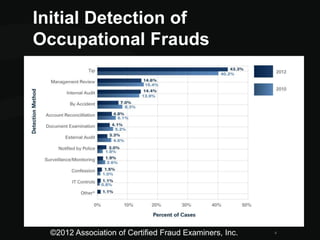
This document discusses whistleblower strategies and fraud detection methods. It recommends establishing secure whistleblower hotlines to detect fraud through anonymous tips in local languages. Effective hotlines are available 24/7 through multiple channels, ensure confidentiality and anonymity, and have response teams that thoroughly review and investigate all cases. The document promotes a customized online hotline called Scethicsline.com that supports these best practices for detecting fraud through whistleblower tips.