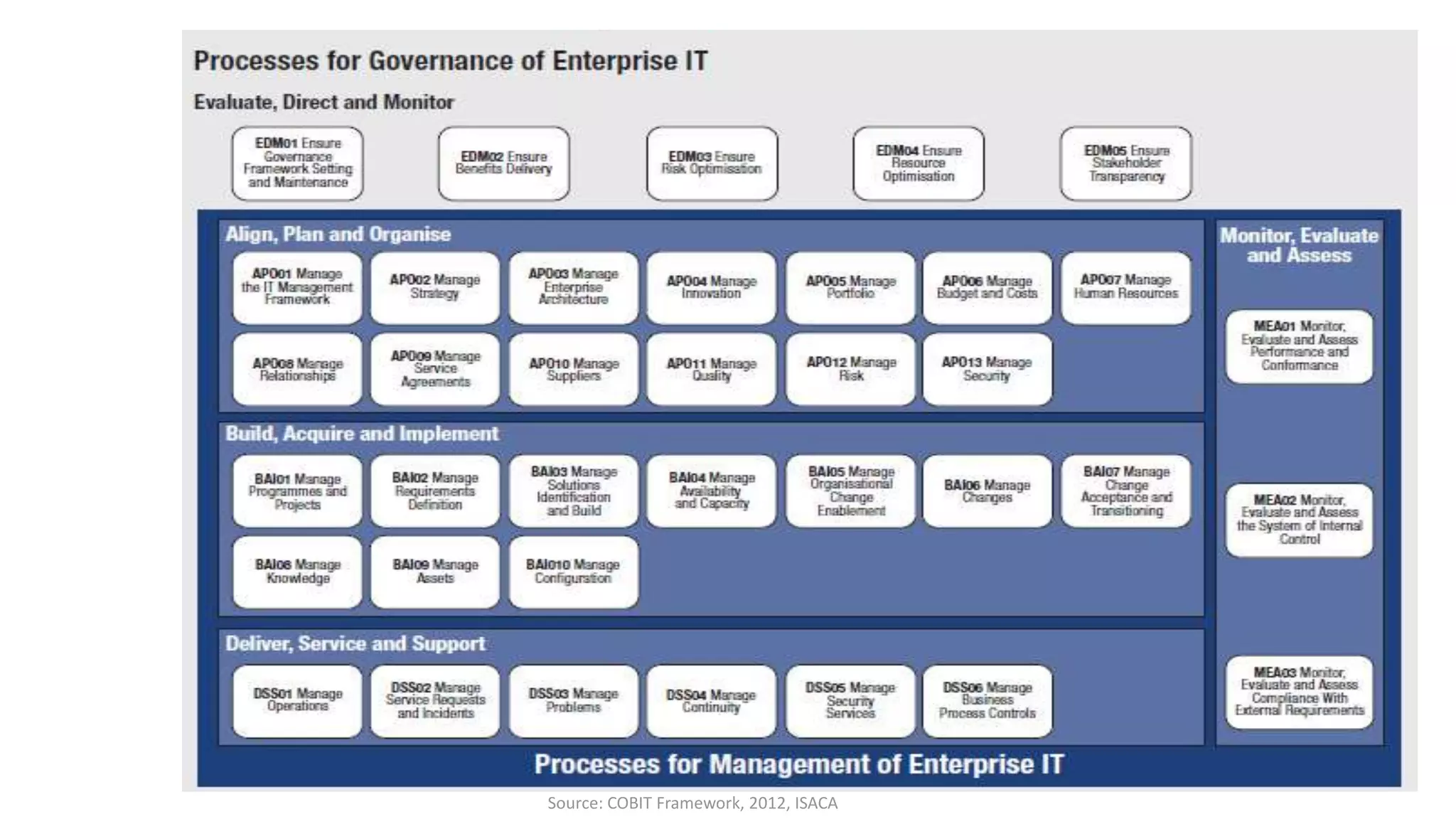
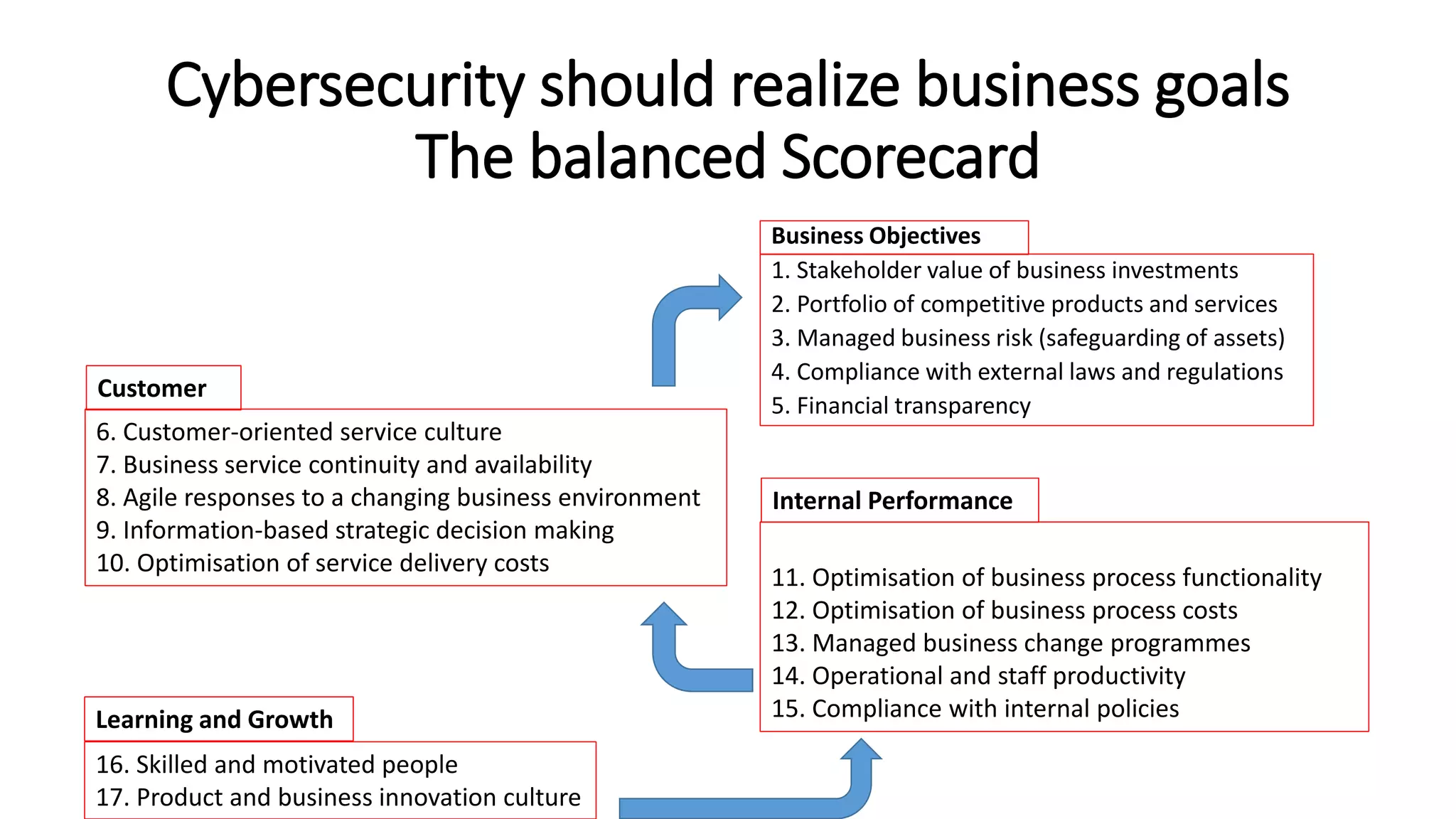
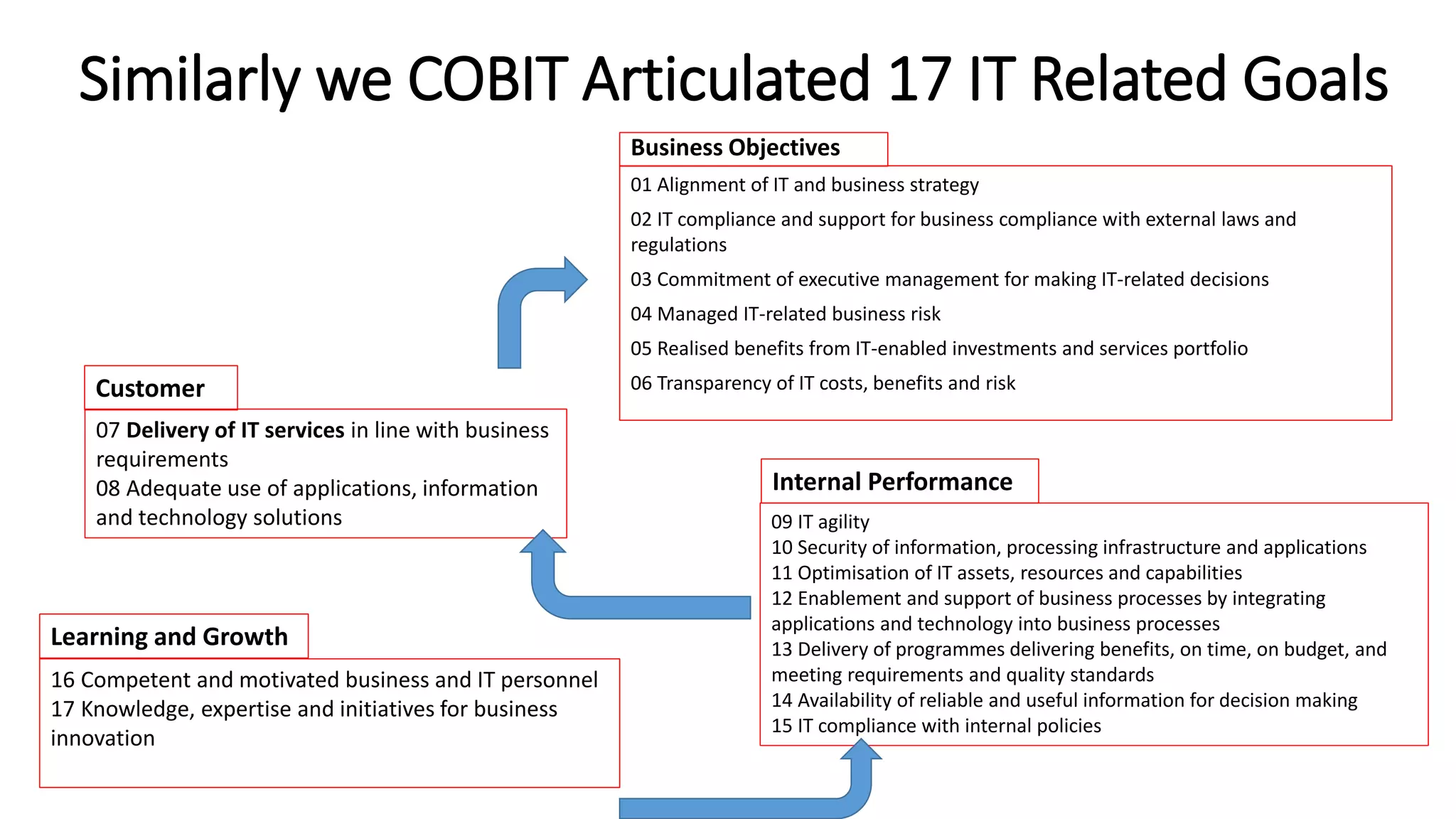
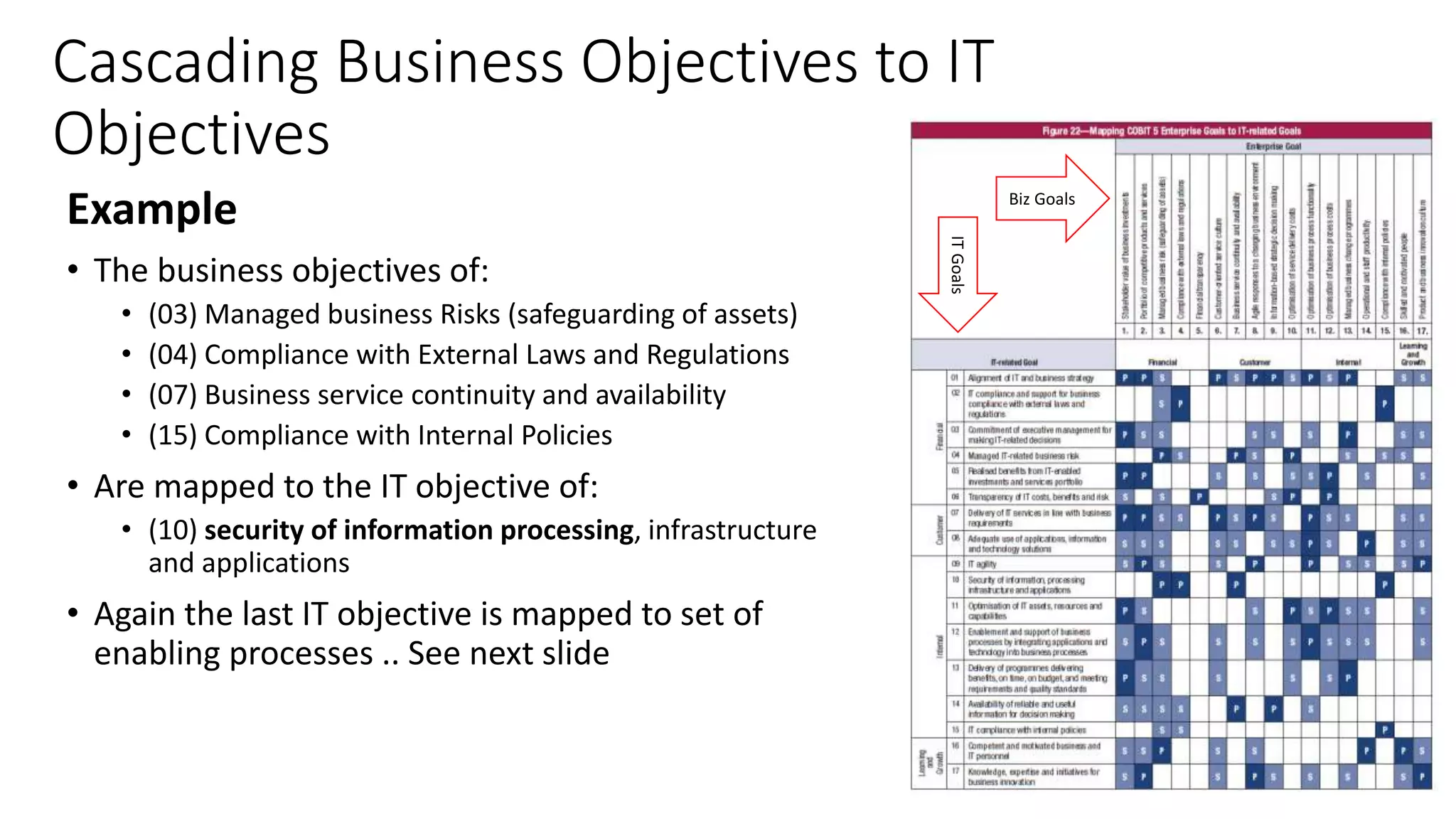
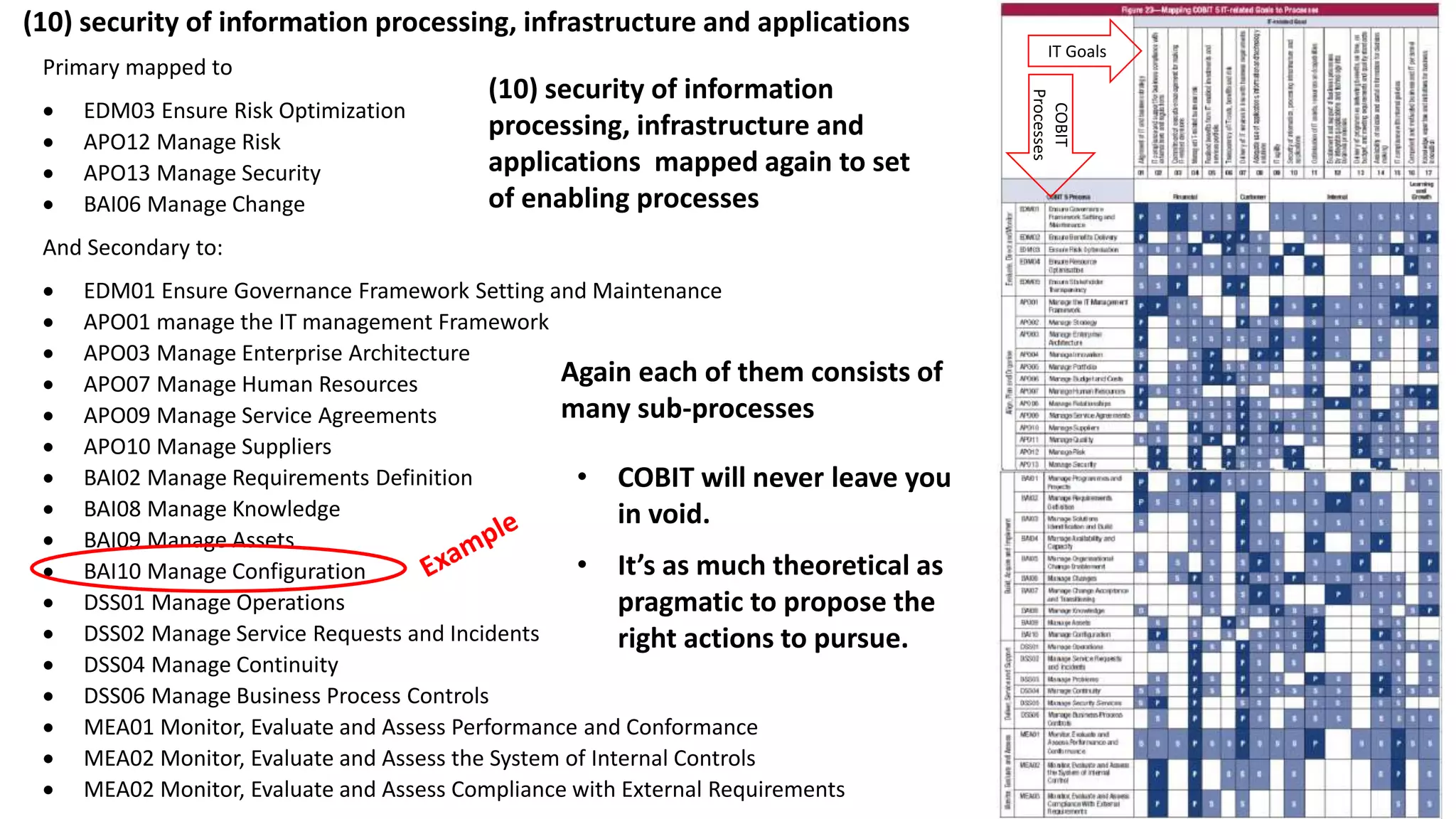
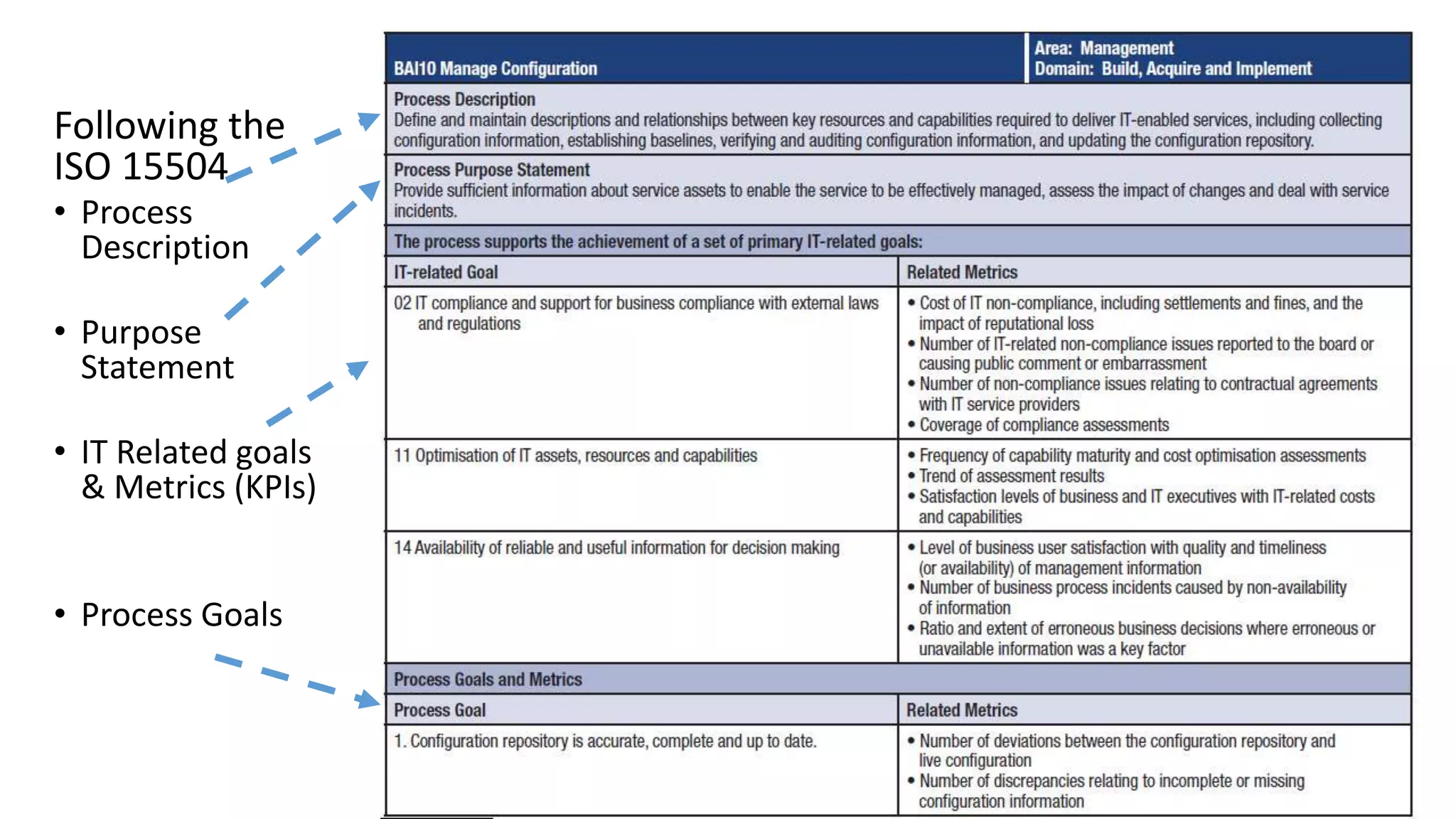
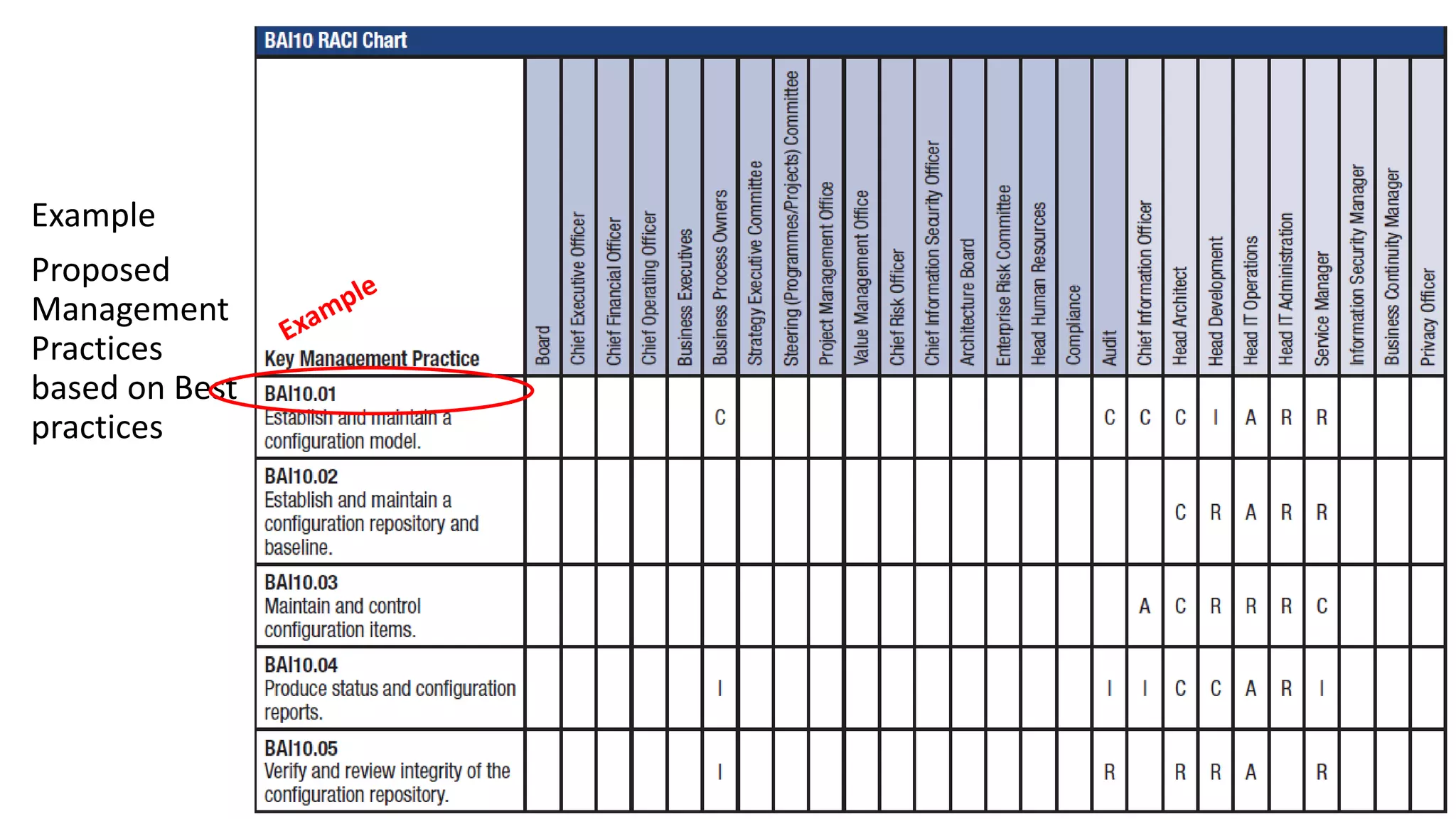
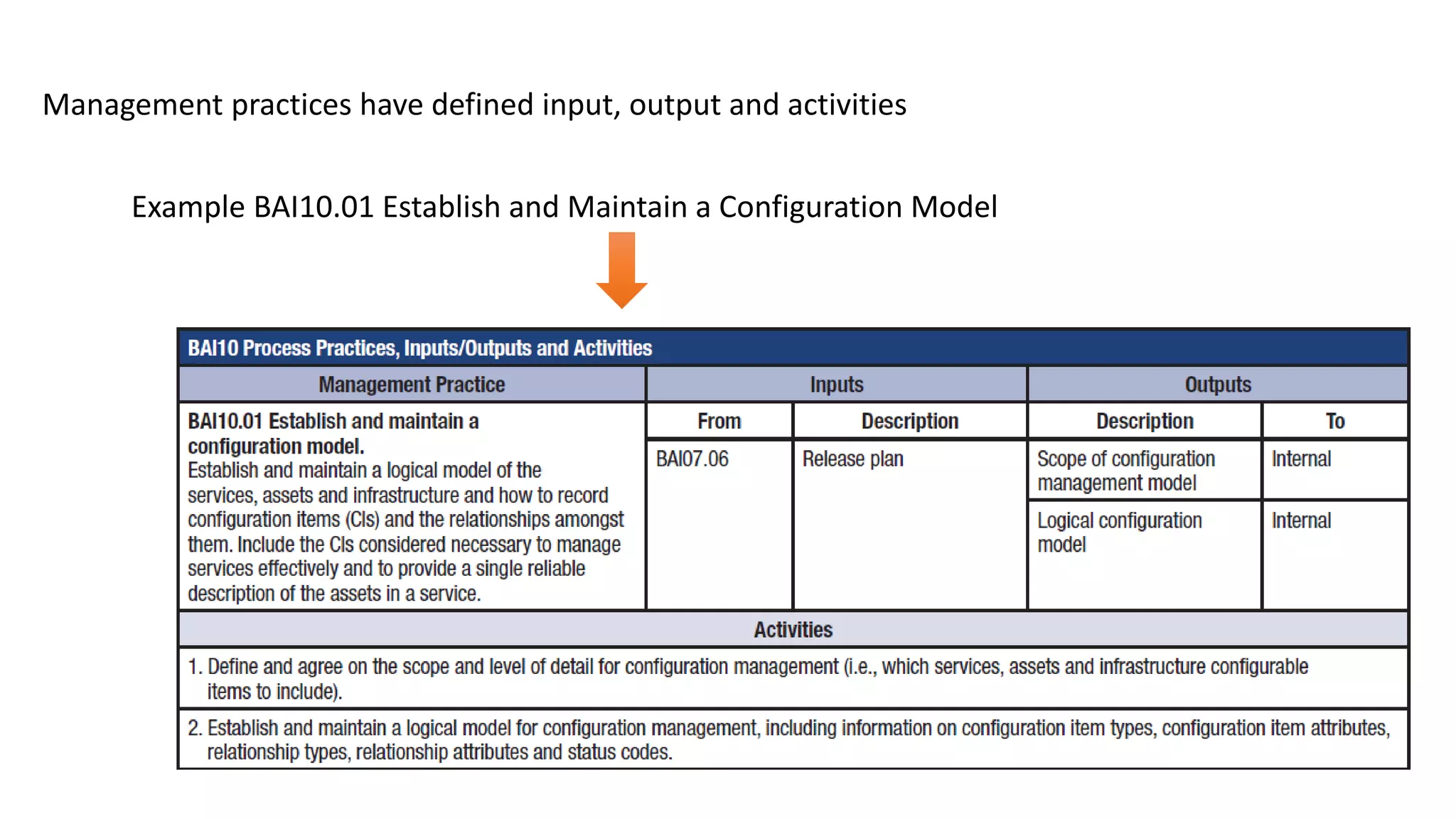
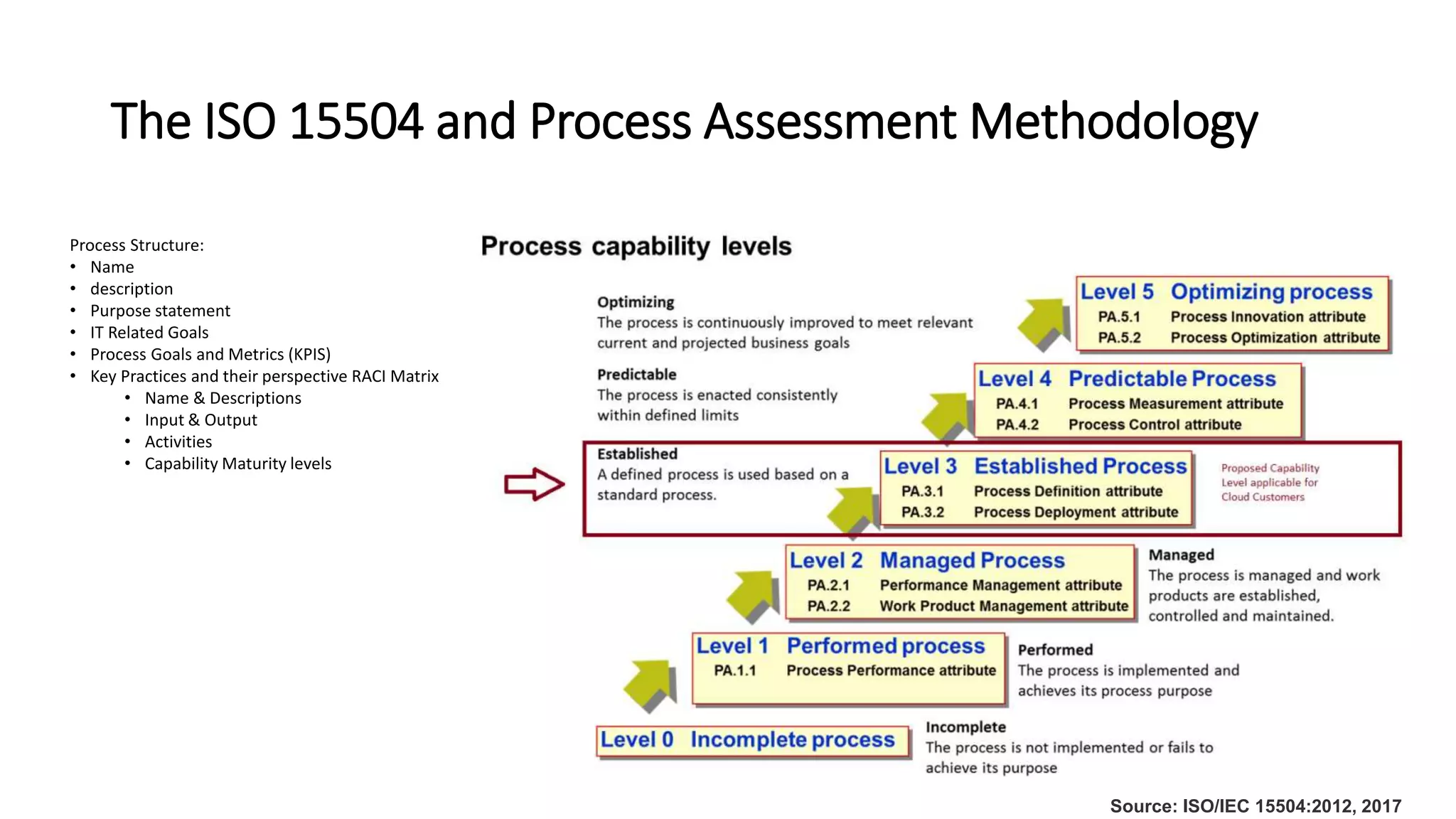
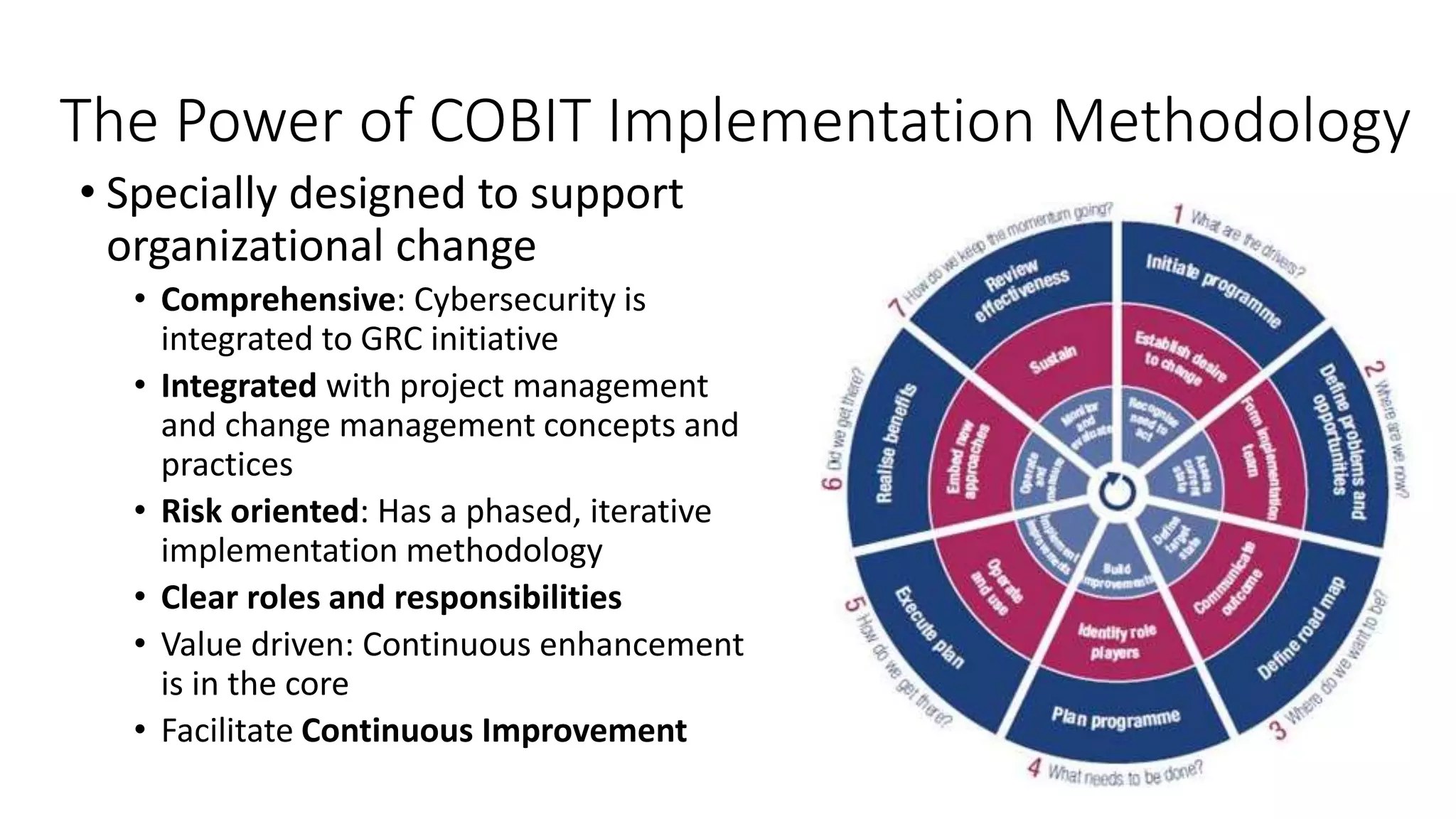
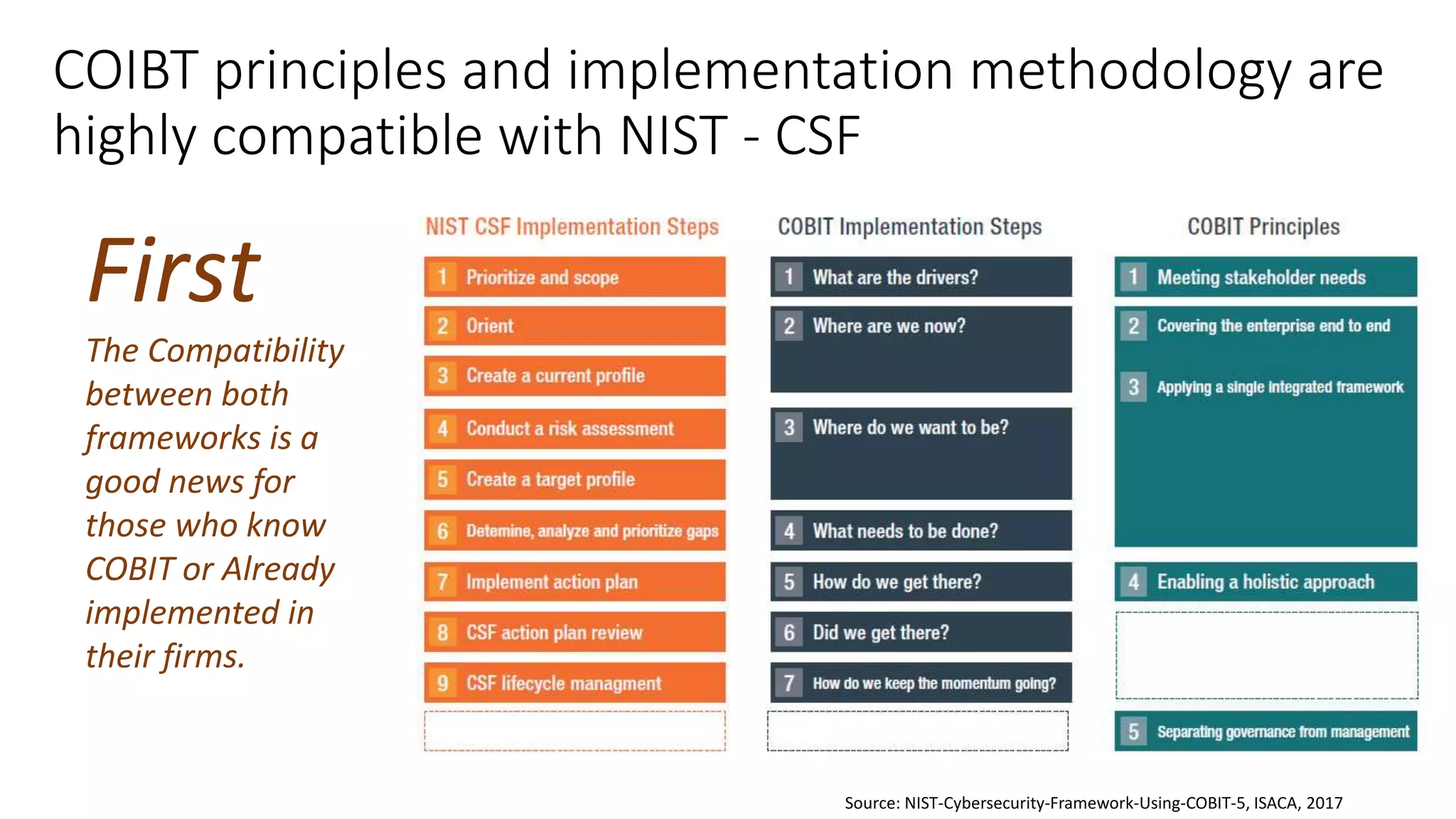
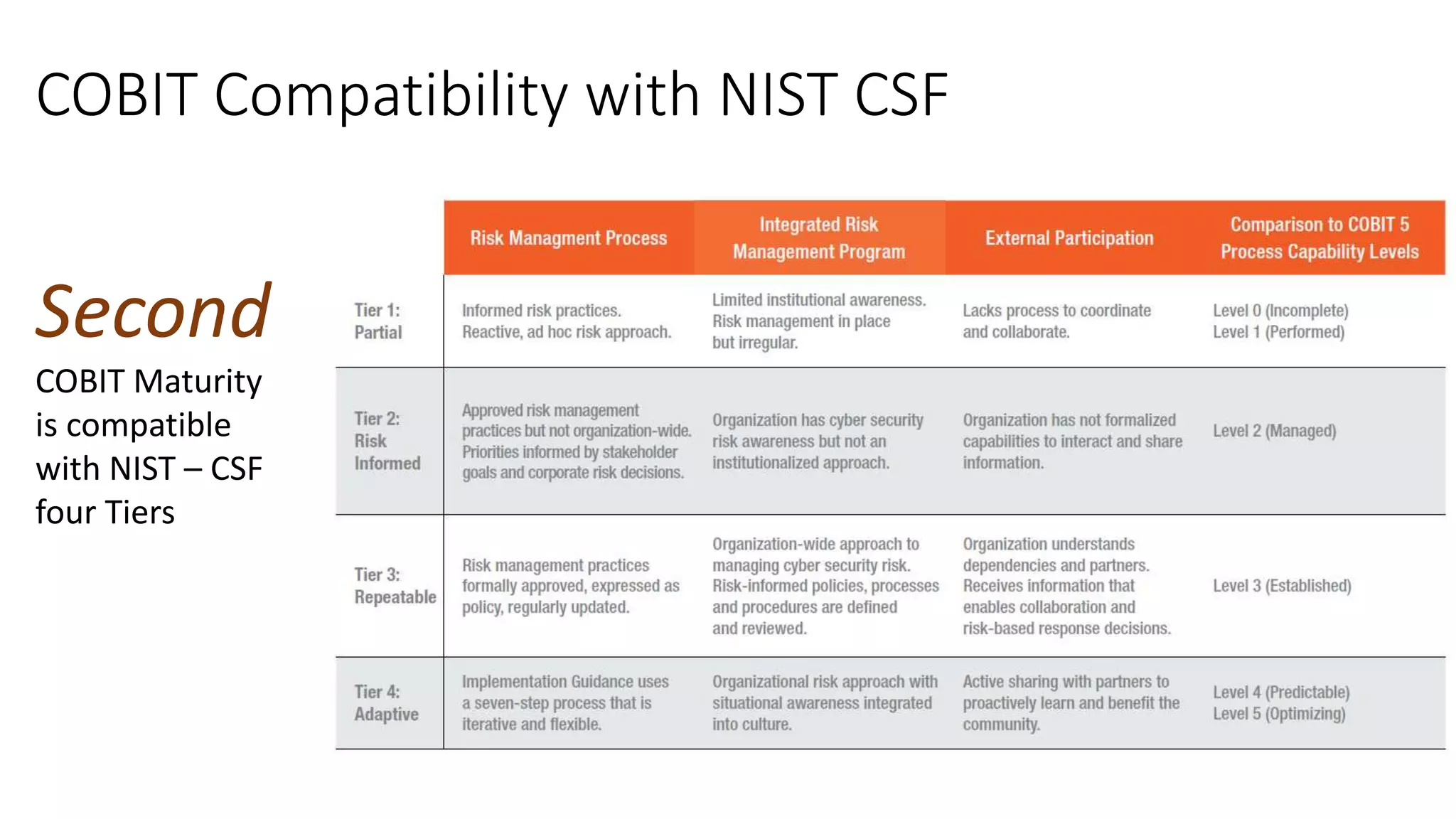
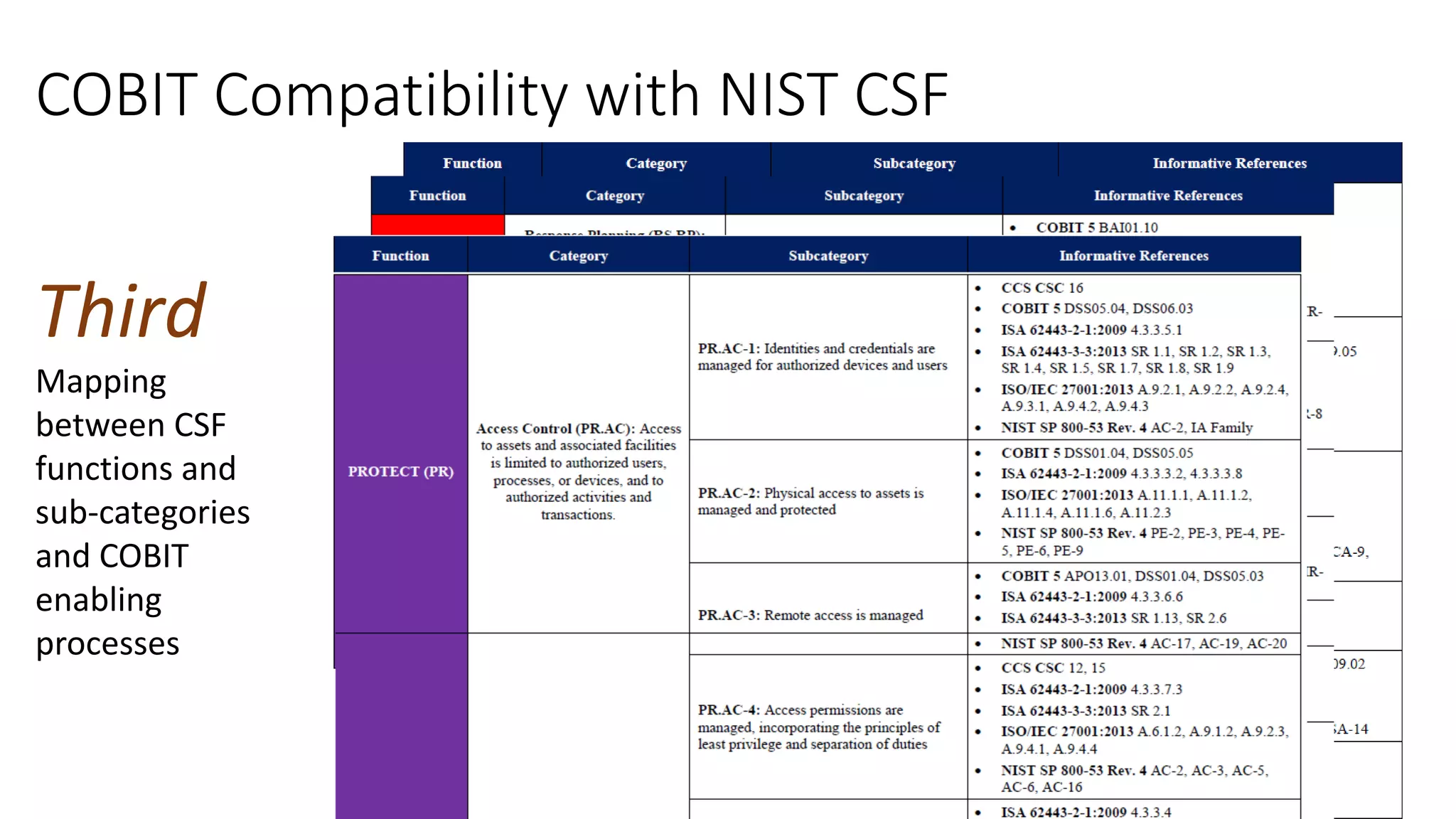
The document discusses the COBIT framework's approach to managing cybersecurity using the NIST Cybersecurity Framework, emphasizing the importance of aligning business and IT strategies. It outlines COBIT's practices for governance and performance management, as well as its compatibility with NIST CSF to optimize cybersecurity efforts. The paper stresses that effective cybersecurity governance requires a comprehensive understanding of risk management and alignment with business goals.