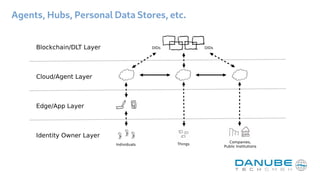
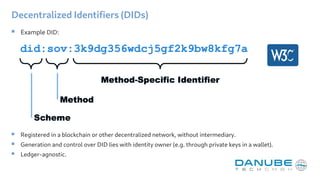
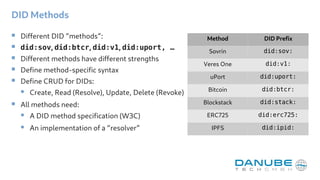
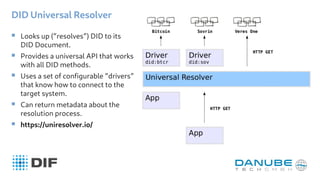
The document provides an overview of decentralized identifiers (DIDs) and the DID universal resolver. It discusses how DIDs enable self-sovereign identity and describes their key properties. It then explains how the universal resolver allows looking up DID documents across different DID methods through configurable drivers. Finally, it outlines several potential applications of DIDs like verifiable credentials, authentication, and decentralized key management.




![DID Resolution
DID Resolution: DID → DID Document
Set of public keys
Set of service endpoints
Timestamps, proofs
Other identifier metadata
May be dynamically constructed
rather than actually stored in this form.
Resolution parameters can select
parts of the DID document.
{
"@context": "https://w3id.org/did/v1",
"id": "did:sov:WRfXPg8dantKVubE3HX8pw",
"service": {
"type": "hub",
"serviceEndpoint":
"https://azure.microsoft.com/dif/hub/did:sov:WRfXPg8dantKVubE3H"
},
"publicKey": [
{
"id": "did:sov:WRfXPg8dantKVubE3HX8pw#key-1",
"type": "Ed25519VerificationKey2018",
"publicKeyBase58": "H3C2AVvLMv6gmMNam3uVAjZpfkcJCwDmqPV"
}
],
"authentication": {
"type": "Ed25519SignatureAuthentication2018",
"publicKey": [
"did:sov:WRfXPg8dantKVubE3HX8pw#key-1"
]
}
}
Example DID Document:](https://image.slidesharecdn.com/masterclassonthediduniversalresolver-181102122653/85/Masterclass-on-the-DID-Universal-Resolver-6-320.jpg)




![Verifiable Credentials
Example:
{
"@context": "https://w3id.org/credentials/v1",
"id": "did:sov:WRfXPg8dantKVubE3HX8pw/credentials/1",
"type": ["Credential", "NameCredential"],
"issuer": "did:sov:WRfXPg8dantKVubE3HX8pw",
"issued": "2018-05-01",
"claim": {
"id": "did:btcr:x6lj-wzvr-qqrv-m80w",
"name": "Jane Doe"
},
"proof": {
"type": "RsaSignature2018",
"created": "2017-06-18T21:19:10Z",
"creator": "did:sov:WRfXPg8dantKVubE3HX8pw#key-1",
"nonce": "c0ae1c8e-c7e7-469f-b252-86e6a0e7387e",
"signatureValue": "BavEll0/I1zpYw8XNi1bgVg/sCneO4Jugez8RwDg/+
MCRVpjOboDoe4SxxKjkCOvKiCHGDvc4krqi6Z1n0UfqzxGfmatCuFibcC1wps
PRdW+gGsutPTLzvueMWmFhwYmfIFpbBu95t501+rSLHIEuujM/+PXr9Cky6Ed
+W3JT24="
}
}](https://image.slidesharecdn.com/masterclassonthediduniversalresolver-181102122653/85/Masterclass-on-the-DID-Universal-Resolver-13-320.jpg)