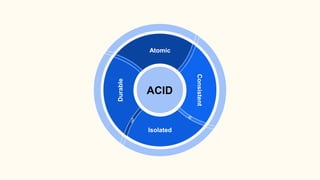
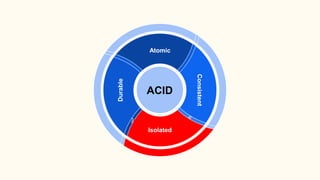
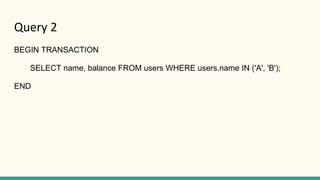
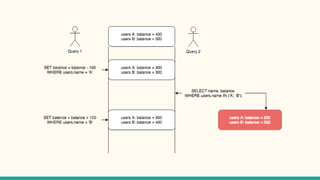
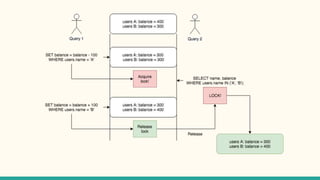
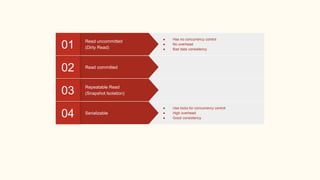
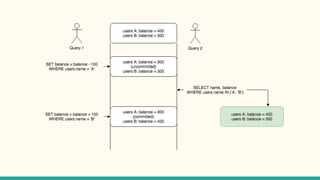
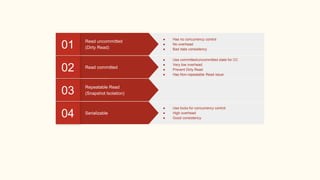
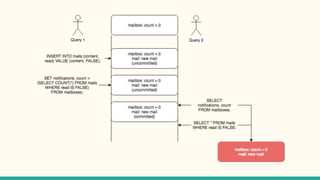
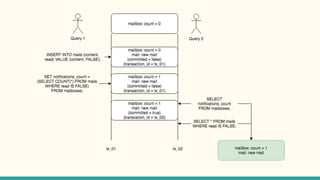
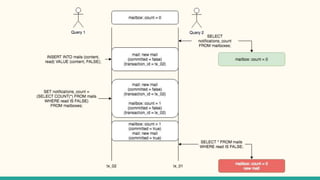
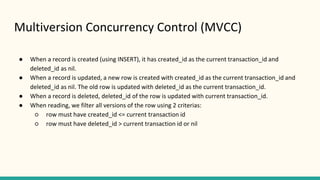
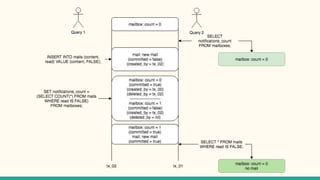
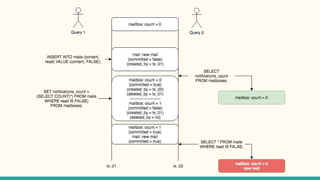
The document outlines various isolation levels in database transactions, including serializable, repeatable read, read committed, and read uncommitted. It discusses the trade-offs between consistency and concurrency for each level and describes how transactions are handled and their visibility to other transactions. The conclusion emphasizes the importance of selecting the appropriate isolation level to prevent data inconsistency.