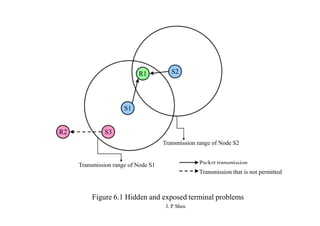
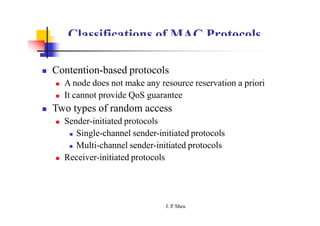
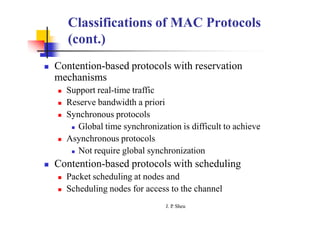
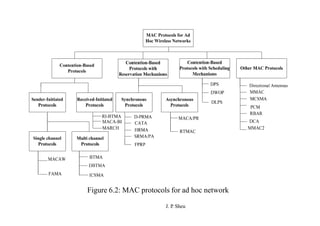
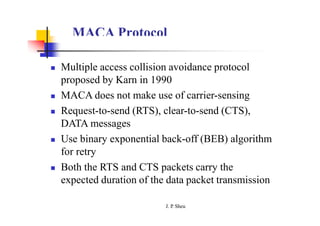
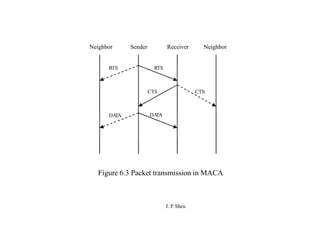
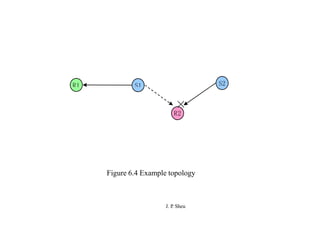
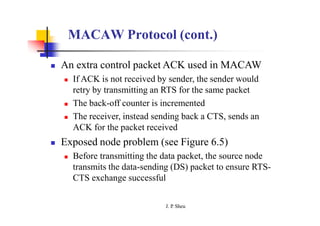
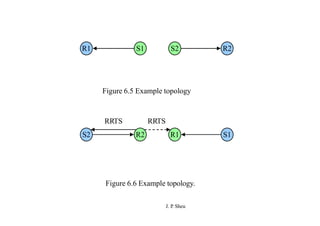
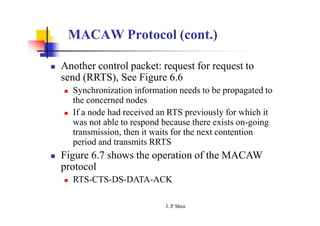
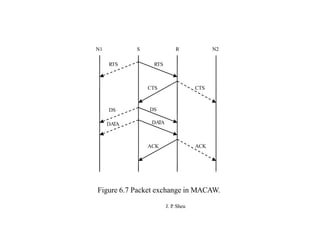
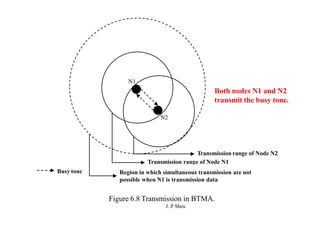
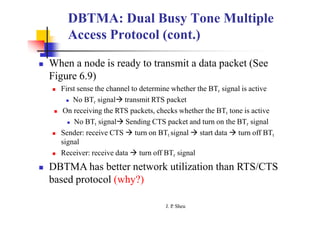
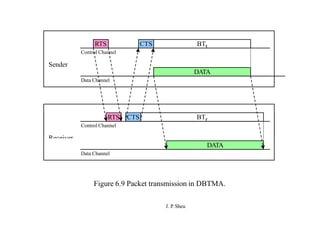
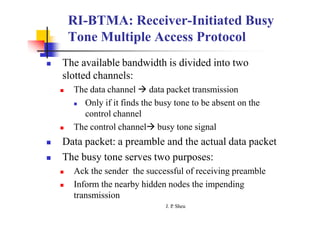
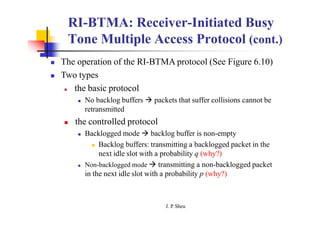
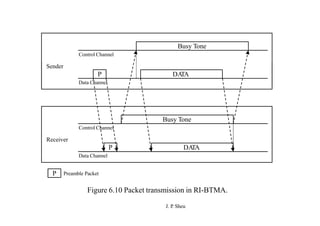
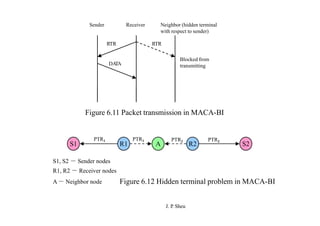
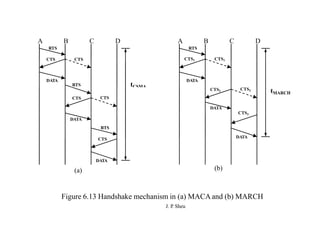
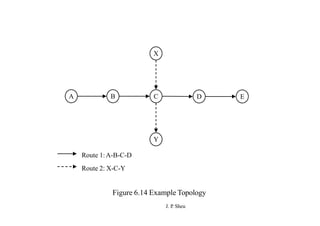
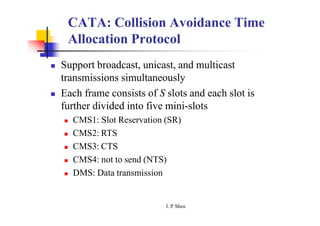
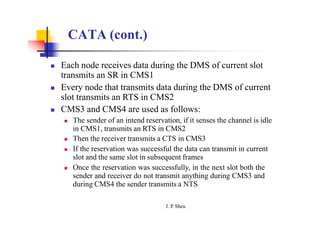
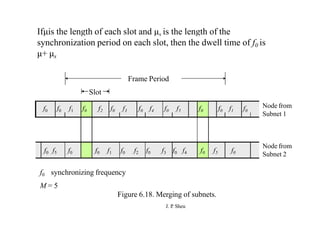
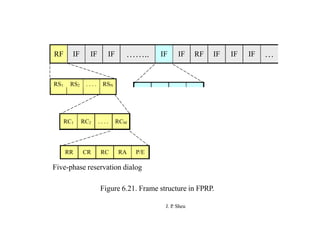
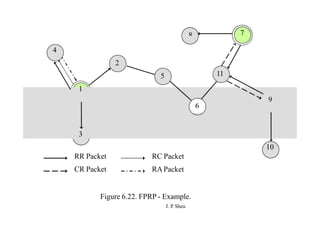
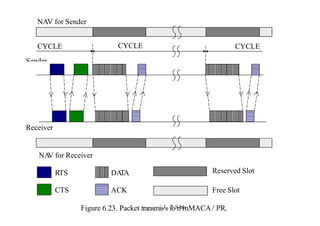
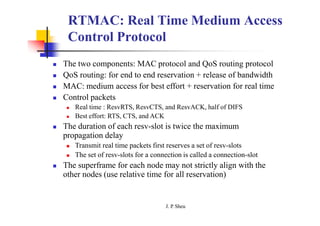
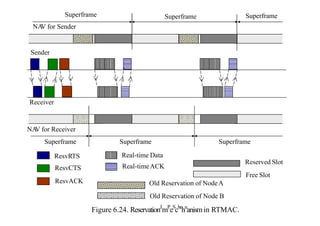
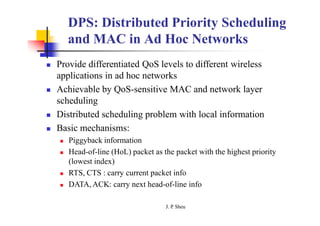
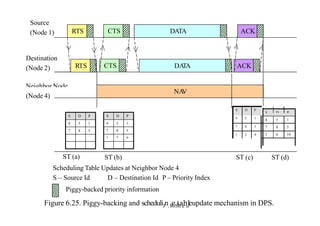
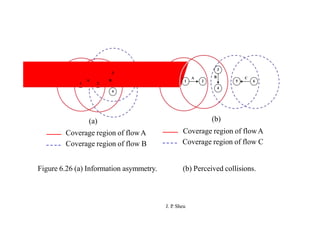
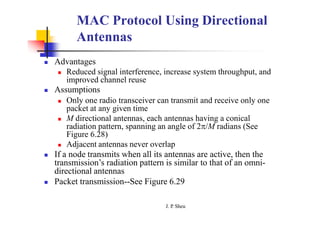
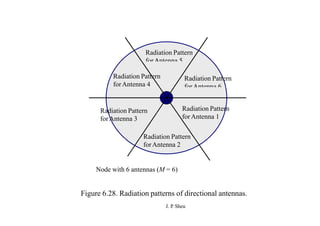
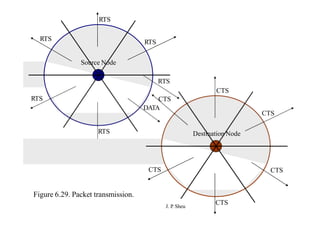
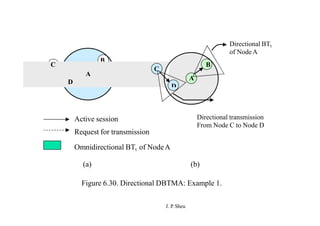
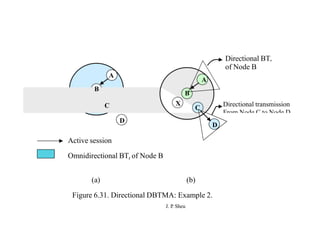
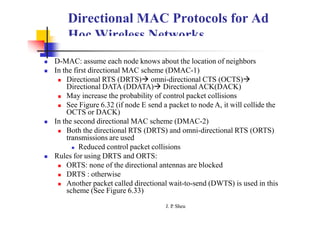
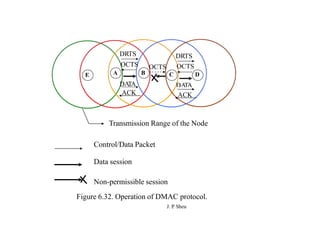
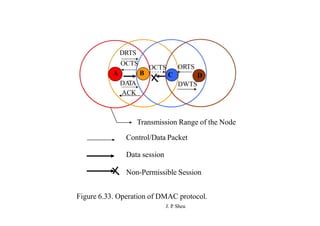
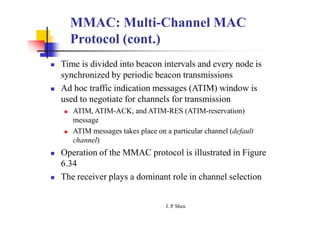
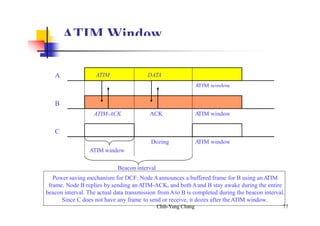
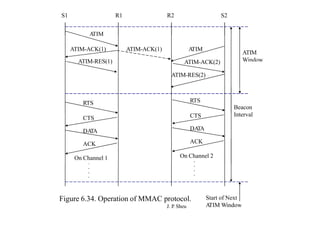
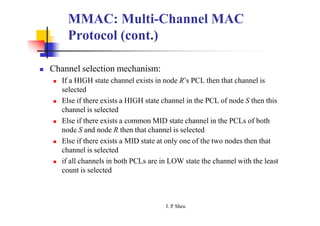
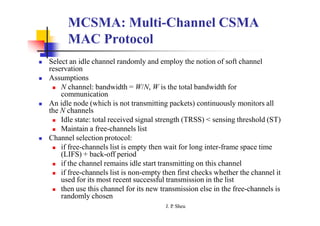
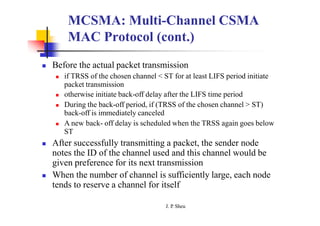
This document summarizes and outlines a chapter about MAC protocols for ad hoc wireless networks. It discusses several key issues in designing MAC protocols, including bandwidth efficiency, quality of service support, synchronization, and mobility. It then describes various classifications of MAC protocols, including contention-based protocols, contention-based protocols with reservation mechanisms, and contention-based protocols with scheduling mechanisms. Finally, it provides details on specific MAC protocol designs, including MACA, MACAW, FAMA, BTMA, DBTMA, RI-BTMA, MACA-BI, and MARCH.