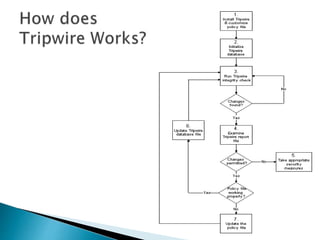
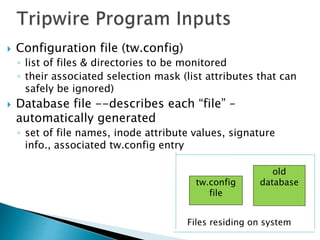
Tripwire is a free and open-source software tool that monitors key attributes of files to detect changes from an established baseline. It creates a database of original file attributes and then constantly checks for any unauthorized changes, reporting them to the user. Tripwire can increase security, accountability, and visibility of changes while also ensuring availability through rapid detection and recovery. However, it has some limitations with frequently changing files and requires more effort to install and maintain.