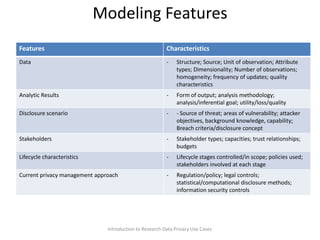
The document discusses the integration of privacy approaches across the research data lifecycle, outlining use cases related to data privacy, stakeholder concerns, and legal frameworks. It emphasizes the importance of balancing privacy and replicability in research outputs while addressing the challenges of data management and analysis. The document also raises essential questions regarding current practices, enhancing methodologies, and future directions in managing research data privacy.

![DISCLAIMER
These opinions are my own, they are not the opinions
of MIT, Brookings, any of the project funders, nor (with
the exception of co-authored previously published
work) my collaborators.
Secondary disclaimer:
“It’s tough to make predictions, especially about the
future!”
-- Attributed to Woody Allen, Yogi Berra, Niels Bohr, Vint Cerf, Winston Churchill,
Confucius, Disreali [sic], Freeman Dyson, Cecil B. Demille, Albert Einstein, Enrico Fermi,
Edgar R. Fiedler, Bob Fourer, Sam Goldwyn, Allan Lamport, Groucho Marx, Dan Quayle,
George Bernard Shaw, Casey Stengel, Will Rogers, M. Taub, Mark Twain, Kerr L. White,
etc.
Introduction to Research Data Privacy Use Cases](https://image.slidesharecdn.com/usecaseoverview-130924145112-phpapp02/85/Privacy-in-Research-Data-Managemnt-Use-Cases-2-320.jpg)



![ExampleUseCases Name/Description Examples
Comparison case: Official Statistics
Well-resourced data collector summarizes
tables/relational data in the form of summary
statistics and contingency tables
• U.S. Census dissemination
• European statistical agencies
Privacy-Aware Journal Replication Policies
Scholarly journals adopting policies for deposit
and disposition of data for verification and
replication. How to balance privacy and
replicability without intensive review?
• Data Sharing Systems for Open Access
Journals
• American Political Science Association Data
Access and Research Transparency [DART]
Policy Initiative
Long-term Longitudinal data Collection
Data collections tracking individual subjects (and
possibly friends and relations) over decades
• National Longitudinal Study of Adolescent
Health (Add Health)
• Framingham Heart Study
• Panel Study of Income Dynamics
Computational Social Science
“Big” data. New forms and sources of data.
Cutting-edge analytical methods and algorithms.
Analyzing …
• Netflix
• Facebook
• Hubway
• GPS
• Blogs
Introduction to Research Data Privacy Use Cases](https://image.slidesharecdn.com/usecaseoverview-130924145112-phpapp02/85/Privacy-in-Research-Data-Managemnt-Use-Cases-12-320.jpg)



