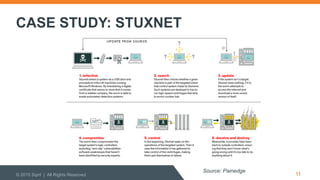
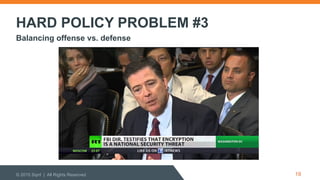
The document discusses cybersecurity threats and policymaking. It summarizes Ely Kahn's background in cybersecurity and defines cybersecurity. It then outlines the types of cyber threats including advanced persistent threats and targeted attacks. The document discusses the Stuxnet case study. It explains how national cybersecurity policy is made through the National Security Council, Congress, and regulatory agencies. It identifies three hard policy problems around information sharing, cyber espionionage, and balancing offense and defense in cybersecurity.