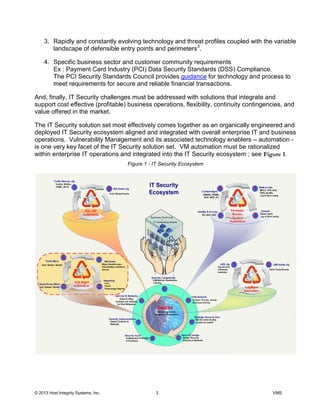
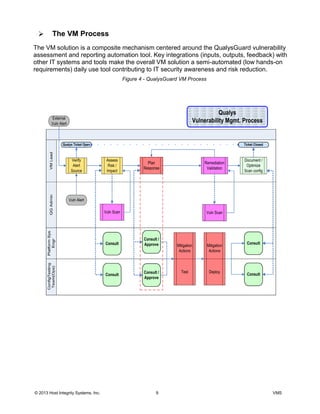
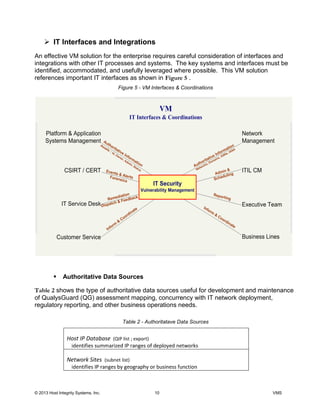
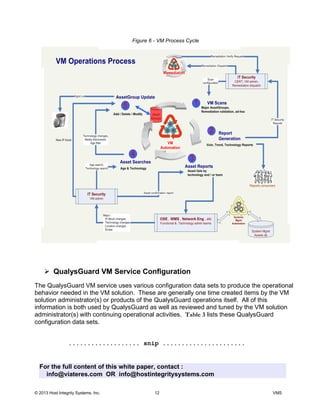
This document discusses the deployment of a vulnerability management solution using QualysGuard. It proposes a strategy of collaboration, integration, and automation (CIA). The solution would integrate QualysGuard vulnerability assessments with existing IT systems and processes. This would allow vulnerabilities to be detected and remediated efficiently while minimizing new infrastructure. Authoritative data sources would be used to map assessments and allow QualysGuard data to refine asset tracking over time. The solution is intended to provide vulnerability management while reducing costs and integrating with IT operations.