This document summarizes Shawn Merdinger's presentation on weaponizing consumer devices like the Nokia N900 smartphone. Some key points:
1) The Nokia N900 is highlighted as a powerful open platform that can run security tools like nmap, Kismet, and Ettercap out of the box.
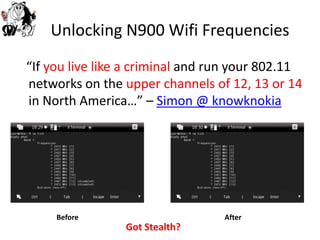
2) Wireless attacks demonstrated on the N900 include rogue access point deployment, packet injection, MITM attacks, and wireless sniffing.
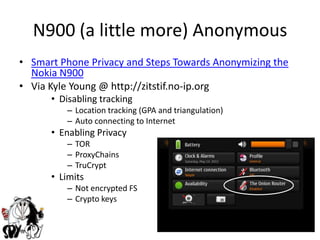
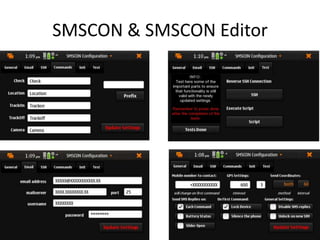
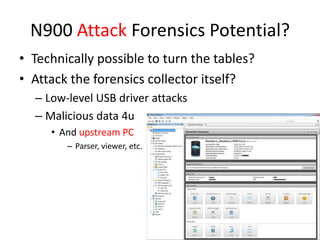
3) Other attacks discussed include using the N900 for voip attacks, Bluetooth/Zigbee attacks, SMS command and control, and digital forensics avoidance.
4) Running alternative operating systems on the N900