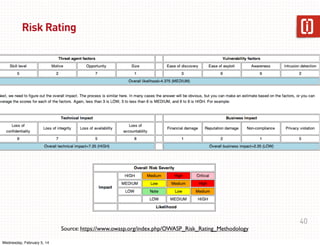
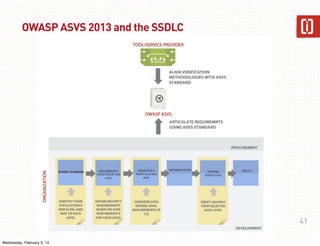
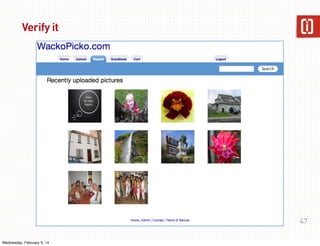
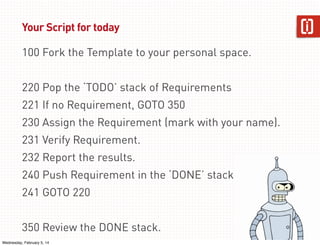
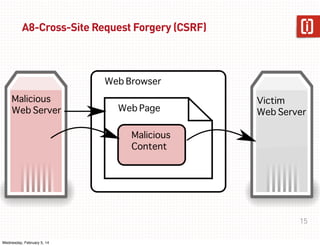
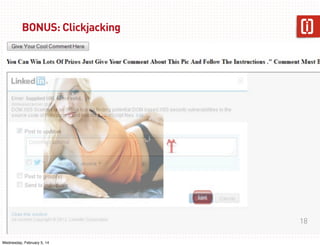
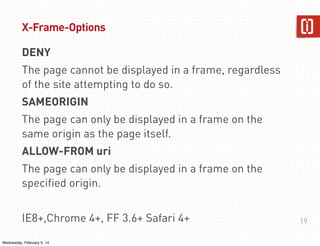
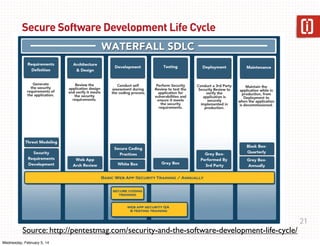
This document summarizes a presentation on web application security given on January 29th, 2014. The presentation covered common web application vulnerabilities like injection flaws, broken authentication, insecure direct object references, cross-site scripting, and more. It also discussed the OWASP Top 10 risks and how to address them through practices like following the OWASP Application Security Verification Standard (ASVS) and implementing a secure software development lifecycle with security testing throughout. Attendees were given an assignment to participate in an "ASVS Bingo" verification exercise of the OWASP requirements.


























![An AASVS Requirement has...
‣ Short Title
‣ Long Title
‣ Verification PASS
‣ Verification FAIL
‣ Verification Help
‣ [Verification Help for PHP]
‣ [Verification Help for Drupal]
‣ [Verification Help for Symfony 2]
‣ Related Resources
38
Wednesday, February 5, 14](https://image.slidesharecdn.com/webappsec-at-ibuildings-140219022420-phpapp01/85/WebAppSec-Ibuildings-in-2014-38-320.jpg)