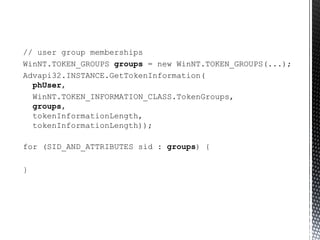
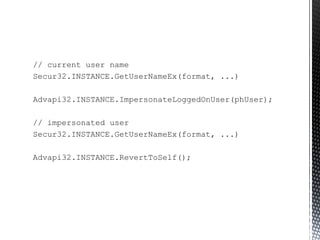
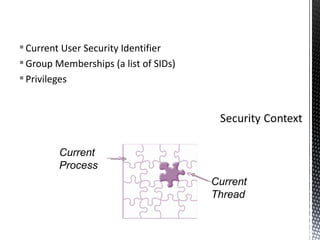
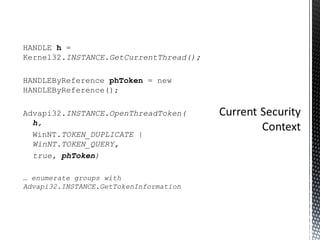
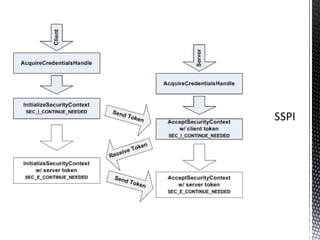
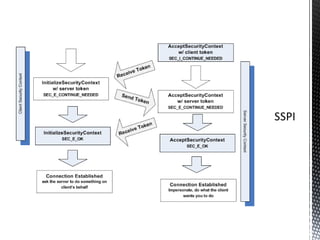
The document discusses authentication and authorization on Windows domains using Active Directory. It describes how to programmatically retrieve a user's group memberships by using Windows API functions to log in with a username and password, get the user token, and enumerate the groups in the token. It also introduces Waffle, an open-source Java library that provides Windows authentication functionality for application servers like Tomcat.