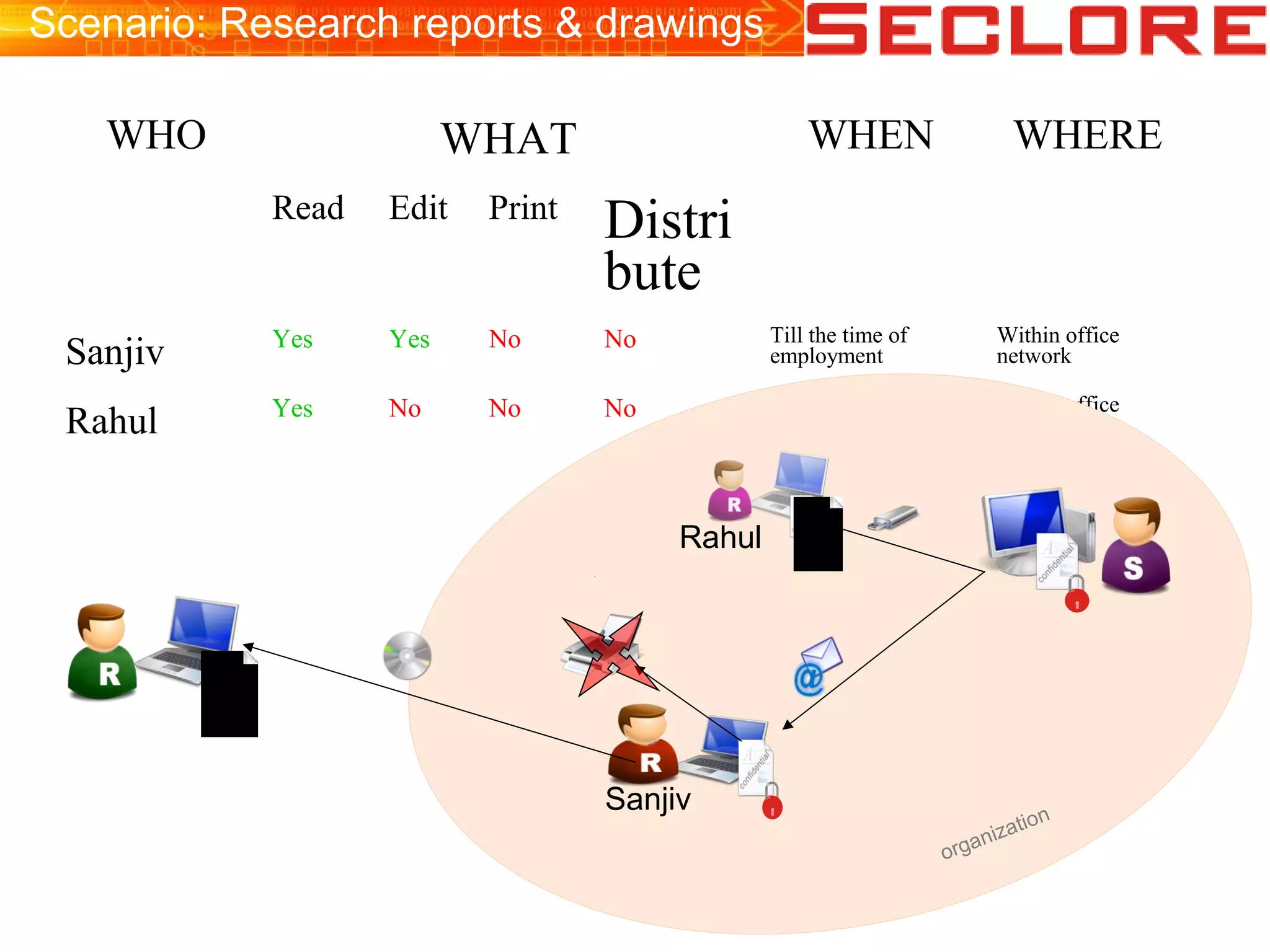
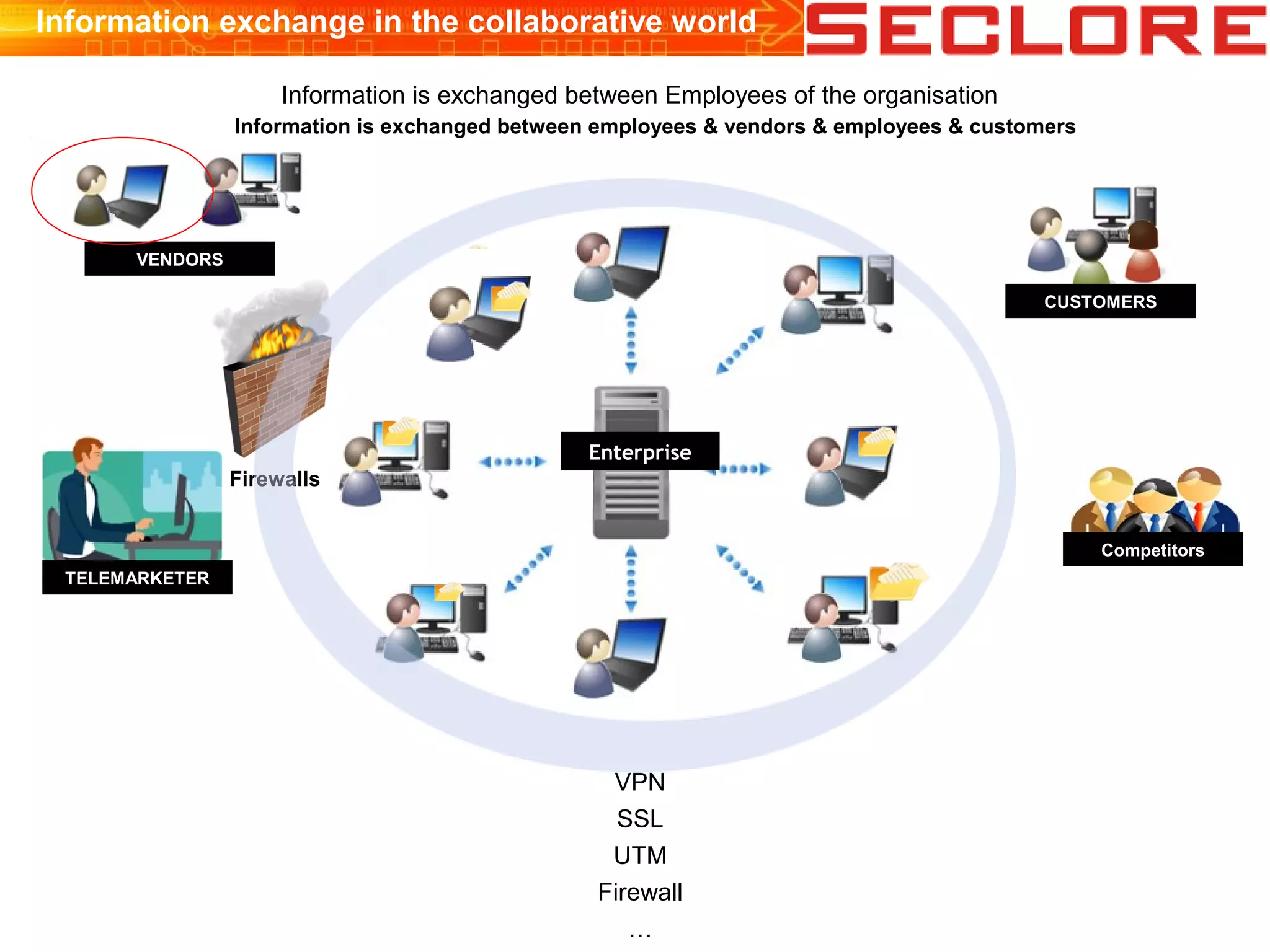
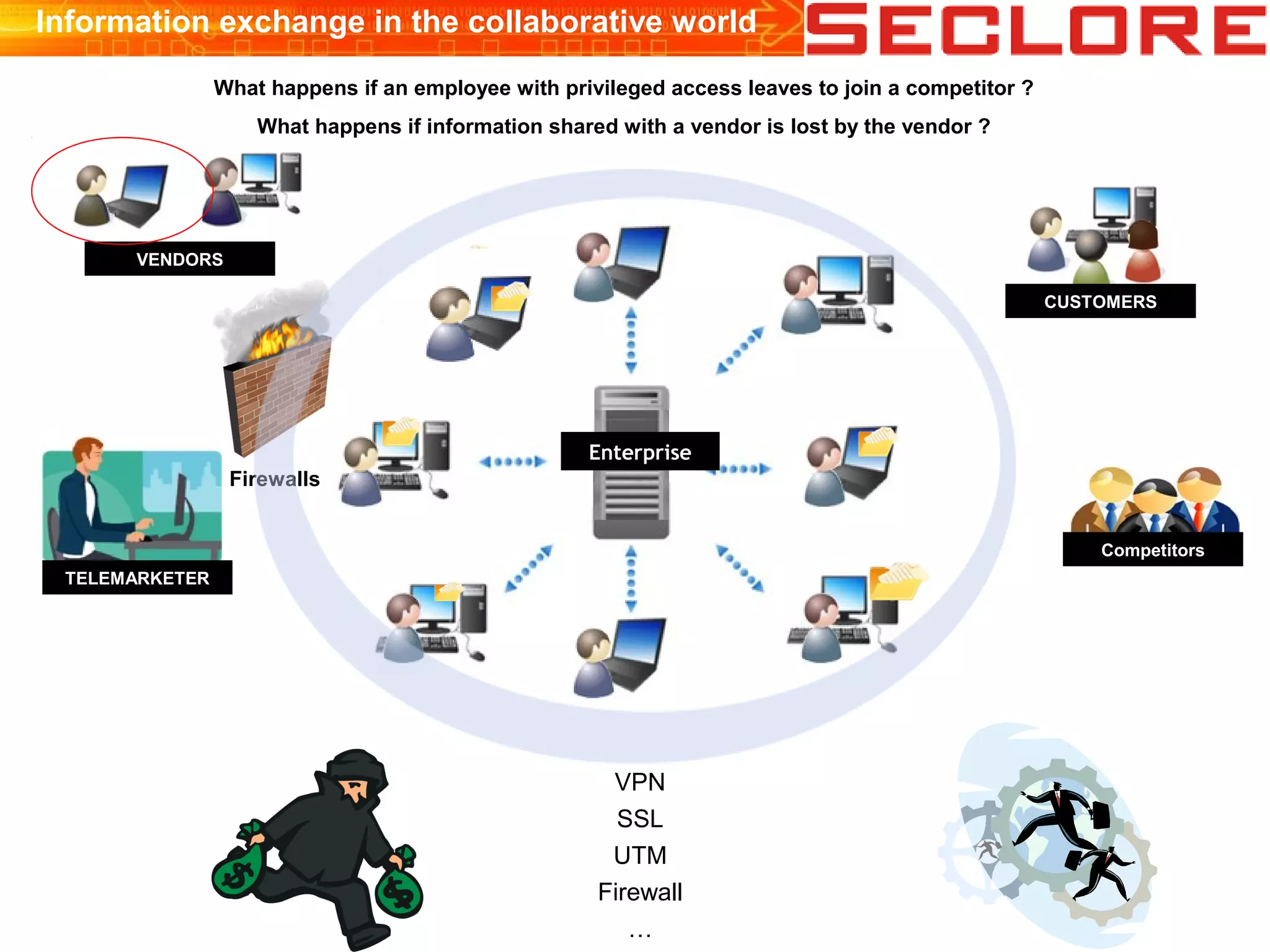
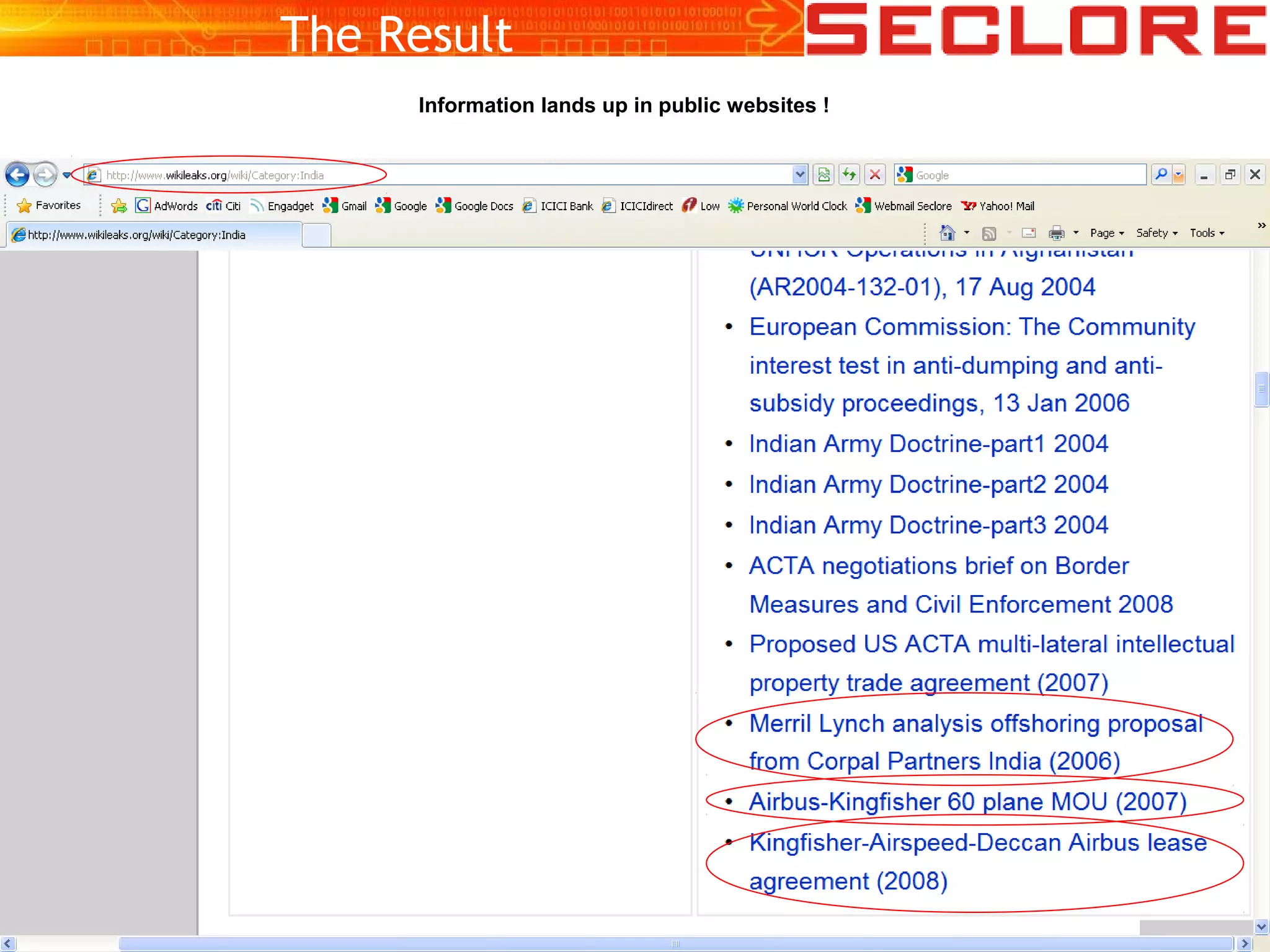
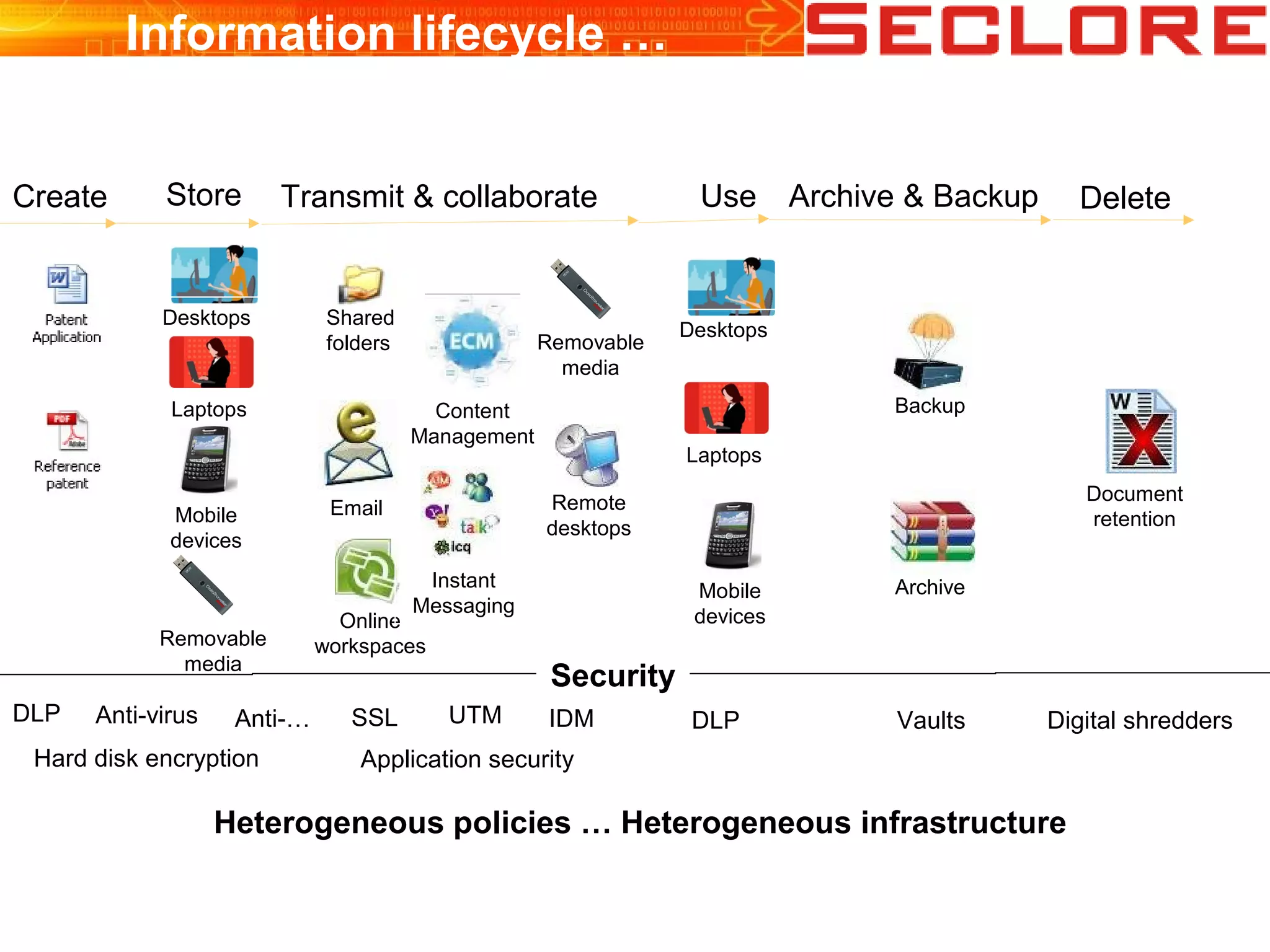
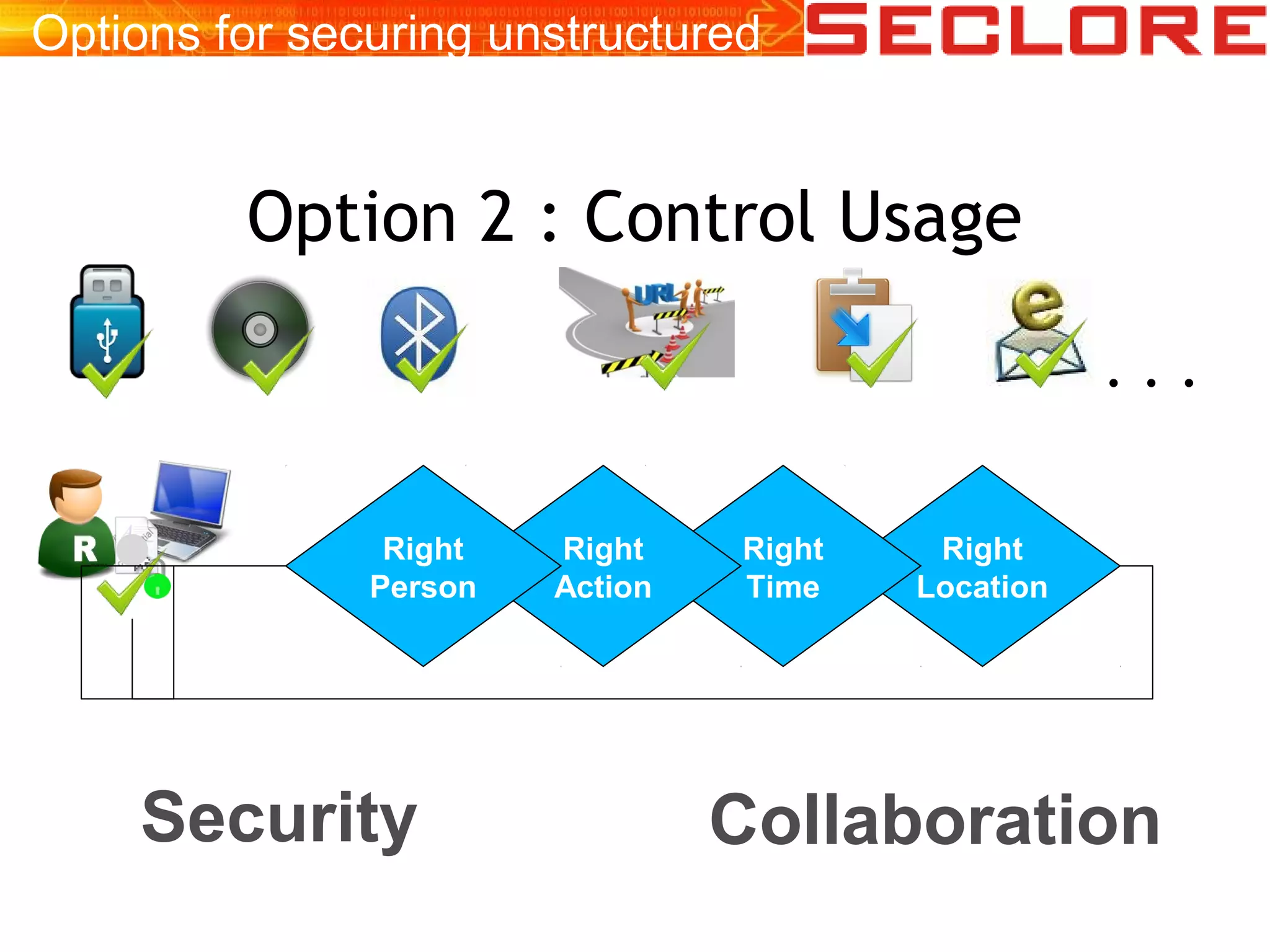
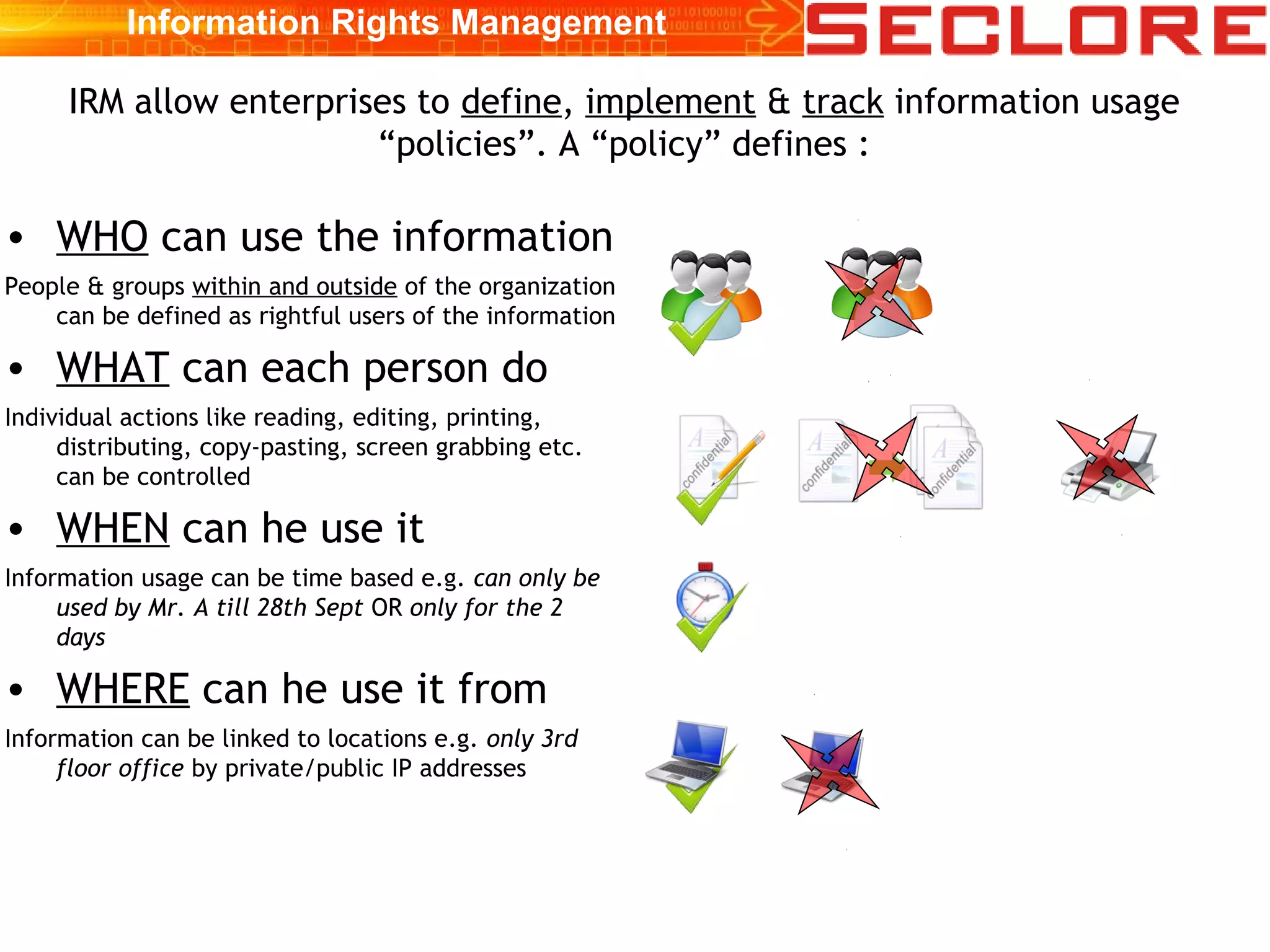
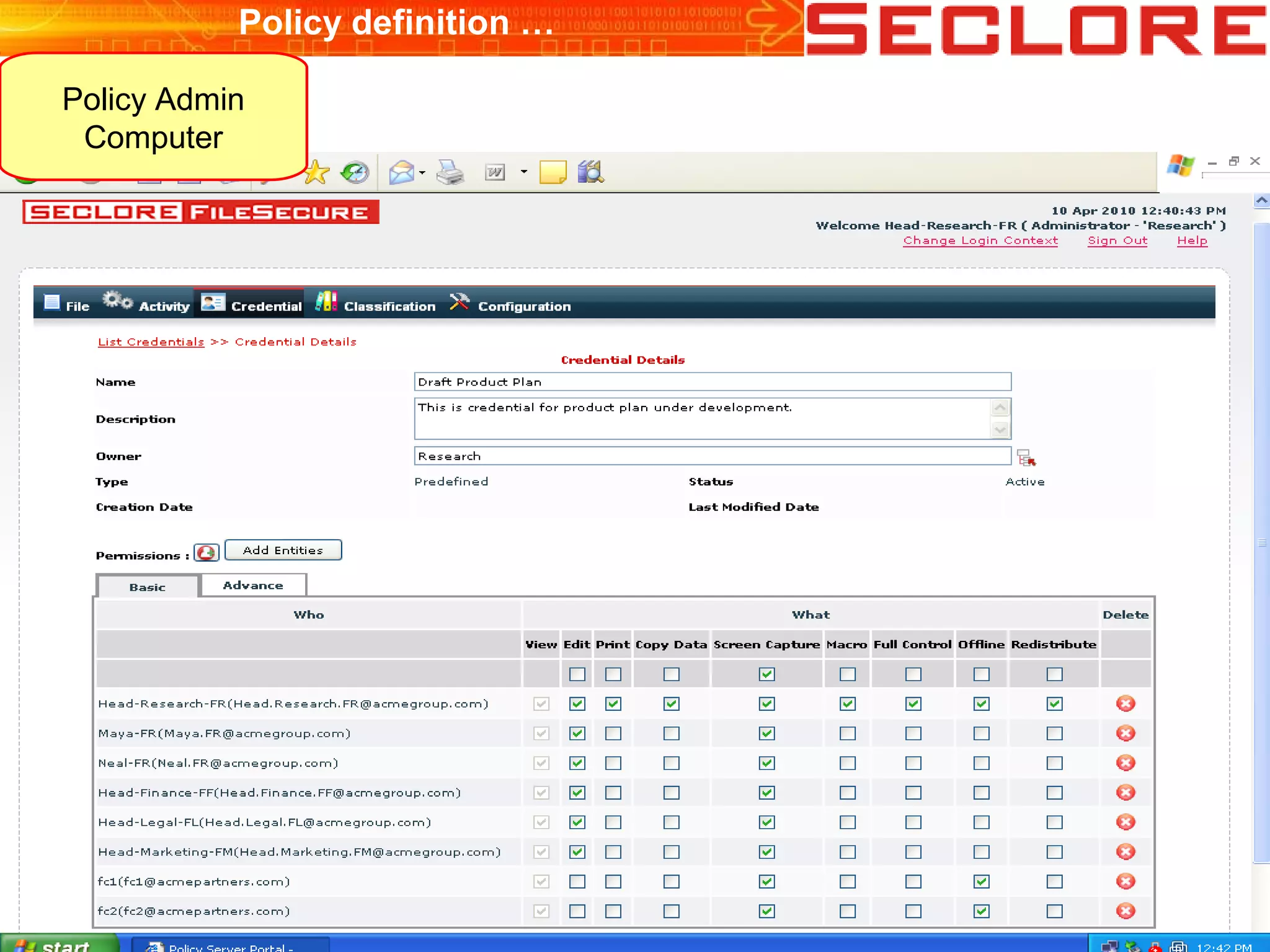
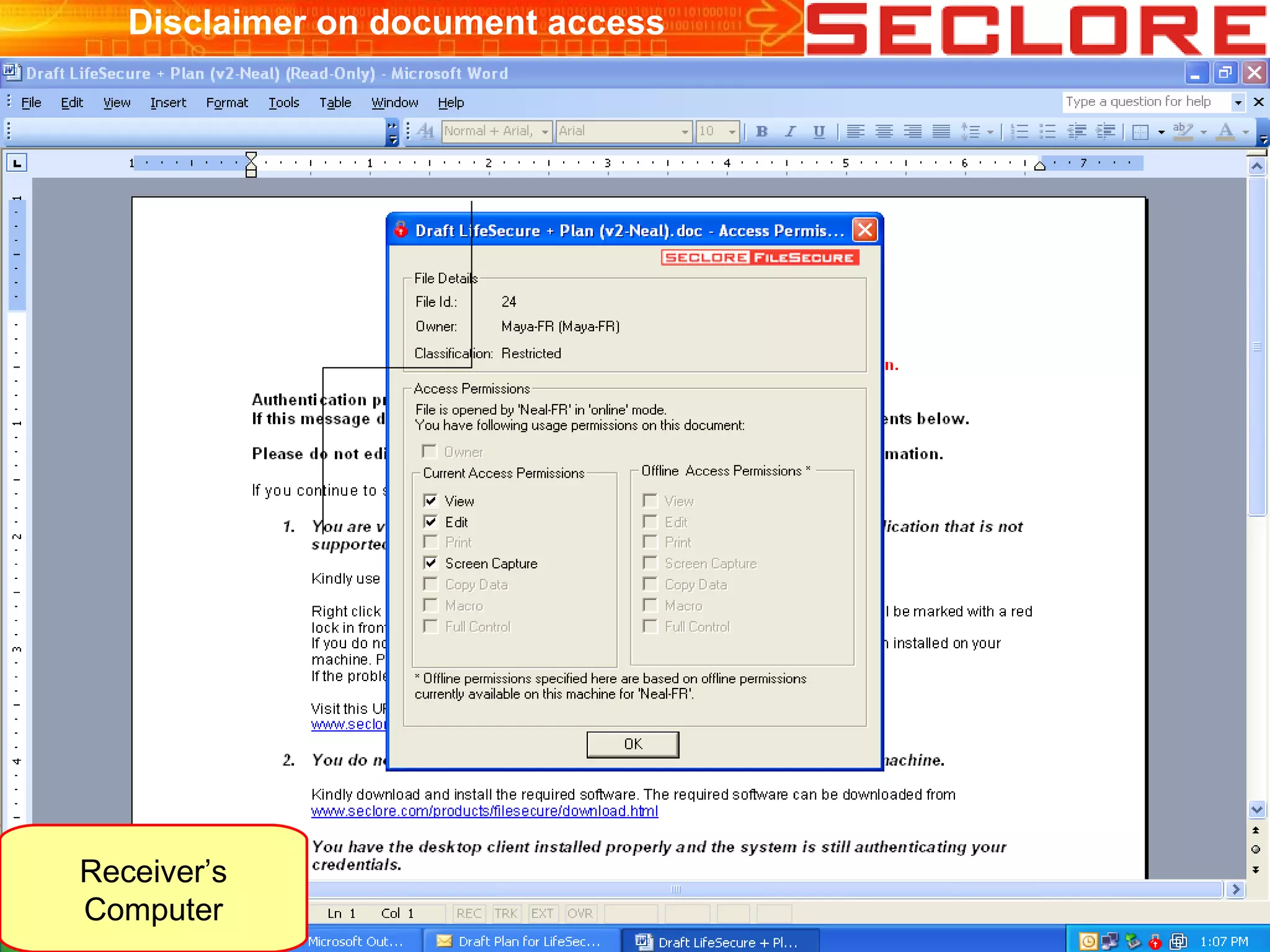
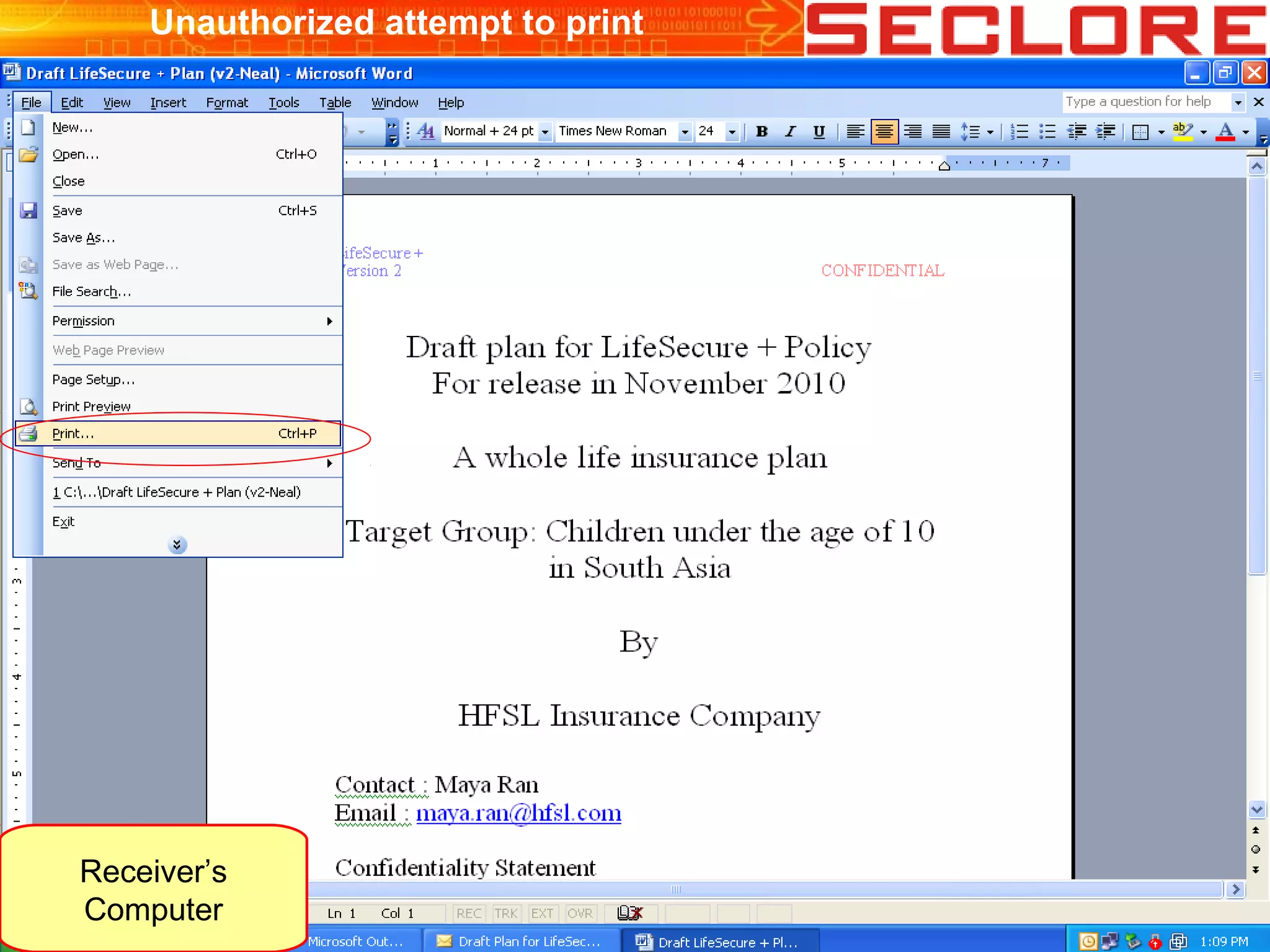
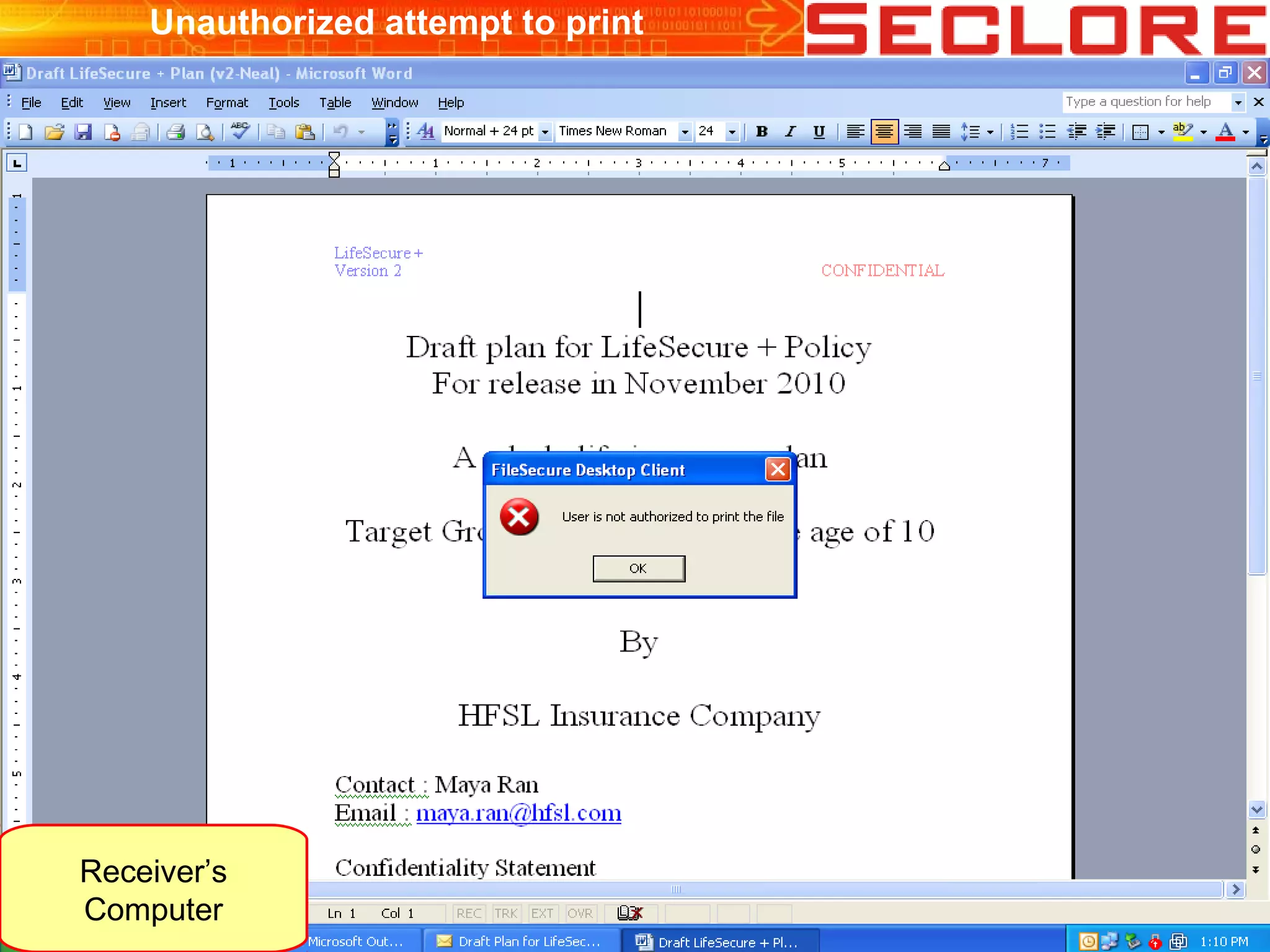
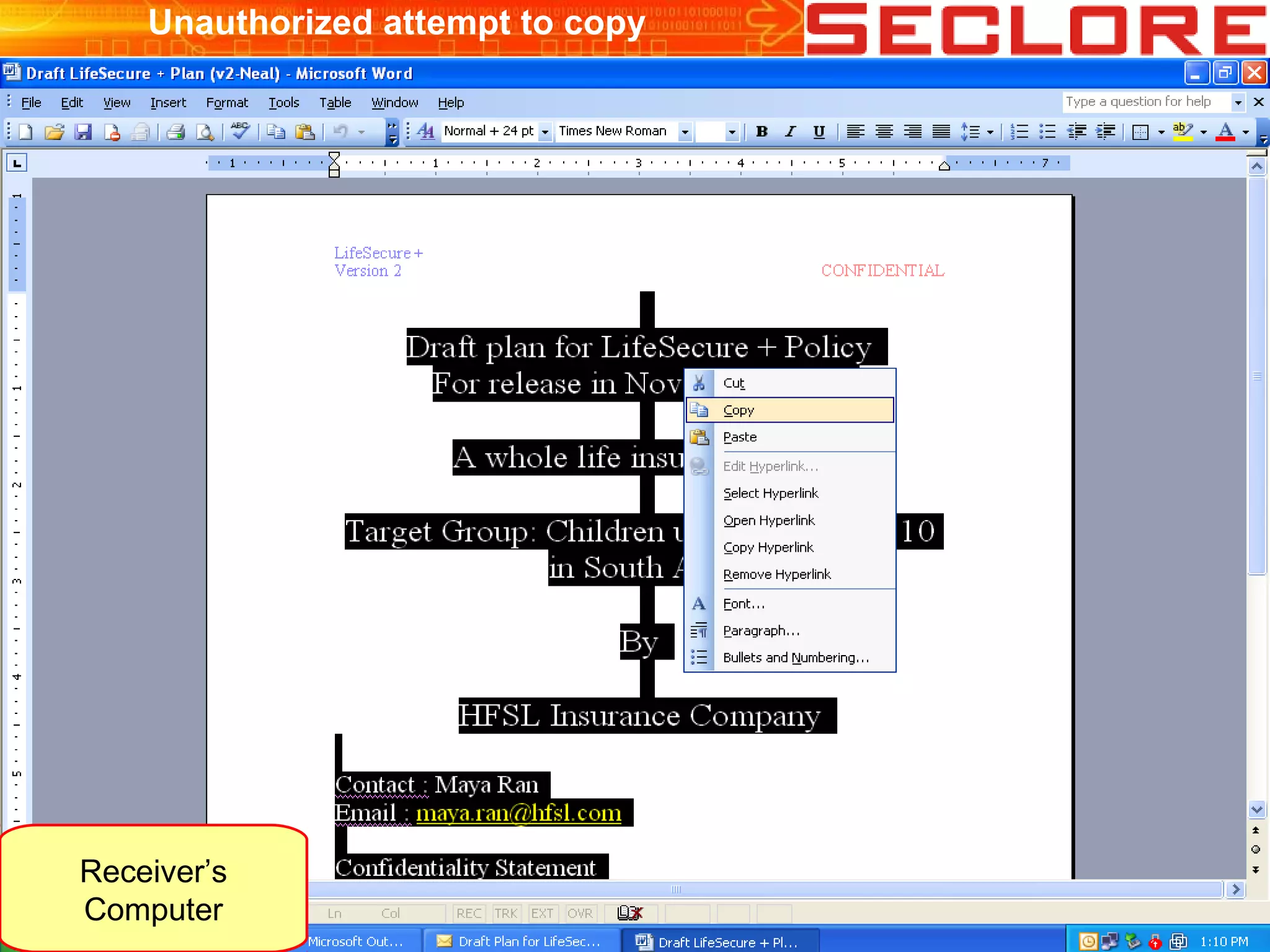
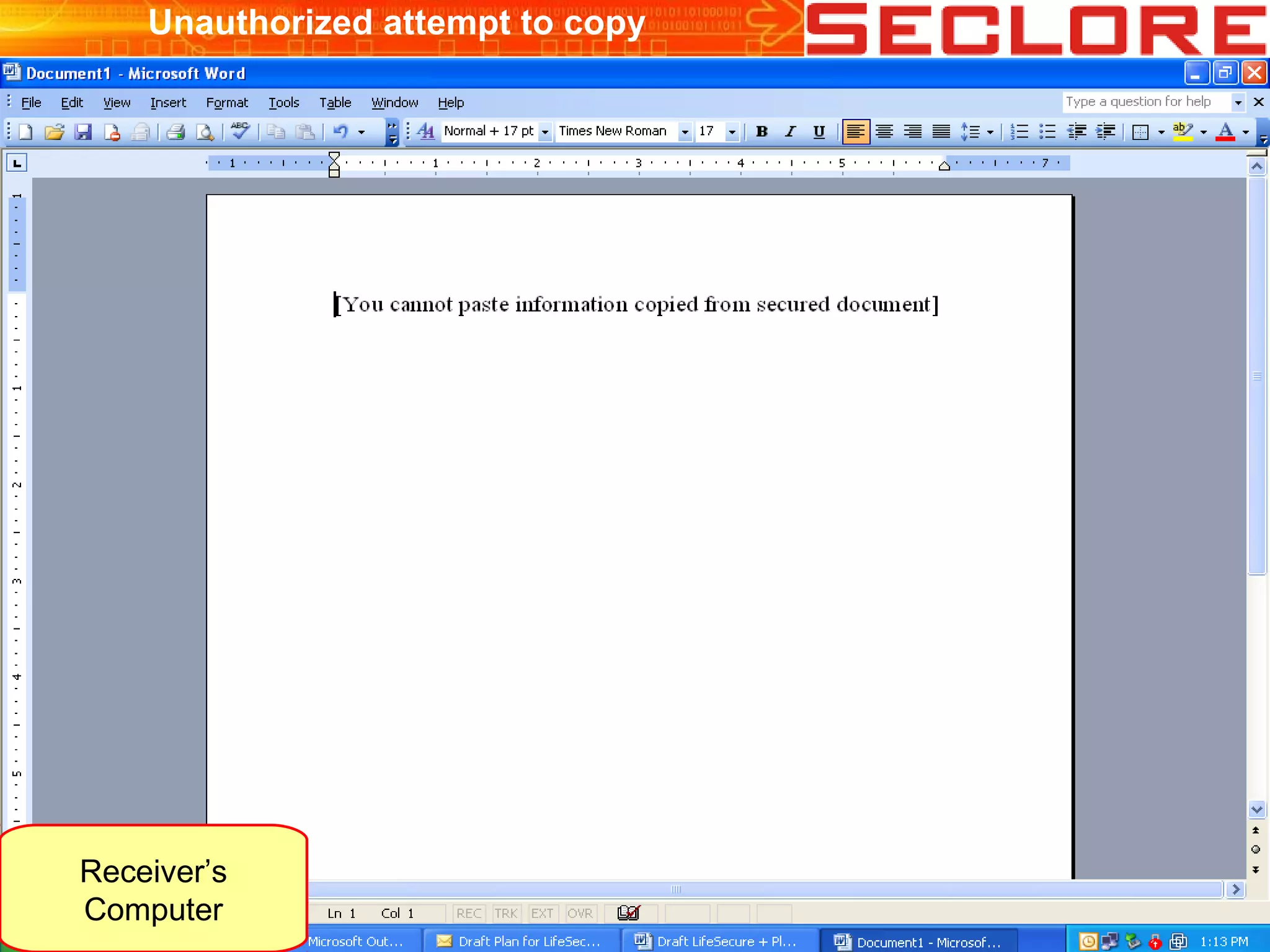
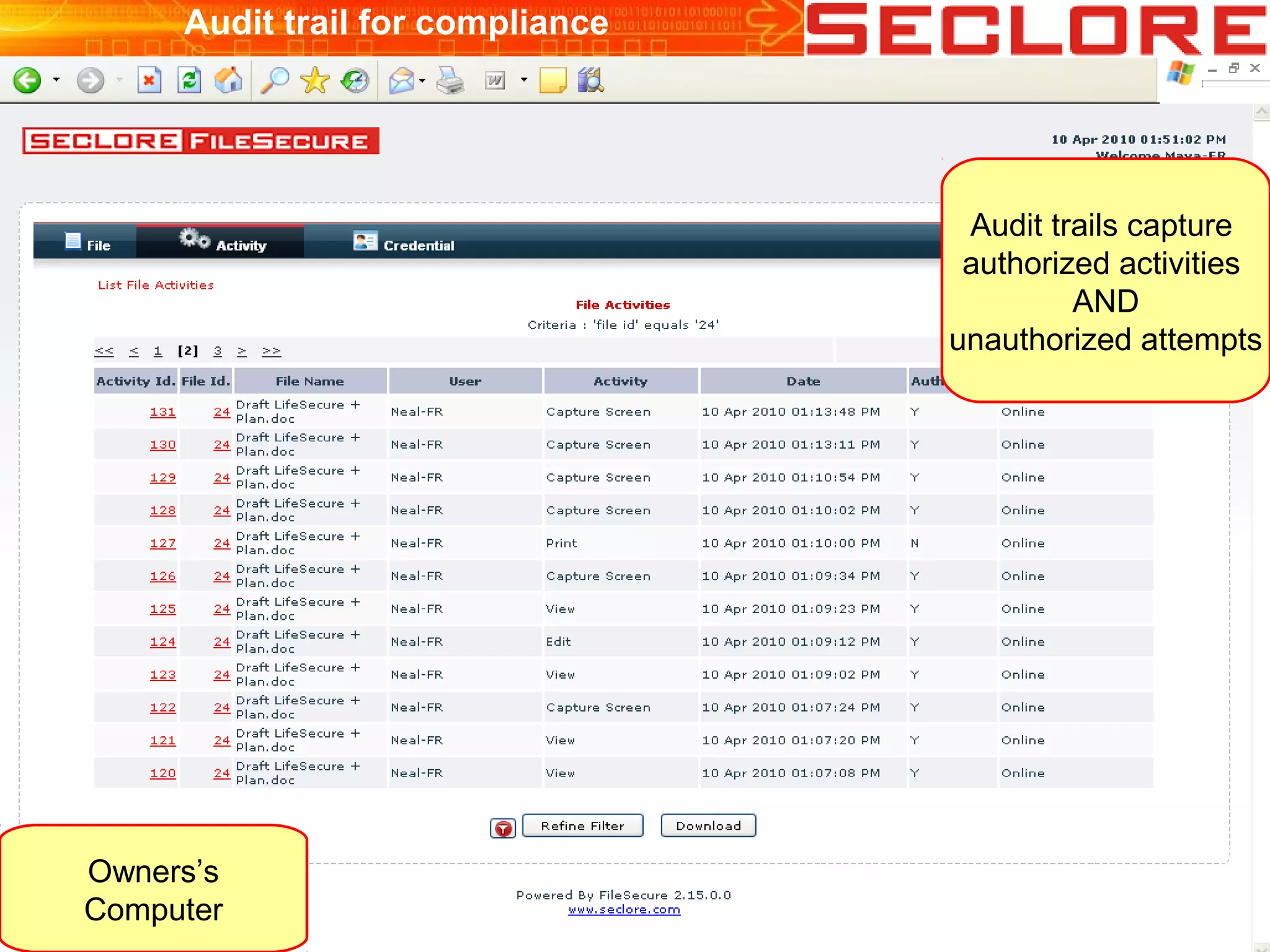
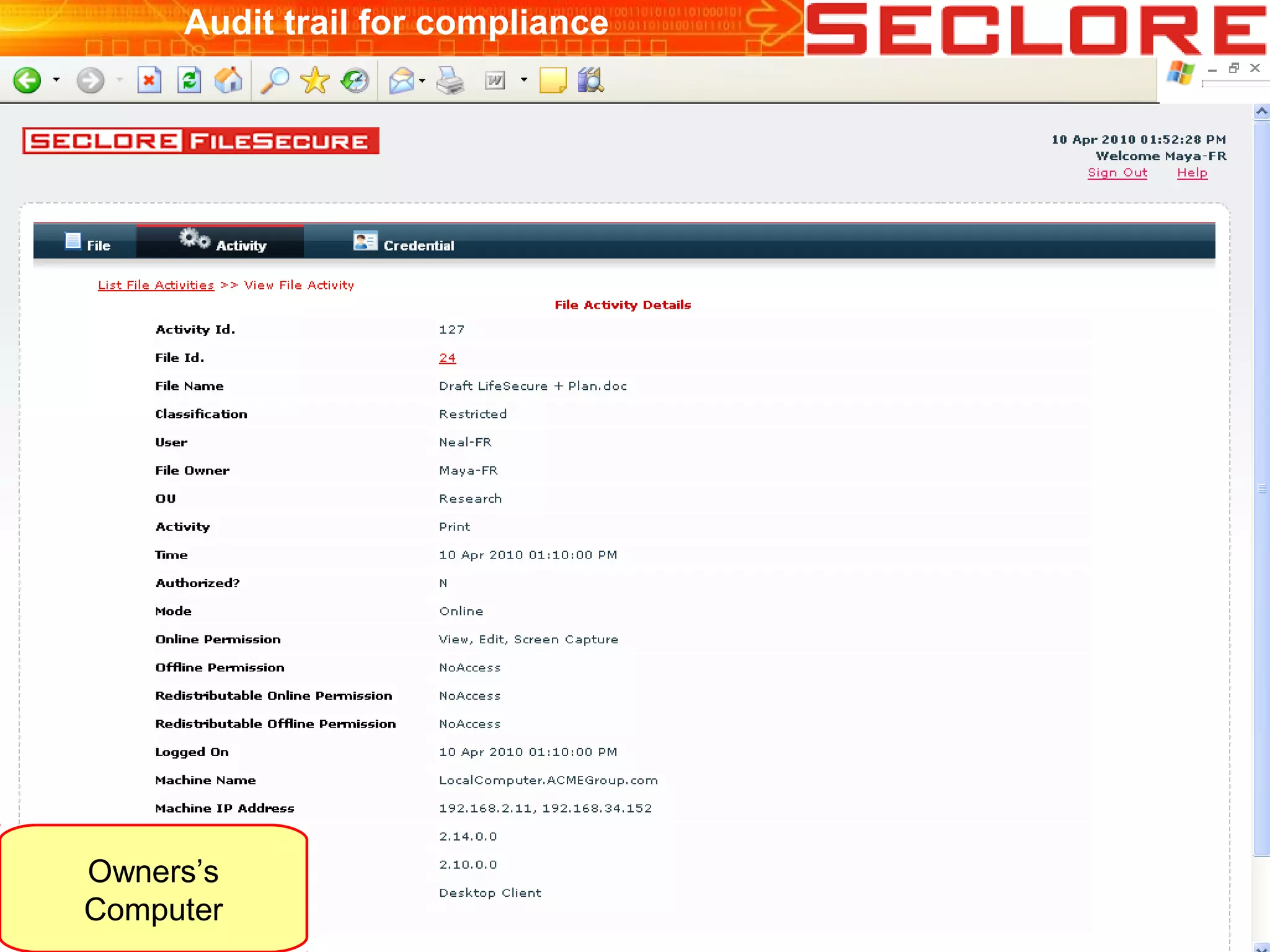
The document discusses Information Rights Management (IRM) security and compliance for unstructured information, emphasizing the significance of controlling information distribution and usage within organizations. It highlights potential risks regarding information sharing with employees, vendors, and competitors, and proposes strategies for secure collaboration by defining user rights, actions, and access locations for information. Seclore, the company highlighted in the document, provides solutions to ensure information security while enabling collaboration through their product, Seclore FileSecure.





![Thank You
Vishal Gupta
info [at] seclore dot com
+91-22-4015-5252
www.seclore.com](https://image.slidesharecdn.com/whatisirm-brighttalk-101130015307-phpapp01/75/What-is-IRM-bright-talk-24-2048.jpg)