Embed presentation



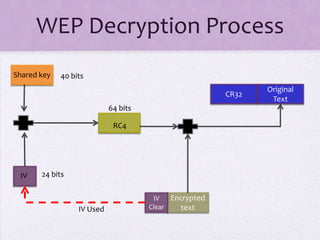


Wireless Security Q&A discusses WEP encryption and the role of initialization vectors (IVs) in the encryption and decryption process. It explains that IVs are used to prevent repetition in encrypted text and that capturing IV packets is necessary for cracking WEP keys. It also provides a high-level overview of the differences between WPA and WPA2 wireless security protocols.




