Embed presentation
Download to read offline



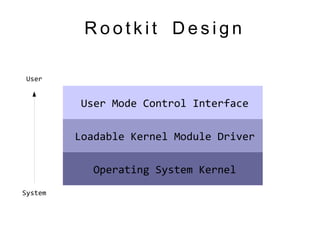
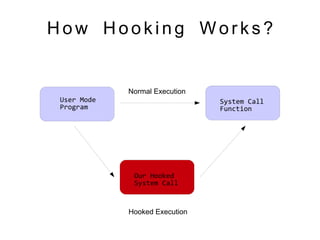



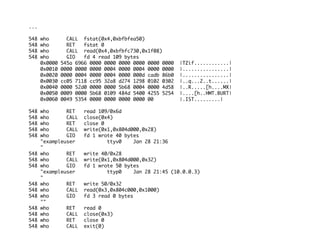






The document discusses UNIX rootkits and how they can hijack system calls in the Linux kernel to achieve stealth. It explains how rootkits work by loading kernel modules that hook system calls to hide processes, files, network ports and more. The document also provides examples of how rootkits can hijack specific system calls like open, read, write and more to implement stealth and covert functionality.














