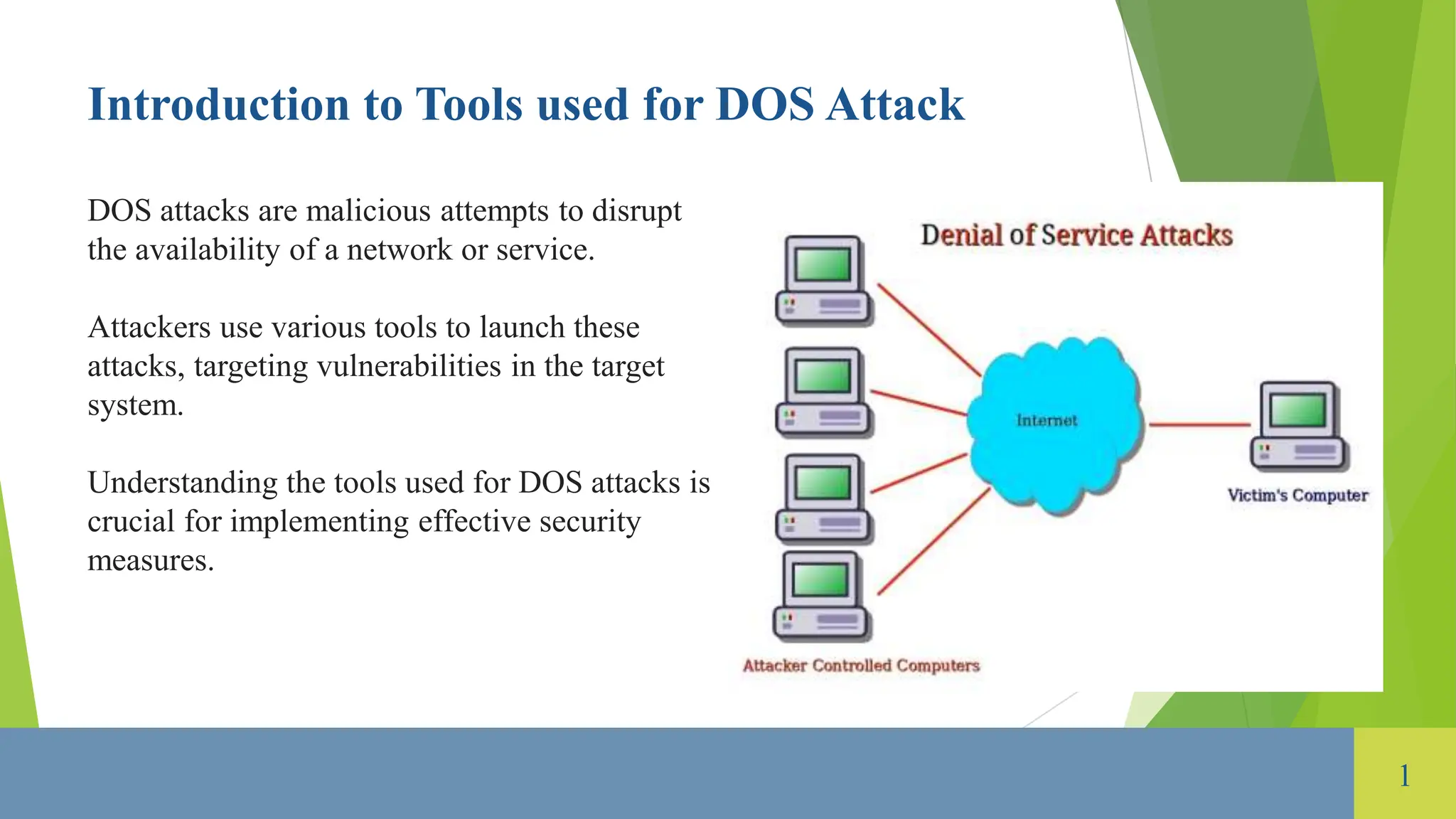
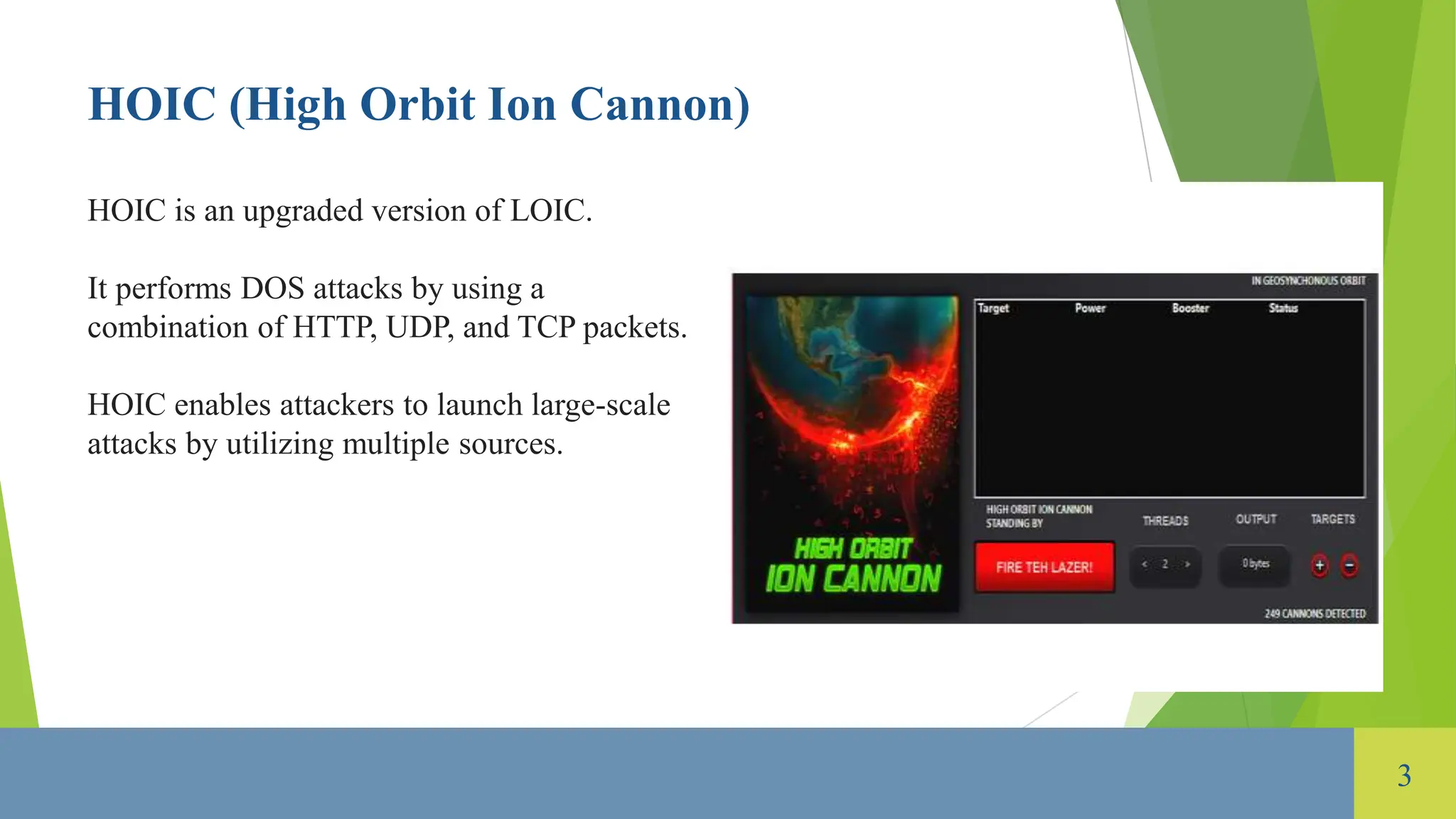
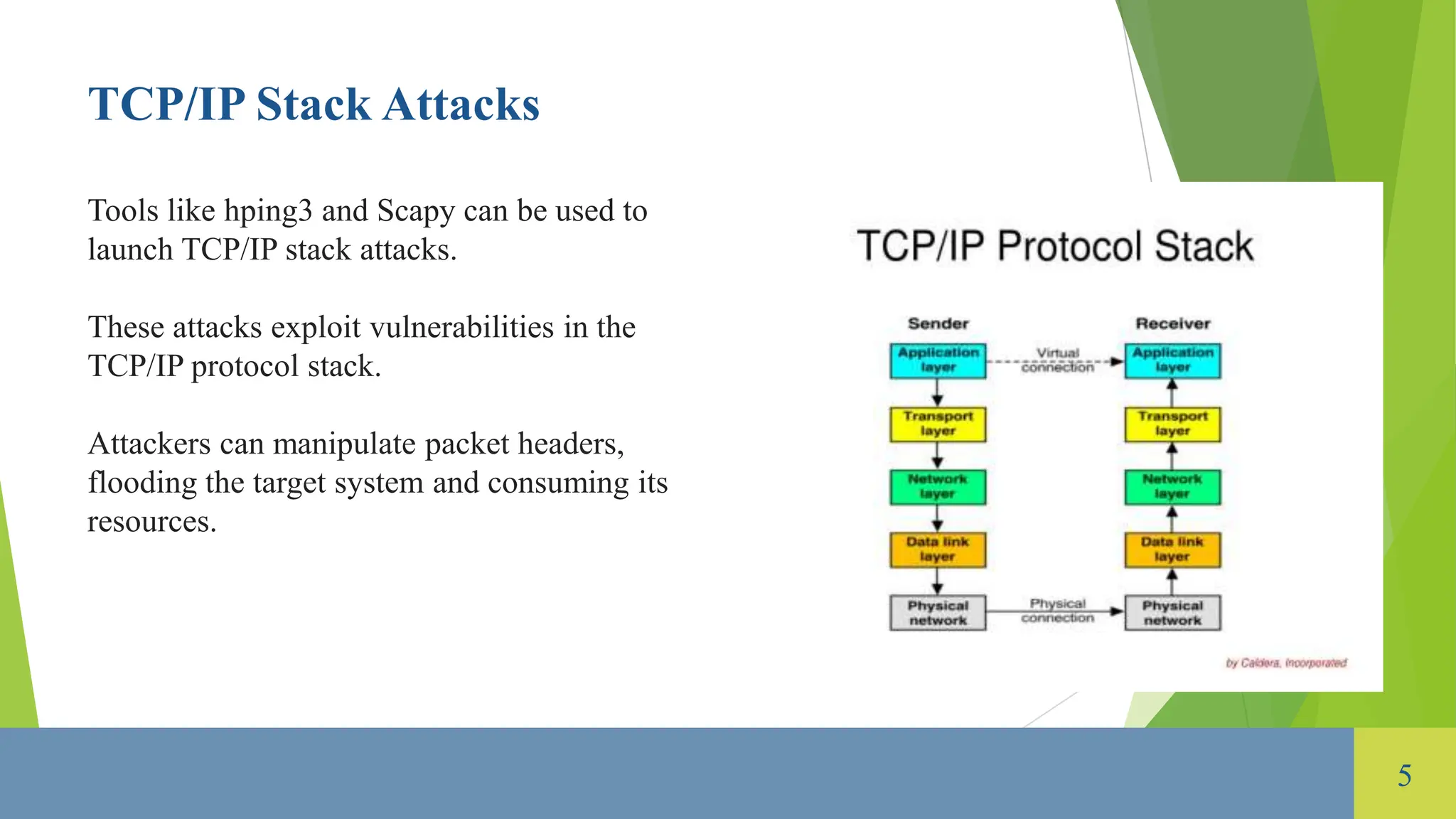
The document provides an overview of tools used for launching Denial of Service (DoS) attacks, which aim to disrupt the availability of networks or services. Various types of DoS attacks are discussed, including volume-based, protocol, and application layer attacks, along with tools such as LOIC, HOIC, Slowloris, and various UDP and ICMP flood attack tools. Additionally, the document highlights defense mechanisms like intrusion prevention systems and firewalls to mitigate these attacks.