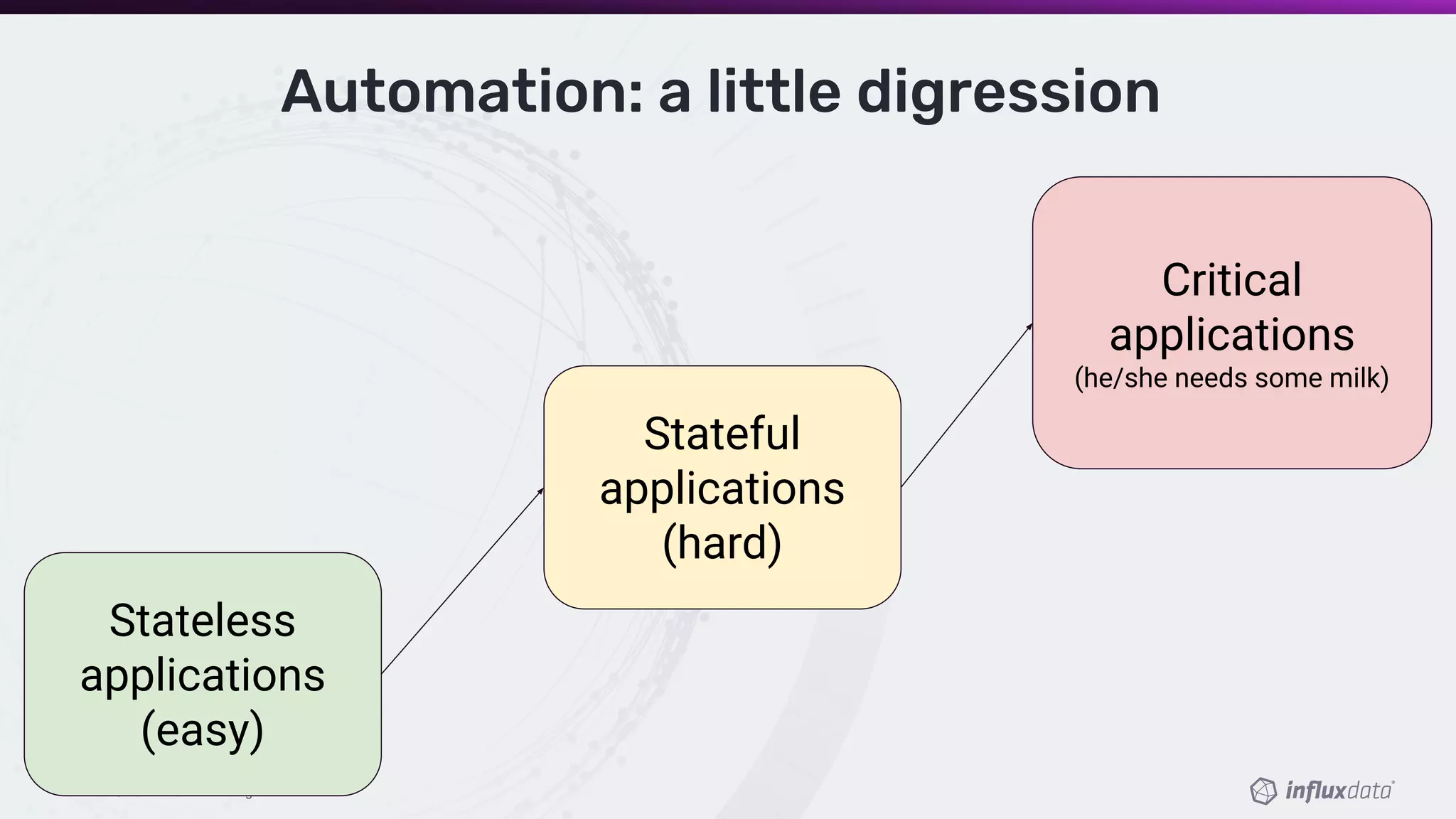
The document discusses challenges in managing Kubernetes clusters and how Vault can assist in addressing security and automation issues. It emphasizes the importance of managing secrets and credentials, particularly in multi-cluster and multi-cloud environments. The webinar outlines various solutions, including using Vault to simplify access control and enhance operational efficiency.















![© 2019 InfluxData. All rights reserved.27
[[inputs.x509_cert]]
sources = [
"/etc/kubernetes/pki/ca.crt",
"/etc/kubernetes/pki/front-proxy-ca.crt",
"/etc/kubernetes/pki/front-proxy-client.crt",
"/etc/kubernetes/pki/etcd/ca.crt",
"/etc/kubernetes/pki/etcd/peer.crt",
"/etc/kubernetes/pki/etcd/healthcheck-client.crt",
"/etc/kubernetes/pki/etcd/server.crt",
"/etc/kubernetes/pki/apiserver.crt",
"/etc/kubernetes/pki/apiserver-kubelet-client.crt",
"/etc/kubernetes/pki/apiserver-etcd-client.crt",
]
Monitoring Certifcates with Telegraf](https://image.slidesharecdn.com/kubernetesvaultwebinardevops-191105192055/75/Troubles-in-Kubernetes-Land-Vault-to-the-Rescue-27-2048.jpg)