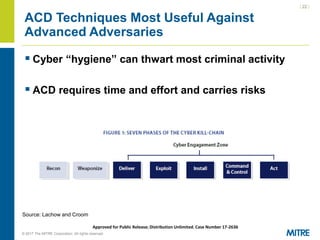
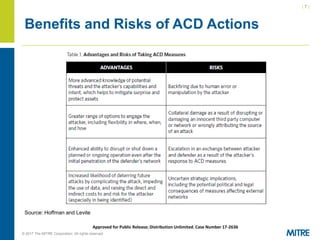
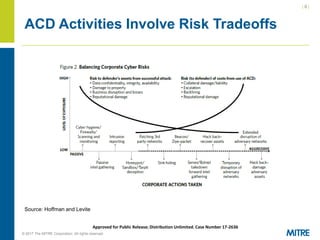
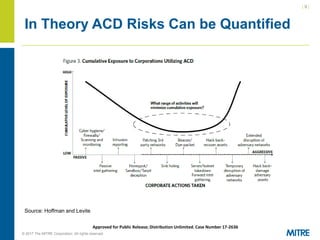
The document discusses the importance and implications of active cyber defense (ACD) for the private sector, highlighting that governments cannot solely protect it and companies must take proactive measures. It addresses the legal challenges and policy questions surrounding ACD, including the need for clarity and acceptable frameworks to empower companies while managing risks. Recommendations include defining acceptable actions, improving public-private cooperation, and developing international standards.




![| 5 |
© 2017 The MITRE Corporation. All rights reserved. For Internal MITRE Use.
Approved for Public Release; Distribution Unlimited. Case Number 17-2636
What Does “Active Cyber Defense” Mean?
▪ Center for Cyber and Homeland Security
– Active defense is a term that captures a spectrum of proactive
cybersecurity measures that fall between traditional passive defense
and offensive….the term is NOT synonymous with “hacking back.”
(Emphasis added.)
▪ Hoffman and Levite (from Robert Dewar)
– An approach to achieving cybersecurity predicated upon the
deployment of measures to detect, analyze, identify and mitigate
threats…combined with the capability and resources to take proactive
or offensive action against threats…
▪ DARPA
– DARPA’s Active Cyber Defense (ACD) program is designed
to…[provide] cyber defenders a “home field” advantage: the ability to
perform defensive operations that involve direct engagement with
sophisticated adversaries in DoD-controlled cyberspace.](https://image.slidesharecdn.com/pdflachowanu-170713105501/85/Pdf-lachow-anu-5-320.jpg)



![| 12 |
© 2017 The MITRE Corporation. All rights reserved. For Internal MITRE Use.
Approved for Public Release; Distribution Unlimited. Case Number 17-2636
Legal Frameworks: Not Much Help
▪ National Laws vary considerably but most prevent
the bulk of ACD activities
– Example: United States' Computer Fraud and Abuse Act
▪ International Laws
– "Formal international treaties have no apparent direct application
to the [ACD] questions being considered."
▪ Which legal models are most applicable?
▪ This lack of guidance needs to be addressed…
Source: Lachow, CCHS, Rosenzweig](https://image.slidesharecdn.com/pdflachowanu-170713105501/85/Pdf-lachow-anu-12-320.jpg)








![| 21 |
© 2017 The MITRE Corporation. All rights reserved. For Internal MITRE Use.
Approved for Public Release; Distribution Unlimited. Case Number 17-2636
UK’s Government ACD Program
▪ Goal: “tackle, in [an] automated way, a significant
proportion of the cyber attacks that hit the UK.”
▪ Led by National Cyber Security Centre
▪ Program elements
– Strengthen infrastructure protocols
– Secure email
– Take down criminal websites
– Filter DNS
– Strengthen identity authentication
Source: National Cyber Security Centre](https://image.slidesharecdn.com/pdflachowanu-170713105501/85/Pdf-lachow-anu-21-320.jpg)