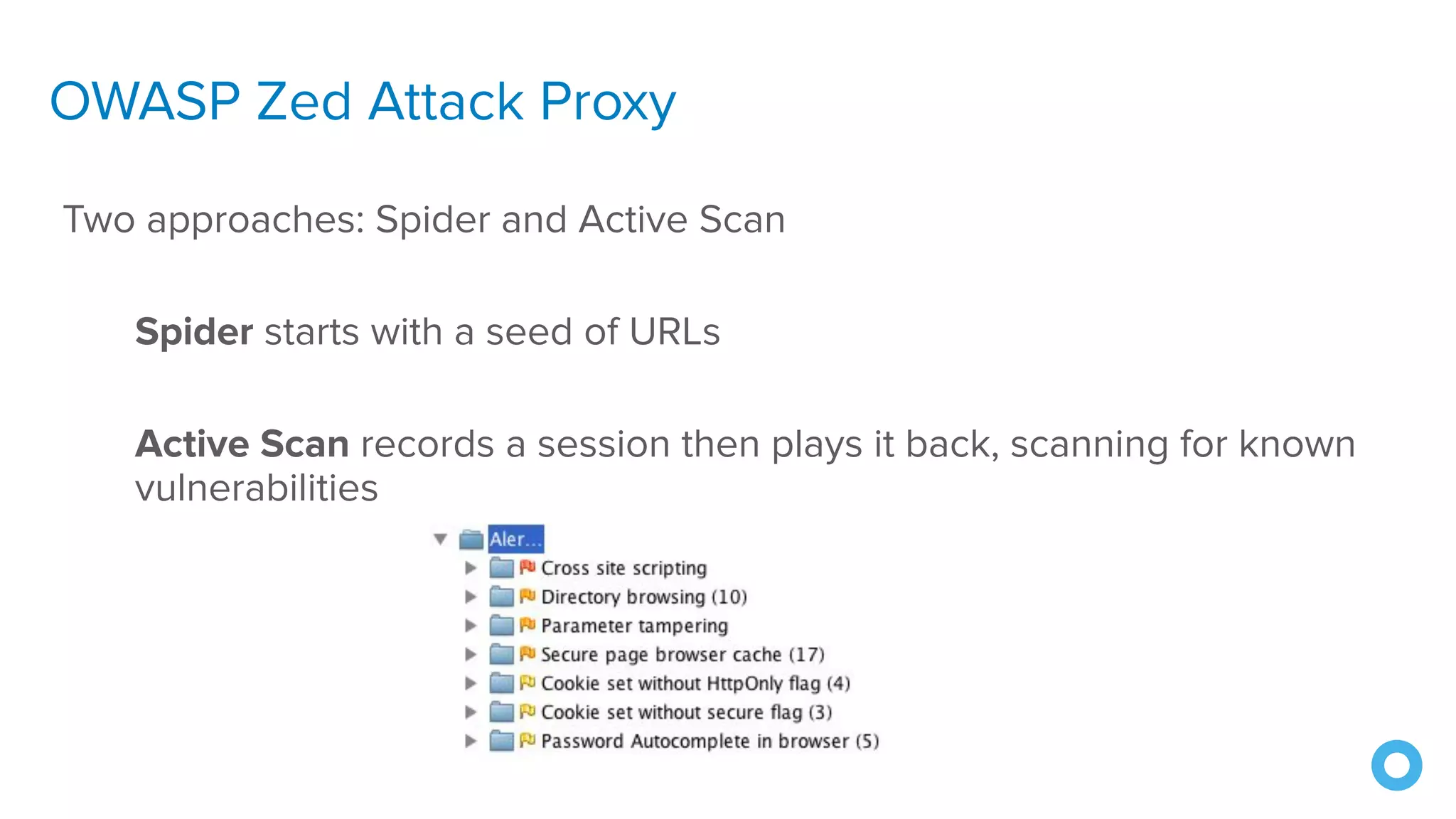
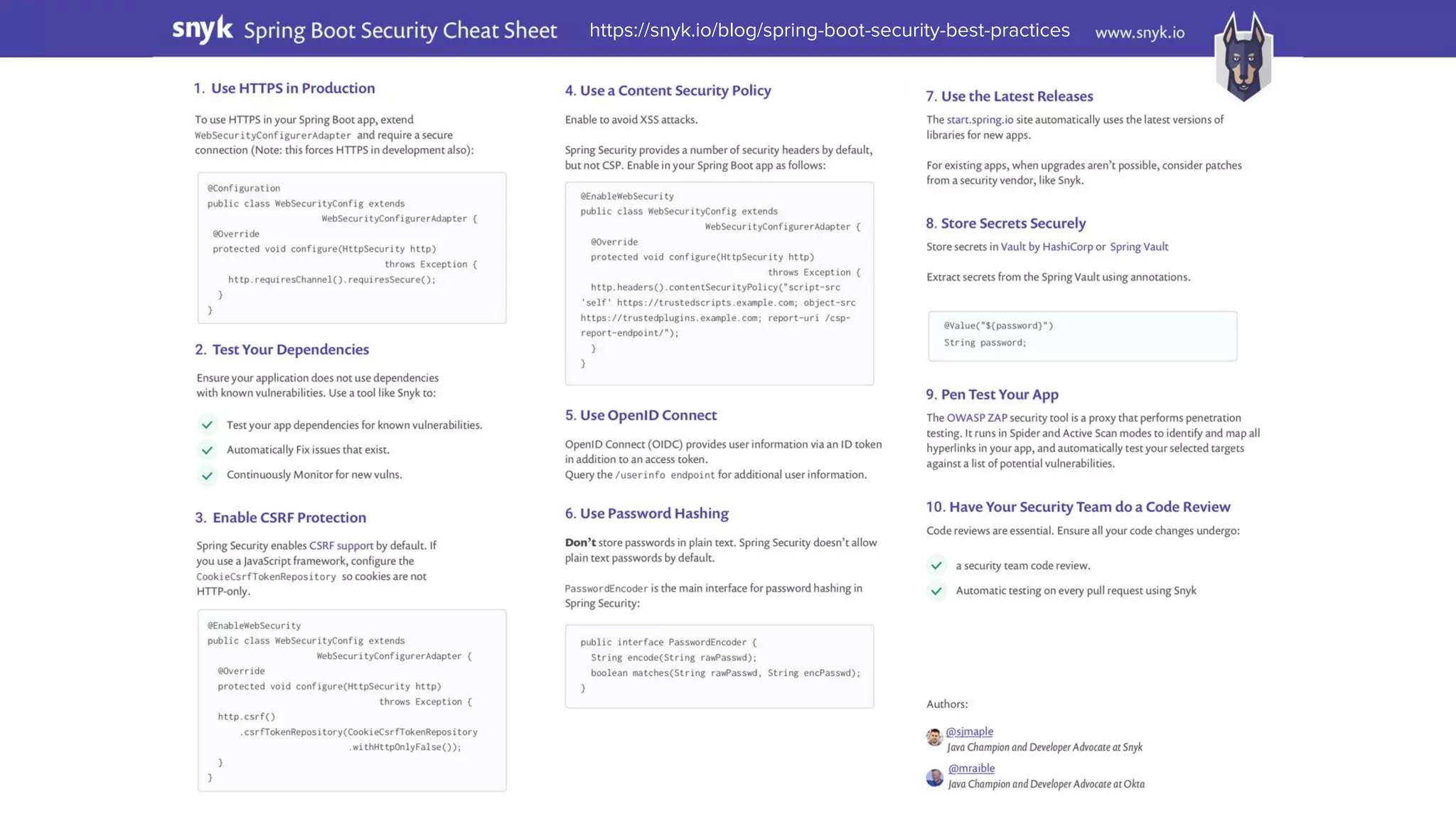
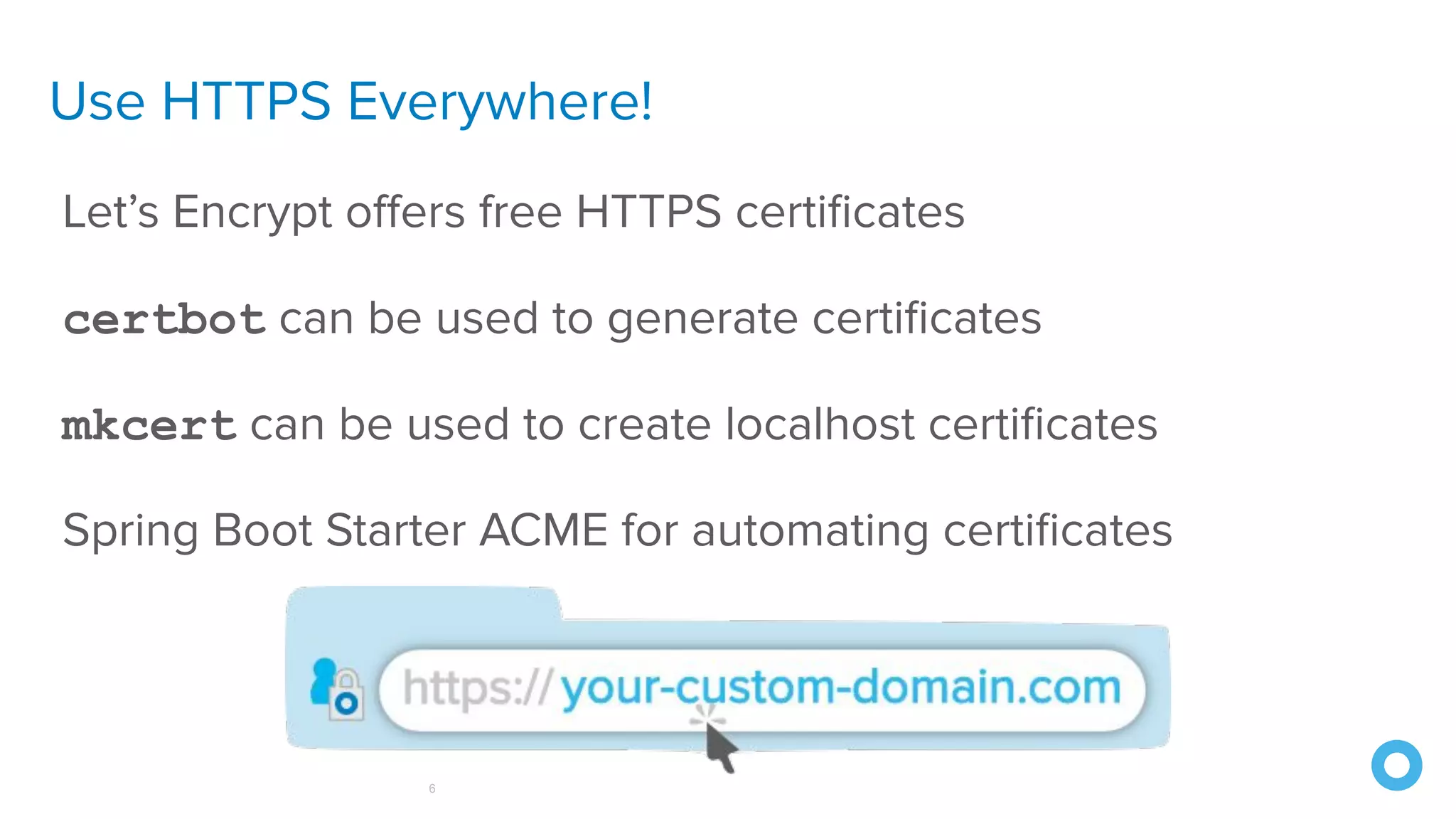
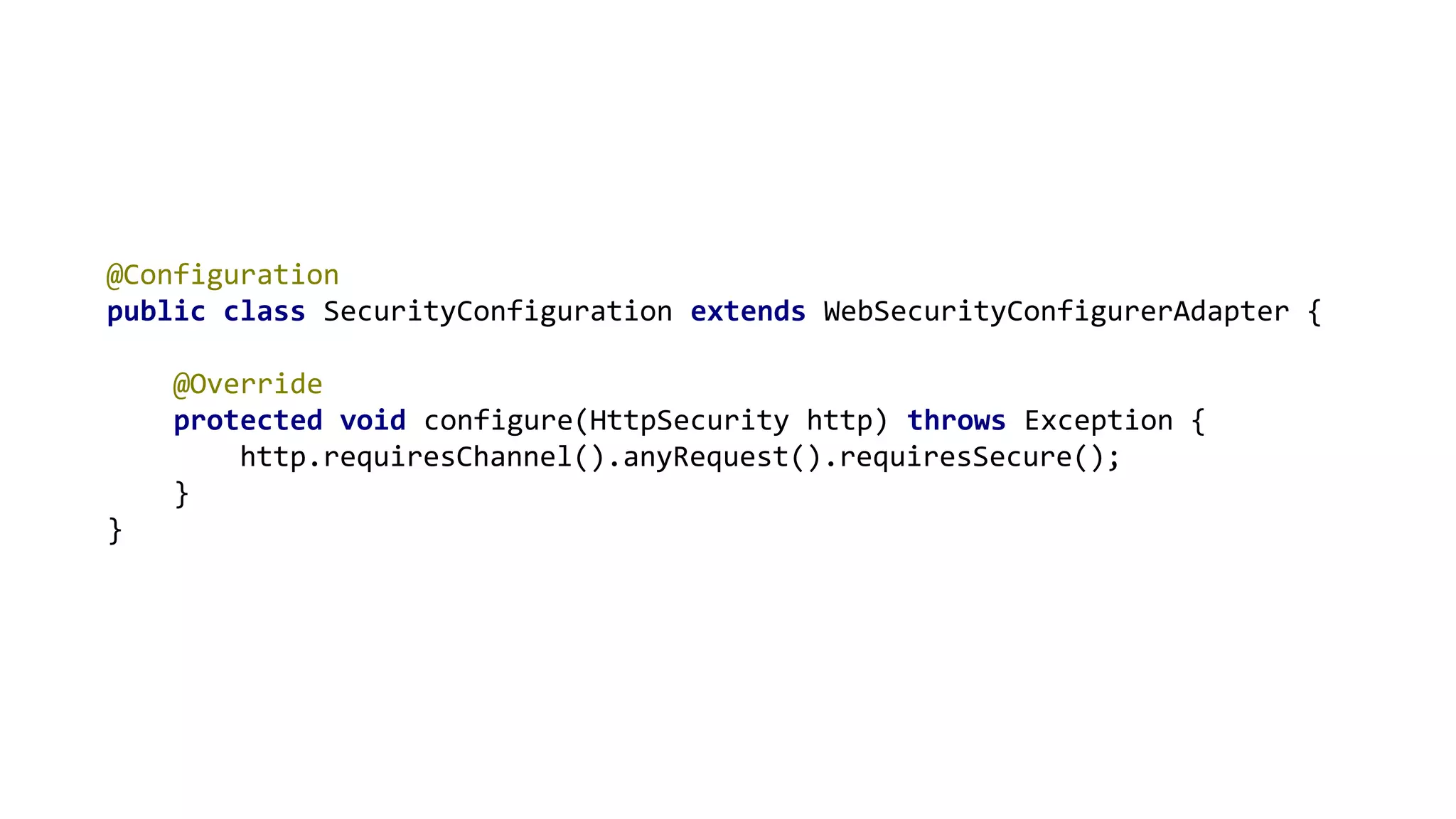
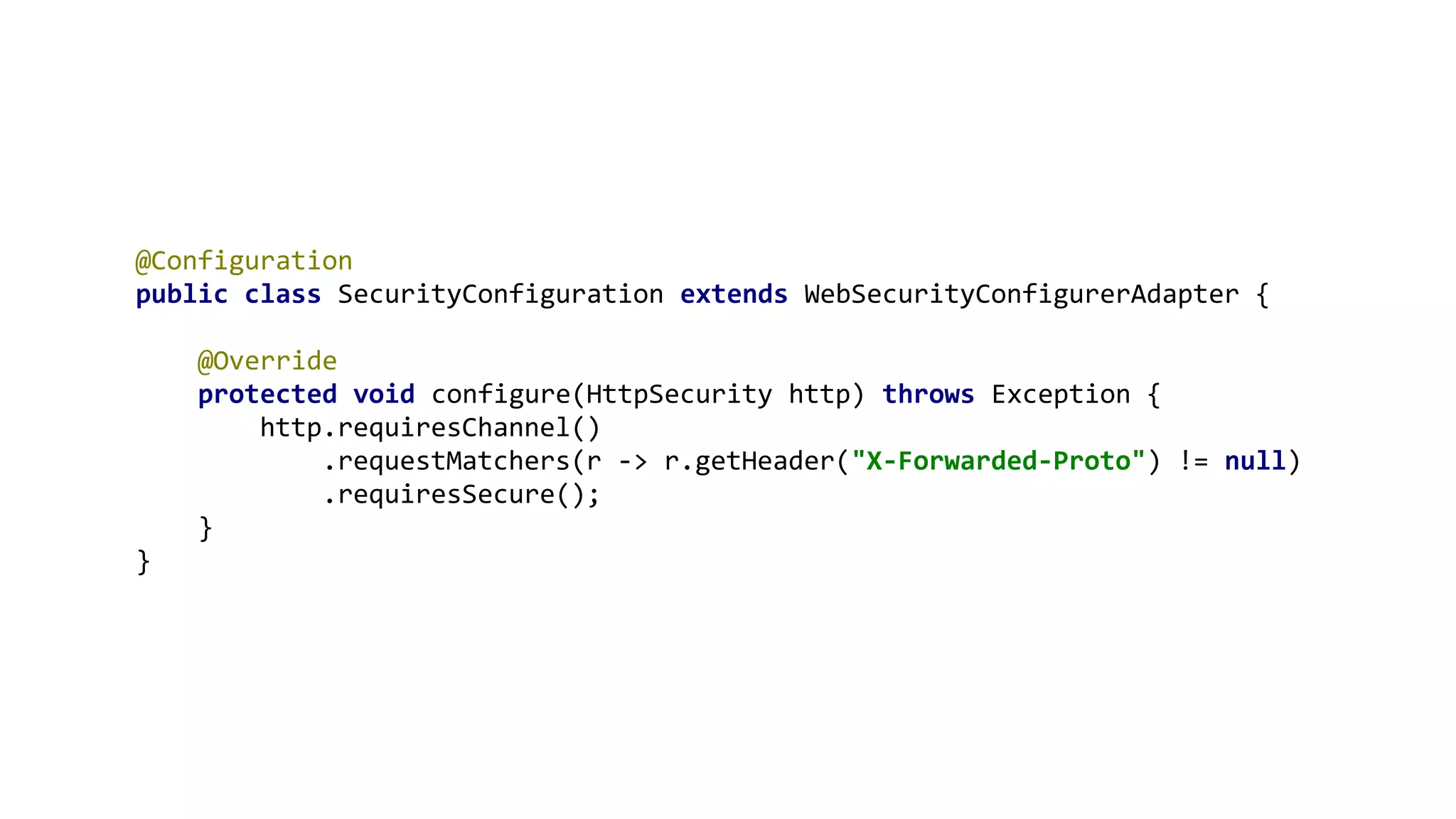
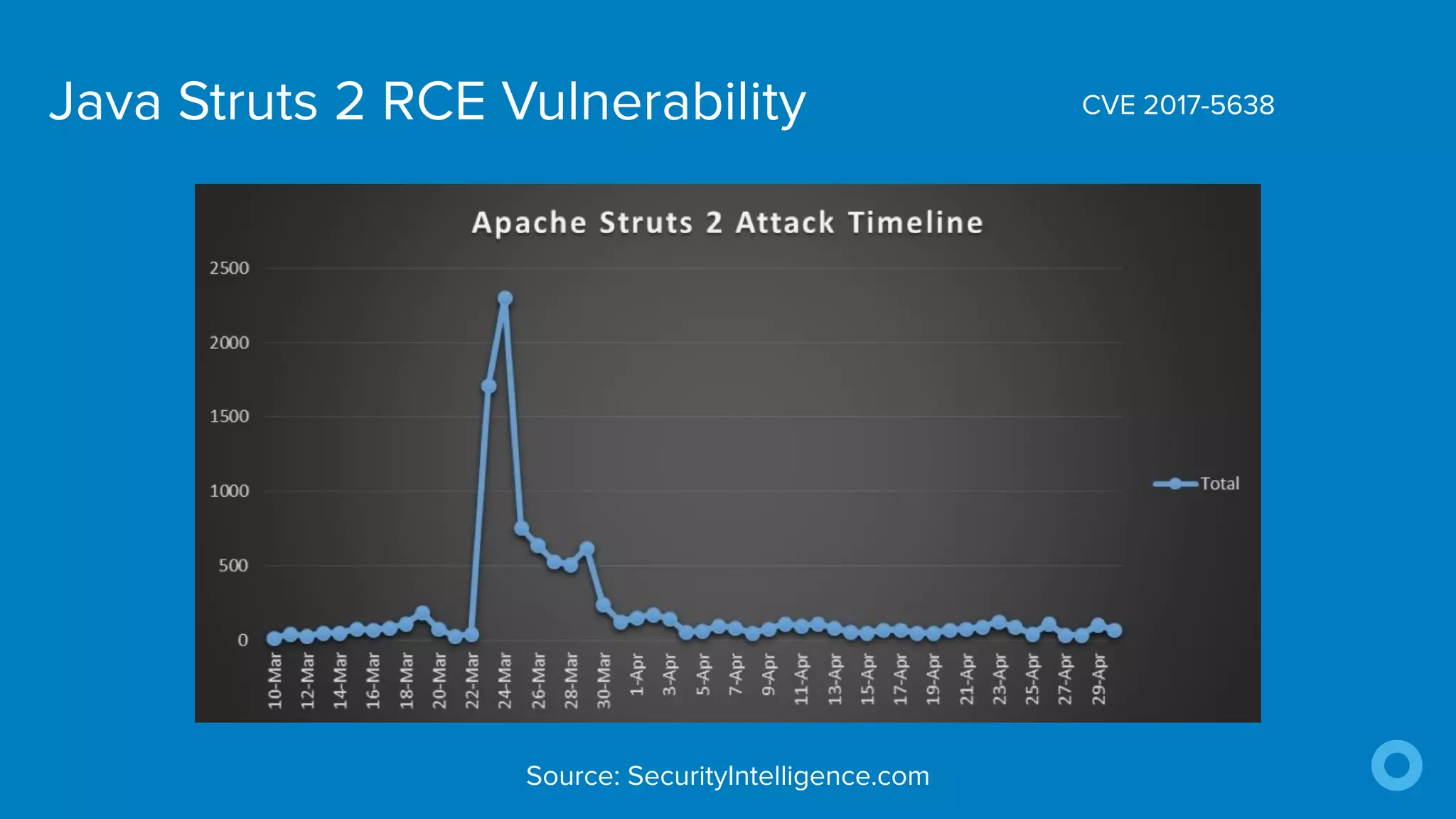
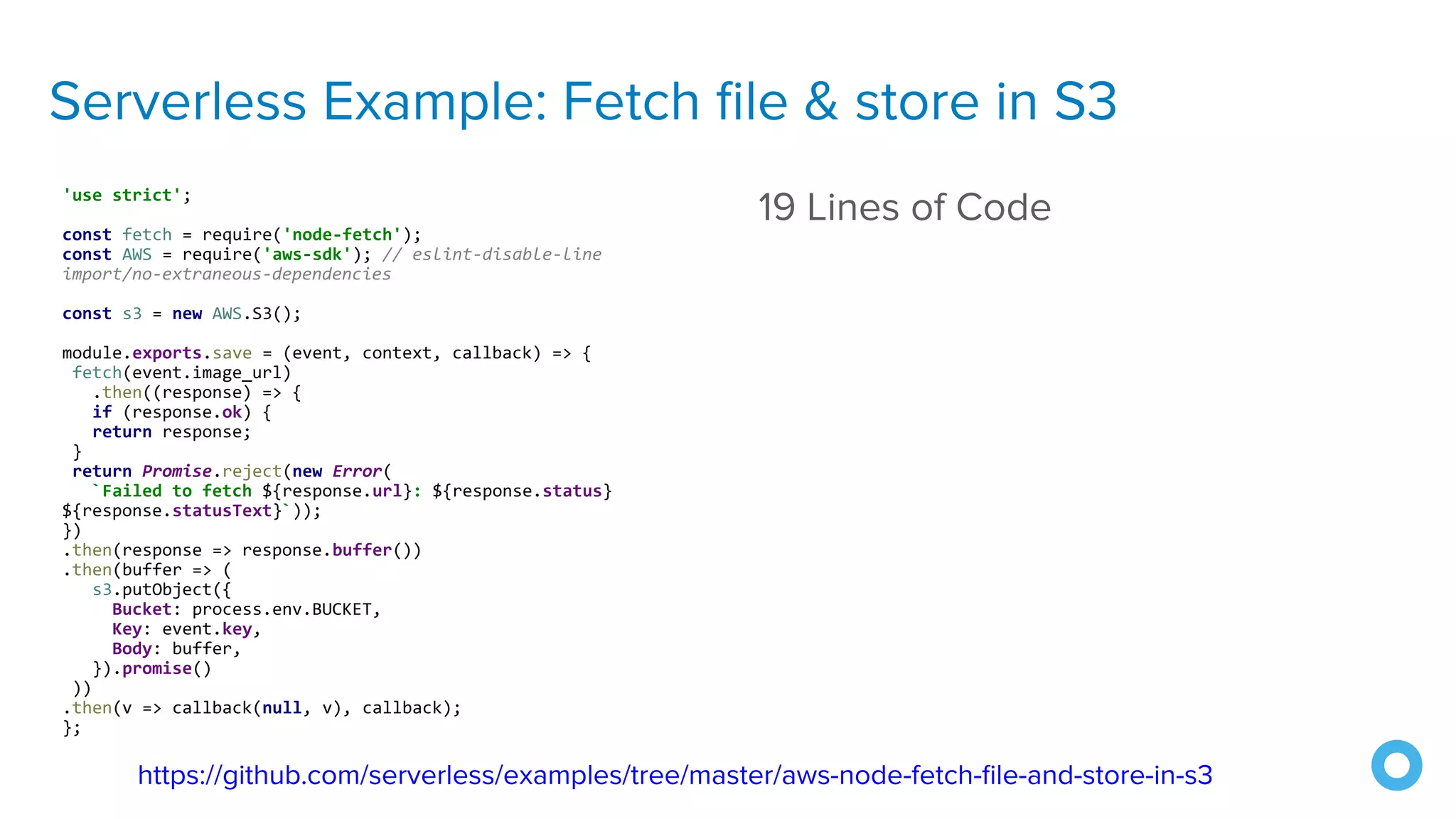
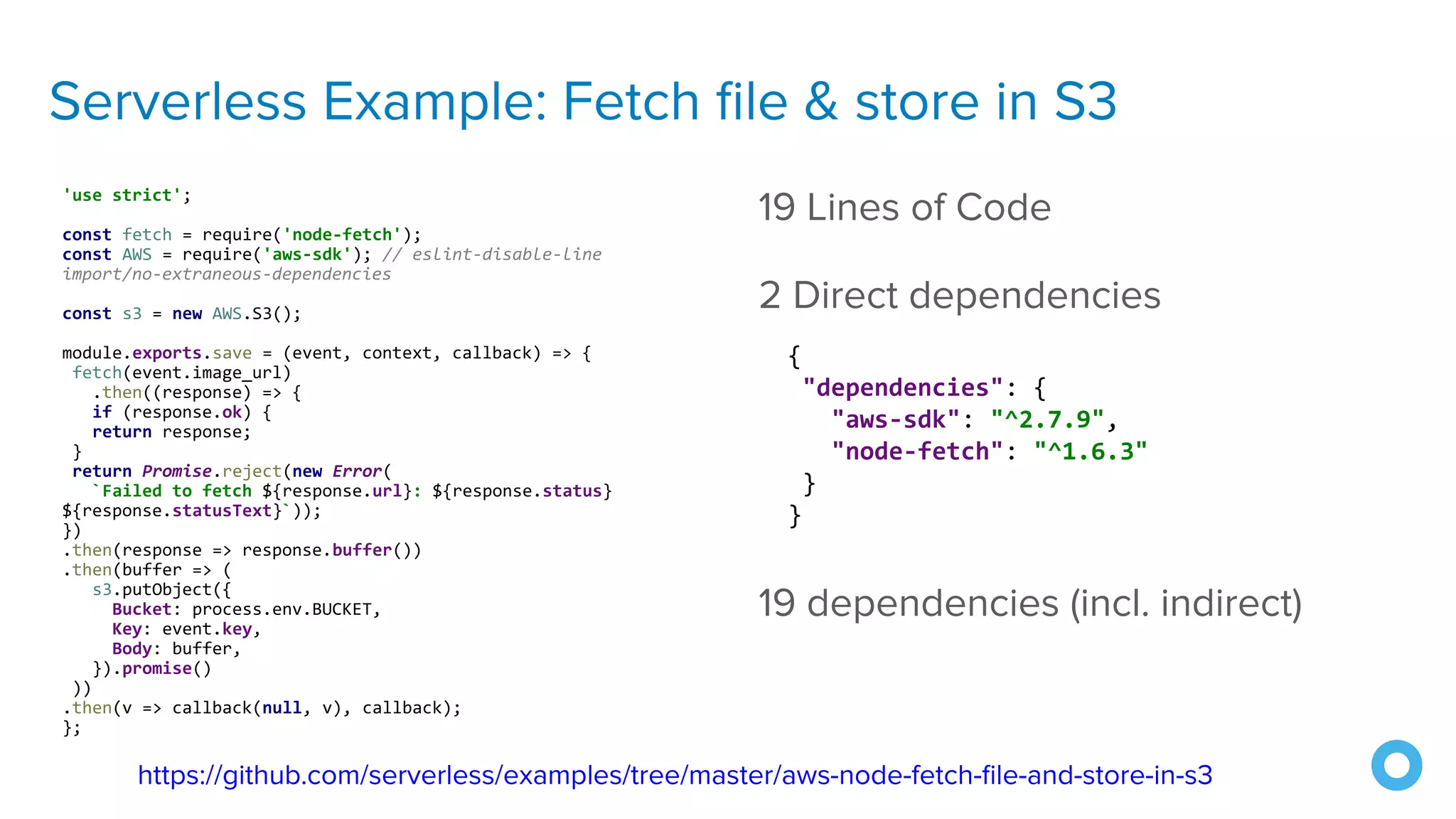
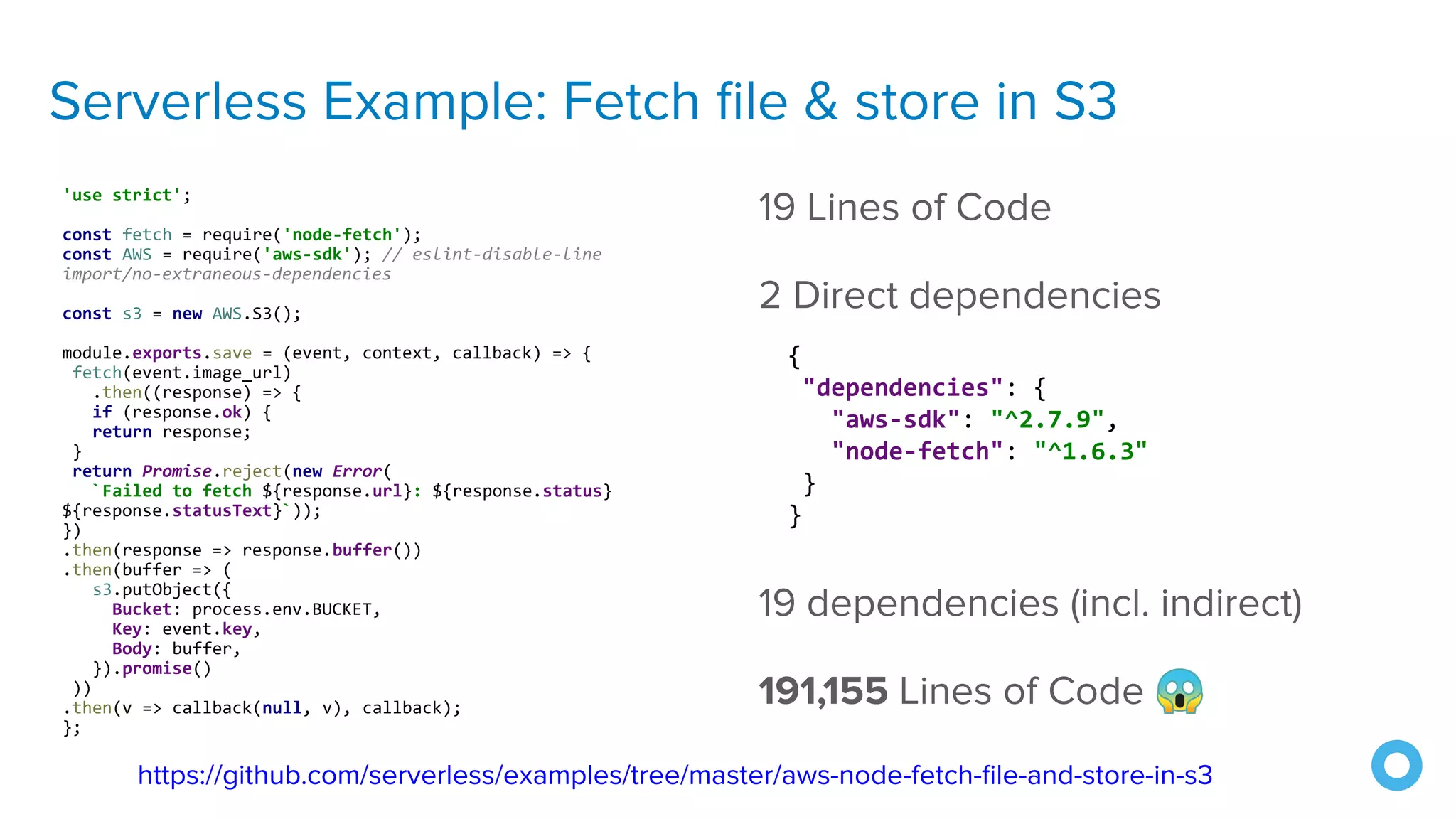
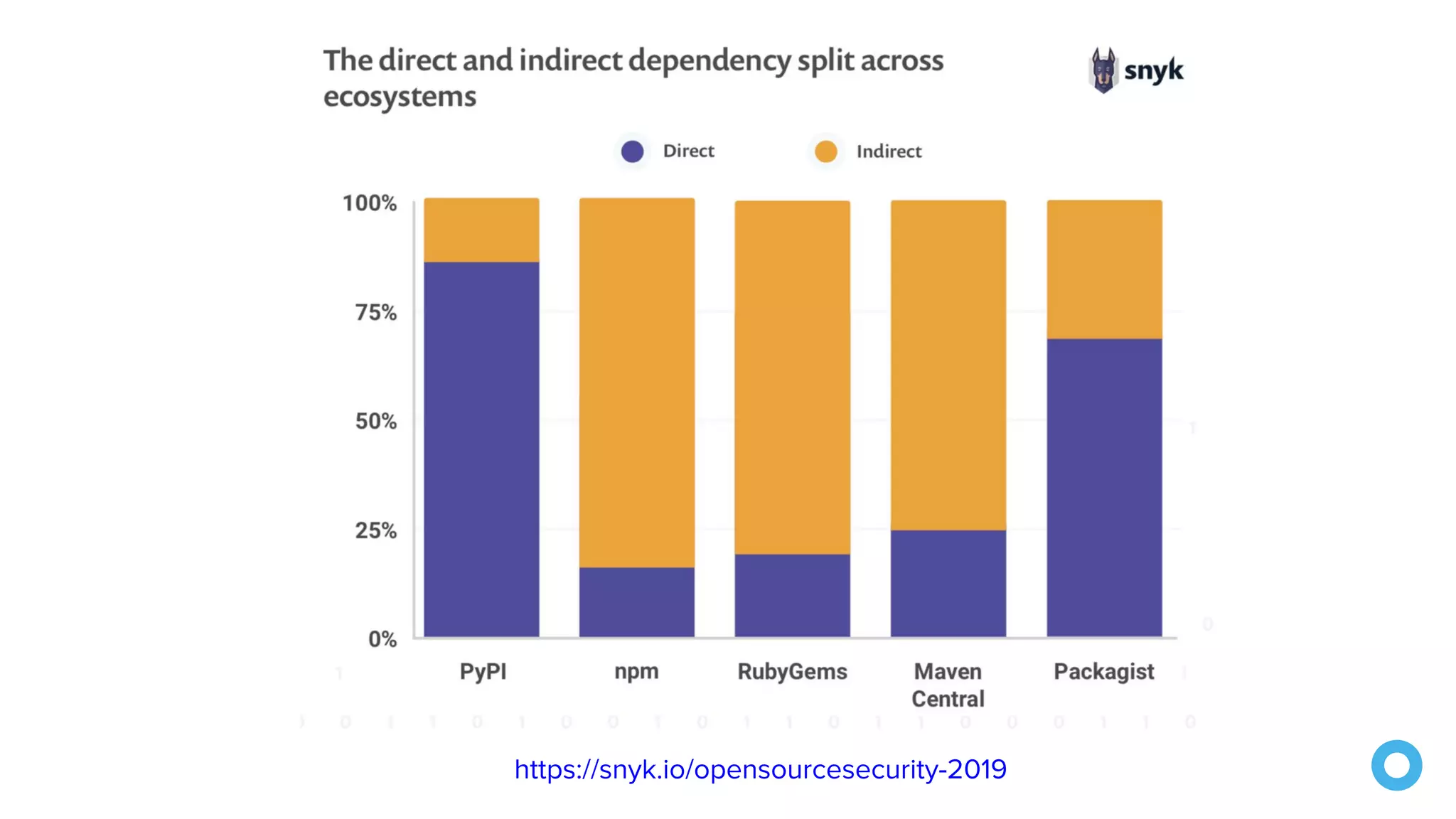
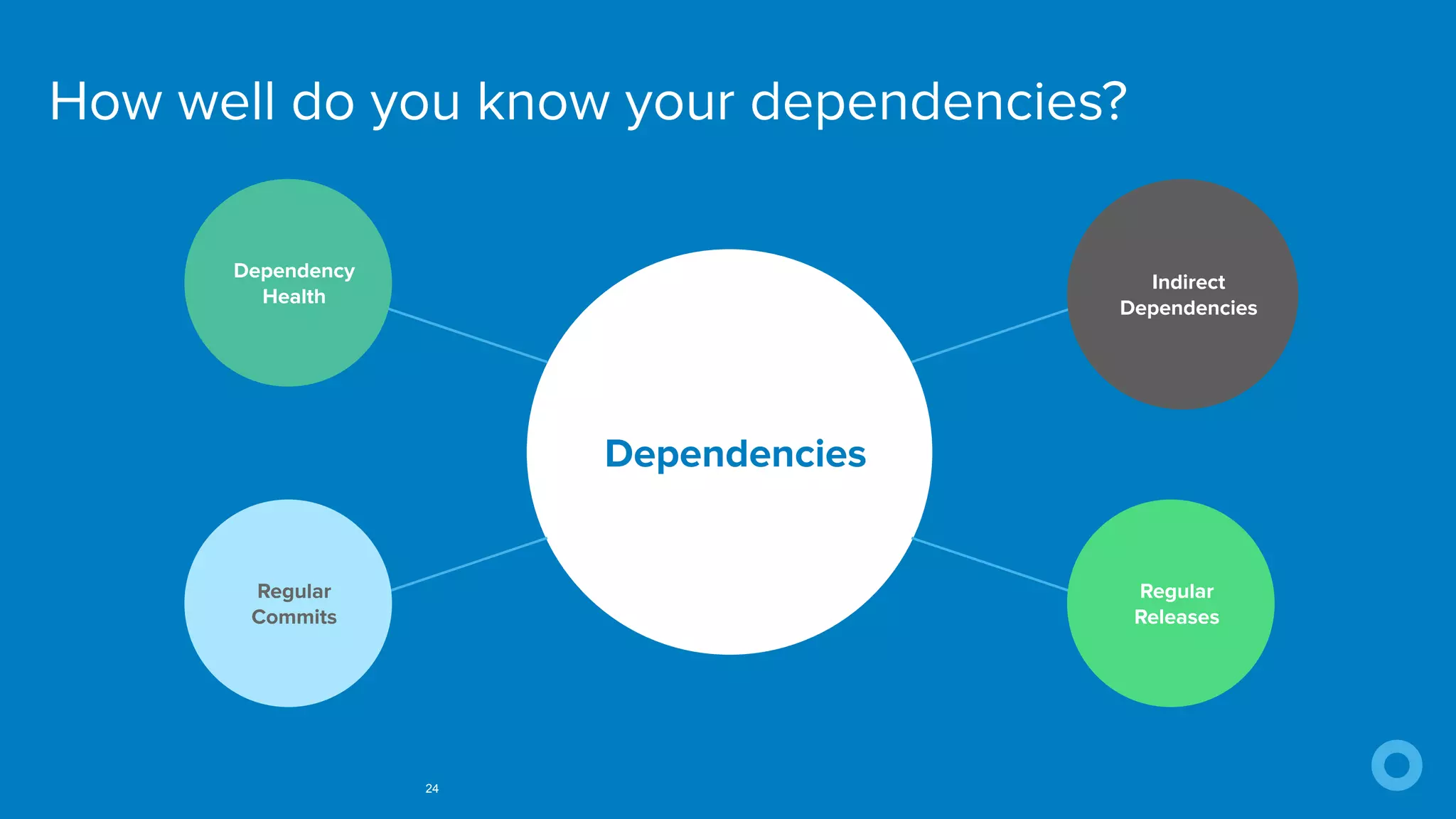
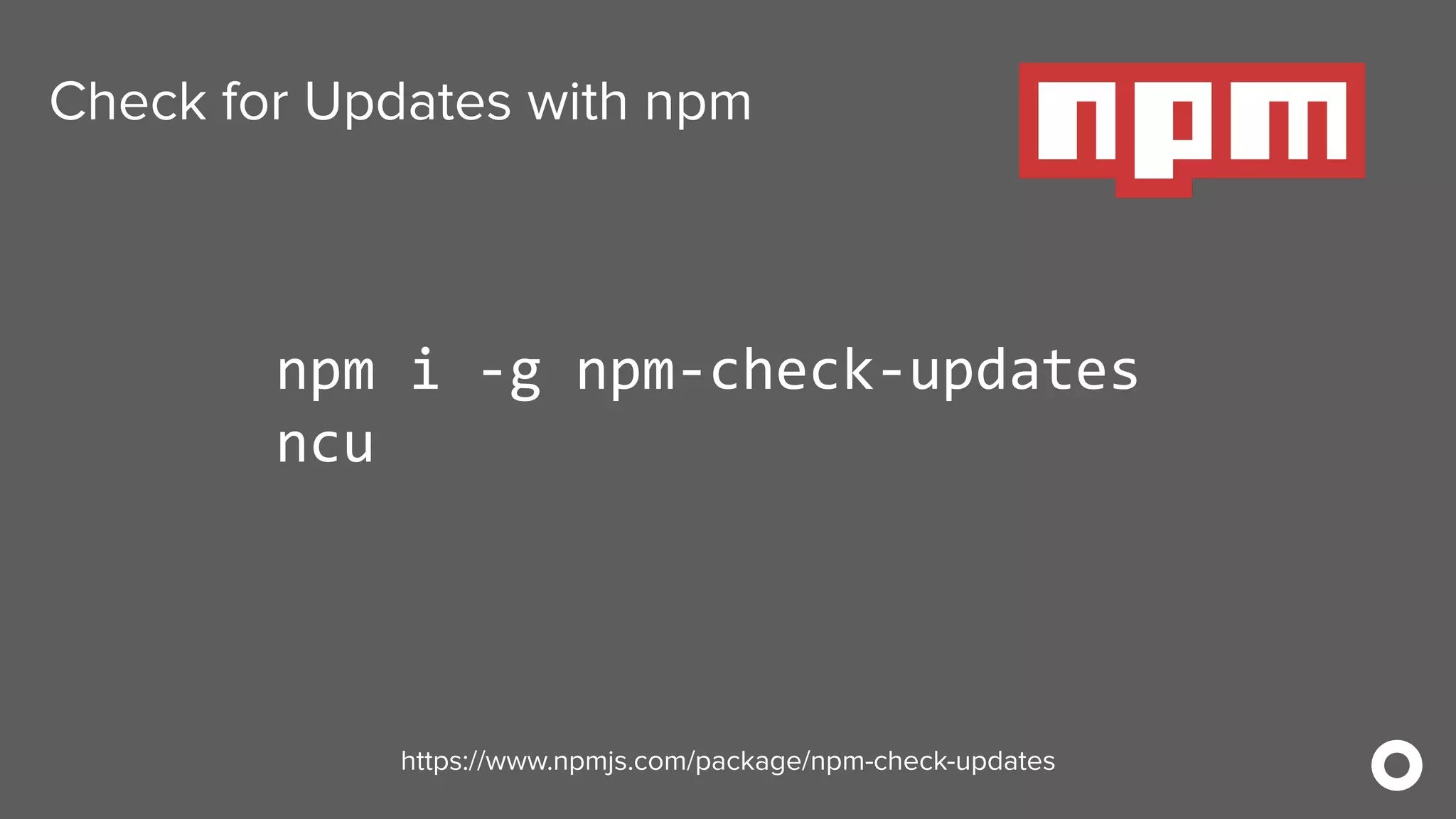
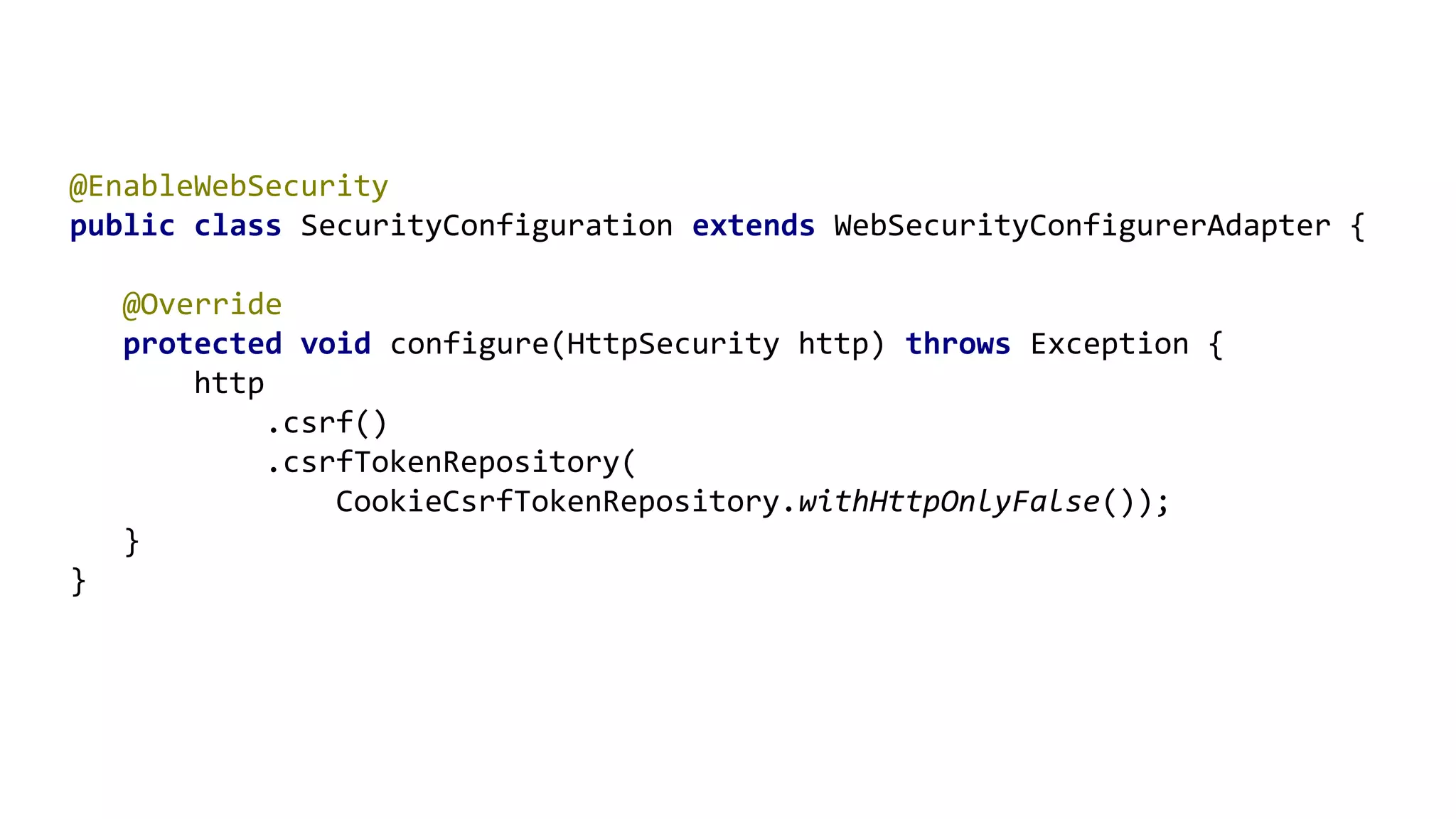
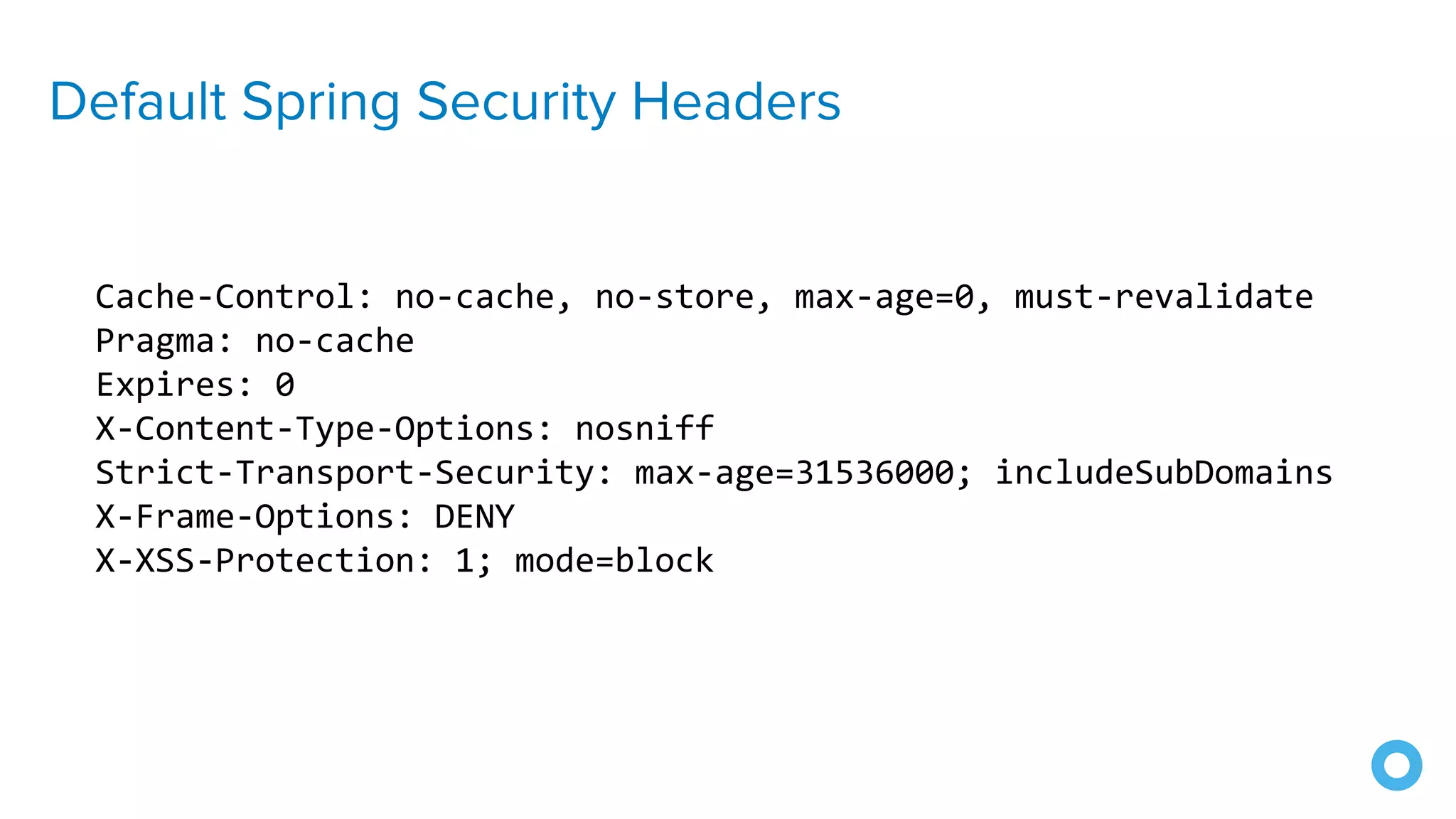
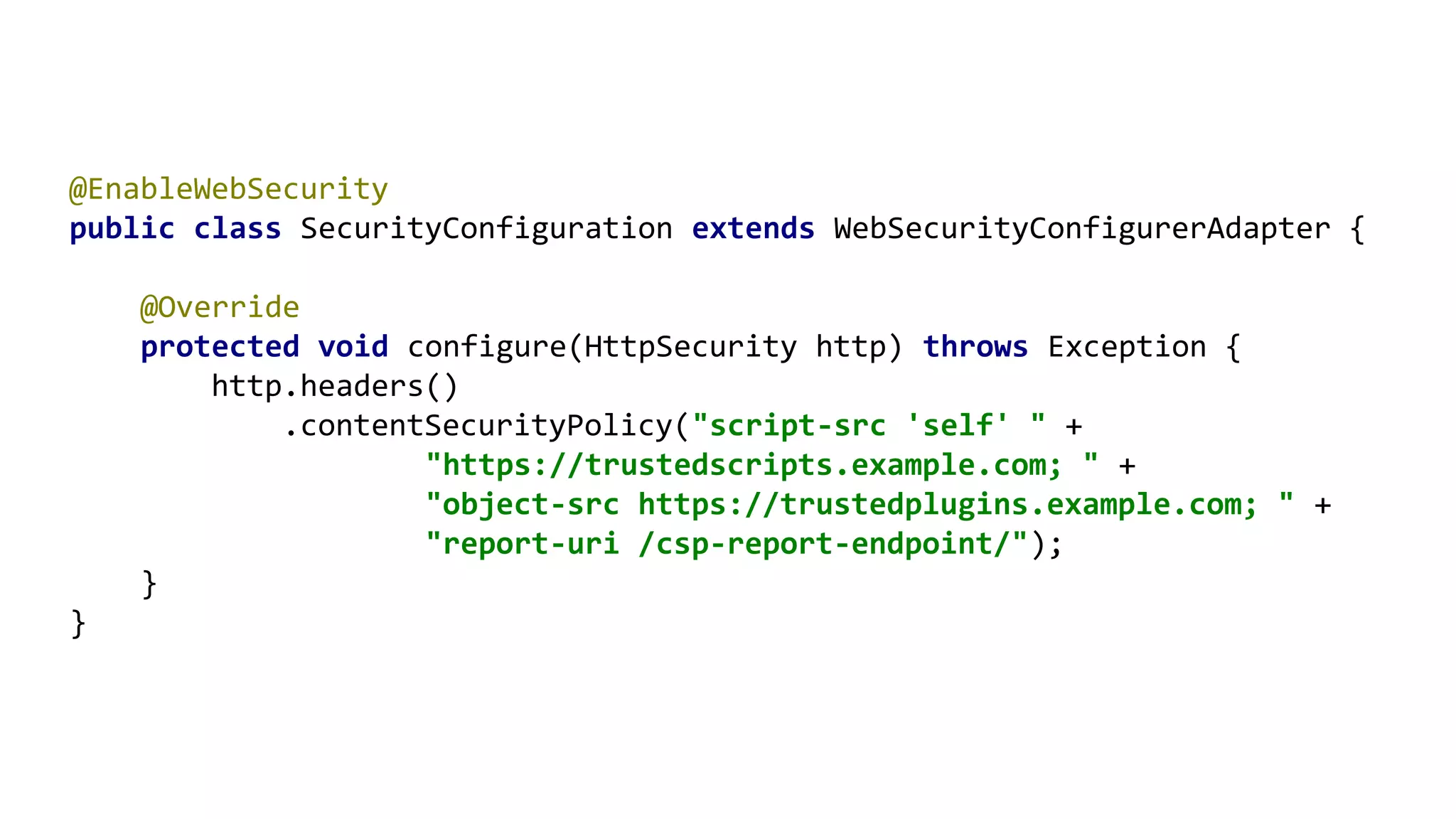
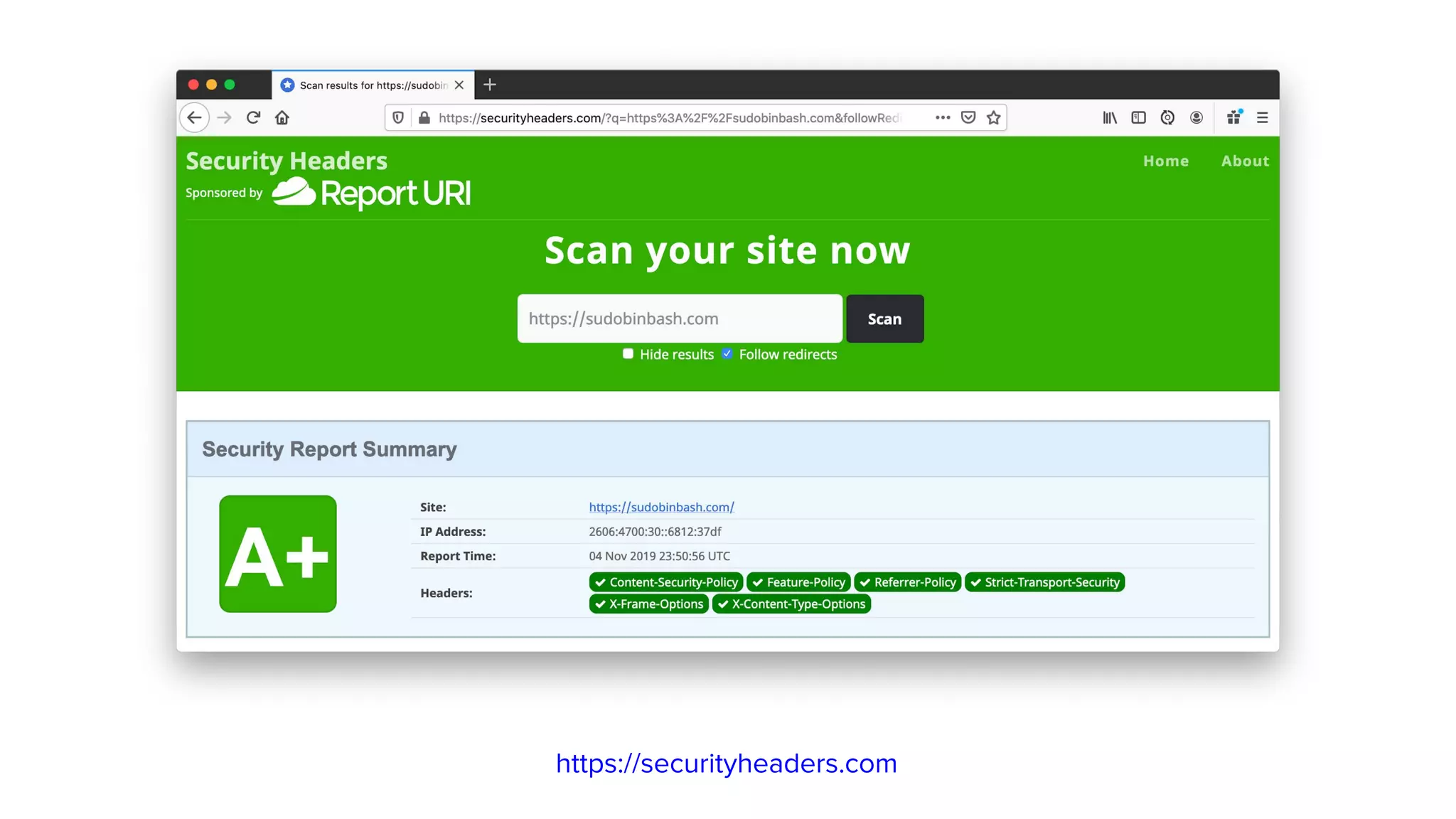
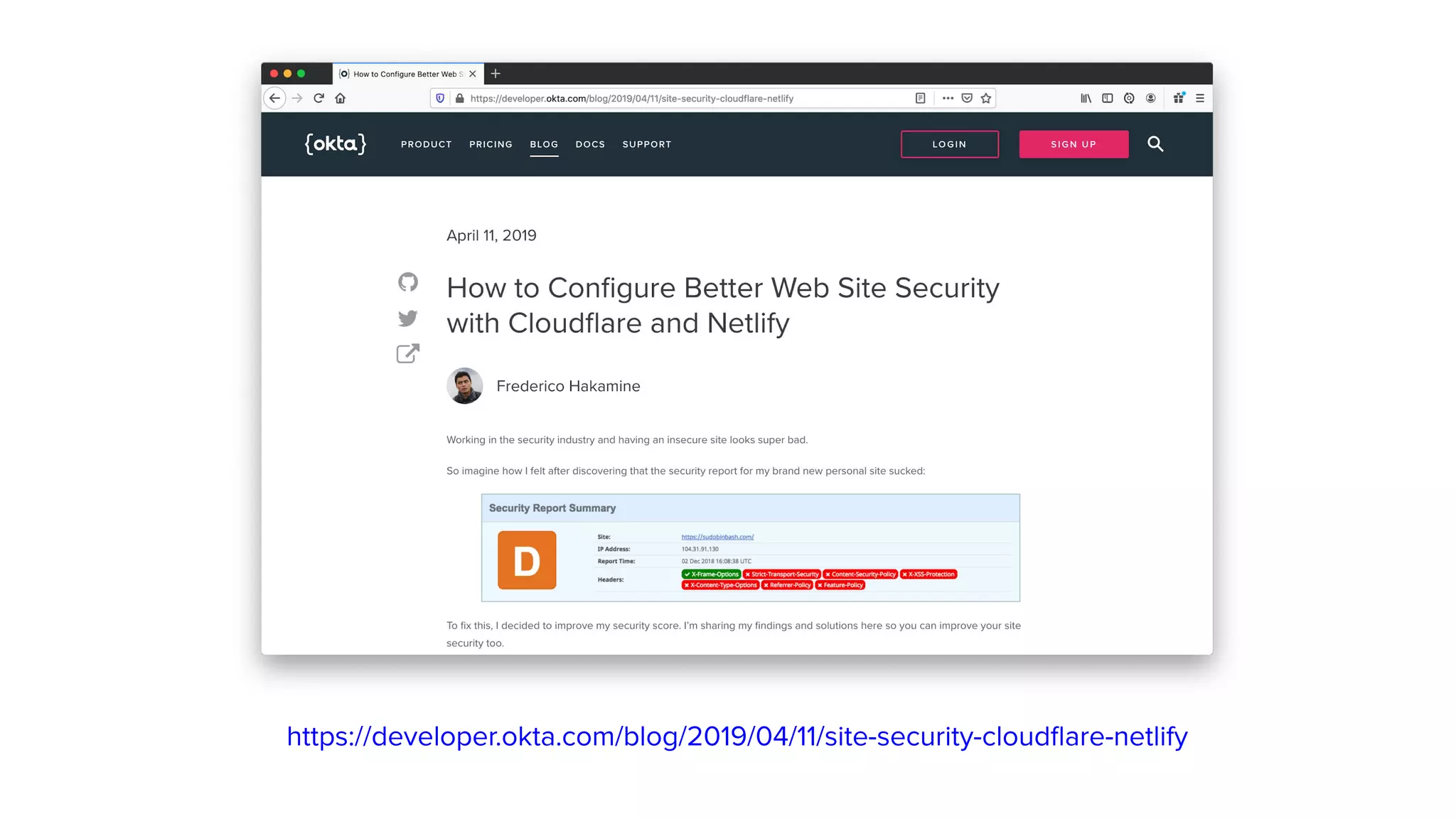
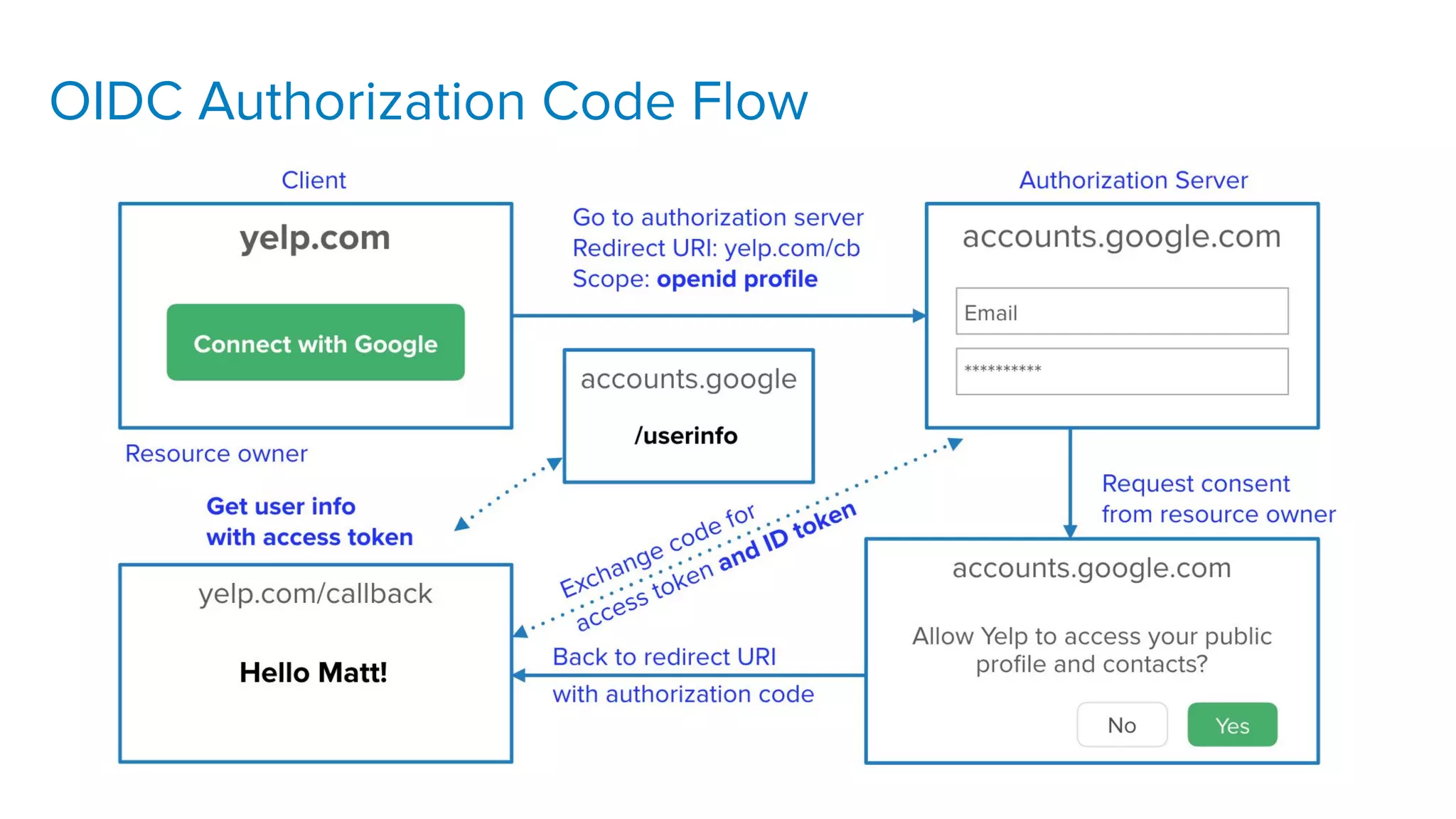
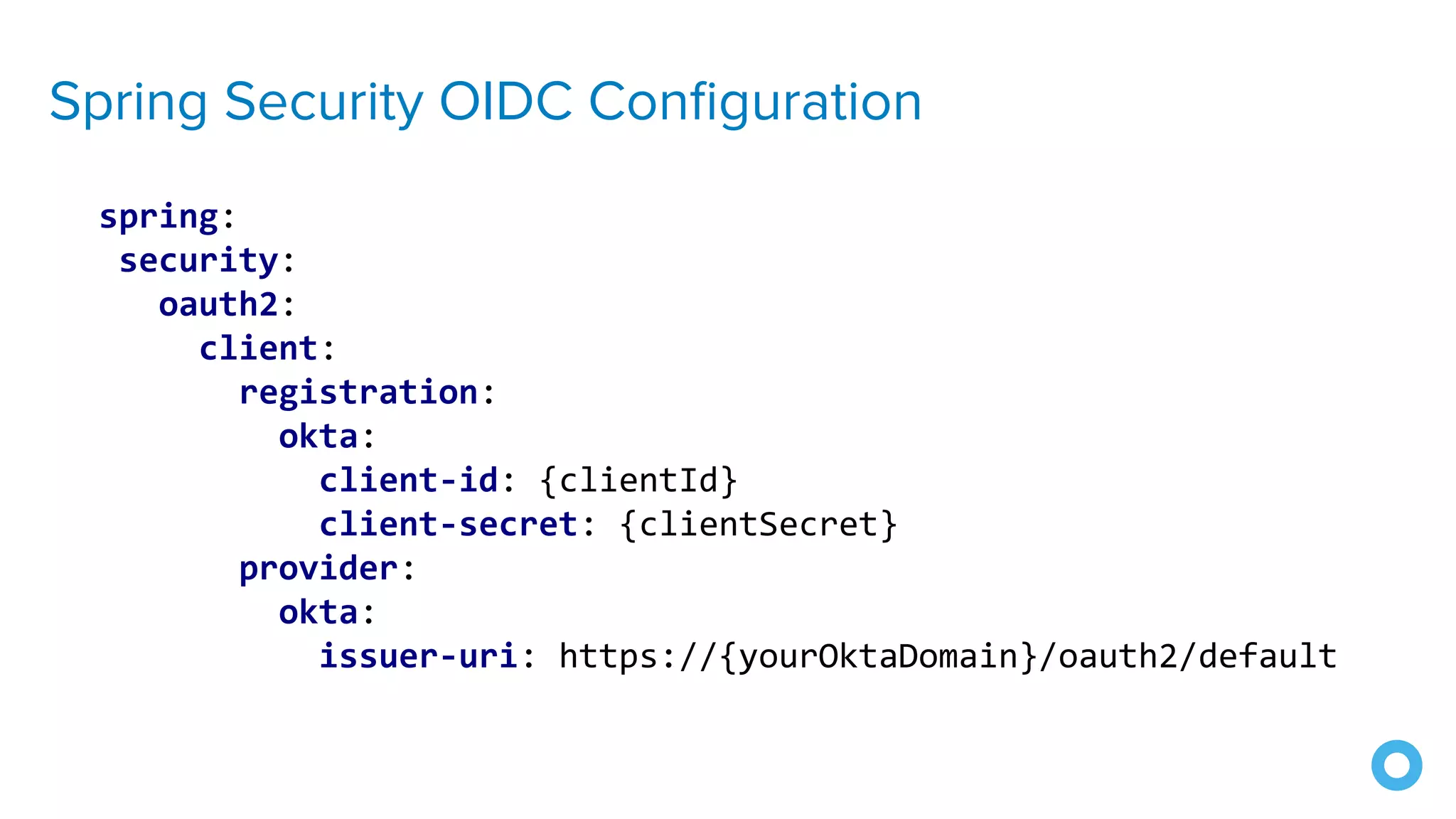
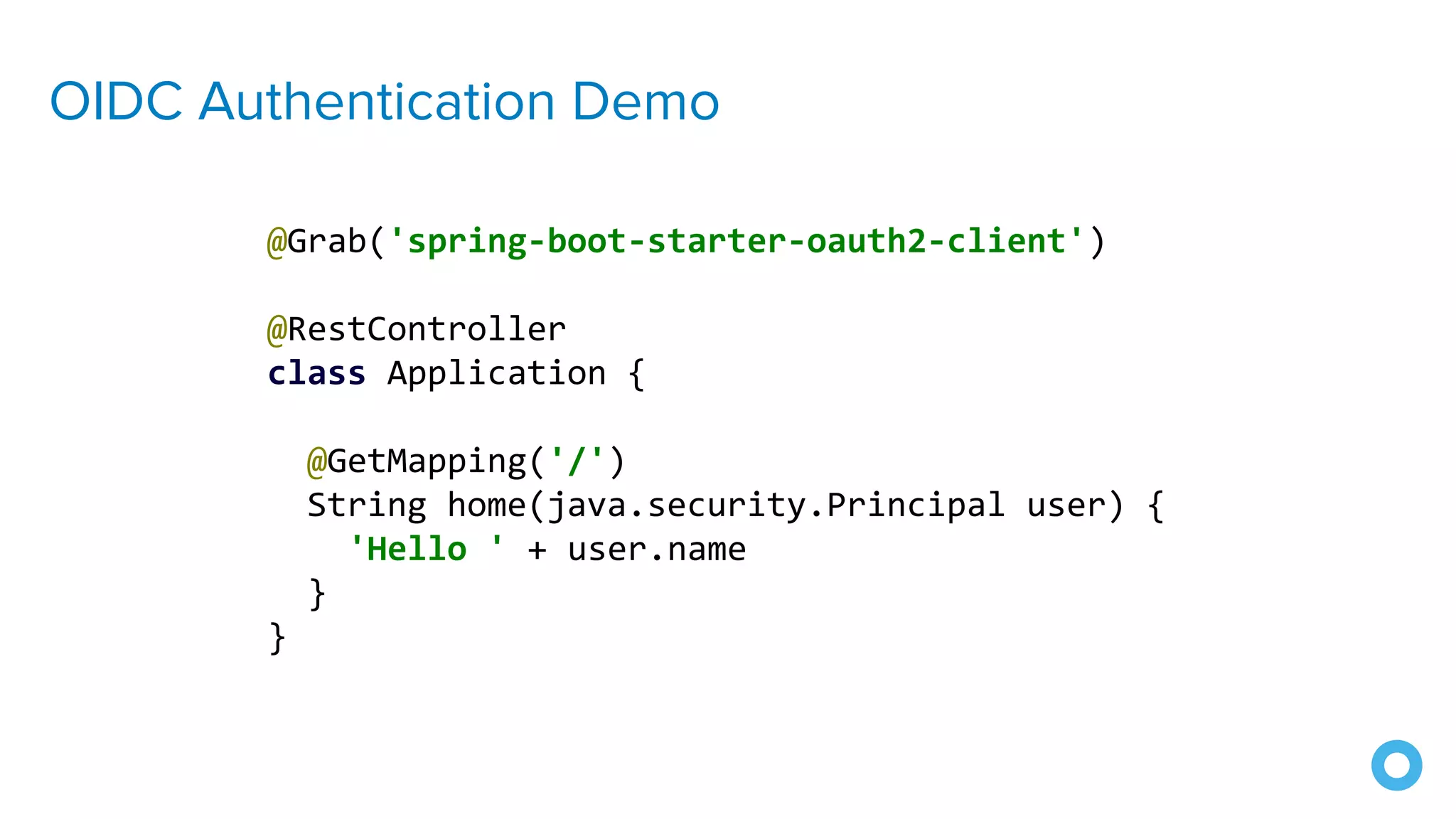
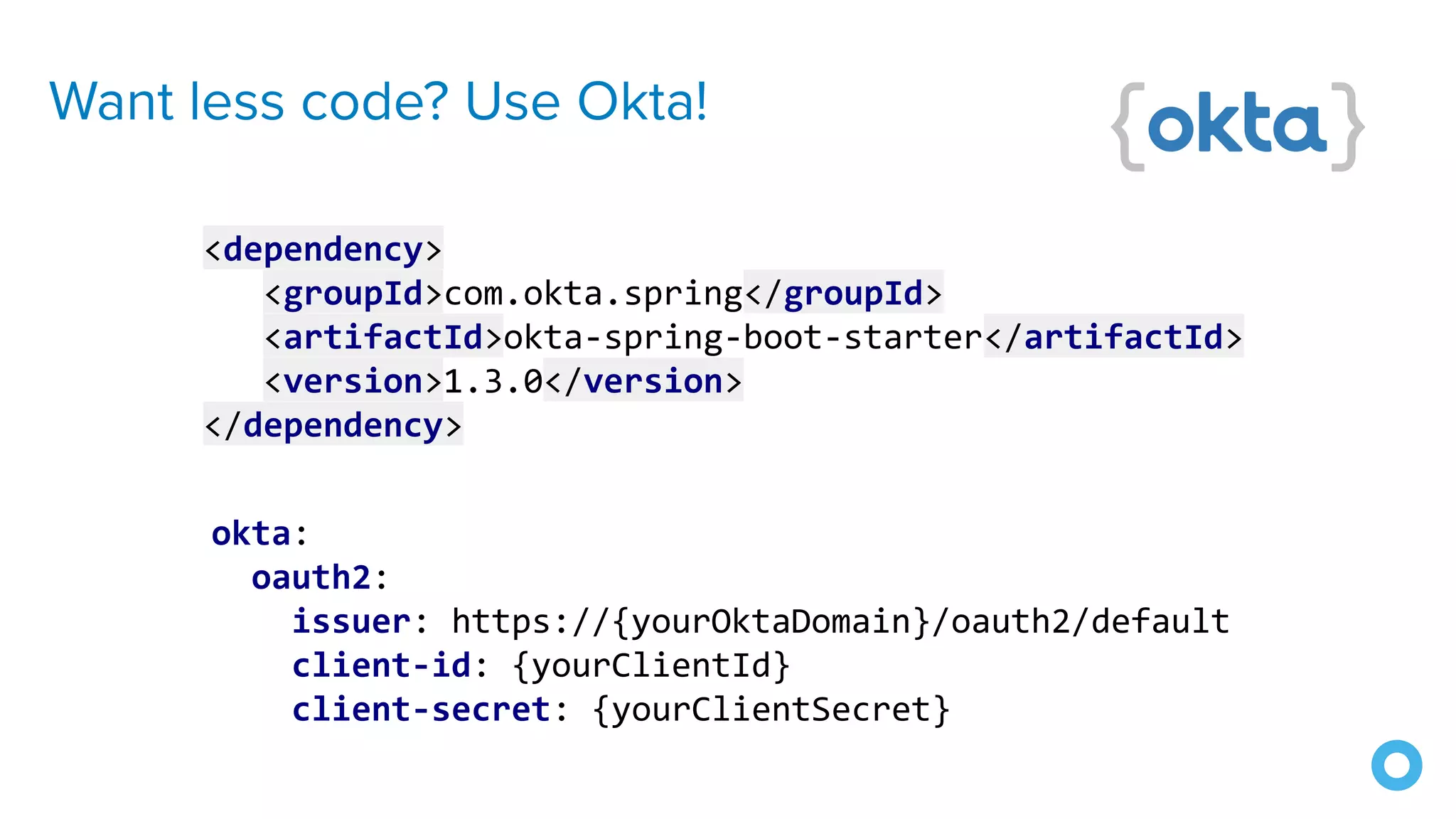
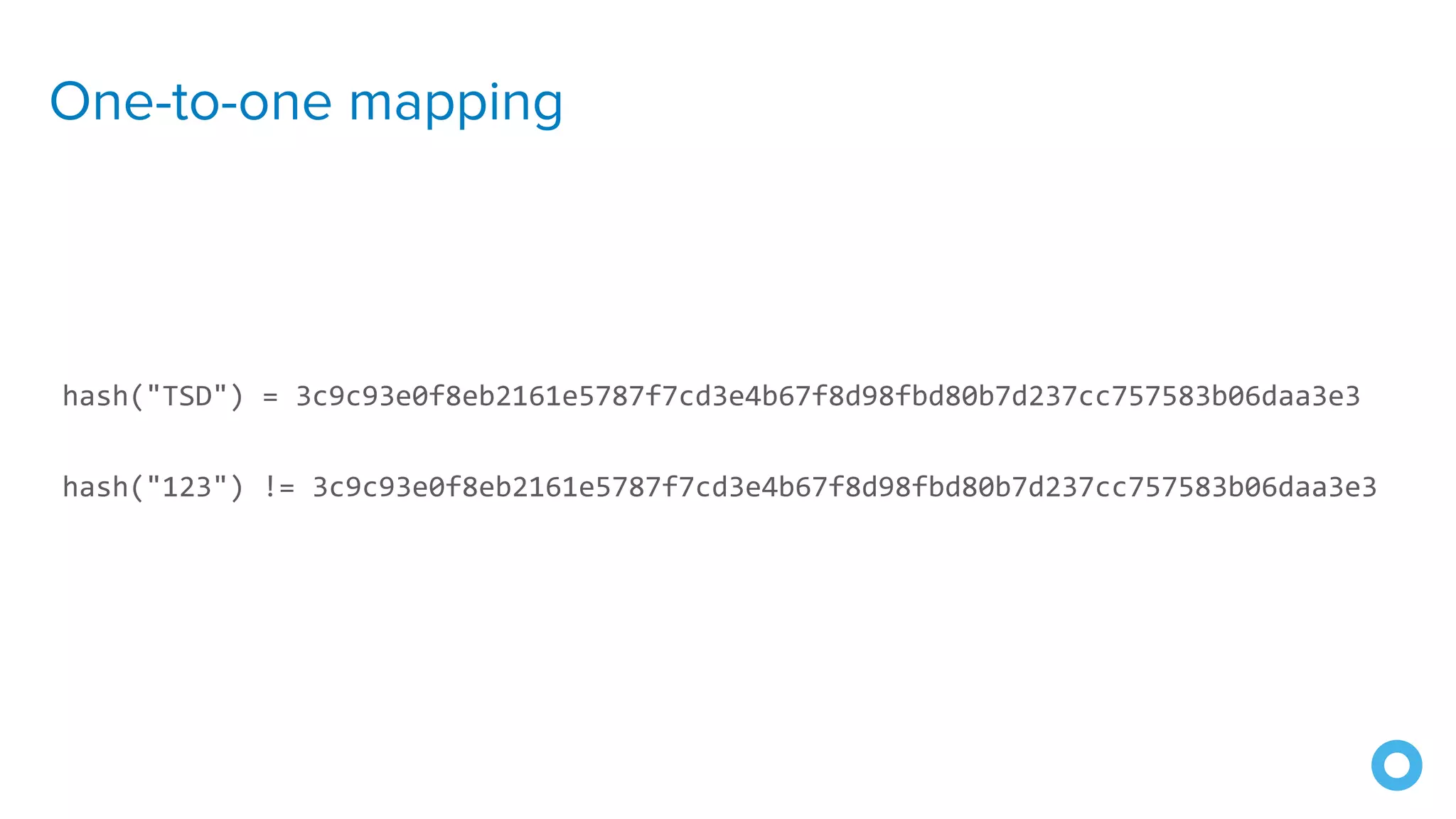
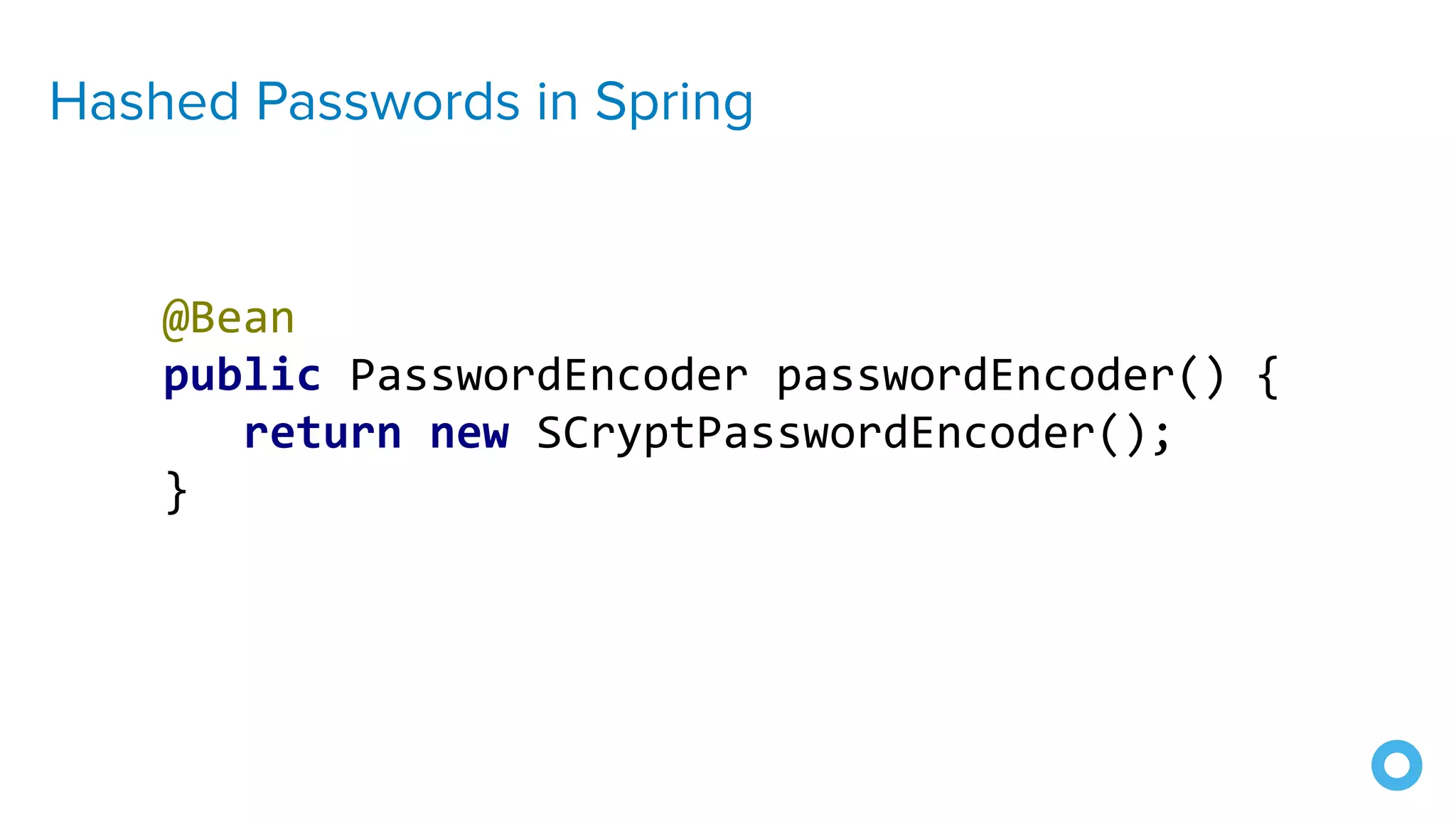
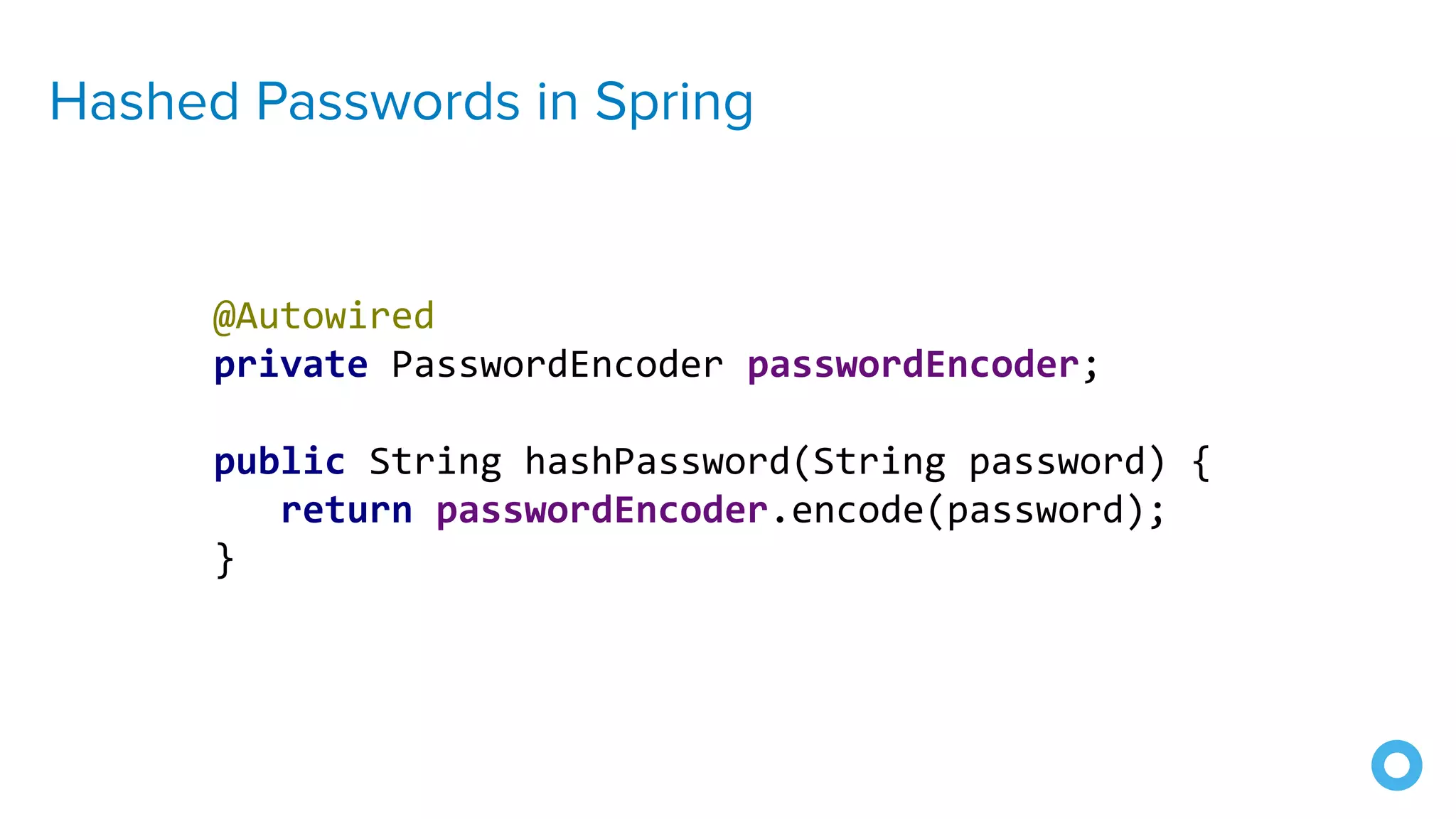
The document outlines ten effective strategies for securing Spring Boot applications. Key recommendations include using HTTPS, scanning for vulnerable dependencies, enabling CSRF protection, implementing content security policies, using OpenID Connect for authentication, and ensuring secure password hashing. Additional tips involve maintaining up-to-date libraries, securely storing secrets, testing with OWASP's ZAP tool, and conducting thorough code reviews.














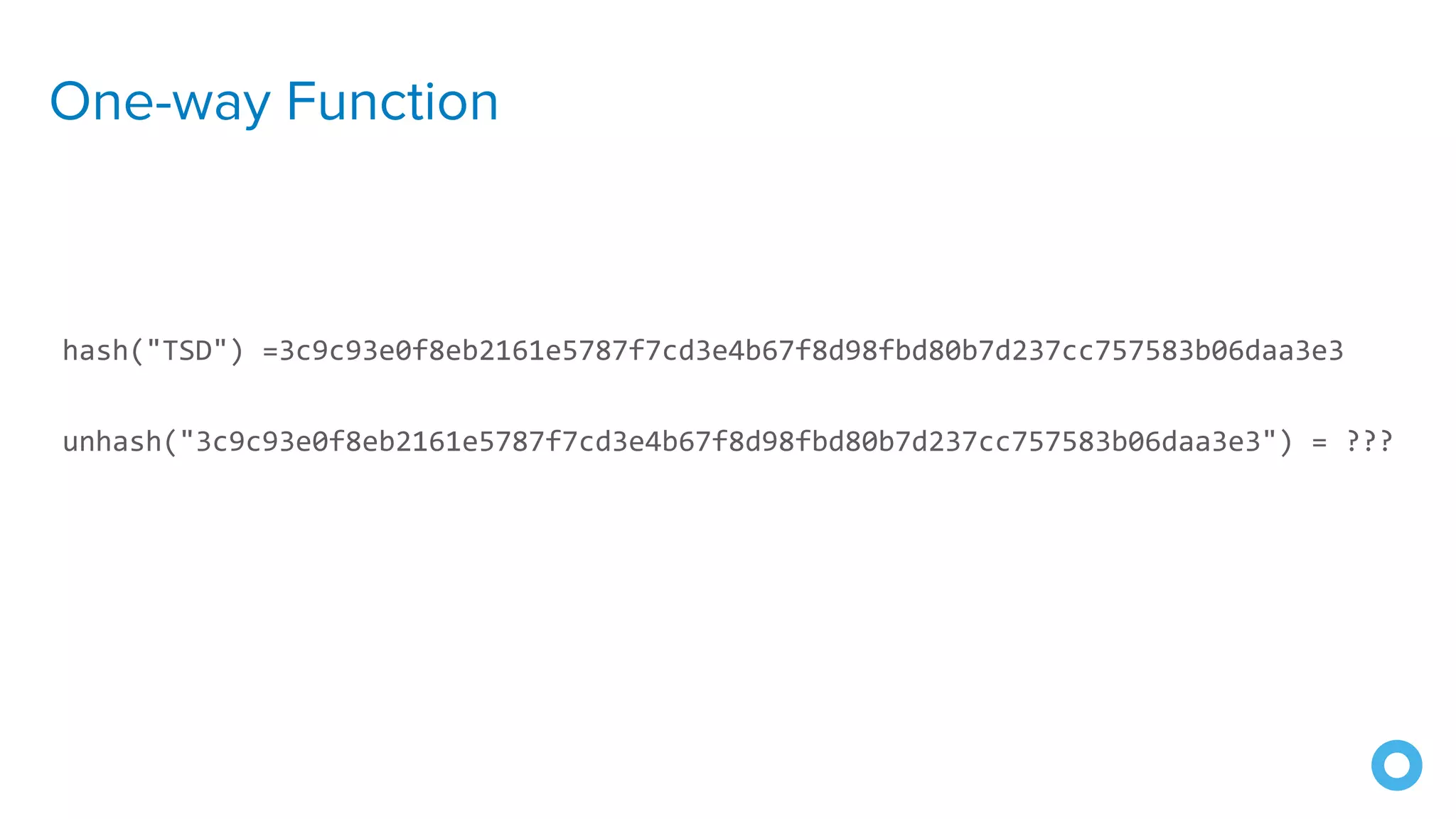
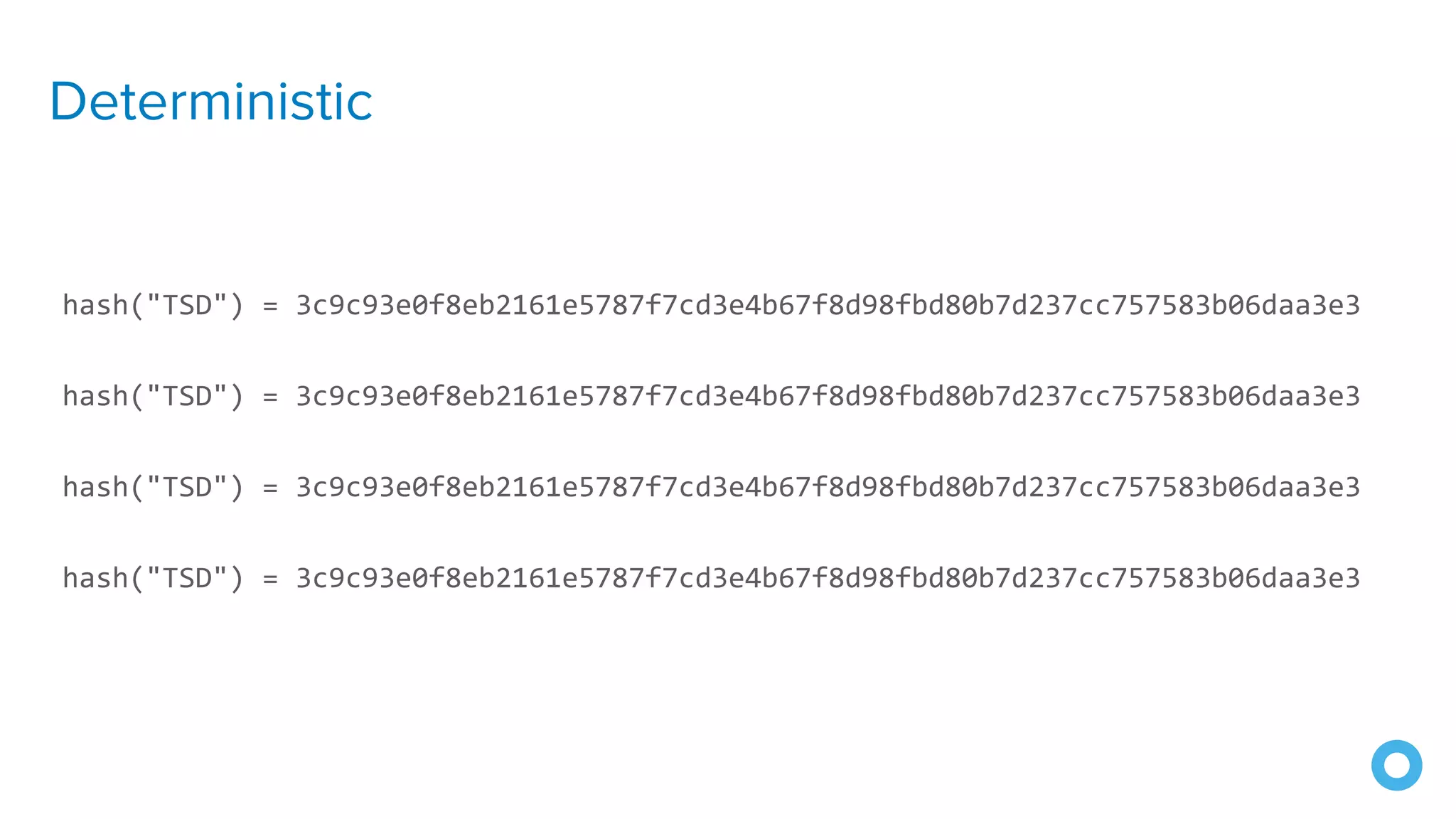
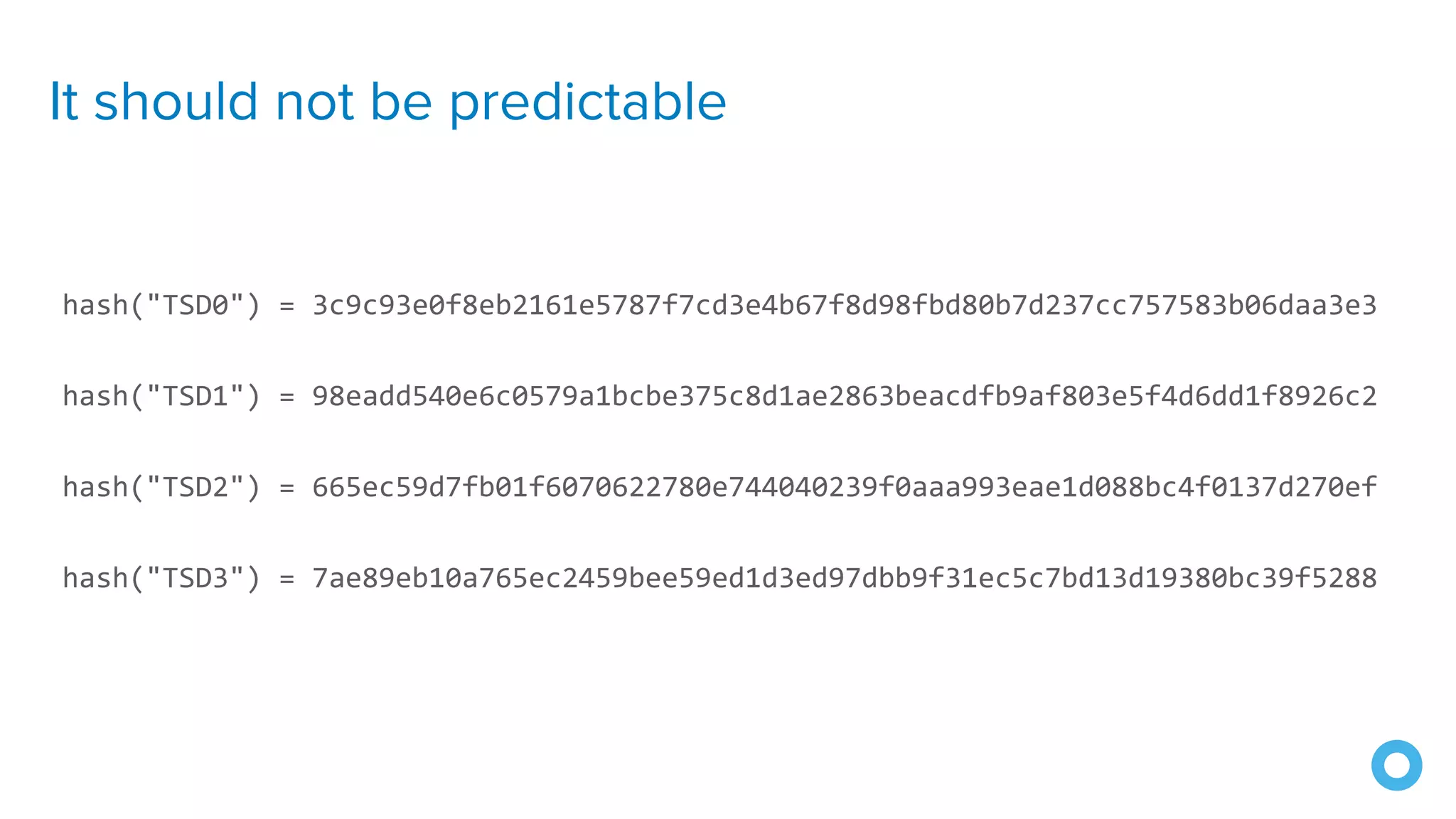


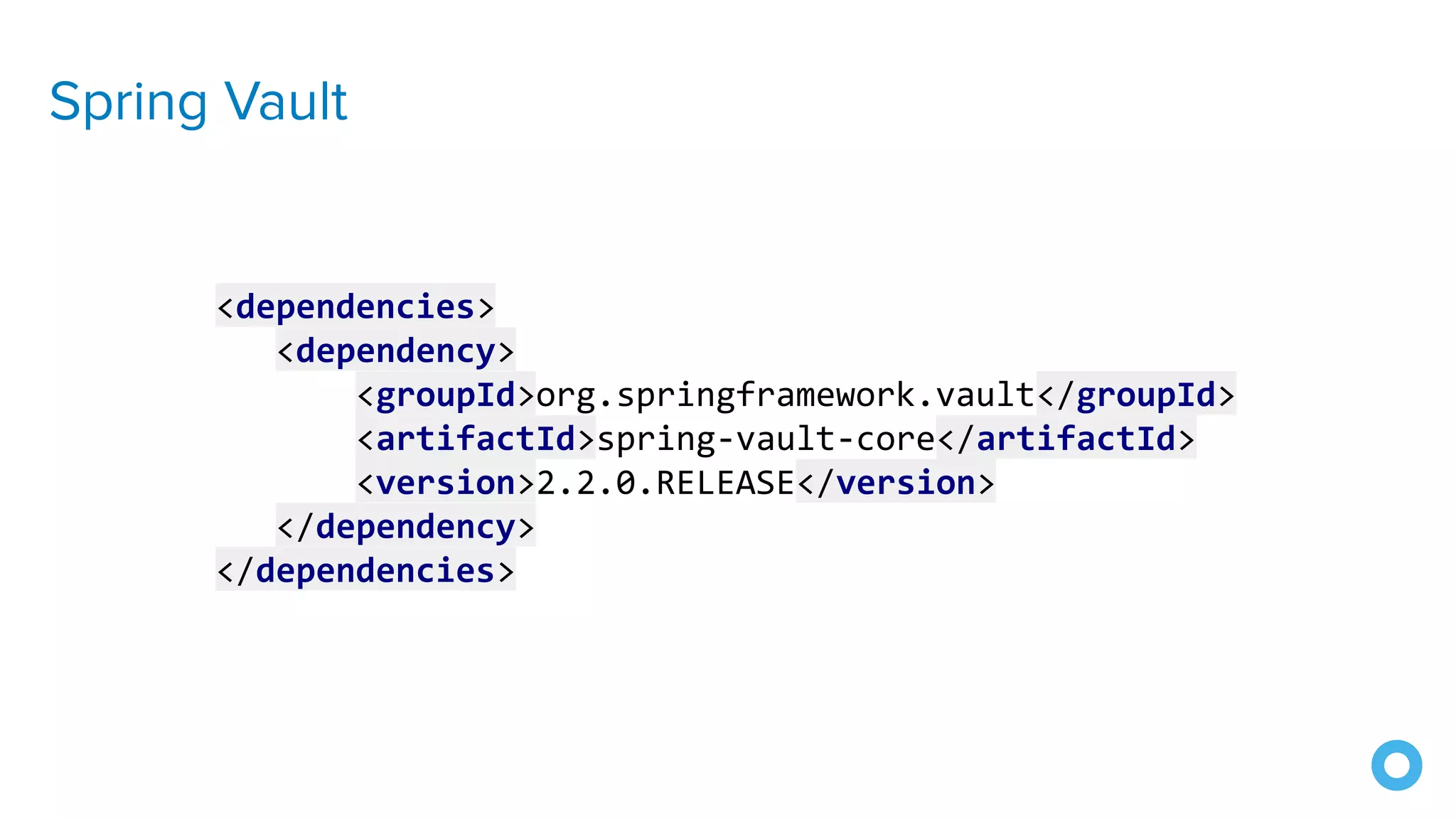
![Spring Vault
@Value("${password}")
char[] password;](https://image.slidesharecdn.com/10excellentwaystosecurespringbootapplications-200116222441/75/10-Excellent-Ways-to-Secure-Spring-Boot-Applications-Okta-Webinar-2020-54-2048.jpg)
![Why char[] instead of String for password?
Strings are immutable, can't wipe data
String passwords can be accidentally printed
https://www.baeldung.com/java-storing-passwords
Printing String password -> password
Printing char[] password -> [C@6e8cf4c6](https://image.slidesharecdn.com/10excellentwaystosecurespringbootapplications-200116222441/75/10-Excellent-Ways-to-Secure-Spring-Boot-Applications-Okta-Webinar-2020-55-2048.jpg)