This document outlines Kent Farries' presentation on how TransAlta Corporation uses Splunk for security and operational intelligence. Some key points:
- TransAlta generates over 18 billion events per month that are indexed in Splunk.
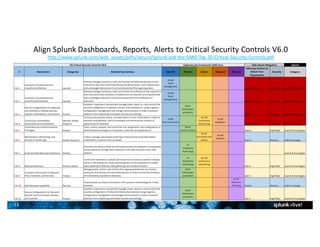
- Splunk consolidated data from multiple legacy systems and tools into a single platform, improving investigation times and allowing cross-team analysis.
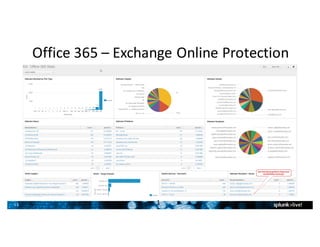
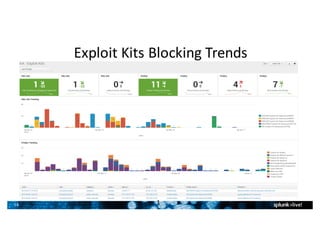
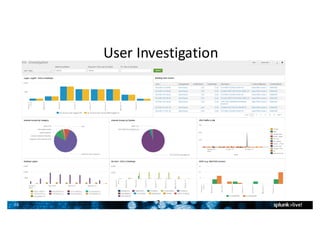
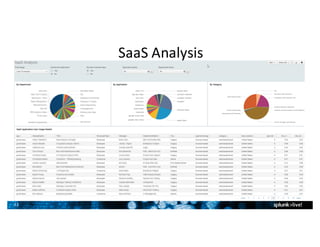
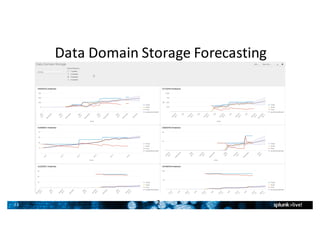
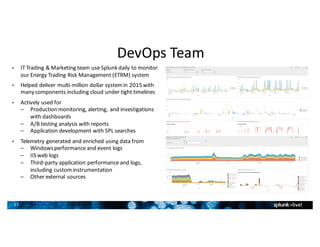
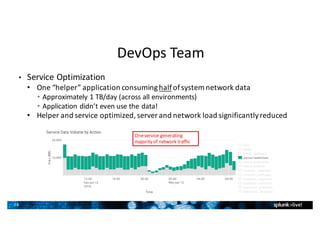
- Splunk supports a wide range of use cases across IT security, operations, and DevOps. Example dashboards and alerts were shown for security monitoring, infrastructure monitoring, and application development/testing.
- Future plans include expanding endpoint monitoring, integrating additional data sources, and using Splunk for compliance reporting and awareness training.