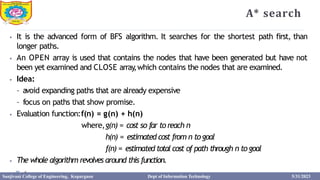
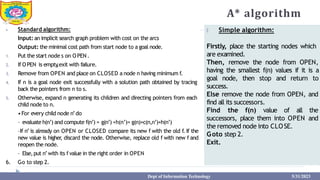
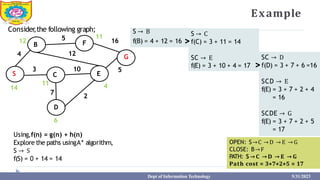
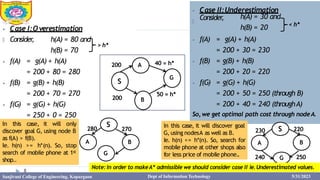
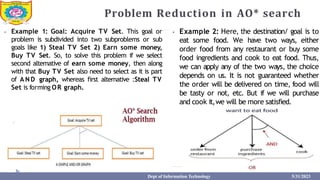
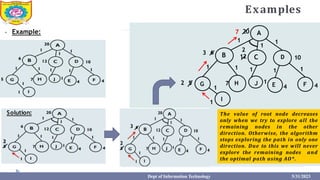
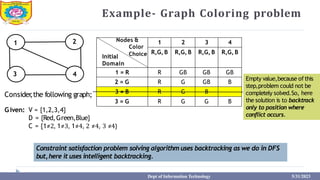
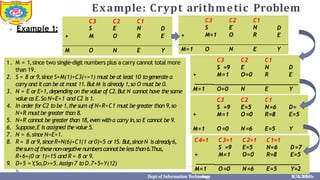
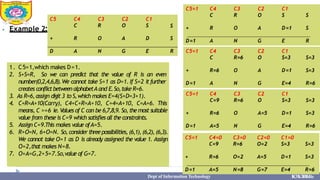
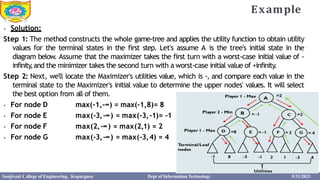
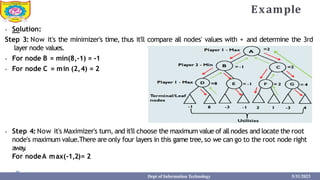
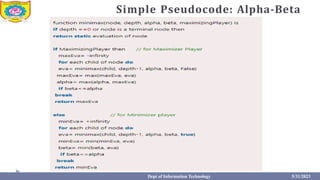
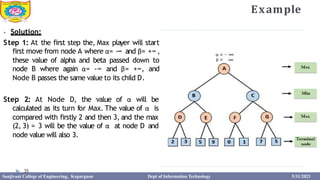
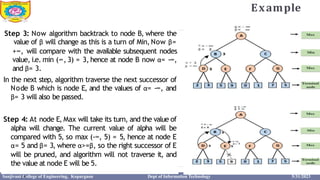
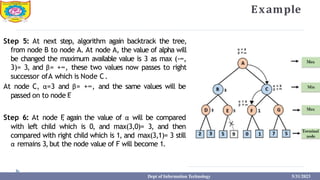
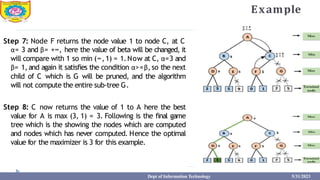
This document provides information about the A* search algorithm. It begins with an overview of A* search and its advantages and disadvantages. It then discusses the concepts of admissibility and consistency which are required for A* search to be optimal. The standard A* algorithm is presented involving maintaining OPEN and CLOSE lists. An example of running A* search on a graph is provided. Finally, it discusses how to make A* search admissible by ensuring the heuristic function underestimates the actual cost rather than overestimating it.