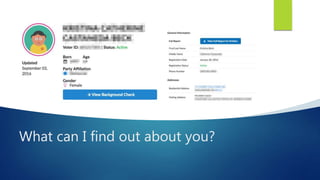
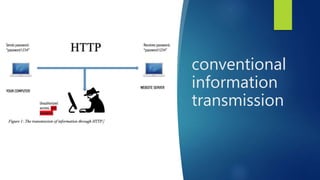
Ayman Siraj is a junior at USC majoring in chemical engineering and minoring in digital forensics. The document discusses the importance of cyber security and how social engineering is a common way that people are victimized by having personal information exposed online. It recommends people check haveibeenpwned.com to see if their information has been part of a data breach.