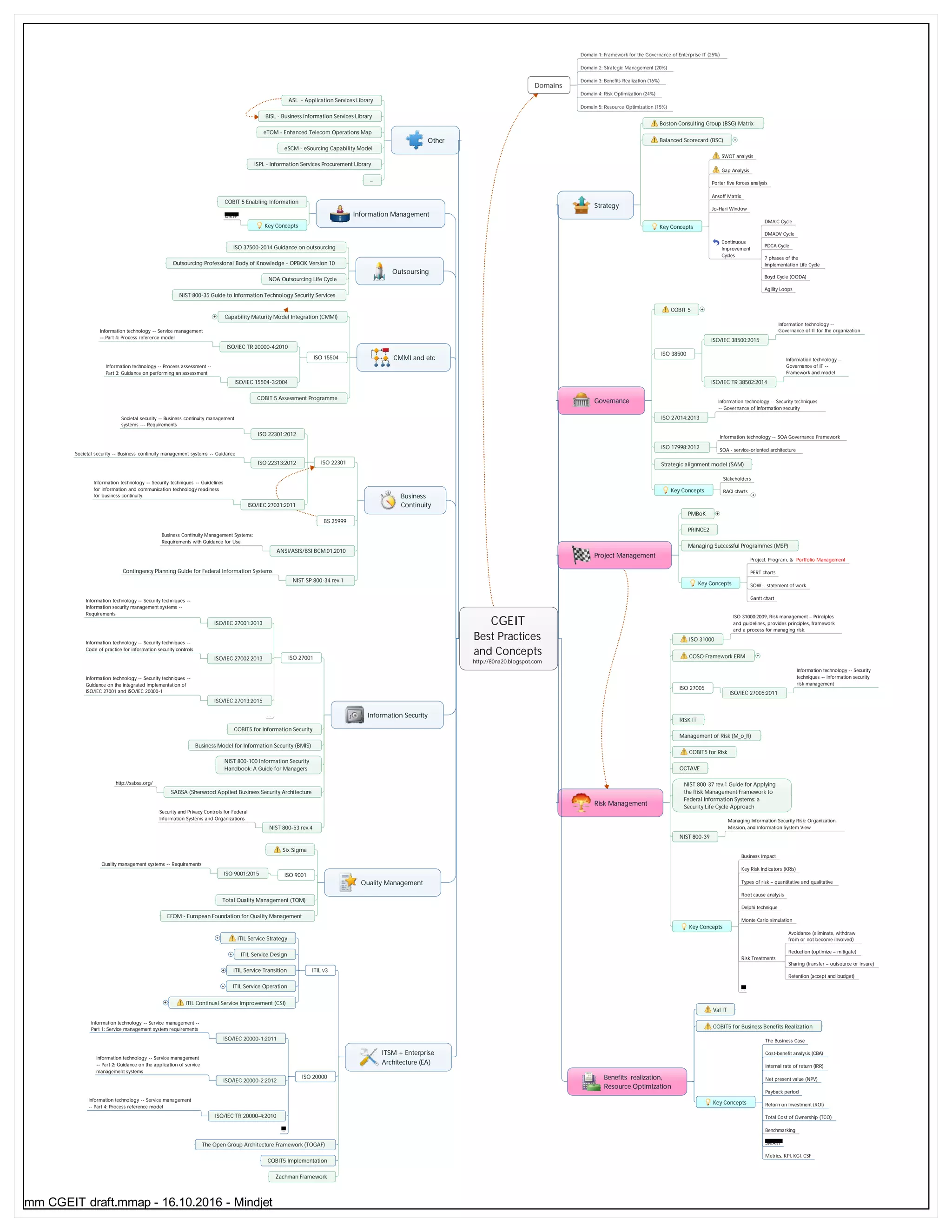
This document provides an overview of best practices, concepts, frameworks, standards, and methodologies related to enterprise IT governance. It covers key areas such as strategy, continuous improvement, governance, project management, risk management, benefits realization, IT service management, enterprise architecture, quality management, information security, and business continuity. Frameworks mentioned include COBIT, ISO standards, ITIL, TOGAF, PRINCE2, Val IT, and NIST. The CGEIT exam focuses on enterprise IT governance with emphasis on strategic management, benefits realization, and risk optimization.