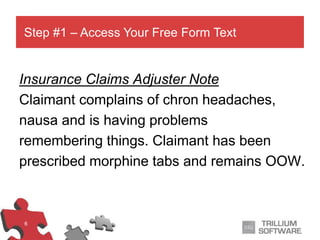
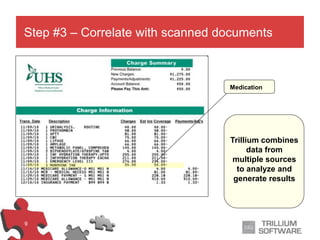
The document outlines a process for rapidly and accurately identifying high-risk insurance claims using automation. It describes the steps involved, including accessing free form text, flagging risk indicators, correlating data with scanned documents, and alerting the right adjuster at the appropriate time. The goal is to minimize risk, reduce costs, and optimize resource allocation to prevent potential insurance claim issues.