Embed presentation
Download to read offline




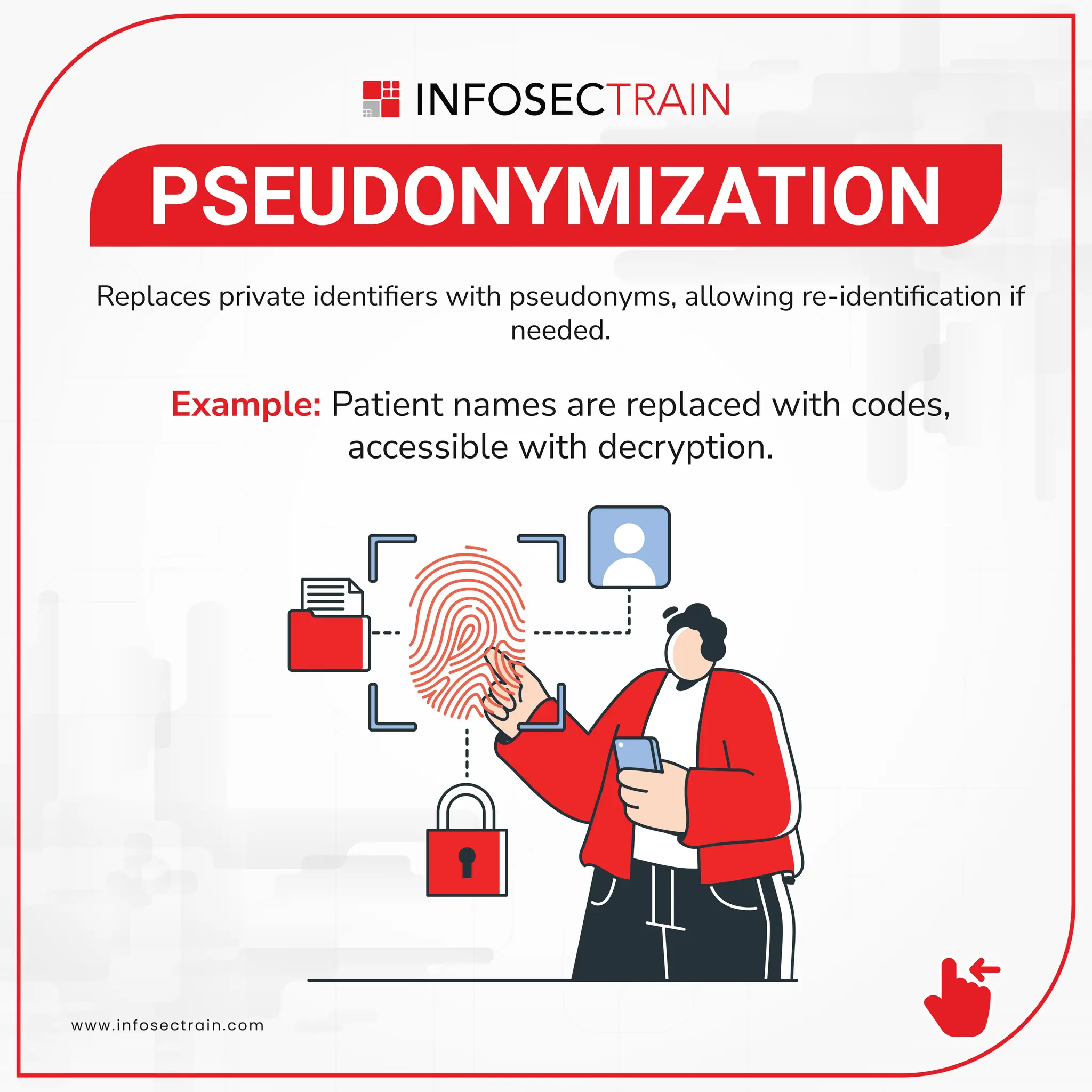




The document outlines various data anonymization techniques aimed at replacing sensitive information while preserving its utility for analysis. Techniques include data masking, generalization, data swapping, pseudonymization, data perturbation, and synthetic data generation. Each technique provides examples to illustrate how sensitive data can be modified or replaced to maintain privacy during testing or analysis.







