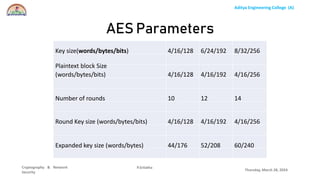
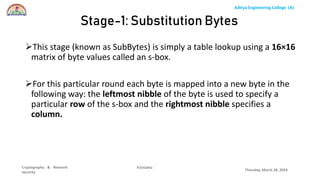
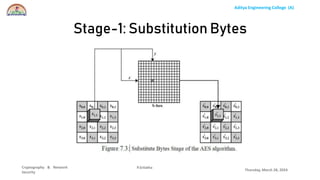
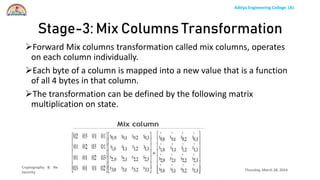
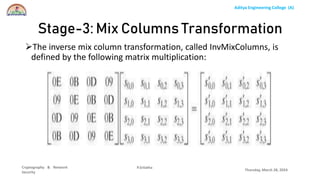
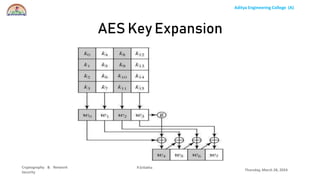
The document discusses the Advanced Encryption Standard (AES) algorithm. AES is a symmetric block cipher that uses 128-bit blocks and 128, 192, or 256-bit keys. It operates on a 4x4 column-row matrix through a series of transformations including byte substitution, shifting rows, mixing columns, and adding a round key. The key is expanded through successive XOR operations to derive round keys for each round. At the end of the class, students will be able to implement AES to securely transfer data over a network.